#exploitdev 検索結果
CVE-2025-52915 assigned - my first vulnerability!🥳 A classic BYOVD case: kernel driver with unrestricted process termination. Vendor coordination turned out more challenging than the exploit itself. Technical write-up: blacksnufkin.github.io/posts/BYOVD-CV… #ExploitDev #CVE #BYOVD #RedTeam
If you're exploiting a driver offering R/W access to physical memory on Win11 24H2, you can leverage this simple trick to circumvent kernel address leak restrictions and retrieve the kernel base address :p xacone.github.io/kaslr_leak_24h… #exploitdev #driverexploitation
🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
🇦🇺 Corelan hits Melbourne for the FIRST time! 💥 Stack Exploit Dev: Feb 3–6, 2026 🧨 Heap Masterclass: Feb 9–12, 2026 🎯 w/ @TantoSecurity 🧠 Real skills. No fluff. 💣 Come prepared. 🕐 Early bird ends Sept 2025 👉 bit.ly/corelan-traini… #Corelan #ExploitDev
🚨 Released a full SEH exploit chain for DeepFreeze 8! With custom shellcode and ROP chain. Software was fully reversed, and an SEH vuln discovered studying for the #OSED 💪Blog write-up coming soon.🔍github.com/snowcra5h/Faro… #CyberSecurity #ExploitDev
Happy New Year 2025! #infosec #CyberSec #ExploitDev #Hacker #Bug #bugbountyhunter #vulnerabilityResearcher #ReverseEngineering #Binex

This should be the final set of labs published publicly. That's all folks for now... #RE #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com



Pwning LLaMA.cpp RPC Server #LLAMACpp #RPCServer #ExploitDev #CTF pwner.gg/2024/10/03/lla…
Privilege escalation isn't always about the shell. Kernel memory leaks can offer direct paths to root access. Details: versprite.com/blog/the-shell… #PrivilegeEscalation #LinuxSecurity #ExploitDev
All the Assembly and #RE labs have now been shared. I just need to find the reference to the Crackme(s) I used and then it should be 100% complete. #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com

🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
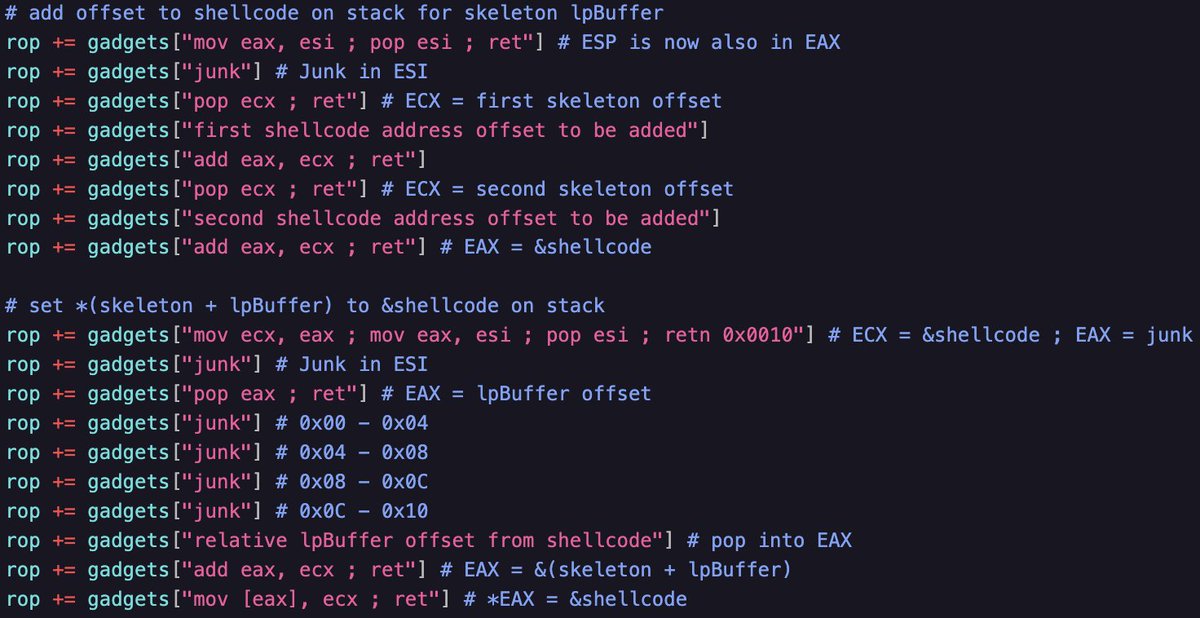
Hand-crafted ROP chain 🛠️! Had limited gadgets, so I used an IAT entry for HeapAlloc and calculated the VirtualAllocStub RVA offset. Got creative without ASLR and possibly should've used a read primitive. Details in the gist! #ROP #ExploitDev #osed gist.githubusercontent.com/snowcra5h/a7c1…

