#securityframework نتائج البحث
The 12 Pillars of Cyber Security! 🛡️ Know your defense: from Encryption to API Security. Are you covering all 12? #CyberSecurity #InfoSec #SecurityFramework #digitalearn #DevOps

The advantage of aligning your or your customer’s #cybersecurity roadmap to a #securityframework is defining a route to follow using established security best practices. bit.ly/3Ke7gWy #cybersecurityroadmap
Static defenses died when AI entered the chat 🤖 Your AI needs: ✓ Adversarial training ✓ Continuous threat intel ✓ Automated response Because attackers are using AI too. #AI #SecurityFramework #DevSecOps #Resilience

#IEMLabs #securityframework #cybersecurity #cybersecurityawareness #cybersecuritytraining #cybersecuritytips #systemsecurity

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has released 'Decider,' an open-source tool that helps defenders and security analysts quickly generate MITRE ATT&CK mapping reports 👩💻🛡️ #securityframework #securitybaseline buff.ly/3mybej2

Once you have aligned to a #securityframework, it's time to hit the road and put your cybersecurity roadmap into action. Find out how to get started. bit.ly/3Ud4Bj5 #cyberhygiene #cybersecurityroadmap

With a CIS SecureSuite Membership, your organization will be able to effectively track your implementation of the CIS Controls with our self-assessment tool. bit.ly/40dofNH #cybersecurityroadmap #securityframework

Join our February 16th #Webinar with #CISO Karl Mattson and learn how to balance security and business priorities, implement robust #SecurityFramework, adopting a business-centric approach. Register now: bit.ly/3vXtqr3 #ECCouncil #Cybersecurity #RiskManagement

Unlock the Power of Data Sharing! The benefits are vast, but so are the risks. Sensitive data needs protection. Learn how Securiti simplifies secure data sharing—maximizing value without compromising security. 🔒 bit.ly/494DnkQ #DataSharing #SecurityFramework

In the process of simplifying your use of a framework, you’ll be able to make meaningful progress when it comes time to begin implementing your roadmap. bit.ly/3Ke7gWy #cybersecurity #cybersecurityroadmap #securityframework

Proposing a configurable and comprehensive hardware-software #securityframework: “IoTrust - a HW/SW framework supporting security core baseline features for #IoT“ by M. Korona, B. Zabołotny, F. Kozioł, et al. ACSIS Vol. 35 p. 1029–1034; tinyurl.com/j8w56rkb

Last 48 hours left for our February 16th #Webinar. Join Karl Mattson and learn to build an effective #SecurityFramework, its requirements, and how to maintain a versatile #CybersecurityStrategy to sustain #CyberLeadership. Register now: bit.ly/3vXtqr3 #ECCouncil

Join our February 16th #Webinar with Karl Mattson and explore balancing security and business priorities. Learn the importance of the shift to a business-centric approach, creating a #SecurityFramework. Register now:bit.ly/3vXtqr3 #Cybersecurity #CyberThreat #ECCouncil

Embrace the power of Node.js permission model for robust security! Safeguard resources, fortify apps, and navigate modern development confidently with Pedals Up. 🔒 🌐 pedalsup.com 📧 [email protected] #NodeJS #SecurityFramework #CyberSecurity
We have arrived at stop two on our cybersecurity roadmap to success! When you map your route, you are able to identify a reference point that you can use to organize and plan your #cybersecurity efforts around. bit.ly/3Ke7gWy #cybersecurityroadmap #securityframework

Most frameworks look solid on paper — until attackers use new tactics that bypass them entirely. At HITRUST, we’ve built a framework that learns from the front lines. Learn about the top 5 current threats. hubs.ly/Q03jY3l10 #ThreatIntelligence #SecurityFramework

Join our March 26th #Webinar, where cyber expert Sentil Velaytham shares insights on the effectiveness of proactive detection and response, creating a cyber-resilient #SecurityFramework. Register now: bit.ly/3wB676M #CTIA #ECCouncil

Applying the Zero Trust Security Principles to SSH Access. One of the major issues of using SSH to share data and information is using the SSH keys. Know more: zurl.co/41CS #ZeroTrust #ZeroTrustSecurity #SecurityFramework #Cybersecurity #NetworkSecurity

Static frameworks quickly become obsolete. HITRUST is different as it adapts with emerging threats. Explore the top 5 attack techniques and how HITRUST helps organizations stay one step ahead. hubs.ly/Q03CX2zG0 #ThreatIntelligence #ThreatManagement #SecurityFramework

Cloud security standards provide a framework for organizations to assess and demonstrate their security posture. Learn about the most common cloud security standards and their requirements. #CloudSecurityStandards #SecurityFramework
8️⃣ THE 4D STRATEGY FOR INTERNAL SECURITY (UPSC-READY) Deter → Detect → Develop → Deliver. Each district’s transformation = synergy of security, social policy, and sustainable livelihoods. #GS3 #SecurityFramework
The 12 Pillars of Cyber Security! 🛡️ Know your defense: from Encryption to API Security. Are you covering all 12? #CyberSecurity #InfoSec #SecurityFramework #digitalearn #DevOps

