#netsec результаты поиска
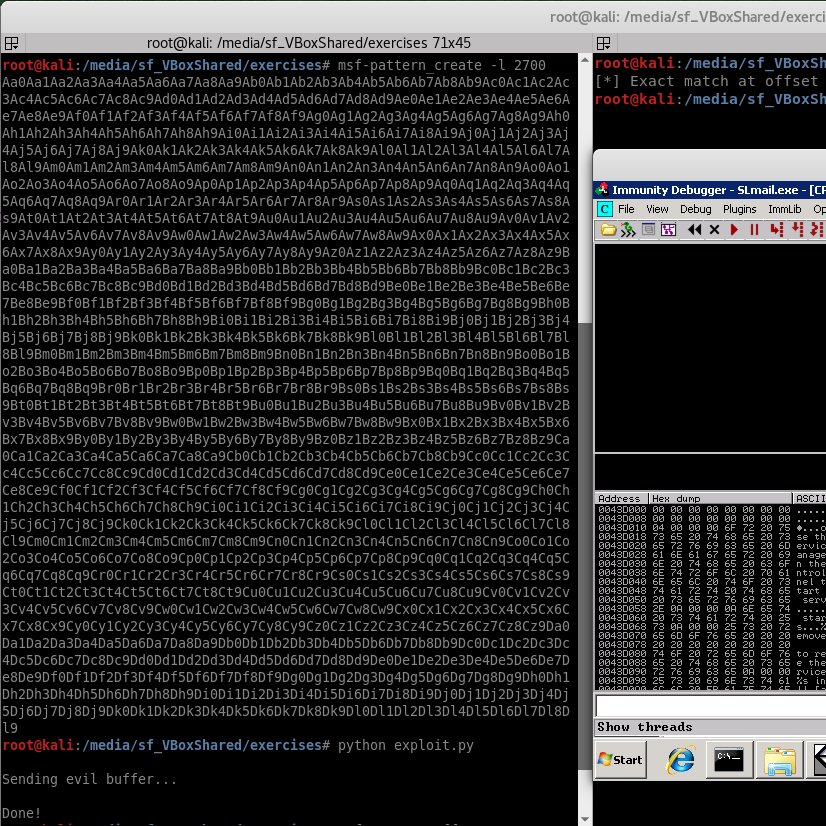
Silence in the network is louder than noise. Keeping watch. 👁️🗨️ #CyberSecurity #NetSec #AlwaysLearning

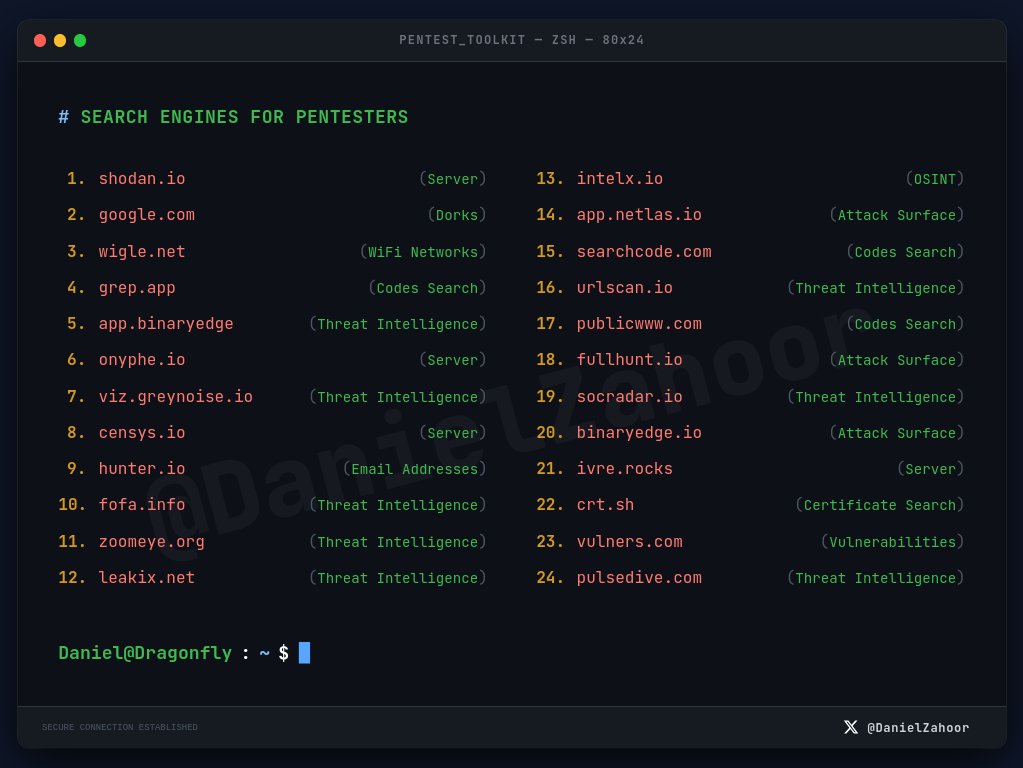
Someone's quick and basic recon routine for finding Subdomains while doing Bug Bounty😁✌️ . . #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec #CTF #OWASP #hacking #cybersecurity #infosec #ethicalhacking #recon

AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec
🧭 The CSO story covered what happened. LinuxSecurity covers why it keeps happening. Registry weaknesses are the real problem to fix. #opensrc #netsec #linuxsec bit.ly/3X3Z8NQ

If you are thinking of a good port scanner that is simple and fast, you could check out https://github\.com/nullt3r/jfscan I have tested it and it's pretty accurate. Of course, nothing can replace OG Nmap entirely. #networksec #netsec #infosecurity

#NetSec #Malware_analysis 1⃣ LinkPro: eBPF rootkit analysis synacktiv.com/en/publication… // LinkPro is a stealthy Linux rootkit utilizing eBPF and user-space techniques for covert process/file hiding, persistent C2, and targeted attacks on AWS for financial gain 2⃣ Defrosting…
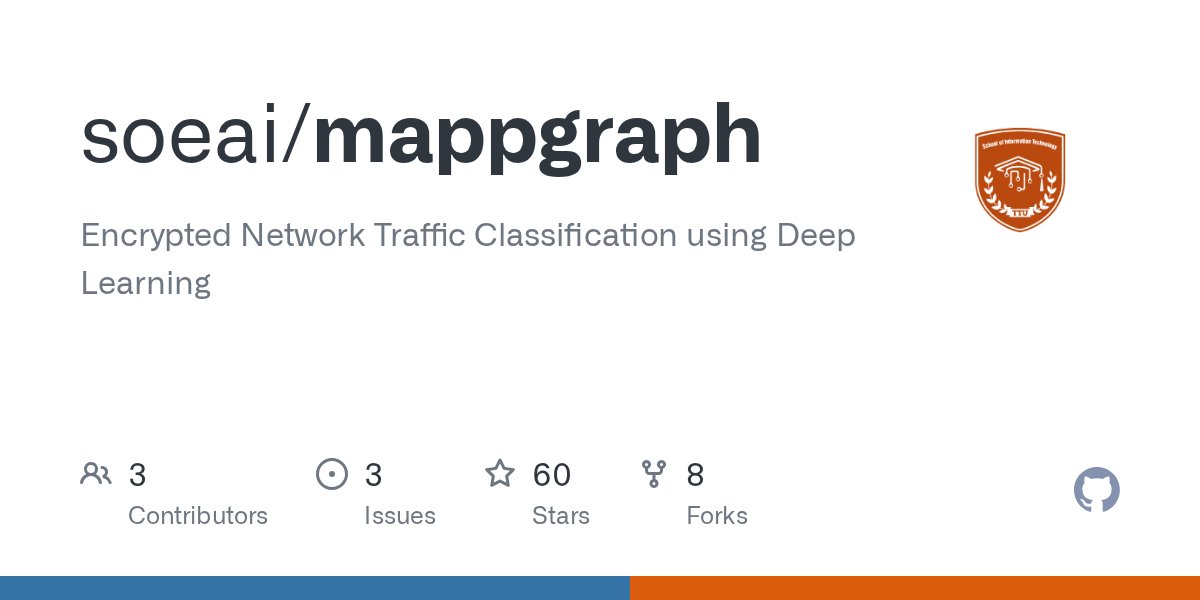
#NetSec #Research "Generalized Encrypted Traffic Classification Using Inter-Flow Signals", ARES 2025. ]-> MAppGraph - Encrypted Network Traffic Classification using Deep Learning - github.com/soeai/mappgraph // In this paper, we present a novel encrypted traffic classification…
🔍 CSO Online covered the npm typo that slipped into GitHub Actions. What the piece missed is how these attacks ride on weak validation and old credentials. LinuxSecurity lays out the protection angle clearly. #linuxsec #cybersec #netsec bit.ly/3X3Z8NQ

