#networkaccess search results
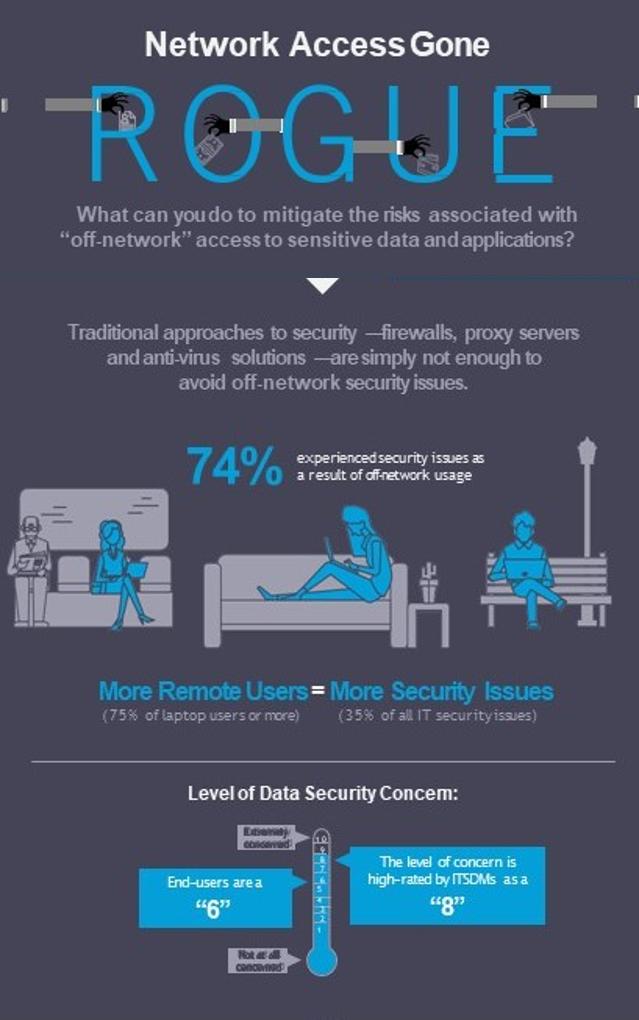
Businesses must do everything possible to minimize the risk of easy network access and data exfiltration. Some startling new trends are covered by Chris Boyd of Rapid7 🔗in the comments We are proud to partner with Rapid7 💯 #ransomware #networkaccess #mfa #patchmanagement
🔌 NANO FACT #98 A network of public RPC nodes allows developers and users to interact with the Nano network without running their own full node. #RPCNodes #DeveloperTools #NetworkAccess #NanoFacts #XNO @nano

How to move from VPN to ZTNA (3 best practices) mig.us/46tMFqn #ZeroTrust #Cybersecurity #networkaccess

