#netsec 검색 결과
AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec
#NetSec #Research "Decoy Databases: Analyzing Attacks on Public Facing Databases", Oct. 2025. ]-> a detailed mapping of the log files, configurations, and honeypots github.com/YuqianSong6/da… // Our findings highlight that DBMS-targeted attacks are distinct from those on other…
Silence in the network is louder than noise. Keeping watch. 👁️🗨️ #CyberSecurity #NetSec #AlwaysLearning

🔎 CSO focused on the GitHub Actions angle. LinuxSecurity dives into how these malicious packages persist quietly. That is the risk operators must watch. #netsec #cybersec #appsec bit.ly/3X3Z8NQ

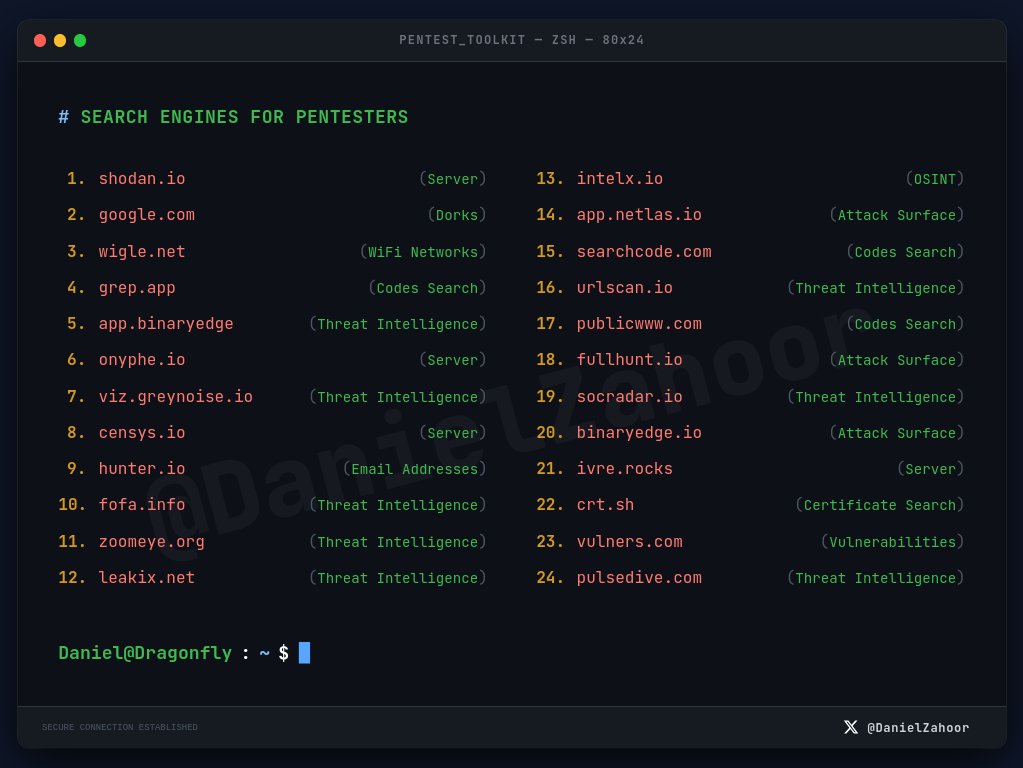
Someone's quick and basic recon routine for finding Subdomains while doing Bug Bounty😁✌️ . . #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec #CTF #OWASP #hacking #cybersecurity #infosec #ethicalhacking #recon

