#proxyshell wyniki wyszukiwania
ProxyShell is still alive in the networks of giant players! 🫡 #ProxyShell #windows #ActiveDirectory #BugBounty
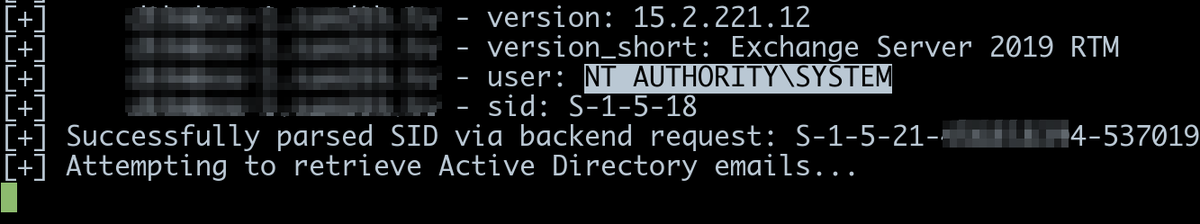
Vídeo NUEVO ❗️ Ustedes se enteraron de la vulnerabilidad #ProxyShell en #ExcahngeServer? Muchos no y de hecho todavía no han actualizado sus servidores. La Fiscalía de Colombia se vió afectada y te cuento este caso 👇🏻 youtu.be/h-dPwsmBPwI Deja tu me gusta 💙

🚨 #ProxyLogon and #ProxyShell Pose Ongoing Threats to #Government Mail Servers 🔍 Researchers found ongoing exploitation of these vulnerabilities in #MicrosoftExchange servers, targeting government entities in Asia, Europe, and South America to steal sensitive communications. 🔗…