Just 3 DAYS remaining to register! Don't miss #OPSWATAcademy's upcoming webinar, “Gatekeepers of the Network: Mastering #NetworkAccessControl Systems.” 🗓️ Discover strategies to secure both local and remote #NetworkAccess! Sign up now! hubs.la/Q02Mvb3c0
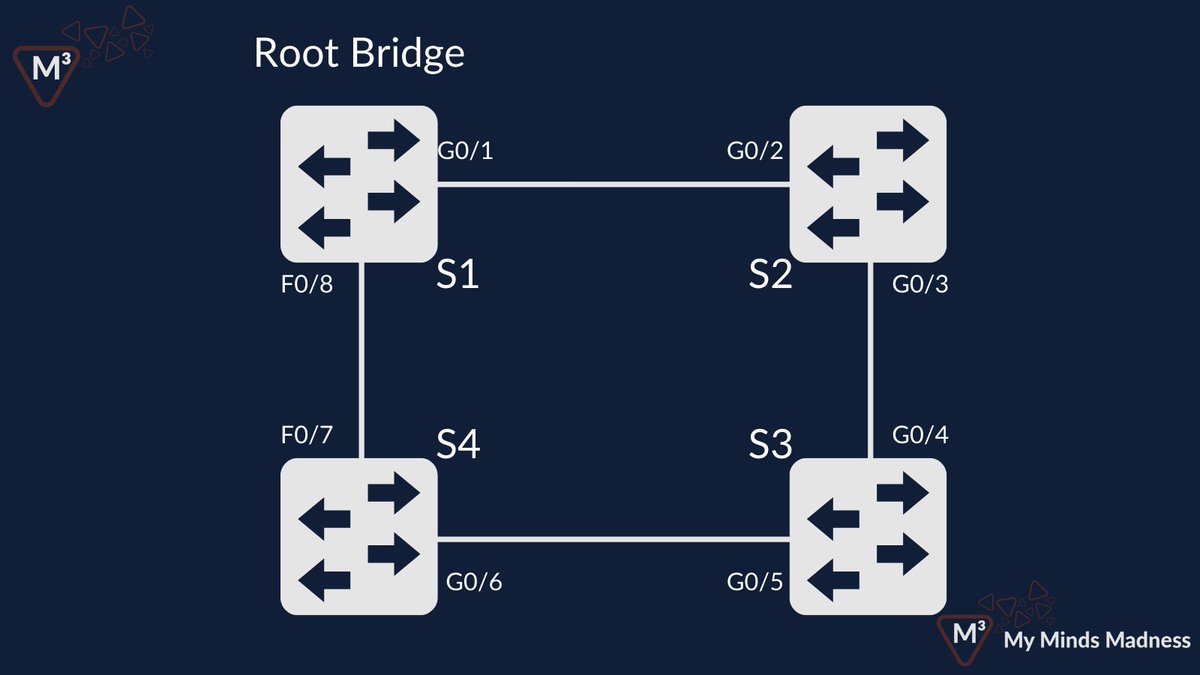
#DailyCCNAQuestion #NetworkAccess Refer to the exhibit. In Spanning Tree, What interface type would G0/5 be on S3? #CCNA #CiscoCert #Cisco #Networking #NetEng
Here are 5 of the best ZTNA Zero Trust Network architecture practices to follow for your enterprise. Read more: zurl.co/jsyk #ZTNA #ZeroTrust #NetworkAccess #Cybersecurity #InstaSafe

🔗 Network access = where devices meet the infrastructure. From Ethernet & fiber to Wi-Fi, VLANs, port security & FCS — mastering this ensures efficient, secure connections. 💡 Strong foundations = stronger networks. #Networking #NetworkAccess #CyberSecurity

Here are some of the top VPN disadvantages that make it unsuitable for your modern enterprise and workforce. Read more: zurl.co/RP3P #VPN #NetworkAccess #Cybersecurity #ZeroTrust #InstaSafe

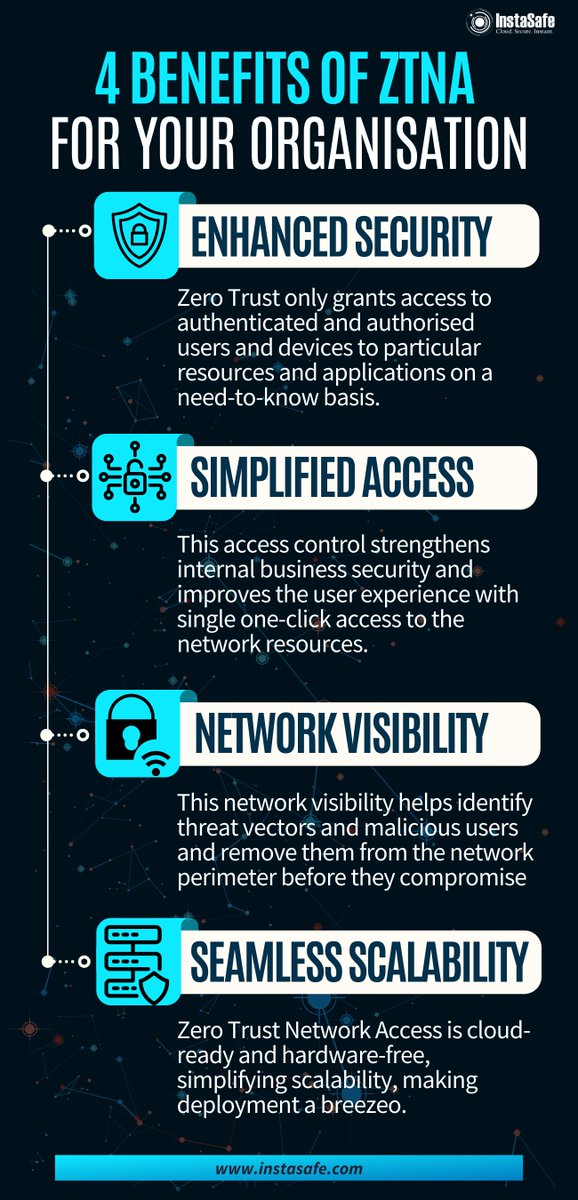
🛡️ Empower your organization with Zero Trust Network Access and unlock a new level of cybersecurity. Discover these 4 key benefits. Know more: zurl.co/m3Ud #Cybersecurity #NetworkAccess #TechAdvancements #ZeroTrust #Instasafe #ZTNA
There are many methods to improve #ClickHouse security at the user level. User level #networkaccess rules are a key method to protect ClickHouse data. Learn how they work and how to apply them in this post: hubs.ly/Q01CRC6C0 #kubernetes

