#itsecurity 搜索结果
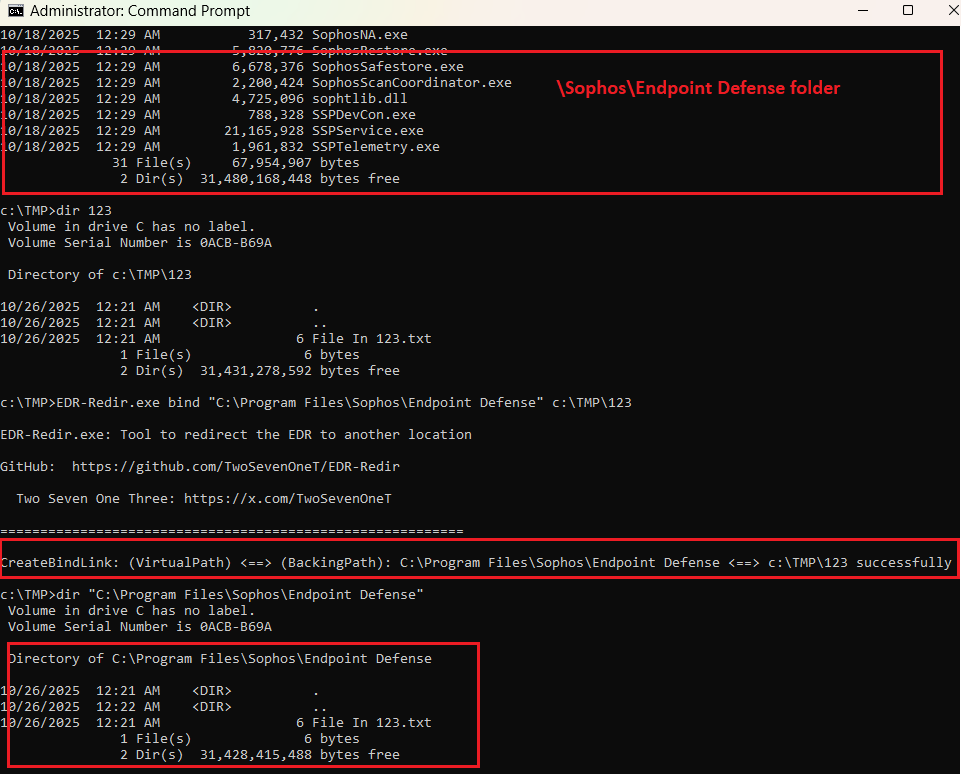
EDR-Redir: You can break EDRs/Antivirus from user mode with bind link and cloud minifilter. Because your payload deserves privacy. #antimalware #itsecurity #redteam

#PAM strengthens security by controlling privileged access, enforcing least privilege, automating workflows & ensuring compliance—protecting critical systems while improving efficiency across environments. bit.ly/3XlEfOR #ITSecurity #Cybersecurity #IAM

EDR-Redir V2 can redirect entire folders like "Program Files" to point back to themselves, except for the folders of #antimalware EDR. This means that other software continues to function normally, while only the EDR is redirected or blocked. #itsecurity #redteam



Is your IT ready for the Windows's security requirements? Microsoft’s NTLM deprecation is happening now, soon to be blocked by default. ➡️ Kerberos is now mandatory for Windows monitoring. Read more: adremsoft.com/blog/view/blog… #ITSecurity #InfoSec #Kerberos #ITManagement #SecureIT

Most companies rely on vendors who've been breached. In 2024, 61% of incidents stemmed from third parties, and vendor-related ransomware made up 70% of all claims. MoveIt alone hit 2,700 orgs, exposing 93M records. #cybersecurity #infosec #itsecurity trustle.com/post/secure-ve…
🔗 tinyurl.com/3pezfmr9 “Identity is the thing attackers ride once they’re in.” Google Cloud Threat Horizons H2 2025 flags prolonged access, supply-chain exposure, and identity misuse in GCP environments. #cybersecurity #itsecurity #infosec

Because in today’s world, security isn’t just an option, it’s the foundation. #TranterIT #Cybersecurity #ITSecurity #DigitalTransformation #DataProtection #TechInnovation #BusinessSecurity
AI adoption is accelerating. Is your cyberdefense keeping pace? Discover how GenAI-powered threat intelligence can proactively detect and mitigate threats like prompt injection, shadow AI, and sensitive data exposure. zurl.co/Ec01Y #Cybersecurity #GenAI #ITsecurity