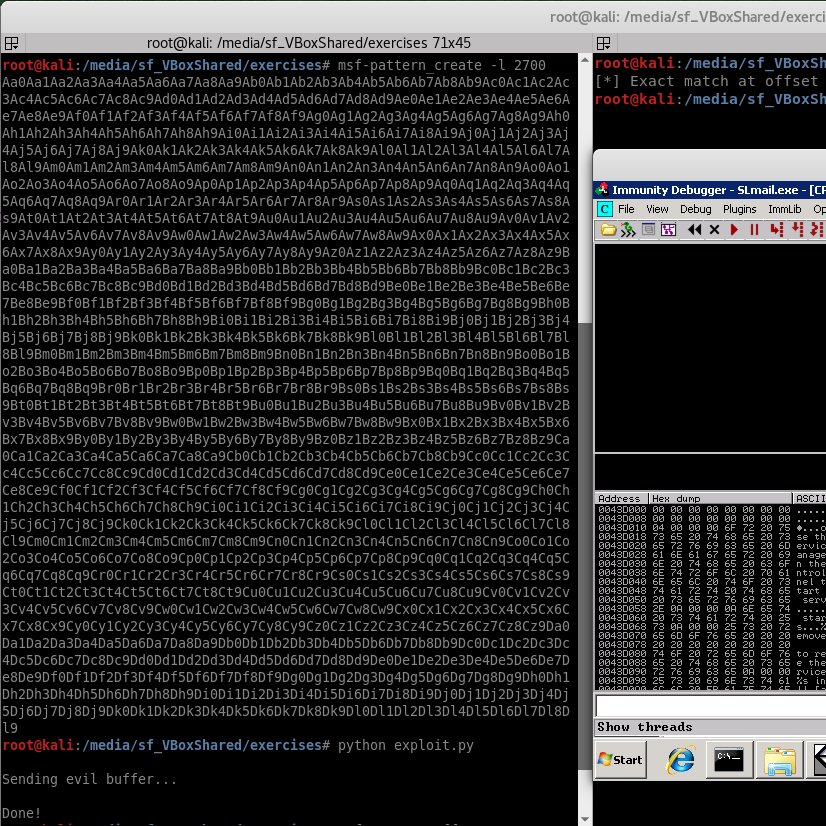
If you are thinking of a good port scanner that is simple and fast, you could check out https://github\.com/nullt3r/jfscan I have tested it and it's pretty accurate. Of course, nothing can replace OG Nmap entirely. #networksec #netsec #infosecurity

#NetSec #Research "Generalized Encrypted Traffic Classification Using Inter-Flow Signals", ARES 2025. ]-> MAppGraph - Encrypted Network Traffic Classification using Deep Learning - github.com/soeai/mappgraph // In this paper, we present a novel encrypted traffic classification…
sn1persecurity.com/wordpress/inte… Centralize your security data with one easy to use interface. Aggregate, analyze and report on all of the leading tools in a single system so you can stay ahead! External Attack Surface Management #infosec #bugbounty #netsec #offsec #pentest

#NetSec #Malware_analysis 1⃣ LinkPro: eBPF rootkit analysis synacktiv.com/en/publication… // LinkPro is a stealthy Linux rootkit utilizing eBPF and user-space techniques for covert process/file hiding, persistent C2, and targeted attacks on AWS for financial gain 2⃣ Defrosting…
Using @openziti or zrok and want to have your voice heard? NetFoundry is looking to hear from you to help drive the roadmap for open source and product features. Talk to @smilindave26, co-founder and CTO! openziti.discourse.group/t/seeking-open… #zerotrust #appsec #netsec #userinput
Detect network threats sooner: deep learning for traffic anomaly detection - architectures; features; evaluation - full study: glcnd.io/deep-learning-… #NetSec #AI #Anomaly
Tufin is excited to be at #CPX2024! As a Check Point partner for over 30 years, we know how to automate and improve visibility across your Hybrid, #NetSec, and Cloud environments. Stop by Tufin booth #3 to meet with the team and enter for a chance to win an Avengers Tower Lego!

Join the growing number of #netsec & distributed system security workshops that have co-located with #NDSSsymposium. Submit a proposal by 1 August for next year's event ndss-symposium.org/ndss2025/submi…




Misconfigurations are open invitations to bad actors. Fixing them should be part of your operational rhythm — not an annual clean-up. Discover why cyber hygiene is a critical endeavor: eu1.hubs.ly/H0ks_m50 #Cybersecurity #riskmanagement #netsec
🔍 CSO Online covered the npm typo that slipped into GitHub Actions. What the piece missed is how these attacks ride on weak validation and old credentials. LinuxSecurity lays out the protection angle clearly. #linuxsec #cybersec #netsec bit.ly/3X3Z8NQ

This is what's coming, bof-launcher will become Open Adversary Simulation Kit. Ultimate flexibility and modularity, every piece of the system is a BOF which can be independently replaced. Cross-platform. With memory masking. #netsec #CyberSecurity #offensivesecurity #ziglang