Securing #networkaccess across hybrid workforces by knitting together static solutions is a risky approach. #ZTNA unifies simple, secure connections for users anywhere to resources everywhere; learn how in @AppgateSecurity’s ebook: appgate.com/resources/eboo… #ZeroTrust

If you are looking for a healthcare professional, we got you. We can give you access to a network of professionals so that you will be able to easily find the best candidate that fits your standards. #HealthcareStaffing #PhiladelphiaPA #NetworkAccess

Are you interested in learning more about #ZeroTrust #NetworkAccess (ZTNA) solutions? @gigaom analysts just released an in-depth report about the market-leading solutions, and Banyan is highlighted for its focus on simplicity. 💡 Download the report here: ow.ly/QgNJ50Mf96E

Enabling Seamless and Secure #NetworkAccess for you #HybridWorkforce How IT/ITeS companies can identify and address their #Network blind spots to maximize productivity of a hybrid workforce @rangu_s, CTO of Hewlett Packard Enterprise Read More rb.gy/qa1c8 #IT #tech

Amazon’s team uncovered attacks exploiting zero-day flaws in Cisco ISE and Citrix NetScaler, using custom web shells with advanced evasion techniques targeting enterprise networks. #ZeroDayExploits #NetworkAccess #USA ift.tt/SQbaOGJ
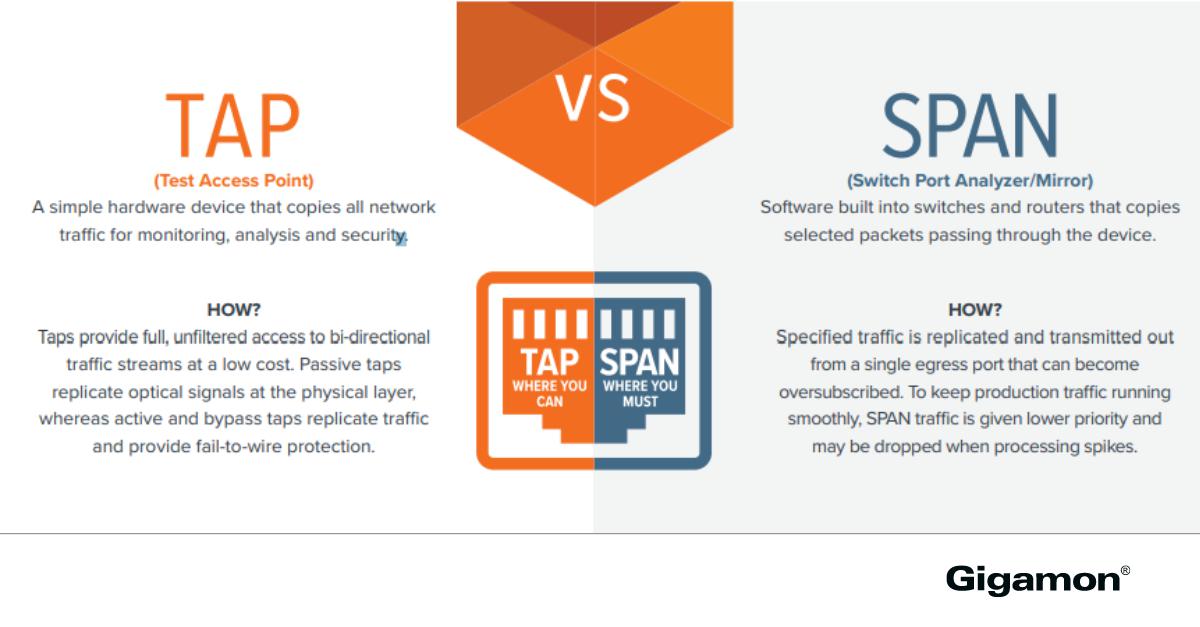
🔍To TAP or SPAN? What's the difference? Read more to learn how TAP and SPAN differ in providing #networkaccess in today's infrastructures! ow.ly/mjIx104nak5
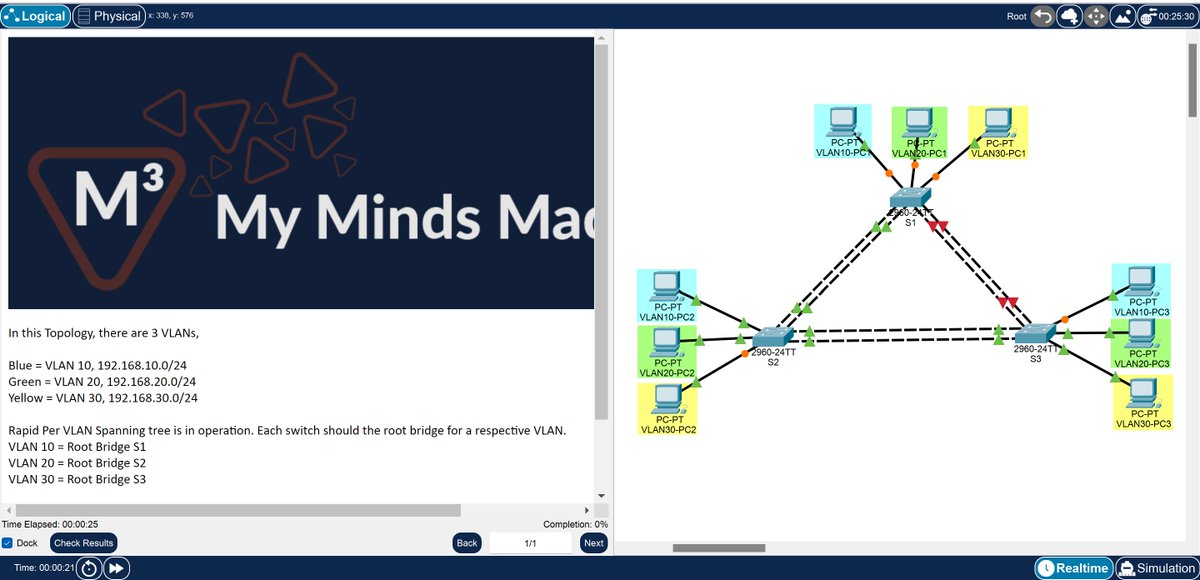
#DailyCCNAQuestion #NetworkAccess This weeks #TShooter is a combination of RSTP and Ether-channel... Got what it takes? Download Here: github.com/MyMindsMadness… #CCNA #Cisco #Networking
How did the State of Michigan utilize @tufintech to lower the number of days it took them to implement a #networkaccess change? Find out here: okt.to/Ci9M5W

Discover the power of #NetworkAccess in OT: From automatic access authorization to the reduction of administrative effort - find out more about the 12 reasons why macmon NAC revolutionizes control and security in networks. bit.ly/3NCcI6G #otsecurity #cybersecurity

