#learntohack نتائج البحث
So you got laid off from a tech company? No worries! #LearnToHack Not so you can get a well paying job in #infosec. Do it so you can get the sweet revenge you deserve. Sweet. Revenge.

There is a lot of industry language in Ethical Hacking and Cybersecurity! Our latest graphic breaks down some key phrases to help you understand the essentials. Dive in and decode the language of cybersecurity! 🔐 #EthicalHacking #CyberSecurity #LearnToHack #Hacking #TechJargon…




When notepad.exe goes from 'just taking notes' to 'taking control' 😳💻🔥 #EthicalHacking #CyberSecurity #LearnToHack

When you think being small makes you invisible to hackers. #EthicalHacking #CyberSecurity #LearnToHack #Hacking

When Chrome is the villain, but Phone Link is the final boss. 💾 #EthicalHacking #CyberSecurity #LearnToHack #Hacking

Me vibing with the hotel WiFi... until I see that 172.16 IP. Oh, we LAN now? 😅💻 #EthicalHacking #CyberSecurity #LearnToHack #Hacking #TechTips #CyberAwareness #HackerLife #CyberEssentials #SecurityTips #OnlineSafety #LearnCyberSecurity

Fun Fact: Did you know you can use Nmap for subdomain enumeration? 💡 Not the best subdomain enum tool by any means, but a solid intro for beginners to learn Nmap scripting! #hacking101 #hackingtips #learntohack

When security goes from protecting users to gaslighting them 😂 #EthicalHacking #CyberSecurity #LearnToHack #Hacking

Unlocking the Digital Realm: Beginner's Guide to Hacking 🔓💻 #Cybersecurity101 #HackersUnite #LearnToHack #TechTrends #DigitalSkills #EthicalHacking #CyberSecurityAwareness #InfoSec #TechForGood #ExploreTech #OnlineSecurity #HackingForBeginners #MindMajix




How to directory brute force with specific file extensions using gobuster! 👇 #gobuster #learntohack #pentesting
The Lesson: This is a critical reminder for all developers! ⚠️ NEVER trust user input. Especially don't pass it directly into a system shell. Always sanitize and validate your inputs to prevent command injection. Follow for more @maesttros #BugBounty #LearnToHack #DailyHacking
Thanks for your time, stay updated for more interesting threads on cybersecurity ethical hacking ✌️ #Cybersecurity #EthicalHacking #LearnToHack
Want to become an ethical hacker? Here’s your step-by-step roadmap 🧑💻 🎯 Skills 🎓 Certifications 🛠️ Tools 🔒 Legal practice Ethical hacking = securing the future. #EthicalHacking #CyberSecurity #LearnToHack #Plutosec
🚀Want a future-proof IT career? ✍️Register now: tr.ee/Orp2AP Step into Cyber Security & Ethical Hacking with us! 💡 CTF Challenges | SOC Analysis | Real Tools 📅Starts 31st July | 🕗8:00 AM IST #CyberDefense #LearnToHack #SecurityExperts #HackerSkills #NareshIT

Started learning AI + Cybersecurity like a kid. Day 1: Printed “Hello World”. Day 30: Predicting fraud and hacking login forms with Hydra. Let’s get smarter, not older. #CyberKid #AIvibes #LearnToHack Made with @vibesdotfun

So you got laid off from a tech company? No worries! #LearnToHack Not so you can get a well paying job in #infosec. Do it so you can get the sweet revenge you deserve. Sweet. Revenge.

When you think being small makes you invisible to hackers. #EthicalHacking #CyberSecurity #LearnToHack #Hacking

Windows has finally embraced its true calling in 2024 😂💻 #EthicalHacking #CyberSecurity #LearnToHack

When notepad.exe goes from 'just taking notes' to 'taking control' 😳💻🔥 #EthicalHacking #CyberSecurity #LearnToHack

When Chrome is the villain, but Phone Link is the final boss. 💾 #EthicalHacking #CyberSecurity #LearnToHack #Hacking

Me vibing with the hotel WiFi... until I see that 172.16 IP. Oh, we LAN now? 😅💻 #EthicalHacking #CyberSecurity #LearnToHack #Hacking #TechTips #CyberAwareness #HackerLife #CyberEssentials #SecurityTips #OnlineSafety #LearnCyberSecurity

Unlocking the Digital Realm: Beginner's Guide to Hacking 🔓💻 #Cybersecurity101 #HackersUnite #LearnToHack #TechTrends #DigitalSkills #EthicalHacking #CyberSecurityAwareness #InfoSec #TechForGood #ExploreTech #OnlineSecurity #HackingForBeginners #MindMajix




There is a lot of industry language in Ethical Hacking and Cybersecurity! Our latest graphic breaks down some key phrases to help you understand the essentials. Dive in and decode the language of cybersecurity! 🔐 #EthicalHacking #CyberSecurity #LearnToHack #Hacking #TechJargon…




When security goes from protecting users to gaslighting them 😂 #EthicalHacking #CyberSecurity #LearnToHack #Hacking