Leaked internal APT35 docs show a quota-driven IRGC cyber unit using Exchange and Ivanti exploits, HERV-style phishing from Global Address Lists, and persistent mailbox monitoring with centralized KPI and attendance logs. #APT35 #ProxyShell #Iran ift.tt/ehTO0NY
🚨 vulnerabilidades de Microsoft Exchange siguen siendo explotadas por grupos criminales #ProxyNotShell #ProxyShell #cybersecurity #ciberseguridad
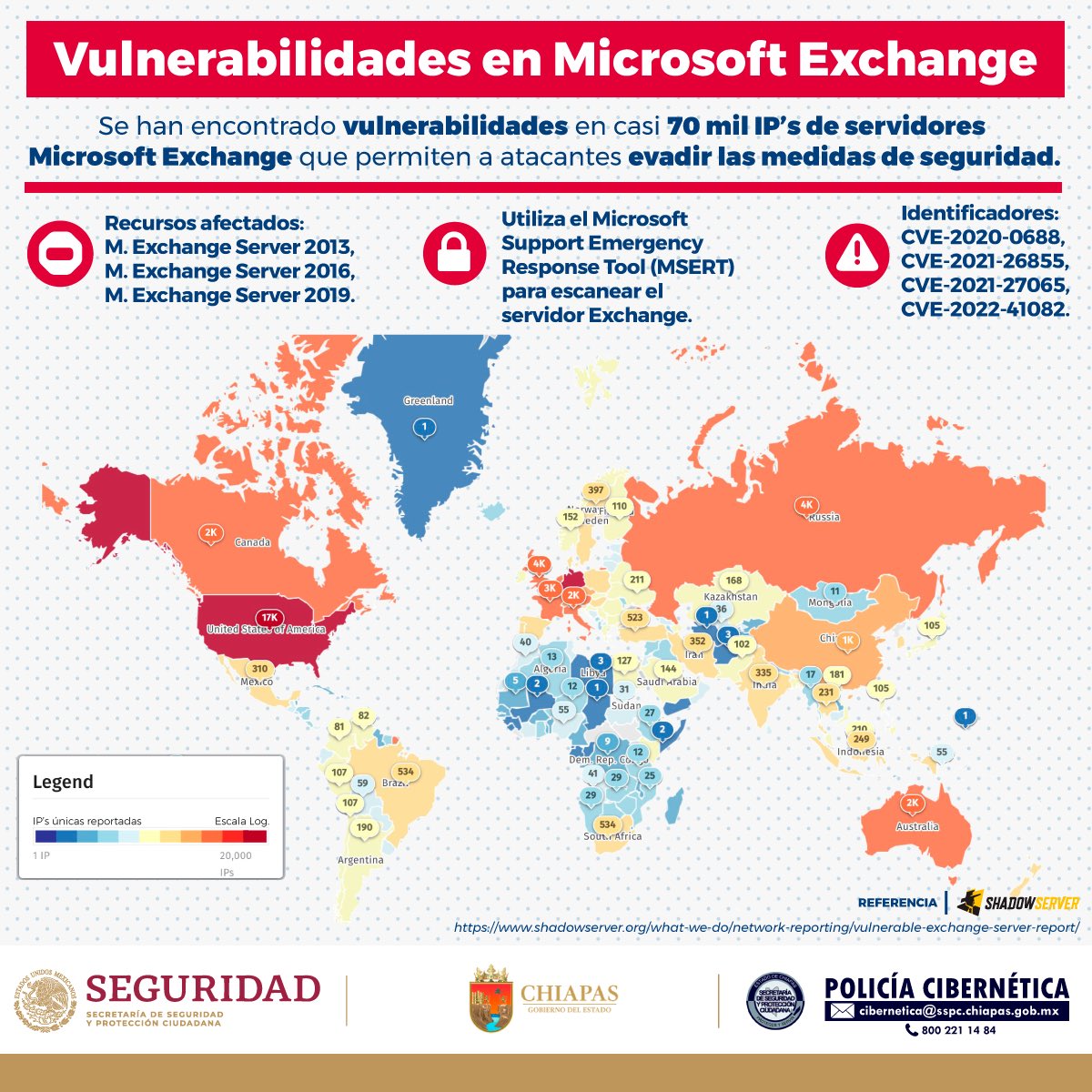
Microsoft Exchange ProxyShell is being exploited to mine crypto once again #MicrosoftExchange #ProxyShell #Crypto ow.ly/x9xk50MWhOF