Amazon’s team uncovered attacks exploiting zero-day flaws in Cisco ISE and Citrix NetScaler, using custom web shells with advanced evasion techniques targeting enterprise networks. #ZeroDayExploits #NetworkAccess #USA ift.tt/SQbaOGJ
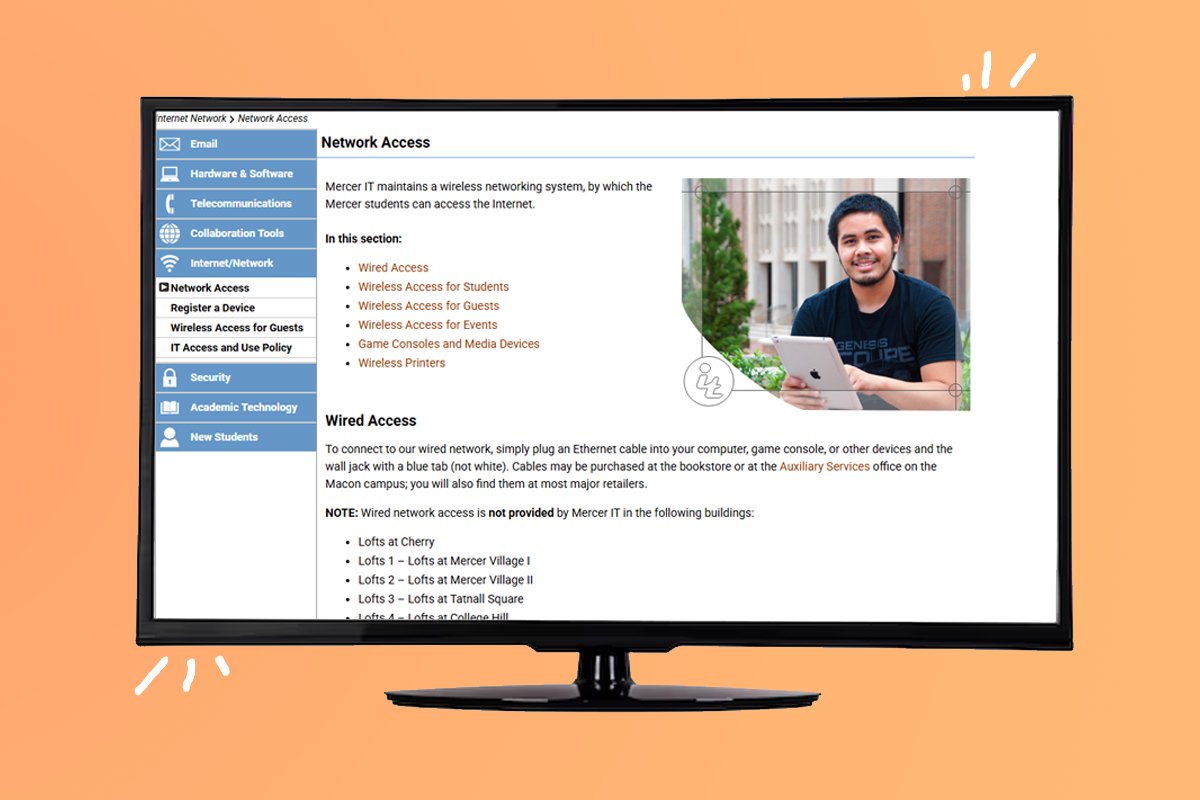
Students: Having visitors? They can connect to mercer Wi-fi too! Visit it.mercer.edu to find instructions for all wireless networks. it.mercer.edu/student/intern… #mercerIT #networkaccess
🔗 Network access = where devices meet the infrastructure. From Ethernet & fiber to Wi-Fi, VLANs, port security & FCS — mastering this ensures efficient, secure connections. 💡 Strong foundations = stronger networks. #Networking #NetworkAccess #CyberSecurity