Rickrolling: The unintentional pioneer of clickbait awareness and digital trust issues. #EthicalHacking #CyberSecurity #LearnToHack #Hacking

Fun Fact: Did you know you can use Nmap for subdomain enumeration? 💡 Not the best subdomain enum tool by any means, but a solid intro for beginners to learn Nmap scripting! #hacking101 #hackingtips #learntohack

Can you answer the following question? Let us know the answer in the comments along with a valid explanation. 🚀 Check out the ethical hacking course here: shorturl.at/apyAJ #ethicalhacking #infosec #learntohack #onlinetraining #techskills

Need to check the time or date in the terminal? ⌚️ Use the date command to tell you: ✅ Day of the week ✅ Current Date ✅ Current Time ✅ Timezone 📆 Use the cal command to display the calendar for the month! #bash101 #learntocode #learntohack

In our latest post, learn how direct system calls can be used to bypass API Hooking techniques used by modern EDRs/AVs to block malicious in-memory attacks. Find the post on zSecurity: zsecurity.org/bypass-edr-api… #EthicalHacking #CyberSecurity #LearnToHack #Hacking

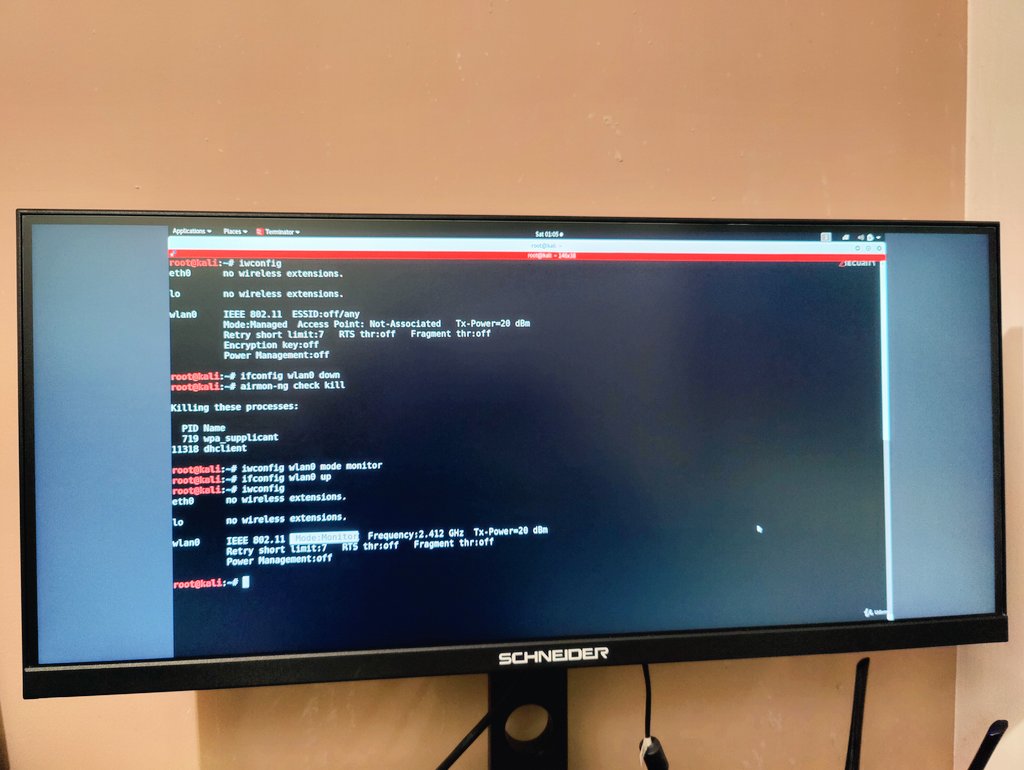
Day 10 of my hacking journey: Exploring Wi-Fi vulnerabilities & pre-connection attacks. Time to dive deeper into how networks can be compromised before you even connect. Stay tuned! #EthicalHacking #WiFiHacking #LearnToHack #CyberSecurity #PenTesting
Something went wrong.
Something went wrong.
United States Trends
- 1. Black Friday 386K posts
- 2. Mississippi State 2,704 posts
- 3. Kamario Taylor N/A
- 4. Egg Bowl 4,288 posts
- 5. Emmett Johnson N/A
- 6. #SkylineSweeps N/A
- 7. NextNRG Inc 1,790 posts
- 8. Trinidad Chambliss N/A
- 9. Wetjen N/A
- 10. #Rashmer 23.7K posts
- 11. Stricklin N/A
- 12. #FanCashDropPromotion 1,736 posts
- 13. Solo Ball N/A
- 14. Kewan Lacy N/A
- 15. #Huskers N/A
- 16. #jonita 19.8K posts
- 17. Black Ops 7 XP 1,486 posts
- 18. Fisch 1,006 posts
- 19. WHO DEY 12.2K posts
- 20. Mainz Biomed N.V. N/A