From internal threats to external risks, our new catalog has you covered. It's an indispensable resource for creating a robust security framework. Discover it on Etsy! #InternalThreats #ExternalRisks #SecurityFramework #CyberSecurity #GRC atelyedr.etsy.com/listing/433708…
From vulnerability management to policy enforcement, our GRC framework covers it all. Stop guessing and start strategizing with a proven system. Discover our product on Etsy. #VulnerabilityManagement #CyberPolicy #SecurityFramework #GRC #CyberSecurity atelyedr.etsy.com/listing/436630…
Static defenses died when AI entered the chat 🤖 Your AI needs: ✓ Adversarial training ✓ Continuous threat intel ✓ Automated response Because attackers are using AI too. #AI #SecurityFramework #DevSecOps #Resilience

Static frameworks quickly become obsolete. HITRUST is different as it adapts with emerging threats. Explore the top 5 attack techniques and how HITRUST helps organizations stay one step ahead. hubs.ly/Q03CX2zG0 #ThreatIntelligence #ThreatManagement #SecurityFramework

Improving existing security protocols can help prevent AI security breaches and maintain trust in AI ecosystems #securityframework
Regular audits and security assessments can help identify and mitigate potential threats #securityframework
Enhancing AI agent security requires a detailed plan, leveraging expertise in blockchain forensics and AI security to protect AI ecosystems ~ #securityframework
The 12 Pillars of Cyber Security! 🛡️ Know your defense: from Encryption to API Security. Are you covering all 12? #CyberSecurity #InfoSec #SecurityFramework #digitalearn #DevOps

🟢Join us live today at 4 PM IST for our next webinar by Sid @sidnext2none @BellLabs find out about Bhadra framework & get a chance to contribute to this framework Register now➡️bit.ly/3DqGRzb #Nullcon #telcomsecurity #securityframework #infosec #cybersecurity #5G

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has released 'Decider,' an open-source tool that helps defenders and security analysts quickly generate MITRE ATT&CK mapping reports 👩💻🛡️ #securityframework #securitybaseline buff.ly/3mybej2

Static defenses died when AI entered the chat 🤖 Your AI needs: ✓ Adversarial training ✓ Continuous threat intel ✓ Automated response Because attackers are using AI too. #AI #SecurityFramework #DevSecOps #Resilience

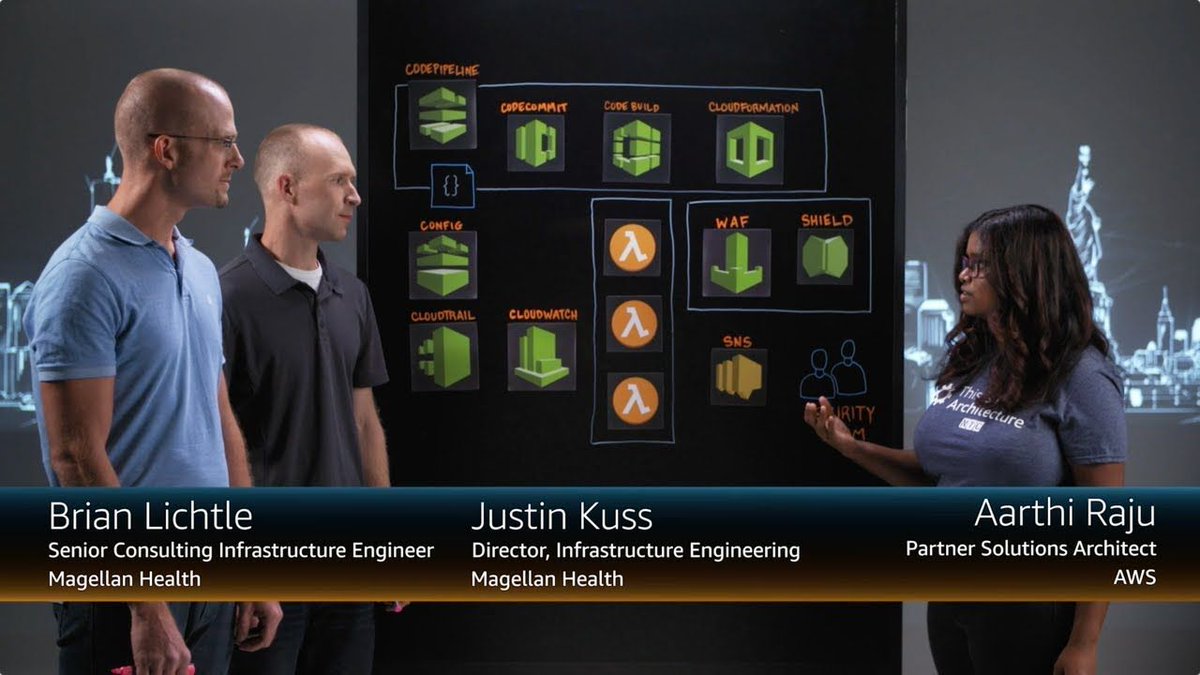
Check it out. See how Magellan Health is using #AWS to build a new centralized #securityframework: buff.ly/2JmQPGh
Join our February 16th #Webinar with #CISO Karl Mattson and learn how to balance security and business priorities, implement robust #SecurityFramework, adopting a business-centric approach. Register now: bit.ly/3vXtqr3 #ECCouncil #Cybersecurity #RiskManagement