Hackers are targeting unpatched Microsoft Exchange servers in 26 countries with JavaScript keyloggers to steal credentials. Read more! thehackernews.com/2025/06/hacker… #CyberSecurity #MicrosoftExchange #ProxyShell #CredentialTheft #ThreatIntelligence #InfoSec

Microsoft Exchange ProxyShell flaws exploited in new crypto-mining attack bleepingcomputer.com/news/security/… #Microsoft #Exchange #ProxyShell
Keylogger found on Microsoft Exchange Server steals login credentials globally. Discovered by Positive Technologies, this #Keylogger targets gov't and business logins since 2021. Exploits #ProxyShell vulnerability. #Cybersecurity #MicrosoftExchange

Weeks back, #CISA shared their '22 top exploited vulns, including #Log4shell, #ProxyShell & more. As always, we've got you covered w/ security tests for all 12, 🆓 to use on 25 endpoints + source code available. preludesecurity.com/advisories/aa2… #infosec #redteam
preludesecurity.com
Explore the latest insights on security control validation | Prelude
Find expert perspective and the latest news on how organizations are making the most of their security controls from the Prelude team.
#CobaltStrike beacon was deployed via a webshell that was planted by exploiting the #ProxyShell vulnerability. This #HsHarada campaign targets healthcare and healthcare-adjacent organizations, and relies on github.com/Tas9er
This year's #ProxyShell incident was a humbling reminder that no vendor is immune to #cyberattacks. Check out this article that dives into some of the lessons we learned as this vulnerability made its rounds. cpomagazine.com/cyber-security…
Keylogger Malware Deployed Through MS Exchange Server Vulnerabilities in Targeted Attacks #Keylogger #keylogging #ProxyShell #logonaspx #MicrosoftExchangeServer #clkLgn ptsecurity.com/ww-en/analytic…
Hunt identified a server likely exploiting #ProxyLogon & #ProxyShell flaws to gain initial access and steal sensitive communications. This renewed activity has affected government entities across multiple regions, including Asia, Europe, and South America securityonline.info/proxylogon-pro…
securityonline.info
ProxyLogon & ProxyShell Vulnerabilities Back: Gov't Emails Breached
Nearly three years after the notorious ProxyLogon and ProxyShell vulnerabilities caused widespread havoc on Microsoft Exchange servers
Top causes of a #ransomware attack: 1. ☠️Exploited Vulnerabilities (36%): Attacks carried out by exploiting vulnerabilities found in devices, often due to lack of diligent patching. #ProxyShell and #Log4Shell vulnerabilities were frequently present in affected assets. 2.…
未確認の攻撃者が65台の古いExchangeサーバにキー入力ログ挿入。既知ProxyShell脆弱性悪用し、JavaScriptで送信型/保存型キーロガー仕込み。政府・金融等が標的。古い脆弱Exchangeサーバの放置は致命的。#ExchangeAttack #Keylogger #ProxyShell thehackernews.com/2025/06/hacker…
thehackernews.com
Hackers Target Over 70 Microsoft Exchange Servers to Steal Credentials via Keyloggers
Hackers target Microsoft Exchange servers worldwide, injecting keyloggers to steal credentials from victims in 26 countries.
🚨Major Threat Alert: Keylogger Found Lurking in Microsoft Exchange Server - #ProxyShell CVE-2021-34523 CVE-2021-31207 CVE-2021-34473 CVE-2020-1472 Severity: 🔴 High Maturity: 💥 Mainstream fletch.ai/p/proxyshell #CyberSecurity #ThreatIntel #InfoSec
#ProxyShell y #ProxyLogon fueron grandes oportunidades para adversarios, es hora de un nuevo set de vulnerabilidades abusadas on-the-wild. Más detalles en @behackerpro behacker.pro/proxynotshell-…
Leaked internal APT35 docs show a quota-driven IRGC cyber unit using Exchange and Ivanti exploits, HERV-style phishing from Global Address Lists, and persistent mailbox monitoring with centralized KPI and attendance logs. #APT35 #ProxyShell #Iran ift.tt/ehTO0NY
Hackers are targeting unpatched Microsoft Exchange servers in 26 countries with JavaScript keyloggers to steal credentials. Read more! thehackernews.com/2025/06/hacker… #CyberSecurity #MicrosoftExchange #ProxyShell #CredentialTheft #ThreatIntelligence #InfoSec

未確認の攻撃者が65台の古いExchangeサーバにキー入力ログ挿入。既知ProxyShell脆弱性悪用し、JavaScriptで送信型/保存型キーロガー仕込み。政府・金融等が標的。古い脆弱Exchangeサーバの放置は致命的。#ExchangeAttack #Keylogger #ProxyShell thehackernews.com/2025/06/hacker…
thehackernews.com
Hackers Target Over 70 Microsoft Exchange Servers to Steal Credentials via Keyloggers
Hackers target Microsoft Exchange servers worldwide, injecting keyloggers to steal credentials from victims in 26 countries.
Basic failures led to hack of Electoral Commission data on 40 million people computerweekly.com/news/366599512… via @computerweekly # China #vulnerability #ProxyShell #passwords #Microsoft
computerweekly.com
Basic failures led to hack of Electoral Commission data on 40 milli...
The Information Commissioners Office has issued a reprimand to the Electoral Commission after basic security errors allowed hackers linked to the Chinese state to gain access to servers containing ...
🚨 #ProxyLogon and #ProxyShell Pose Ongoing Threats to #Government Mail Servers 🔍 Researchers found ongoing exploitation of these vulnerabilities in #MicrosoftExchange servers, targeting government entities in Asia, Europe, and South America to steal sensitive communications. 🔗…