Week in review: WSUS vulnerability exploited to drop Skuld infostealer, PoC for BIND 9 DNS flaw published - helpnetsecurity.com/2025/11/02/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

Join the growing number of #netsec & distributed system security workshops that have co-located with #NDSSsymposium. Submit a proposal by 1 August for next year's event ndss-symposium.org/ndss2025/submi…




Find #netsec inspiration and save money this New Year Register for #NDSSsymposium2025 by 17 January to save up to USD 200 🐤 Student rates are also available. ndss-symposium.org/ndss2025/atten…

AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec
📢Call for #NDSSsyposium2025 co-located workshops is now open! ndss-symposium.org/ndss2025/submi… #netsec

GET THE ULTIMATE PENTEST TOOLKIT Visit our website to see how Sn1per can help your security team! sn1persecurity.com/wordpress/?ult… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec #OSINT #recon #CTF
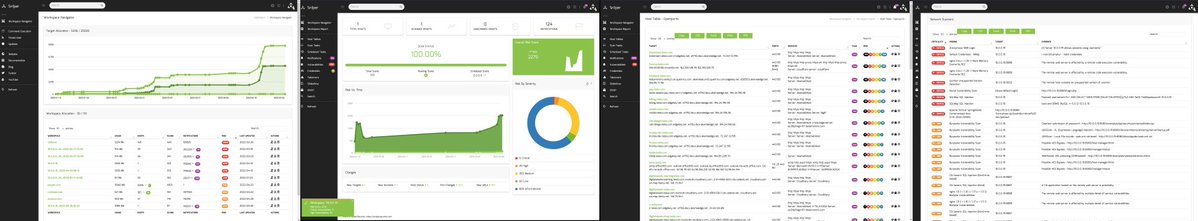
sn1persecurity.com/wordpress/inte… Centralize your security data with one easy to use interface. Aggregate, analyze and report on all of the leading tools in a single system so you can stay ahead! External Attack Surface Management #infosec #bugbounty #netsec #offsec #pentest
Tufin is excited to be at #CPX2024! As a Check Point partner for over 30 years, we know how to automate and improve visibility across your Hybrid, #NetSec, and Cloud environments. Stop by Tufin booth #3 to meet with the team and enter for a chance to win an Avengers Tower Lego!

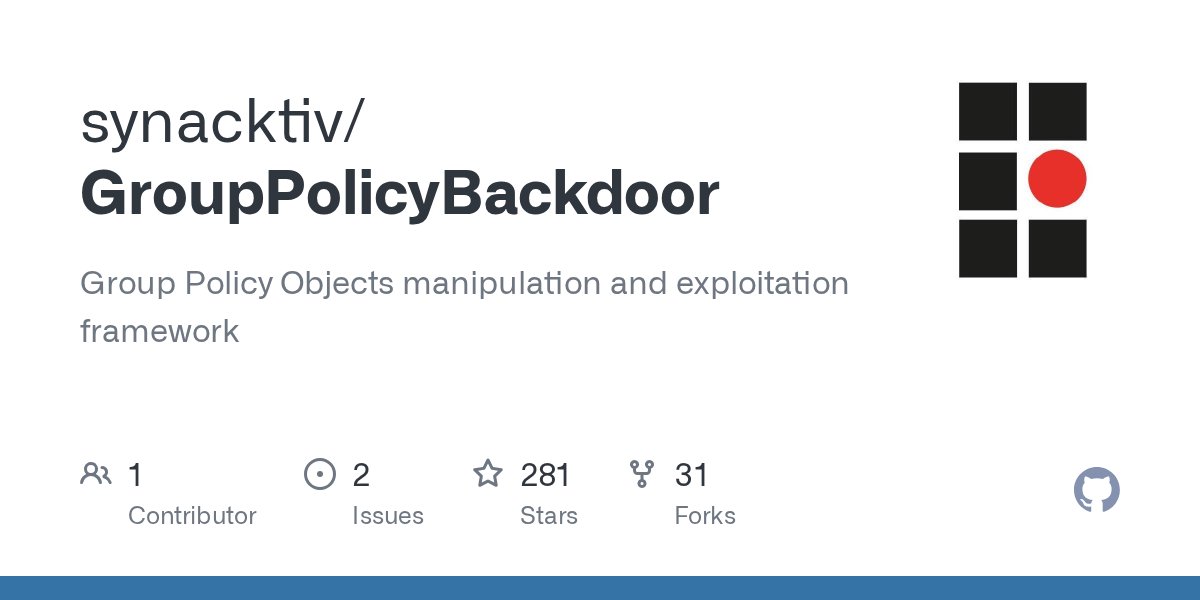
#exploit #NetSec 1. GPOs manipulation and exploitation framework github.com/synacktiv/Grou… // GroupPolicyBackdoor - Python tool for stealthy manipulation of Active Directory GPOs to enable privilege escalation, featuring creation, modification, and removal functions, with safety…
Misconfigurations are open invitations to bad actors. Fixing them should be part of your operational rhythm — not an annual clean-up. Discover why cyber hygiene is a critical endeavor: eu1.hubs.ly/H0ks_m50 #Cybersecurity #riskmanagement #netsec
🚨 CVE-2025-13486: Advanced Custom Fields: Extended... Unauthenticated RCE in ACF:Extended via call_user_func_array() abuse gives attackers server-level code execution withou... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13486 - Security Alert
The Advanced Custom Fields: Extended plugin for WordPress is vulnerable to Remote Code Execution in versions 0.9.0.5 through 0.9.1.1 via the prepare_f...
AUTOMATE THE MOST POWERFUL SECURITY TOOLS Check our YouTube channel to see how Sn1per can help your security team! youtube.com/c/Sn1perSecuri… External Attack Surface Management | Offensive Security | Penetration Testing | OSINT | Bug Bounty #infosec #bugbounty #netsec #offsec

