#webshells search results
Once again #Emotet changed their #Webshells, providing minor modifications such as the title (#fsociety), password and comments. Source IP addresses accessing them to update the payloads and grep commands to identify those files have been updated on my Github @Cryptolaemus1

Banco en Latinoamérica lleva más de 1 mes comprometido vía #ProxyLogon CVE-2021-26855. Es demasiada negligencia! simplemente algunas organizaciones no estan preparadas o no son conscientes del riesgo y la evolución constante de las ciberamenazas, CUIDADO. #backdoors #webshells

Banco Pichincha Hacked ~ Threat Actor: Hotarus Corp #Webshells #DataLeak #Extorsion



WSO2 - CVE-2022-29464 🚨 Unrestricted File Upload lead to RCE 1ra ronda de explotación inicio el 21 de Abril con la instalación masiva de #webshells como backdoor. Al menos 212 servidores en el mundo ya están comprometidos (última imagen con el TOP 25 servidores por país).




#opendir #webshells #qbot hxxp://samsung-drivers[.]xyz app.any.run/tasks/4c84dfe9… @James_inthe_box @JAMESWT_MHT
![jstrosch's tweet image. #opendir #webshells #qbot
hxxp://samsung-drivers[.]xyz
app.any.run/tasks/4c84dfe9…
@James_inthe_box @JAMESWT_MHT](https://pbs.twimg.com/media/EwFNbgpWgAsOkzs.jpg)
![jstrosch's tweet image. #opendir #webshells #qbot
hxxp://samsung-drivers[.]xyz
app.any.run/tasks/4c84dfe9…
@James_inthe_box @JAMESWT_MHT](https://pbs.twimg.com/media/EwFNcAQXEAAbTVg.jpg)
In my experience #webshells are the most overlooked risk topic in the #CISO community. Being that #SharePoint is beloved by enterprises, this #CVE 2019-0604 is a great opportunity to explain adversary web shell placement and usage tactics. #vulnerabilities @RecordedFuture



#opendir hosting #CobaltStrike #webshells and #shellcode loader 152.32.170.129 🇭🇰 121.exe and 12.exe (both CobaltStrike) connect to 152.42.226.16 🇸🇬 for C2 Interesting payload hosted in Sqlite database (also CobaltStrike)



#phishing #webshells //milangroupinternational[.]com/wp-content/uploads/ Phishing using Excel sheet login and another for DHL @DHLUS @PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXuqzX4AAelY-.png)
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXvgYWkAEDDHS.jpg)
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXwLaW4AAeI-g.png)
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXw4eX4AIffpC.jpg)
Again! This one is a real mess... @auspost and @Israelpost2022 #phishing kits as PHP #webshells #phishingkit #webshell #soc #cybersecurity #scam #stalkphish #opendir