Hunt identified a server likely exploiting #ProxyLogon & #ProxyShell flaws to gain initial access and steal sensitive communications. This renewed activity has affected government entities across multiple regions, including Asia, Europe, and South America securityonline.info/proxylogon-pro…
securityonline.info
ProxyLogon & ProxyShell Vulnerabilities Back: Gov't Emails Breached
Nearly three years after the notorious ProxyLogon and ProxyShell vulnerabilities caused widespread havoc on Microsoft Exchange servers
Keylogger Malware Deployed Through MS Exchange Server Vulnerabilities in Targeted Attacks #Keylogger #keylogging #ProxyShell #logonaspx #MicrosoftExchangeServer #clkLgn ptsecurity.com/ww-en/analytic…
🚨Major Threat Alert: Keylogger Found Lurking in Microsoft Exchange Server - #ProxyShell CVE-2021-34523 CVE-2021-31207 CVE-2021-34473 CVE-2020-1472 Severity: 🔴 High Maturity: 💥 Mainstream fletch.ai/p/proxyshell #CyberSecurity #ThreatIntel #InfoSec
Keylogger found on Microsoft Exchange Server steals login credentials globally. Discovered by Positive Technologies, this #Keylogger targets gov't and business logins since 2021. Exploits #ProxyShell vulnerability. #Cybersecurity #MicrosoftExchange

🚨 Ahora, más de 384.000 correos (67 GB) del Ministerio de Justicia de Chile 🇨🇱 han sido filtrados a raíz de un ataque a la plataforma Microsoft Exchange, al parecer, utilizando las mismas vulnerabilidades explotadas por #Guacamaya. #ProxyLogon #ProxyShell 🥹


Alternate tactic being used in #ProxyShell: attacker modified IIS "MSExchangeOWAAppPool" app pool by adding additional virtual directory to "/owa" with path "/auth/类/hxxxy". Webshell located in C:\ProgramData\COM1\hxxxy. Check your configs when hunting!

dmaasland / proxyshell-poc github.com/dmaasland/prox… #Pentesting #ProxyShell #CyberSecurity #Infosec



Sigma rules to detect #Exchange #ProxyShell exploitation attempts I'll improve the rules tomorrow with actual PoCs (someone was so kind and offered to share his PoC with me) HTTP log github.com/SigmaHQ/sigma/… Process Creation github.com/SigmaHQ/sigma/…


I have written an @pdnuclei rule to detect the compromise of the Proxyshell vulnerability. I'll test a little more before committing. Very happy with the result 🚀 #proxyshell #CVE-2021-34473 #CTI

Turns out you don't need a valid email address to exploit #ProxyShell. You can just ask the server for them: github.com/dmaasland/prox…

A basic proxylogon scanner github.com/dinosn/proxysh… #Pentesting #ProxyShell #ProxyLogon #CyberSecurity #Infosec

Exchange Exploit Leads to Domain Wide Ransomware thedfirreport.com/2021/11/15/exc… #Pentesting #Ransomware #ProxyShell #CyberSecurity #Infosec




For a compromise assessment of #Exchange servers I recommend using our free THOR Lite scanner We've added all rules & IOCs relevant to #ProxyShell exploitation & update them frequently THOR Lite nextron-systems.com/thor-lite/ YARA rules github.com/Neo23x0/signat… github.com/Neo23x0/signat…




Some cheeky #ProxyShell shenanigans in a discovered webshell -- the BQPQ variable looks like enough gibberish to be consider Base64 at first glance, but it's just a pool of characters to pull from and index the letters to build out the "unsafe" keyword for the eval function.

From PWN2OWN 2021 : A New Attack Surface on Microsoft Exchange - ProxyShell! zerodayinitiative.com/blog/2021/8/17… #Pentesting #ProxyShell #PWN2OWN #CyberSecurity #Infosec


🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells] El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás. 💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware REF: bleepingcomputer.com/news/security/…
![1ZRR4H's tweet image. 🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells]
El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás.
💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware
REF: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/FDilIbKWYAoQvl3.png)
![1ZRR4H's tweet image. 🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells]
El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás.
💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware
REF: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/FDikIJyWUAY4Toh.png)
Keep your Exchange servers safe this weekend. @HuntressLabs has seen 140+ webshells across 1900+ unpatched boxes in 48hrs. Impacted orgs thus far include building mfgs, seafood processors, industrial machinery, auto repair shops, a small residential airport and more. #ProxyShell