Thousands to lose in-network access to Johns Hopkins Medicine if UnitedHealthcare contract expires Aug. 24 By Mylika Scatliffe, AFRO Health Writer ow.ly/eOs450WEQC3 #johnshopkins #unitedhealthcare #networkaccess #patientcare #insurancecoverage

A threat actor is selling network access to a major Argentinian telecom company on the dark web, including a shell for command-line control and 133 GB of data with pivoting potential. #Argentina #TelecomBreach #NetworkAccess ift.tt/zkipgut
🔌 NANO FACT #98 A network of public RPC nodes allows developers and users to interact with the Nano network without running their own full node. #RPCNodes #DeveloperTools #NetworkAccess #NanoFacts #XNO @nano

Today's pentest crystal ball. Implement network access control measures. Visit ayb.ad. #DeviceSecurity #CyberProtection #NetworkAccess #SecurityTips

🔌 Single Sign-On Wi-Fi Piloted ETC launched nationwide Wi-Fi authentication on 24 April. WFP staff are piloting it; partners will follow. #NetworkAccess #HumanitarianIT
Businesses must do everything possible to minimize the risk of easy network access and data exfiltration. Some startling new trends are covered by Chris Boyd of Rapid7 🔗in the comments We are proud to partner with Rapid7 💯 #ransomware #networkaccess #mfa #patchmanagement
#Hacking #NetworkAccess #Ransomware #Malware #Vulnerability #CyberCrime #CyberAttack #CyberSecurity Network hackers asked for over $1 million in initial access offers. bleepingcomputer.com/news/security/…
How Can Manufacturing Companies Improve Network Access and Security? j.mp/2F8L4rP #NetworkAccess #Security #SSO

Sage advice from @bobgourley: Think twice before using a personal VPN: bit.ly/Think-twice. #networkaccess #IAM #networksecurity #cybersec #smarthome #Internet #login #VPN #encryption #webdev @ctovision

#networkaccess #it #technology #workingfromhome #security #workfromhome #pandemicplanning #pandemicpreparedness #covid19 #coronavirus #covid #coronavirus2020 #pandemic #covid19uk #covid_19 #itsupport #itservices #microcomms #thetechnologypeople

Read how Talari Networks is partnering with Meta Networks to give their customers the option of using Meta’s NaaS platform. This will enable the Talari SD-WAN capabilities to extend beyond the perimeter of the enterprise hubs.ly/H0dDqr70 #zerotrust #networkaccess
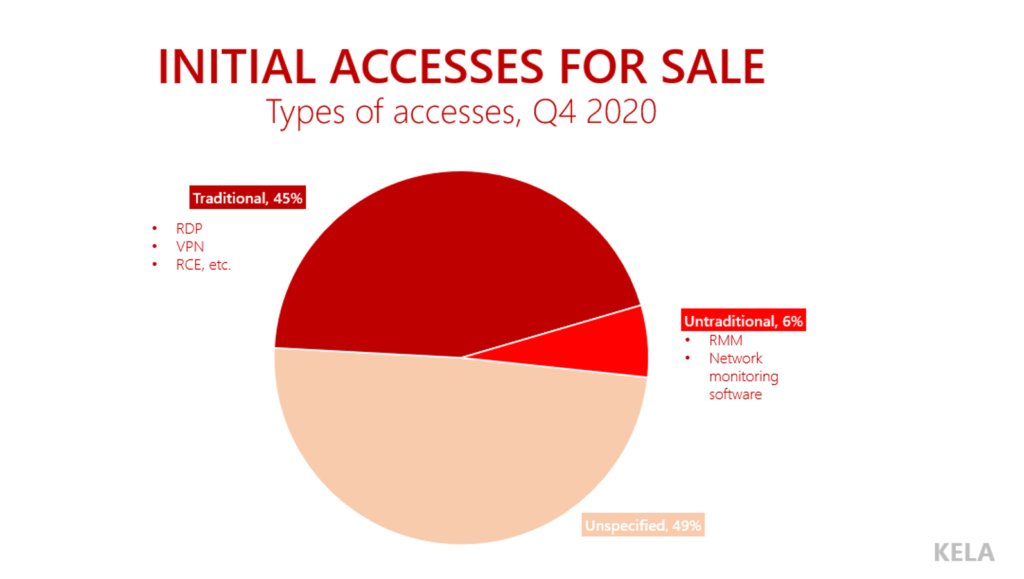
Right on time for RSA Conference, KELA releases another report by its Cybercrime Threat Research team, looking into #ransomware victims and #networkaccess sales in Q1 2022. 👉 Click to read the full report: ke-la.com/wp-content/upl… #cybercrimeawareness #threatintelligence