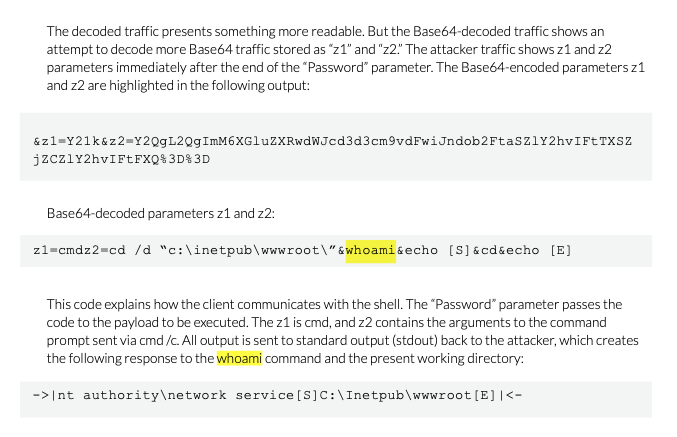
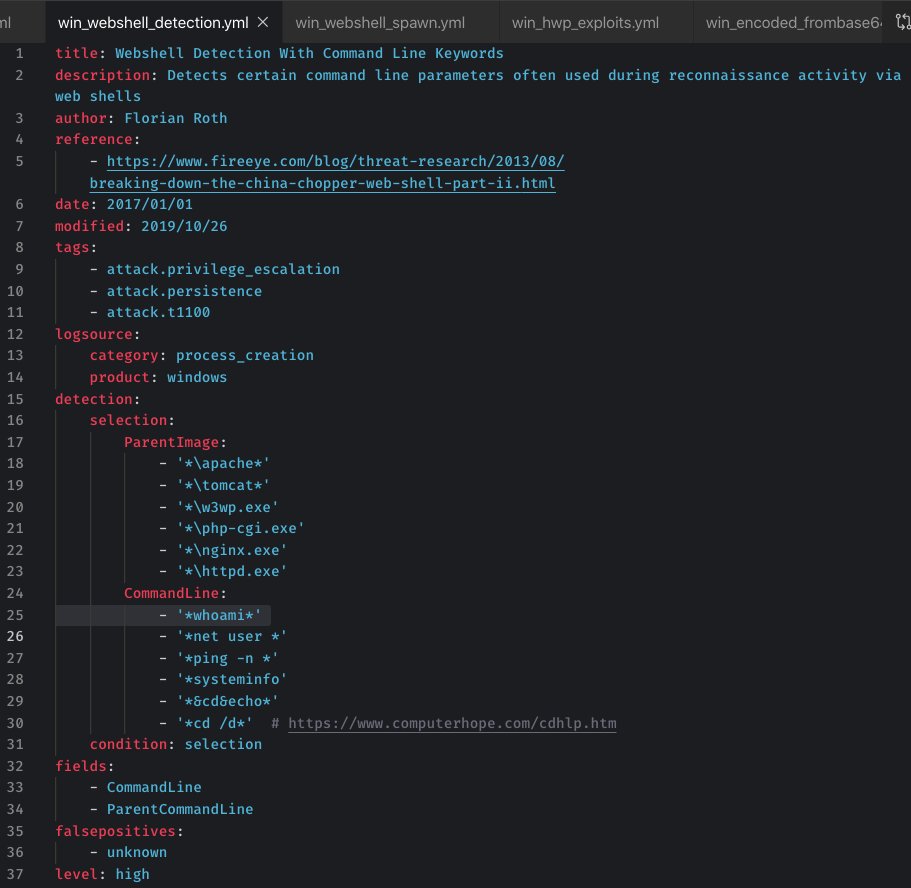
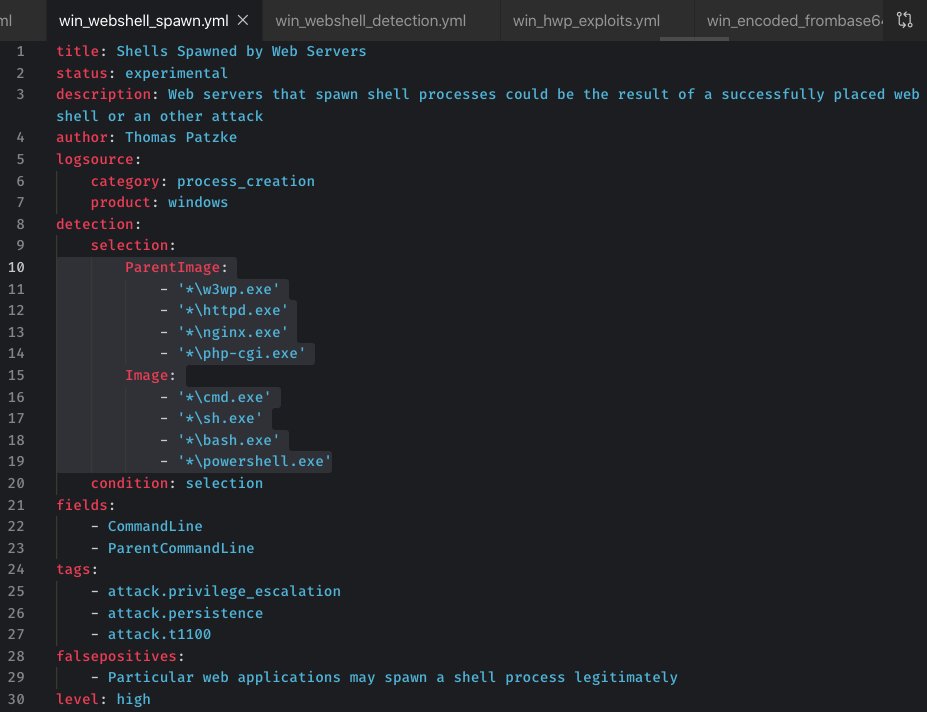
It may be hard to detect #Webshells in your Sandbox 🙃 But there's a generic way to detect webshells w/ Sigma rules that trigger on susp parent->child process relations @FireEye example China Chopper fireeye.com/blog/threat-re… Rules github.com/Neo23x0/sigma/… github.com/Neo23x0/sigma/…
Know thy #webshells and may your #hunting prove productive! github.com/fengchenzxc/fe… #MondayMotivaton #Malware #infosec #cybersecurity #DFIR #ThreatHunting #threatintel #riskmanagement #chinachopper #cknife #antsword #behinder #xise #altman #weevely #quasibot #sniper #manager