💻 Go-exploit A Go-based exploit framework for creating compact, portable, and uniform exploits, with minimal dependencies and cross-compilation capabilities By VulnCheck's @Junior_Baines et al #infosec #exploitdev github.com/vulncheck-oss/…
I’m happy to announce that I passed OSED from @offsectraining 😍😍 I just got the email and man IT FELT SO GOOD #CyberSecurity #exploitdev

Important note to those new to this account. The course below is completely FREE. I know someone (maybe more) has ripped the videos & probably now the labs & is selling them on @udemy. Please do not pay for this course, it is FREE! #ExploitDev #Offsec exploitation.ashemery.com
This week was the last public class of 2023, we’re already filling up the agenda for 2024. However, we still have some timeslots for private classes. (either at your company or in Belgium, for small groups). Interested? DM for info! #corelan #exploitdev #windows11 #stack #heap

Exploiting Ghostscript? Achieve SAFER sandbox bypass! 🛡️ Dive into CVE 2024–29510—because your PDFs should never betray you. Ready to test your mettle? 🔍 #CyberSecurity #ExploitDev packetstormsecurity.com/files/179645/g…
New whitepaper: Polymorphic shellcode bypasses on modern architectures—evasion techniques, detection gaps, and practical defenses. Read: github.com/MottaSec/White… #SecurityResearch #ExploitDev #BlueTeam
CVE-2025-52915 assigned - my first vulnerability!🥳 A classic BYOVD case: kernel driver with unrestricted process termination. Vendor coordination turned out more challenging than the exploit itself. Technical write-up: blacksnufkin.github.io/posts/BYOVD-CV… #ExploitDev #CVE #BYOVD #RedTeam
Privilege escalation isn't always about the shell. Kernel memory leaks can offer direct paths to root access. Details: versprite.com/blog/the-shell… #PrivilegeEscalation #LinuxSecurity #ExploitDev
NEW: Digital Demonology Grimoire - A dark exploration into buffer overflow exploitation & shellcode analysis Perfect reading for👹 github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #Shellcode #BufferOverflow #InfoSec #HackTheGibson
"Those who gaze into the assembler, take care that the assembler does not gaze also into them." The silicon souls whisper their secrets... github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #DigitalDemonology
We dissect a DFG compiler bug we discovered in Safari/WebKit. This post covers root cause, impact, and technical analysis: blog.exodusintel.com/2025/08/04/oop… #WebKit #VulnerabilityResearch #ExploitDev #Safari #CyberSecurity #ExodusIntel
🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
🇦🇺 Corelan hits Melbourne for the FIRST time! 💥 Stack Exploit Dev: Feb 3–6, 2026 🧨 Heap Masterclass: Feb 9–12, 2026 🎯 w/ @TantoSecurity 🧠 Real skills. No fluff. 💣 Come prepared. 🕐 Early bird ends Sept 2025 👉 bit.ly/corelan-traini… #Corelan #ExploitDev
🇦🇺 Corelan hits Melbourne for the FIRST time! 💥 Stack Exploit Dev: Feb 3–6, 2026 🧨 Heap Masterclass: Feb 9–12, 2026 🎯 w/ @TantoSecurity 🧠 Real skills. No fluff. 💣 Come prepared. 🕐 Early bird ends Sept 2025 👉 bit.ly/corelan-traini… #Corelan #ExploitDev
Built my own 64-bit ELF packer — something I always wanted to try. XOR encrypts the .text section with a dynamic key and injects a custom stub in new PT_LOAD segment github.com/0x3xploit/entr… #Linux #ELF #Exploitdev #ReverseEngineering #RedTeam #BinaryAnalysis #infosec



8. 🔥 Maddie Stone Google Project Zero star. Finds zero-days in Android and the wild. Her writeups are art. Keeps pressure on vendors to fix fast. A bug-hunting sniper for the common good. #exploitdev #zeroday
If you're exploiting a driver offering R/W access to physical memory on Win11 24H2, you can leverage this simple trick to circumvent kernel address leak restrictions and retrieve the kernel base address :p xacone.github.io/kaslr_leak_24h… #exploitdev #driverexploitation
🇧🇪 Belgian Roots. Global Impact. 🌍 Corelan delivers world-class exploit dev training for Windows: 🔹 Stack Smashing 🔹 Heap Masterclass Built in Europe. Respected worldwide. Sign up 👉 bit.ly/corelan-traini… #CyberSecurity #ExploitDev #MadeInBelgium
🇧🇪 Belgian Roots. Global Impact. 🌍 Corelan delivers world-class exploit dev training for Windows: 🔹 Stack Smashing 🔹 Heap Masterclass Built in Europe. Respected worldwide. Sign up 👉 bit.ly/corelan-traini… #CyberSecurity #ExploitDev #MadeInBelgium
Happy New Year 2025! #infosec #CyberSec #ExploitDev #Hacker #Bug #bugbountyhunter #vulnerabilityResearcher #ReverseEngineering #Binex