Another good thing to look out for, is webshells saved as attachments in people's mailboxes. They are encoded, but can be decoded with this simple script: gist.github.com/rxwx/b5a8ef0cd… #ProxyShell


96[.]9.225.205 looking for #proxyShell #msexchange vuln #cybercrime #ThreatIntel @smica83 @securitydoggo @bad_packets @malwrhunterteam @Max_Mal_
![whitehoodie4's tweet image. 96[.]9.225.205
looking for #proxyShell #msexchange vuln
#cybercrime #ThreatIntel
@smica83 @securitydoggo @bad_packets @malwrhunterteam @Max_Mal_](https://pbs.twimg.com/media/E-r69yCXsAwuUCl.png)
Update your THOR Lite with thor-lite-util.exe update to get the newest #YARA signature that detects #ProxyShell exploitation attempts in log files Tomorrow I'll split the rules into "attempts" and "successful attempts" to provide a better verdict
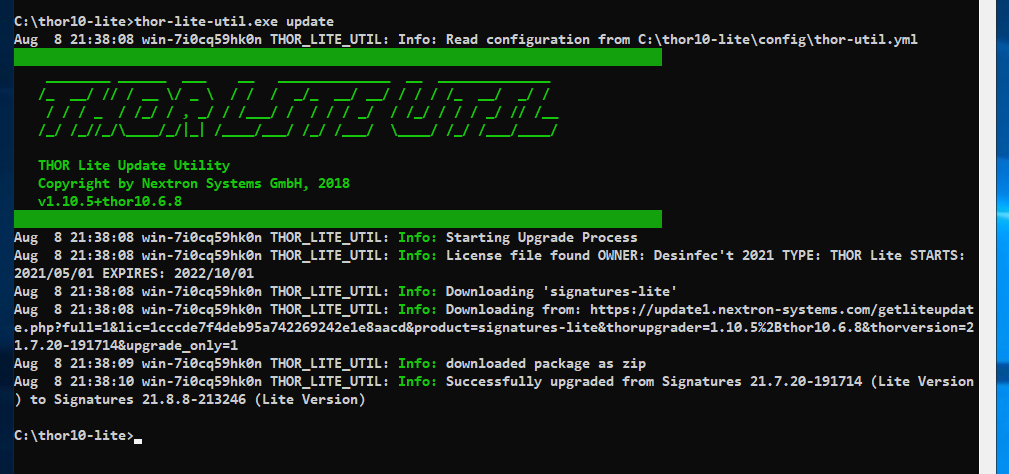
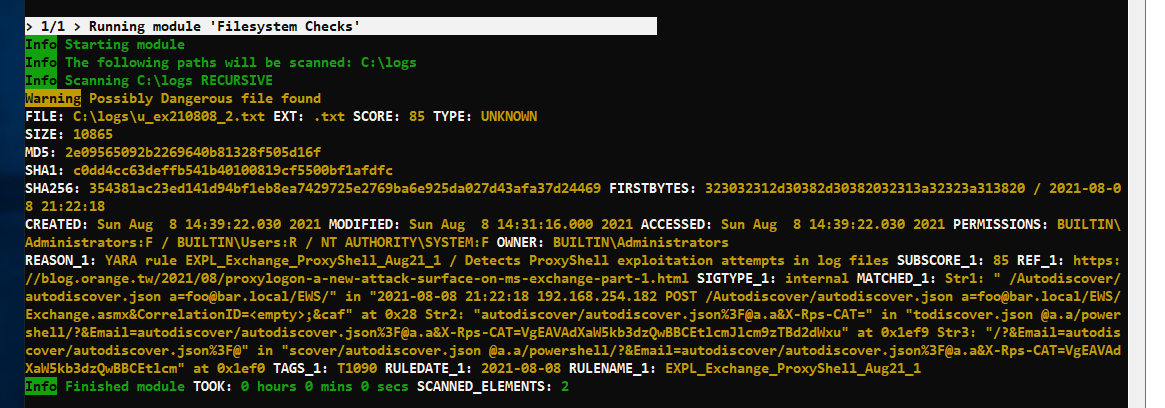