Week in review: WSUS vulnerability exploited to drop Skuld infostealer, PoC for BIND 9 DNS flaw published - helpnetsecurity.com/2025/11/02/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

#exploit #NetSec 1. GPOs manipulation and exploitation framework github.com/synacktiv/Grou… // GroupPolicyBackdoor - Python tool for stealthy manipulation of Active Directory GPOs to enable privilege escalation, featuring creation, modification, and removal functions, with safety…
🚨 CVE-2025-34027: Versa Concerto Authentication By... Traefik misconfiguration in Versa Concerto creates perfect storm: auth bypass + TOCTOU race condition = unauthenticated... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-34027 - Security Alert
The Versa Concerto SD-WAN orchestration platform is vulnerable to an authentication bypass in the Traefik reverse proxy configuration, allowing at att...
🚨 CVE-2025-34026: Versa Concerto Actuator Authenti... Traefik misconfiguration in Versa Concerto exposes Actuator endpoints, enabling unauthenticated heap dumps and trace ex... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-34026 - Security Alert
The Versa Concerto SD-WAN orchestration platform is vulnerable to an authentication bypass in the Traefik reverse proxy configuration, allowing at att...
🚨 CVE-2022-50589: SuiteCRM < 7.12.6 SQL Injection ... Unauthenticated SQL injection in SuiteCRM's export 'uid' parameter offers direct path to RCE - patch immediately or dis... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2022-50589 - Security Alert
SuiteCRM versions prior to 7.12.6 contain a SQL injection vulnerability within the processing of the ‘uid’ parameter within the ‘export’ functionality...
🚨 CVE-2025-34111: Tiki Wiki <= 15.1 ELFinder Unaut... ELFinder's connector.minimal.php in Tiki Wiki <=15.1 exposes a trivial unauthenticated RCE—zero auth checks, zero file ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-34111 - Security Alert
An unauthenticated arbitrary file upload vulnerability exists in Tiki Wiki CMS Groupware version 15.1 and earlier via the ELFinder component's default...
#NetSec #Research "Decoy Databases: Analyzing Attacks on Public Facing Databases", Oct. 2025. ]-> a detailed mapping of the log files, configurations, and honeypots github.com/YuqianSong6/da… // Our findings highlight that DBMS-targeted attacks are distinct from those on other…
Go beyond Attack Surface Management (ASM) with our all-in-one offensive security platform 👉 sn1persecurity.com/wordpress/ External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec #pentest #infosecurity
🚨 CVE-2025-30004: Xorcom CompletePBX <= 5.2.35 Tas... Root-level command injection via Task Scheduler gives attackers complete system control despite requiring admin creds -... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-30004 - Security Alert
Xorcom CompletePBX is vulnerable to command injection in the administrator Task Scheduler functionality, allowing for attackers to execute arbitrary c...
AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec

🔎 CSO focused on the GitHub Actions angle. LinuxSecurity dives into how these malicious packages persist quietly. That is the risk operators must watch. #netsec #cybersec #appsec bit.ly/3X3Z8NQ