It's truly beautiful.🥹Avoiding bad characters, compensating for limited gadgets. It's like crafting a piece of art🎨. Challenges like this make the #OSED so rewarding!💪Got any tricks up your sleeve? Share them with me. Friday is exam day. #ExploitDev #ArtInCode #infosecurity
I’m happy to announce that I passed OSED from @offsectraining 😍😍 I just got the email and man IT FELT SO GOOD #CyberSecurity #exploitdev

Mastering buffer overflows in Vulnserver is essential for exploit development. WinDBG aids in debugging vulnerabilities by controlling EIP and generating shellcode. A must-learn for secure environments! 🔍⚙️ #ExploitDev #BufferOverflow link: ift.tt/fFk6AGK

Hand-crafted ROP chain 🛠️! Had limited gadgets, so I used an IAT entry for HeapAlloc and calculated the VirtualAllocStub RVA offset. Got creative without ASLR and possibly should've used a read primitive. Details in the gist! #ROP #ExploitDev #osed gist.githubusercontent.com/snowcra5h/a7c1…

This should be the final set of labs published publicly. That's all folks for now... #RE #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com



Education is power! corelan-training.com/index.php/trai… #nevergiveup #exploitdev #windows11 #stack #heap @corelanc0d3r

All the Assembly and #RE labs have now been shared. I just need to find the reference to the Crackme(s) I used and then it should be 100% complete. #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com

The whole course, labs, videos, etc can be found below. #Cybersecurity #Offsec #ExploitDev #Debugging #Reversing exploitation.ashemery.com

Bypassing PIE with partial overwrite? 🔥 Instead of guessing full addresses, just overwrite specific bytes to align with predictable offsets. Precision > brute force. A reminder that security evolves, and so must we. 🛡️ #CyberSecurity #ExploitDev #ReverseEngineering


I really enjoy teaching private classes! Even if you're just a small group (min. 4), willing to travel to Belgium, we can make it happen! I still have some timeslots in November & December. DM if interested @corelanconsult #windows #exploitdev #corelan #nevergiveup

Built my own 64-bit ELF packer — something I always wanted to try. XOR encrypts the .text section with a dynamic key and injects a custom stub in new PT_LOAD segment github.com/0x3xploit/entr… #Linux #ELF #Exploitdev #ReverseEngineering #RedTeam #BinaryAnalysis #infosec



Think kernel bugs are too deep to reach? Think again. 🔥 At #NullconBerlin2025, dive headfirst into a hands-on Linux kernel exploitation with security researcher Andrey Konovalov — no prior kernel knowledge required. Know More: nullcon.net/berlin-2025/tr… #LinuxKernel #ExploitDev

🧠 Heap exploits today = brains > brute force. Leaks, UAFs, type confusion—APT-level tactics. Is your defense still stuck in 2015? 👇 What’s your go-to heap hardening move? #CyberSecurity #ExploitDev 👉️ sec.co/blog/modern-he…

Interested in Software Exploitation? This course is for you and will take you from knowing nothing, to understanding how exploits work and how to write them... I hope it will be useful to someone out there! #Offsec #Cybersecurity #ExploitDev #Debugging youtube.com/watch?v=5GGyFb…

This week was the last public class of 2023, we’re already filling up the agenda for 2024. However, we still have some timeslots for private classes. (either at your company or in Belgium, for small groups). Interested? DM for info! #corelan #exploitdev #windows11 #stack #heap

ONE more chance this year to take our popular Bootcamp. High-quality materials, real class, real instructor (AND the perfect prep for our heap exploitation class). Seats are selling fast! What are you waiting for? deep-conference.com/predeep-bootca… #corelan#windows11 #exploitdev

Officially #OSED certified! I've conquered the Windows User Mode Exploit Development exam and earned the Offensive Security Exploit Developer (OSED) certification. Huge thanks to @offsectraining! #ExploitDev #ReverseEngineering #TryHarder

And we did it ! 🙌🏽 We brought the great @corelanc0d3r to teach a master class of exploit development for the first time in Brazil and Latin America. 😎 Many thx Peter for this amazing experience. #exploitdev #redteam #gohacking #corelan #cyber


Something went wrong.
Something went wrong.
United States Trends
- 1. #FanCashDropPromotion N/A
- 2. Good Friday 60.4K posts
- 3. Reagan 86.4K posts
- 4. #FridayVibes 4,421 posts
- 5. Happy Friyay 1,381 posts
- 6. Core CPI 3,988 posts
- 7. RED Friday 2,387 posts
- 8. #FridayMotivation 3,034 posts
- 9. Finally Friday 5,516 posts
- 10. #FridayFeeling 2,282 posts
- 11. U-Haul 7,219 posts
- 12. #fridaymorning 1,293 posts
- 13. ORM CENTRAL CHIDLOM ANN 642K posts
- 14. September CPI 3,517 posts
- 15. Oval Office 19.2K posts
- 16. Ontario 65.9K posts
- 17. Doug Ford 19.4K posts
- 18. Chelsea Clinton 9,287 posts
- 19. Lover Girl 37.1K posts
- 20. Aaron Gordon 34.8K posts