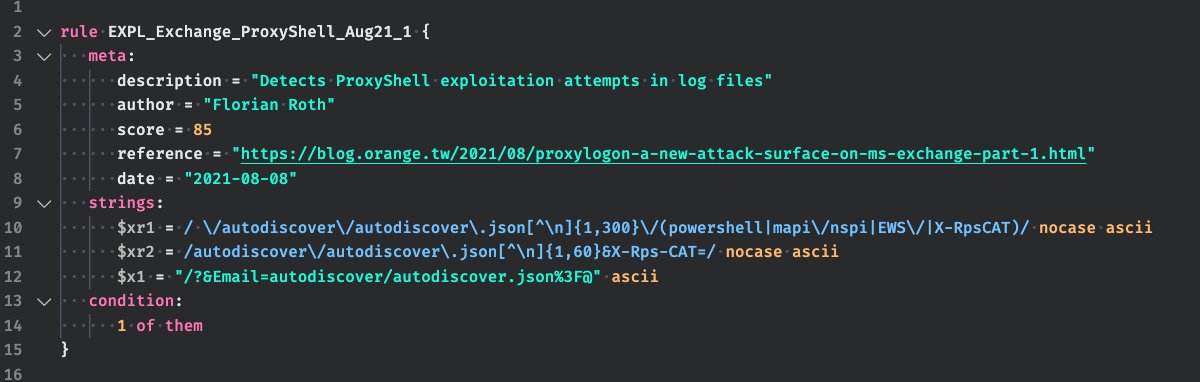
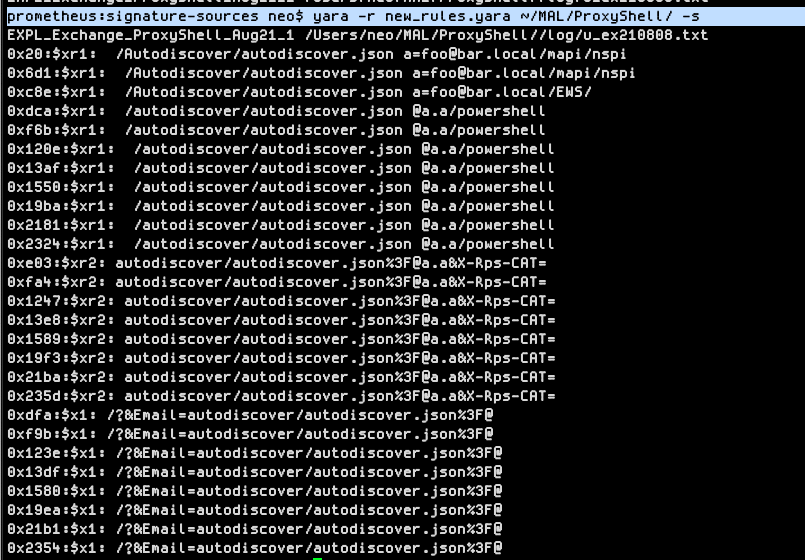
YARA rule to detect #ProxyShell exploitation in log files @buffaloverflow provided a log file of an exploited exchange/iis server to work with gist.githubusercontent.com/rxwx/060743a2b… YARA rule github.com/Neo23x0/signat… Will soon be available in LOKI and THOR Lite
Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 109K posts
- 2. Thanksgiving 620K posts
- 3. Afghan 241K posts
- 4. Reed Sheppard 1,382 posts
- 5. National Guard 611K posts
- 6. Gonzaga 7,675 posts
- 7. robin 62K posts
- 8. holly 45.6K posts
- 9. #AEWDynamite 20.5K posts
- 10. Michigan 75.3K posts
- 11. Dustin 83.9K posts
- 12. Tini 7,287 posts
- 13. Rahmanullah Lakanwal 91.5K posts
- 14. #Survivor49 2,887 posts
- 15. Erica 11.7K posts
- 16. #GoAvsGo 1,277 posts
- 17. Jardine 4,641 posts
- 18. Will Richard 1,940 posts
- 19. Dusty May N/A
- 20. Kevin Knight 2,543 posts