#Webshells Providers 🕸️ CMS exploiter bot, +30 Wordpress/others vulns. ~ #TR #Qakbot #SquirrelWaffle 🤭
several base64 encoded #webshells - retrieved via php file_get_contents/base64_decode: pastebin.com/raw/zUb7iayg pastebin.com/raw/6DuKx17b pastebin.com/raw/NE6MLDK7 pastebin.com/raw/nvZCFqKf pastebin.com/raw/d2Ti4xg9 #opendir #mailer: hxxps://a-mla.org/images/acts/

🔎 Tracking #WebShells in the Wild! 🔎 A list of known #Webshells actively leveraged by #cybercriminals. 📂 Valuable reference for #CyberSecurity researchers & defenders. ➡️ hxxps://gist.github[.]com/sbnsec/352128ea5bd8c95f48d748d5f25e3639 #ThreatIntel #Infosec
![cyberfeeddigest's tweet image. 🔎 Tracking #WebShells in the Wild! 🔎
A list of known #Webshells actively leveraged by #cybercriminals.
📂 Valuable reference for #CyberSecurity researchers & defenders.
➡️ hxxps://gist.github[.]com/sbnsec/352128ea5bd8c95f48d748d5f25e3639
#ThreatIntel #Infosec](https://pbs.twimg.com/media/Gz0hojqWcAALT9w.jpg)
🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells] El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás. 💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware REF: bleepingcomputer.com/news/security/…
![1ZRR4H's tweet image. 🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells]
El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás.
💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware
REF: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/FDilIbKWYAoQvl3.png)
![1ZRR4H's tweet image. 🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells]
El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás.
💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware
REF: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/FDikIJyWUAY4Toh.png)
🔎 Tracking #WebShells in the Wild! 🔎 A list of known #Webshells actively leveraged by #cybercriminals. 📂 Valuable reference for #CyberSecurity researchers & defenders. ➡️ hxxps://gist.github[.]com/sbnsec/352128ea5bd8c95f48d748d5f25e3639 #ThreatIntel #Infosec
![cyberfeeddigest's tweet image. 🔎 Tracking #WebShells in the Wild! 🔎
A list of known #Webshells actively leveraged by #cybercriminals.
📂 Valuable reference for #CyberSecurity researchers & defenders.
➡️ hxxps://gist.github[.]com/sbnsec/352128ea5bd8c95f48d748d5f25e3639
#ThreatIntel #Infosec](https://pbs.twimg.com/media/Gz0hojqWcAALT9w.jpg)
A misconfigured public PHP upload page on a Linux server allowed upload of obfuscated web shells and mailer scripts. Missing EDR, unpatched CVEs, and poor logging hindered detection. #WebShells #UploadSecurity #Varonis ift.tt/iKz7nAZ
Chinese-speaking APT group UAT-7237 targets Taiwan’s web servers using custom open-source tools like SoundBill, JuicyPotato, and Mimikatz to exploit vulnerabilities and maintain persistence via RDP and VPN. #UAT7237 #Taiwan #WebShells ift.tt/Ln18SG2
📌 Webshells evade detection with strong features and encryption. These malicious scripts allow unauthorized remote access to web servers. #CyberSecurity #Webshells tinyurl.com/2bbw35x9