🚨 CVE-2025-13658: Industrial Video & Control Longw... Longwatch ICS devices expose an unauthenticated HTTP endpoint granting SYSTEM-level code execution—perfect for initial ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13658 - Security Alert
A vulnerability in Longwatch devices allows unauthenticated HTTP GET requests to execute arbitrary code via an exposed endpoint, due to the absence of...
🚨 CVE-2025-13510: Iskra iHUB and iHUB Lite has a M... Iskra's smart metering gateways expose admin panel with zero auth - trivial network pivoting into critical infrastructu... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13510 - Security Alert
The Iskra iHUB and iHUB Lite smart metering gateway exposes its web management interface without requiring authentication, allowing unauthenticated us...
🚨 CVE-2025-13542: DesignThemes LMS <= 1.0.4 - Unau... Trivial privilege escalation in DesignThemes LMS allows registration with arbitrary roles - supply "administrator" in P... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13542 - Security Alert
The DesignThemes LMS plugin for WordPress is vulnerable to Privilege Escalation in all versions up to, and including, 1.0.4. This is due to the 'dtlms...
🚨 CVE-2025-13828: Mautic user without privileged a... Low-priv Mautic users can bypass composer restrictions to inject malicious packages, enabling full privilege escalation... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-13828 - Security Alert
SummaryA non privileged user can install and remove arbitrary packages via composer for a composer based installed, even if the flag in update setting...
🚨 CVE-2025-11778: Stack-based buffer overflow vuln... Stack overflow in Circutor PLC TACACSPLUS implementation grants remote code execution with zero authentication—perfect ... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-11778 - Security Alert
Stack-based buffer overflow in Circutor SGE-PLC1000/SGE-PLC50 v0.9.2. This vulnerability allows an attacker to remotely exploit memory corruption thro...
🚨 CVE-2025-11779: Stack-based buffer overflow vuln... Stack overflow in Circutor PLC's 'SetLan' function allows command injection through unsanitized web parameters - trivia... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-11779 - Security Alert
Stack-based buffer overflow vulnerability in CircutorSGE-PLC1000/SGE-PLC50 v9.0.2. The 'SetLan' function is invoked when a new configuration is applie...
🧭 The CSO story covered what happened. LinuxSecurity covers why it keeps happening. Registry weaknesses are the real problem to fix. #opensrc #netsec #linuxsec bit.ly/3X3Z8NQ