Security teams are fond of saying, “Identity is the new perimeter,” but that perimeter doesn’t check for opposable thumbs... Today, identity sprawl is more than a human problem. It’s a machine problem. #cybersecurity #itsecurity #InfoSec trustle.com/post/non-human…
The #cybersecurity skills shortage has become a global risk amplifier, fueling more breaches and higher costs. With 4.7M+ unfilled roles, it’s time to step in, skill up, and close the gap, says @Fortinet's Melonia da Gama. #ITsecurity #CISO #infosec #AI bit.ly/4o8N893
New ID‑driven breach research shows that many cloud incidents stem less from exotic zero‑days and more from identity compromise and process failures (e.g., over‑privileged roles, stale accounts, weak IAM hygiene). #cybersecurity #itsecurity #infosec tinyurl.com/5cb3pvdp
Redesign done <3 dsecured.com/en - now all relevant processes in the background (offers, quoting, invoices, reporting, ...) are mostly automated. #pentest #itsecurity #offsec
Ten npm packages, using typosquatting to imitate popular legitimate packages, were found to spread credential-stealing malware hidden under four layers of obfuscation, @SocketSecurity reported. #cybersecurity #infosec #ITsecurity #CISO bit.ly/4qHmJSb
🚨 Critical Alert: Microsoft Entra ID (formerly Azure AD) had a vulnerability (CVE-2025-55241) that let attackers impersonate any user, including Global Admins, bypassing MFA & going unnoticed. #cybersecurity #infosec #itsecurity Patch now. ➤ thehackernews.com/2025/09/micros…
thehackernews.com
Microsoft Patches Critical Entra ID Flaw Enabling Global Admin Impersonation Across Tenants
Microsoft patched CVE-2025-55241 July 17, 2025; CVSS 10.0 Entra ID bug via legacy Graph enabled cross-tenant impersonation risking tenant compromise.
⏰ Deadline extended Network and Security Engineer: 📍Paris, France 📅 Application deadline: 6 October 2025 at 23:59 (Paris time) 🖱️ ow.ly/giLH50X5vpH #ITSecurity #Vacancy #Hiring #NetworkSecurity #OECDCareers



This week, we spoke with our friend and @Trustle advisor, Bruce Schneier, about access management, cloud identity risks, and his upcoming book. #cybersecurity #infosec #itsecurity youtu.be/CjQO2V6ubgk

youtube.com
YouTube
A Converstion with Bruce Schneier | November 2025.
#PAM strengthens security by controlling privileged access, enforcing least privilege, automating workflows & ensuring compliance—protecting critical systems while improving efficiency across environments. bit.ly/3XlEfOR #ITSecurity #Cybersecurity #IAM

Missed our cybersecurity webinar? Access the on-demand session for actionable strategies to strengthen your defenses, ensure compliance, and protect your business from evolving threats. #CyberSecurity #ITSecurity #ITServices #MSP #TechnologyServices

AI adoption is accelerating. Is your cyberdefense keeping pace? Discover how GenAI-powered threat intelligence can proactively detect and mitigate threats like prompt injection, shadow AI, and sensitive data exposure. zurl.co/Ec01Y #Cybersecurity #GenAI #ITsecurity

The #cybersecurity skills shortage has become a global risk amplifier, fueling more breaches and higher costs. With 4.7M+ unfilled roles, it’s time to step in, skill up, and close the gap, says @Fortinet's Melonia da Gama. #ITsecurity #CISO #infosec #AI bit.ly/4o8N893
🚨 „Versichert = geschützt“? Falsch! Cyberversicherungen zahlen nur, wenn IT-Sicherheit stimmt. 🔒 ➡️Mehr im ESET Whitepaper: eset.com/de/about/press… #Cyberversicherung #ITSecurity #Risikomanagement #ESET #Cybersecurity #MadeInEU

Protect your business from risks and stay compliant with smart IT solutions. Call today and strengthen your security! 🔐💻📞 #ClarksburgMD #ITSecurity #DataProtection #RiskManagement #CyberDefense
Is your IT ready for the Windows's security requirements? Microsoft’s NTLM deprecation is happening now, soon to be blocked by default. ➡️ Kerberos is now mandatory for Windows monitoring. Read more: adremsoft.com/blog/view/blog… #ITSecurity #InfoSec #Kerberos #ITManagement #SecureIT

🚨 „Versichert = geschützt“? Falsch! Cyberversicherungen zahlen nur, wenn IT-Sicherheit stimmt. 🔒 ➡️Mehr im ESET Whitepaper: eset.com/de/about/press… #Cyberversicherung #ITSecurity #Risikomanagement #ESET #Cybersecurity #MadeInEU

EDR-Redir: You can break EDRs/Antivirus from user mode with bind link and cloud minifilter. Because your payload deserves privacy. #antimalware #itsecurity #redteam


#PAM strengthens security by controlling privileged access, enforcing least privilege, automating workflows & ensuring compliance—protecting critical systems while improving efficiency across environments. bit.ly/3XlEfOR #ITSecurity #Cybersecurity #IAM

EDR-Redir V2 can redirect entire folders like "Program Files" to point back to themselves, except for the folders of #antimalware EDR. This means that other software continues to function normally, while only the EDR is redirected or blocked. #itsecurity #redteam



Ab morgen laden wir Sie auf der it-sa 2025 in Nürnberg herzlich an unserem Stand 328 in Halle 9 auf einen erfrischenden Smoothie oder einen Barista-Kaffee ein. #itsa2025 #Digitalisierung #ITSecurity 👉 beyondtrust.com/de/events/it-s…