Malicious web shells pose a persistent threat, exploiting server vulnerabilities for unauthorized access. A zero-trust environment and tools like file integrity monitoring are critical in detecting and mitigating these threats. #Cybersecurity #WebShells fedtechmagazine.com/article/2024/0…
fedtechmagazine.com
How to Detect and Remove Threatening Web Shells
Secretly planted scripts allow entry to malicious actors at a later date. Here’s how to detect and remove them.
#Wshlient A Simple Tool To Interact With #WebShells And Command Injection Vulnerabilities kitploit.com/2025/04/wshlie…
A new critical vulnerability in SAP NetWeaver (CVE-2025-31324) allows threat actors to upload JSP web shells, risking unauthorized access to systems, especially in government and enterprise sectors. 🚨 #SAPSecurity #WebShells #USA link: ift.tt/s6Gt8m1

Similar #Webshells found with 0 Detection ratio ☣️47e3a2efc95263265df226fc6c7b50d4 ☣️92d50706e8d050aa9ff372fdf51883d7 ☣️7abe3fcbdb64af014228bf1f76fa5cc0 ☣️b7b1e65123d3cb6cc105204fa2ee7118


🔐 A Silent Shell Among the Safe Ones? 🕵️♂️🖼️ Visit Us : nixtree.com/cpanel-server-… #CyberSecurity #WebShells #LinuxSecurity #Nixtree #ServerSecurity #SecureUploads #WebHostingSecurity #HostingExperts #FileUploadSecurity #MIMEFiltering #ShellDetection #ThreatPrevention

🚨 #Opendir Alert: Potential #Webshells Exposed! 🚨 🔹 Examples: b374k.txt, c99.php, c99shell.php, neoz.php, r57.txt, phpshell.rar 🔹 Link: server[.]xcode[.]co[.]id/files/phpshell/ 🔹 Warning: Handle with caution—potential webshells! 🔹 Good Source for: #Malware analysts &…
![cyberfeeddigest's tweet image. 🚨 #Opendir Alert: Potential #Webshells Exposed! 🚨
🔹 Examples: b374k.txt, c99.php, c99shell.php, neoz.php, r57.txt, phpshell.rar
🔹 Link: server[.]xcode[.]co[.]id/files/phpshell/
🔹 Warning: Handle with caution—potential webshells!
🔹 Good Source for: #Malware analysts &…](https://pbs.twimg.com/media/GnT1VvkXAAANuI2.jpg)
A sophisticated cyberattack by the China-linked group Weaver Ant targeted a major Asian telecom, employing advanced web shell techniques for persistent access and evasion. 🕵️♂️🔒 #China #CyberEspionage #WebShells link: ift.tt/tCTbZia

The Lazarus Group has breached IIS web servers, deploying web shells and advanced tactics for a multi-stage attack, including LazarLoader malware and obfuscation techniques. 🚨 #LazarusGroup #NorthKorea #WebShells link: ift.tt/JFRVjBr