If you haven't done a User Access Audit in 30 days, you likely have an open door for a breach. ➡️Don't wait for an incident to check your list. Grab our 7-Day Image Planner to stay ahead of the threats.👇 #NetSec #SysAdminLife #CyberSecurity #EncryViaInsights
🚀 Exciting News! Sn1per Scan Engine v10.5 has just been released! 🎉 Discover the latest updates and enhancements in this powerful security tool. Check out the details here: sn1persecurity.com/wordpress/sn1p… #infosec #bugbounty #netsec #offsec #pentesting #cybersecurity #infosecurity
🚨 CVE-2025-66401: MCP Watch has a Critical Command... Classic case of irony: security scanner executes unsanitized user input via execSync() - weaponize with shell metachara... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-66401 - Security Alert
MCP Watch is a comprehensive security scanner for Model Context Protocol (MCP) servers. In 0.1.2 and earlier, the MCPScanner class contains a critical...
🚨 CVE-2025-63525: n/a (CVSS: 9.6)... Trivial privilege escalation in Blood Bank Management System via delete.php allows authenticated users to execute admin... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-63525 - Security Alert
An issue was discovered in Blood Bank Management System 1.0 allowing authenticated attackers to perform actions with escalated privileges via crafted ...
🚨 CVE-2025-63531: n/a (CVSS: 10.0)... Trivial SQLi in Blood Bank Management 1.0 enables full auth bypass via unfiltered remail/rpassword params - literal blo... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-63531 - Security Alert
A SQL injection vulnerability exists in the Blood Bank Management System 1.0 within the receiverLogin.php component. The application fails to properly...
🚨 CVE-2025-63532: n/a (CVSS: 9.6)... Critical SQL injection in Blood Bank Management System 1.0 enables full auth bypass through unsanitized search input in... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-63532 - Security Alert
A SQL injection vulnerability exists in the Blood Bank Management System 1.0 within the cancel.php component. The application fails to properly saniti...
🚨 CVE-2025-63535: n/a (CVSS: 9.6)... Trivial SQLi in Blood Bank Management System's abs.php search field grants full system access with minimal authenticati... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-63535 - Security Alert
A SQL injection vulnerability exists in the Blood Bank Management System 1.0 within the abs.php component. The application fails to properly sanitize ...
🚨 CVE-2025-3500: Integer Overflow in Avast Antiviu... Integer overflow in Avast's AV engine hands attackers local-to-SYSTEM privilege escalation - patch 25.1.981.6 immediatel... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-3500 - Security Alert
Integer Overflow or Wraparound vulnerability in Avast Antivirus (25.1.981.6) on Windows allows Privilege Escalation.This issue affects Antivirus: from...
Looking for a commercial tool for performing Attack Surface Management? Check our latest blog post to see how Sn1per can help! 👉 sn1persecurity.com/wordpress/exte… External Attack Surface Management #infosec #bugbounty #netsec #offsec #pentest #pentesting #cybersecurity #infosecurity
⚡ CVE-2025-20346: Cisco Catalyst Center Privilege ... Observer-to-Admin privilege jump in Catalyst Center via RBAC bypass lets read-only users modify policy configs - classi... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-20346 - Security Alert
A vulnerability in Cisco Catalyst Center could allow an authenticated, remote attacker to execute operations that should require Administrator privile...
🚨 CVE-2025-8351: Avast (CVSS: 9.0)... MacOS Avast heap overflow lets attackers crash the scanner or pivot to code exec with malformed files - ironic when your... zerodaysignal.com/vulnerability/… #netsec #vulnerability #CVE #sysadmin #zeroday
zerodaysignal.com
CVE-2025-8351 - Security Alert
Heap-based Buffer Overflow, Out-of-bounds Read vulnerability in Avast Antivirus on MacOS when scanning a malformed file may allow Local Execution of C...
Silence in the network is louder than noise. Keeping watch. 👁️🗨️ #CyberSecurity #NetSec #AlwaysLearning

Someone's quick and basic recon routine for finding Subdomains while doing Bug Bounty😁✌️ . . #hackers #netsec #bugbountytip #bugbountytips #bugbounty #infosec #redteam #pentesting #pentest #offsec #CTF #OWASP #hacking #cybersecurity #infosec #ethicalhacking #recon

If you are thinking of a good port scanner that is simple and fast, you could check out https://github\.com/nullt3r/jfscan I have tested it and it's pretty accurate. Of course, nothing can replace OG Nmap entirely. #networksec #netsec #infosecurity