Last 48 hours left for our February 16th #Webinar. Join Karl Mattson and learn to build an effective #SecurityFramework, its requirements, and how to maintain a versatile #CybersecurityStrategy to sustain #CyberLeadership. Register now: bit.ly/3vXtqr3 #ECCouncil

Join our February 16th #Webinar with Karl Mattson and explore balancing security and business priorities. Learn the importance of the shift to a business-centric approach, creating a #SecurityFramework. Register now:bit.ly/3vXtqr3 #Cybersecurity #CyberThreat #ECCouncil

Once you have aligned to a #securityframework, it's time to hit the road and put your cybersecurity roadmap into action. Find out how to get started. bit.ly/3Ud4Bj5 #cyberhygiene #cybersecurityroadmap

We’re delighted to have been selected as a supplier for YPO’s Data Centres, Maintenance Cloud Hosting and Security Framework @ypoinfo #CloudHosting #DateCentre #SecurityFramework

Applying the Zero Trust Security Principles to SSH Access. One of the major issues of using SSH to share data and information is using the SSH keys. Know more: zurl.co/41CS #ZeroTrust #ZeroTrustSecurity #SecurityFramework #Cybersecurity #NetworkSecurity

Join our March 26th #Webinar, where cyber expert Sentil Velaytham shares insights on the effectiveness of proactive detection and response, creating a cyber-resilient #SecurityFramework. Register now: bit.ly/3wB676M #CTIA #ECCouncil

Static frameworks quickly become obsolete. HITRUST is different as it adapts with emerging threats. Explore the top 5 attack techniques and how HITRUST helps organizations stay one step ahead. hubs.ly/Q03CX2zG0 #ThreatIntelligence #ThreatManagement #SecurityFramework

Methods to Upgrade your M365 Security Framework - Threat Protection - Identity and Access Management - Information Protection - Security Management Read more about it:lnkd.in/daHrB8Z #M365 #securityframework #microsoft365 #bitscape

Proposing a configurable and comprehensive hardware-software #securityframework: “IoTrust - a HW/SW framework supporting security core baseline features for #IoT“ by M. Korona, B. Zabołotny, F. Kozioł, et al. ACSIS Vol. 35 p. 1029–1034; tinyurl.com/j8w56rkb

With a CIS SecureSuite Membership, your organization will be able to effectively track your implementation of the CIS Controls with our self-assessment tool. bit.ly/40dofNH #cybersecurityroadmap #securityframework

Most frameworks look solid on paper — until attackers use new tactics that bypass them entirely. At HITRUST, we’ve built a framework that learns from the front lines. Learn about the top 5 current threats. hubs.ly/Q03jY3l10 #ThreatIntelligence #SecurityFramework

With so many potential threats, it’s vital to understand what #cybersecurity is, the available solutions, and how to create a robust #SecurityFramework to mitigate risks and keep protected. @NETSCOUT bit.ly/3C6sW0U

Unlock the Power of Data Sharing! The benefits are vast, but so are the risks. Sensitive data needs protection. Learn how Securiti simplifies secure data sharing—maximizing value without compromising security. 🔒 bit.ly/494DnkQ #DataSharing #SecurityFramework

Something went wrong.
Something went wrong.
United States Trends
- 1. Howie 4,428 posts
- 2. Good Monday 38.3K posts
- 3. #MondayMotivation 30.3K posts
- 4. Phillips 493K posts
- 5. $IREN 11.2K posts
- 6. #Talus_Labs N/A
- 7. Victory Monday 1,430 posts
- 8. Kimberly-Clark N/A
- 9. #MondayVibes 2,258 posts
- 10. 60 Minutes 96.1K posts
- 11. Winthrop N/A
- 12. #RomanEmpireByBangChan 22.4K posts
- 13. Kenvue 3,591 posts
- 14. Jets 3rd N/A
- 15. ROMAN EMPIRE OUT NOW 19.2K posts
- 16. $MSFT 17K posts
- 17. #MondayMood 1,154 posts
- 18. Spinoza 1,445 posts
- 19. National Sandwich Day N/A
- 20. Jayden 45.8K posts

