Malicious actors plant #WebShells in networks to create access points for later use. Here’s how to guard against it: biztechmagazine.com/article/2025/0…

.@CISAgov released an emergency directive on #WebShells earlier this year. Here’s what #StateGov and #LocalGov agencies should know: statetechmagazine.com/article/2024/0…

🚨 Chinese hackers exploit critical vulnerabilities in Ivanti CSA 4.6, enabling remote code execution and SQL injection. Persistent webshells hint at sophisticated attack strategies. 📊 #Ivanti #China #Webshells link: ift.tt/3LSthPF

What are malicious #WebShells, and what are the steps you need to take to protect your business from this increasingly popular #cyberattack? biztechmagazine.com/article/2025/0…

Exploitation of Ivanti CSA vulnerabilities, notably CVE-2024-8963, has led to widespread webshell deployments across sectors like healthcare and finance. Insightful analysis highlights tactics used by threat actors. 🔍 #Ivanti #Webshells link: ift.tt/HIRoblP

Once again #Emotet changed their #Webshells, providing minor modifications such as the title (#fsociety), password and comments. Source IP addresses accessing them to update the payloads and grep commands to identify those files have been updated on my Github @Cryptolaemus1

#opendir #webshells #qbot hxxp://samsung-drivers[.]xyz app.any.run/tasks/4c84dfe9… @James_inthe_box @JAMESWT_MHT
![jstrosch's tweet image. #opendir #webshells #qbot
hxxp://samsung-drivers[.]xyz
app.any.run/tasks/4c84dfe9…
@James_inthe_box @JAMESWT_MHT](https://pbs.twimg.com/media/EwFNbgpWgAsOkzs.jpg)
![jstrosch's tweet image. #opendir #webshells #qbot
hxxp://samsung-drivers[.]xyz
app.any.run/tasks/4c84dfe9…
@James_inthe_box @JAMESWT_MHT](https://pbs.twimg.com/media/EwFNcAQXEAAbTVg.jpg)
Banco en Latinoamérica lleva más de 1 mes comprometido vía #ProxyLogon CVE-2021-26855. Es demasiada negligencia! simplemente algunas organizaciones no estan preparadas o no son conscientes del riesgo y la evolución constante de las ciberamenazas, CUIDADO. #backdoors #webshells

Remote access #Trojans (#RATs), #WebShells and #Mimikatz among the top publicly available tools that are used in #CyberAttacks around the world, a five-nation #CyberIntelligence report reveals bit.ly/2NFooUu

Banco Pichincha Hacked ~ Threat Actor: Hotarus Corp #Webshells #DataLeak #Extorsion



🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells] El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás. 💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware REF: bleepingcomputer.com/news/security/…
![1ZRR4H's tweet image. 🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells]
El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás.
💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware
REF: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/FDilIbKWYAoQvl3.png)
![1ZRR4H's tweet image. 🚨 Sitios del gobierno mexicano 🇲🇽 comprometidos vía #ProxyShell [2021-11-06 - LIVE #Webshells]
El sitio de la Secretaría de Seguridad del Estado fue reportado hace 77 días atrás.
💡 Exploit ha sido utilizado por Conti, LockFile y Babuk #Ransomware
REF: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/FDikIJyWUAY4Toh.png)
WSO2 - CVE-2022-29464 🚨 Unrestricted File Upload lead to RCE 1ra ronda de explotación inicio el 21 de Abril con la instalación masiva de #webshells como backdoor. Al menos 212 servidores en el mundo ya están comprometidos (última imagen con el TOP 25 servidores por país).