#Telegram CEO caves to Israeli and U.S. pressure. Will now provide user IP addresses to governments upon request. #NetSec #CyberSec » @ZirafaMedia



📢Call for #NDSSsyposium2025 co-located workshops is now open! ndss-symposium.org/ndss2025/submi… #netsec

Yup. Our students have been busy. #netsec

Spent most of today preparing the NOC talk for the last class of our Introduction to Security class tomorrow. This is the class were we show students all the behind the scene of the class: network, infrastructure, technologies used, and some highlights on our network monitoring.
Getting RCE and arbitrary file disclosure with Ghostscript & PostScript + Bypasses (CVE-2023-36664 and CVE-2023-43115) blog.redteam-pentesting.de/2023/ghostscri… #bugbountytips #appsec #netsec #infosec #cybersecurity #vulnerability #bugbounty


Security credibility matters. Barracuda helps MSPs like M.IT Connect deliver trusted, transparent services that customers rely on. Discover how Connect transformed its MSP services. barracuda.com/partners/succe… #BarracudaONEplatform #NetSec

Week in review: WSUS vulnerability exploited to drop Skuld infostealer, PoC for BIND 9 DNS flaw published - helpnetsecurity.com/2025/11/02/wee… - #WeekInReview #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews

OpenDoor – OWASP WEB Directory Scanner skynettools.com/opendoor-owasp… #infosec #netsec #pentest #cybersecurity #bugbounty

Our Trusted Internet Connections (TIC) program released a final version of TIC 3.0 Cloud Use Case for federal agencies operating in a cloud environment. For more info on the new guide along with updates to other TIC resources, visit: go.dhs.gov/4xP #TIC #NetSec #InfoSec

Smart File Hunter – Identify Files That Contain Sensitive Information Like Passwords & Private Keys skynettools.com/smart-file-hun… #infosec #netsec #pentest #cybersecurity #bugbounty

Join the growing number of #netsec & distributed system security workshops that have co-located with #NDSSsymposium. Submit a proposal by 1 August for next year's event ndss-symposium.org/ndss2025/submi…




Tufin is excited to be at #CPX2024! As a Check Point partner for over 30 years, we know how to automate and improve visibility across your Hybrid, #NetSec, and Cloud environments. Stop by Tufin booth #3 to meet with the team and enter for a chance to win an Avengers Tower Lego!

In WHAT alternate universe does it make sense to plug in your SIN# to a website? Sure as hell not in this one. What's scarier yet - this is a LEGIT email from a supplier I do business with. #netsec

🧭 The CSO story covered what happened. LinuxSecurity covers why it keeps happening. Registry weaknesses are the real problem to fix. #opensrc #netsec #linuxsec bit.ly/3X3Z8NQ

Find #netsec inspiration and save money this New Year Register for #NDSSsymposium2025 by 17 January to save up to USD 200 🐤 Student rates are also available. ndss-symposium.org/ndss2025/atten…

🩻The enigmatic figure of #USDoD (formerly #NetSec on #RaidForums) stands as a testament to the evolving landscape of #cybersecurity, representing the new age of #hackers. The #threatactor has returned, aiming to revitalize #BreachForums. Read more👇 socradar.io/unmasking-usdo…

My latest work has been published: "CTU Hornet 65 Niner: A network dataset of geographically distributed low-interaction honeypots" The dataset has a unique value for studying the nature of Internet attacks over time. sciencedirect.com/science/articl… #honeypots #netsec #deception

Something went wrong.
Something went wrong.
United States Trends
- 1. Chris Paul 10.1K posts
- 2. Clippers 18.2K posts
- 3. FELIX LV VISIONARY SEOUL 15.8K posts
- 4. #FELIXxLouisVuitton 18.6K posts
- 5. Pat Spencer 2,748 posts
- 6. jungkook 241K posts
- 7. rUSD N/A
- 8. Good Wednesday 22K posts
- 9. Kerr 5,780 posts
- 10. Podz 3,366 posts
- 11. Lawrence Frank N/A
- 12. Shai 16.2K posts
- 13. Seth Curry 5,209 posts
- 14. Jimmy Butler 2,683 posts
- 15. Hield 1,616 posts
- 16. TOP CALL 9,660 posts
- 17. Carter Hart 4,220 posts
- 18. Brandy 8,522 posts
- 19. Earl Campbell 1,241 posts
- 20. #SeanCombsTheReckoning 5,685 posts