🚨 CVE-2025-66385: cerebrate-project (CVSS: 9.4)... Trivial privilege escalation in Cerebrate <1.30 lets authenticated users become admin by modifying role_id/organisation... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-66385 - Security Alert
UsersController::edit in Cerebrate before 1.30 allows an authenticated non-privileged user to escalate their privileges (e.g., obtain a higher role su...
🚨 CVE-2025-64314: Huawei (CVSS: 9.3)... Memory permission flaw in HarmonyOS 5.1.0 gives unprivileged local attackers complete system access - classic type conf... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-64314 - Security Alert
Permission control vulnerability in the memory management module. Impact: Successful exploitation of this vulnerability may affect confidentiality....
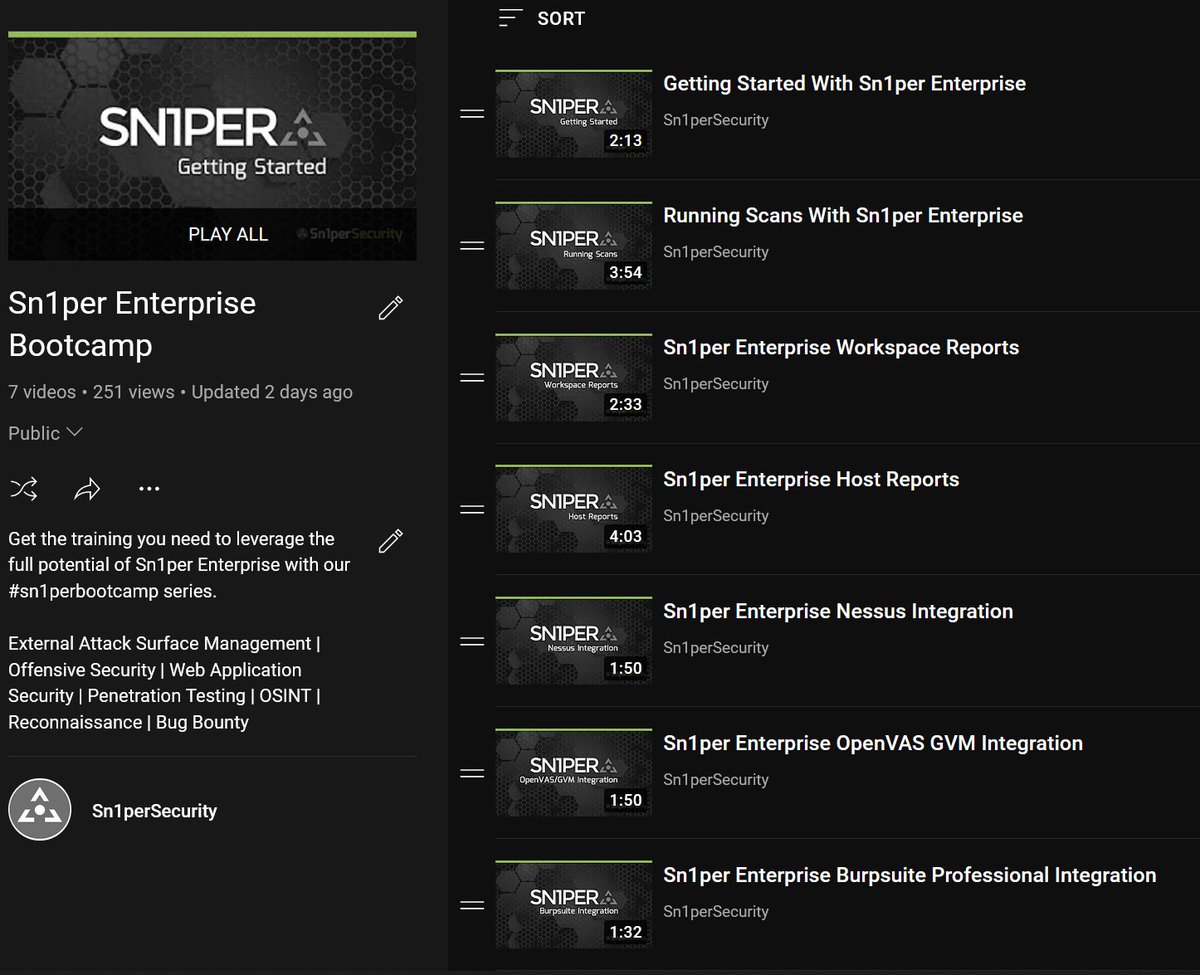
Looking for an in-depth demo of Sn1per Enterprise? Check our YouTube channel where we walk through all the key features and benefits! 👉youtube.com/watch?v=-mSH2w… External Attack Surface Management #infosec #bugbounty #netsec #offsec #pentest #cybersecurity #infosecurity

youtube.com
YouTube
Getting Started With Sn1per Enterprise
🚨 CVE-2025-12421: Account Takeover via Code Exchan... Missing token origin verification in Mattermost's code exchange enables trivial account takeovers when auth transfers a... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-12421 - Security Alert
Mattermost versions 11.0.x <= 11.0.2, 10.12.x <= 10.12.1, 10.11.x <= 10.11.4, 10.5.x <= 10.5.12 fail to to verify that the token used during the code ...
Silence in the network is louder than noise. Keeping watch. 👁️🗨️ #CyberSecurity #NetSec #AlwaysLearning

AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec

Someone's quick and basic recon routine for finding Subdomains while doing Bug Bounty😁✌️ . . #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec #CTF #OWASP #hacking #cybersecurity #infosec #ethicalhacking #recon

🩻The enigmatic figure of #USDoD (formerly #NetSec on #RaidForums) stands as a testament to the evolving landscape of #cybersecurity, representing the new age of #hackers. The #threatactor has returned, aiming to revitalize #BreachForums. Read more👇 socradar.io/unmasking-usdo…

#Telegram CEO caves to Israeli and U.S. pressure. Will now provide user IP addresses to governments upon request. #NetSec #CyberSec » @ZirafaMedia



unfurl is awesome 🚀 Pull bits out of URLs including domains, TLDs, paths, apexes and so much more! Definitely worth checking out. Another great tool from @tomnomnom 😎 #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec

If you are thinking of a good port scanner that is simple and fast, you could check out https://github\.com/nullt3r/jfscan I have tested it and it's pretty accurate. Of course, nothing can replace OG Nmap entirely. #networksec #netsec #infosecurity

Yup. Our students have been busy. #netsec

Spent most of today preparing the NOC talk for the last class of our Introduction to Security class tomorrow. This is the class were we show students all the behind the scene of the class: network, infrastructure, technologies used, and some highlights on our network monitoring.
Getting RCE and arbitrary file disclosure with Ghostscript & PostScript + Bypasses (CVE-2023-36664 and CVE-2023-43115) blog.redteam-pentesting.de/2023/ghostscri… #bugbountytips #appsec #netsec #infosec #cybersecurity #vulnerability #bugbounty


Our Trusted Internet Connections (TIC) program released a final version of TIC 3.0 Cloud Use Case for federal agencies operating in a cloud environment. For more info on the new guide along with updates to other TIC resources, visit: go.dhs.gov/4xP #TIC #NetSec #InfoSec

OpenDoor – OWASP WEB Directory Scanner skynettools.com/opendoor-owasp… #infosec #netsec #pentest #cybersecurity #bugbounty

Smart File Hunter – Identify Files That Contain Sensitive Information Like Passwords & Private Keys skynettools.com/smart-file-hun… #infosec #netsec #pentest #cybersecurity #bugbounty

EasyPark has had a cyber attack resulting in a breach of non-sensitive customer data: Names, phone numbers, physical addresses, email addresses and some digits from credit/debit cards or IBAN. Read EasyPark's official statement here: easypark.com/en-de/comm #CyberSec #netsec

In WHAT alternate universe does it make sense to plug in your SIN# to a website? Sure as hell not in this one. What's scarier yet - this is a LEGIT email from a supplier I do business with. #netsec

📢Call for #NDSSsyposium2025 co-located workshops is now open! ndss-symposium.org/ndss2025/submi… #netsec

My latest work has been published: "CTU Hornet 65 Niner: A network dataset of geographically distributed low-interaction honeypots" The dataset has a unique value for studying the nature of Internet attacks over time. sciencedirect.com/science/articl… #honeypots #netsec #deception

Week in review: WSUS vulnerability exploited to drop Skuld infostealer, PoC for BIND 9 DNS flaw published - helpnetsecurity.com/2025/11/02/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

Something went wrong.
Something went wrong.
United States Trends
- 1. Black Friday 459K posts
- 2. Bears 51.8K posts
- 3. Nebraska 11.7K posts
- 4. Swift 54.6K posts
- 5. Sydney Brown 1,010 posts
- 6. Iowa 13K posts
- 7. Lane Kiffin 9,223 posts
- 8. Rhule 2,661 posts
- 9. Jalon Daniels N/A
- 10. Black Ops 7 Blueprint 11K posts
- 11. Ben Johnson 2,644 posts
- 12. Sumrall 3,503 posts
- 13. #SoleRetriever N/A
- 14. Go Birds 11.5K posts
- 15. Egg Bowl 8,031 posts
- 16. Kansas 15.8K posts
- 17. #CHIvsPHI 1,033 posts
- 18. #Huskers 1,305 posts
- 19. #kufball 1,003 posts
- 20. Mississippi State 5,355 posts