#phishing #webshells //milangroupinternational[.]com/wp-content/uploads/ Phishing using Excel sheet login and another for DHL @DHLUS @PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXuqzX4AAelY-.png)
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXvgYWkAEDDHS.jpg)
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXwLaW4AAeI-g.png)
![Jouliok's tweet image. #phishing #webshells
//milangroupinternational[.]com/wp-content/uploads/
Phishing using Excel sheet login and another for DHL @DHLUS
@PhishKitTracker @PhishingAi @ActorExpose @dave_daves @Spam404Online](https://pbs.twimg.com/media/D9VXw4eX4AIffpC.jpg)
several base64 encoded #webshells - retrieved via php file_get_contents/base64_decode: pastebin.com/raw/zUb7iayg pastebin.com/raw/6DuKx17b pastebin.com/raw/NE6MLDK7 pastebin.com/raw/nvZCFqKf pastebin.com/raw/d2Ti4xg9 #opendir #mailer: hxxps://a-mla.org/images/acts/

Looking forward to talking #WebSecurity #Malware #Webshells in #Seoul #first2016 today at 2:00. @RecordedFuture

Again! This one is a real mess... @auspost and @Israelpost2022 #phishing kits as PHP #webshells #phishingkit #webshell #soc #cybersecurity #scam #stalkphish #opendir

Malware en sitio ganar-dinero-hoy.com Listado de subdominios comprometidos + nombres de Webshell's para los diccionarios ;) -> pastebin.com/RpSeuTvB cc: @0x5061746f #opendir #webshells #malware #payloads


#opendir open #webshells #mailers #phishing @netflix hxxp://laravel.rfinderpro.[net]/vendor/phpunit/phpunit/src/Util/PHP/ @James_inthe_box
![jstrosch's tweet image. #opendir open #webshells #mailers #phishing @netflix
hxxp://laravel.rfinderpro.[net]/vendor/phpunit/phpunit/src/Util/PHP/
@James_inthe_box](https://pbs.twimg.com/media/Ea4ugRYWAAcilz4.png)
![jstrosch's tweet image. #opendir open #webshells #mailers #phishing @netflix
hxxp://laravel.rfinderpro.[net]/vendor/phpunit/phpunit/src/Util/PHP/
@James_inthe_box](https://pbs.twimg.com/media/Ea4uhjqXQAA3e8o.png)
![jstrosch's tweet image. #opendir open #webshells #mailers #phishing @netflix
hxxp://laravel.rfinderpro.[net]/vendor/phpunit/phpunit/src/Util/PHP/
@James_inthe_box](https://pbs.twimg.com/media/Ea4uif3WoAAgE8O.jpg)
Know thy #webshells and may your #hunting prove productive! github.com/fengchenzxc/fe… #MondayMotivaton #Malware #infosec #cybersecurity #DFIR #ThreatHunting #threatintel #riskmanagement #chinachopper #cknife #antsword #behinder #xise #altman #weevely #quasibot #sniper #manager

In my experience #webshells are the most overlooked risk topic in the #CISO community. Being that #SharePoint is beloved by enterprises, this #CVE 2019-0604 is a great opportunity to explain adversary web shell placement and usage tactics. #vulnerabilities @RecordedFuture



Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWDynamite 10.9K posts
- 2. #Survivor49 2,078 posts
- 3. #SistasOnBET N/A
- 4. #iubb 1,126 posts
- 5. Athena 10.8K posts
- 6. #ALLCAPS 1,179 posts
- 7. Binnington 1,100 posts
- 8. Savannah 4,994 posts
- 9. Ovechkin 4,871 posts
- 10. Godzilla 27.3K posts
- 11. Harley 11.6K posts
- 12. Mitchell Robinson N/A
- 13. Claudio 50.2K posts
- 14. Lamar Wilkerson N/A
- 15. Unplanned 3,624 posts
- 16. Paige 28.4K posts
- 17. Randle 2,839 posts
- 18. Cade 27.5K posts
- 19. Breeze 24.5K posts
- 20. Rickea N/A





![JaromirHorejsi's tweet image. #hacked website with #malware and #webshells
https://imskolkata.]]]org/journal/journal_doc/](https://pbs.twimg.com/media/DdYZJOAXUAA-6Gl.jpg)