RT KitPloit "How Can Manufacturing Companies Improve #NetworkAccess and #Security? goo.gl/P2krbz https://t.co/bCfwHPd8X8"

Our Q2 #ransomware and #networkaccess Sales report is here! Click to read the full report by KELA's #cybercrimeintelligence Center: bit.ly/3vS0spV

🔌 NANO FACT #98 A network of public RPC nodes allows developers and users to interact with the Nano network without running their own full node. #RPCNodes #DeveloperTools #NetworkAccess #NanoFacts #XNO @nano

Building out your #ZeroTrust security strategy can be simple. Read our blog to get the answers you need in order to find a secure #networkaccess vendor that can seamlessly scale to meet your needs. bit.ly/3CBCxN0

We’ll see you @CommsConnectANZ on Stand 66! Talk to us about #IoTSimCards and #networkaccess for #CriticalComms industries such as #FirstResponders #Transport #Utilitiesand more m2mone.com.au

Pushing Ahead with Zero Trust and Zero Exceptions ed.gr/d3ddv @PaloAltoNtwks #ZeroTrust #ZeroExceptions #NetworkAccess #virtual_private_networks #VPNs #cybersecurity #cyberattacks #solution #cyberthreats #hybridwork

Are you looking for a way to quickly secure your remote workers while leveraging the agility of a clientless cloud-based solution? Download 6 Best Practices for #ZeroTrust Corporate Access whitepaper. bit.ly/2JEtioP #SASE #networkaccess

Start 2022 on the right foot by building out your #ZeroTrust security strategy. Read our blog to find the answers you need to select a secure #networkaccess vendor that can seamlessly scale to meet your needs. bit.ly/3CBCxN0

Here are 5 of the best ZTNA Zero Trust Network architecture practices to follow for your enterprise. Read more: zurl.co/jsyk #ZTNA #ZeroTrust #NetworkAccess #Cybersecurity #InstaSafe

Here are some of the top VPN disadvantages that make it unsuitable for your modern enterprise and workforce. Read more: zurl.co/RP3P #VPN #NetworkAccess #Cybersecurity #ZeroTrust #InstaSafe

Don’t let just anyone gain #networkaccess by plugging into a wall jack. Learn from this federal agency--including how Force 3 helped deploy #CiscoISE across its network. @CiscoSecurity #ISEStorm ow.ly/2hdc30k2jOX

🛡️ Empower your organization with Zero Trust Network Access and unlock a new level of cybersecurity. Discover these 4 key benefits. Know more: zurl.co/m3Ud #Cybersecurity #NetworkAccess #TechAdvancements #ZeroTrust #Instasafe #ZTNA

Something went wrong.
Something went wrong.
United States Trends
- 1. Josh Allen 39.9K posts
- 2. Texans 60K posts
- 3. Bills 150K posts
- 4. Joe Brady 5,306 posts
- 5. #MissUniverse 467K posts
- 6. #MissUniverse 467K posts
- 7. Anderson 27.9K posts
- 8. #StrayKids_DO_IT_OutNow 53.6K posts
- 9. McDermott 4,725 posts
- 10. Technotainment 19.5K posts
- 11. Troy 12.2K posts
- 12. #Ashes2025 24.4K posts
- 13. joon 12.7K posts
- 14. Beane 2,887 posts
- 15. #criticalrolespoilers 2,373 posts
- 16. GM CT 23.6K posts
- 17. Al Michaels N/A
- 18. Maxey 14.8K posts
- 19. Fátima 201K posts
- 20. FINAL DRAFT FINAL LOVE 1.29M posts