(only one more) 👻#ITSecurity at #Halloween 🎃 “Free Wi-Fi”🍬 “Click Me”🍭 “Open Attachment”🍫 Looks sweet – but tastes like #Ransomware🤢 Not every treat is sweet… some hide a nasty #Phishing trick 🕷️ 💡 Think before you click 🛑 #CyberSecurity #Awareness #HanseSecure #ITSec

Security isn’t just tech - it’s people. Empower teams to spot risks and protect data. 👉 okt.to/3jtdF1 #Security #ITSecurity #SharpEurope

Prevention > Reaction. 🛡️ Always. But what if prevention could be... automatic? The revolution begins November 2025. #CyberDefense #AI #ITSecurity

"Why didn't we see this coming?" – Every MSP, ever. 🤦♂️ Time to rewrite that story. Neutralize threats before they materialize. The wait ends November 2025. #ITSecurity #Cybersecurity #ProactiveIT

After 25+ years in IT and cybersecurity, the #1 lesson I've learned is that most breaches happen because of overlooking some basic best practices. Most threats are not that advanced. bit.ly/4gsDDyW #CyberSecurity #InfoSec #ITSecurity #DataProtection#BusinessSecurity

Is your IT ready for the Windows's security requirements? Microsoft’s NTLM deprecation is happening now, soon to be blocked by default. ➡️ Kerberos is now mandatory for Windows monitoring. Read more: adremsoft.com/blog/view/blog… #ITSecurity #InfoSec #Kerberos #ITManagement #SecureIT

🔗 tinyurl.com/3pezfmr9 “Identity is the thing attackers ride once they’re in.” Google Cloud Threat Horizons H2 2025 flags prolonged access, supply-chain exposure, and identity misuse in GCP environments. #cybersecurity #itsecurity #infosec

⏰ Deadline extended Network and Security Engineer: 📍Paris, France 📅 Application deadline: 6 October 2025 at 23:59 (Paris time) 🖱️ ow.ly/giLH50X5vpH #ITSecurity #Vacancy #Hiring #NetworkSecurity #OECDCareers



🚨 Local Gov't Under Siege: DDoS attacks are crippling essential public services worldwide. Public sector IT leaders: Are your defenses ready? Read our guide to protecting local government ⬇️ bit.ly/4nUrYvR #LocalGovernment #DDoS #ITSecurity

buff.ly/qYKbLBM Preparing for disasters and recovering from them can be daunting. Many organizations are at risk of IT emergencies or catastrophes. Global events can heighten business owners' concerns about their susceptibility to crises. #DisasterRecovery #ITSecurity

Recent research found that one in three organizations were hit with fines large enough to impact their financial health, while businesses continue to pay ransoms. We look at the need to maintain cyber readiness: hubs.la/Q03Q9wMD0 #CyberInsurance #ITSecurity #CyberAttack

You’ve probably lost sight of your network – here’s why - buff.ly/ddHDScy #security #cloud #ITsecurity #IT #hybridcloud #multicloud #cloudsecurity

Ein #Hackerangriff betrifft nicht nur die IT – er betrifft das ganze Unternehmen. Gerade in der #Geschäftsführung zählt jede Entscheidung. Wer vorbereitet ist, kontrolliert die Krise & begrenzt den Schaden. 👇 hansesecure.de/termin #Itsecurity #Cybersec #Krisenmanagement




You’ve probably lost sight of your network – here’s why - buff.ly/ddHDScy #security #cloud #ITsecurity #IT #hybridcloud #multicloud #cloudsecurity

Zu viel #Cyber, zu wenig #Security! Echte Expertise erkennst du z.B. an: ✔️ CVEs & Tools ✔️ Technischen Fachbeiträgen ✔️ Community-Präsenz ✔️ Konferenz-Speaks Den ganzen Beitrag lesen: hansesecure.de/blog #ITSecurity #HanseSecure #Youwillbehacked #Cybersecurity #pentest

Something went wrong.
Something went wrong.
United States Trends
- 1. Blue Origin 7,907 posts
- 2. Megyn Kelly 30.3K posts
- 3. New Glenn 8,908 posts
- 4. Vine 33.9K posts
- 5. Senator Fetterman 18.6K posts
- 6. CarPlay 4,384 posts
- 7. Brainiac 5,624 posts
- 8. #NXXT_JPMorgan N/A
- 9. World Cup 101K posts
- 10. Portugal 62.7K posts
- 11. Matt Gaetz 14.2K posts
- 12. GeForce Season 1,057 posts
- 13. Padres 28.7K posts
- 14. Eric Swalwell 26K posts
- 15. Man of Tomorrow 6,154 posts
- 16. Black Mirror 5,217 posts
- 17. Katie Couric 9,764 posts
- 18. Grade 1 26.3K posts
- 19. Osimhen 101K posts
- 20. Apple TV 8,512 posts


























![rss_itsecurity's profile picture. [Languages: En/Fr] It's a Twitter page to tweet some interesting RSS feeds about IT Security News. Follow me @amindeed](https://pbs.twimg.com/profile_images/1310235663/rss.png)



















































