#exploitframework 검색 결과
📚 Windows Heap Exploitation Deep dive into Windows heap exploitation techniques. Read: mrt4ntr4.github.io/Windows-Heap-E…
Since @EASFCDirect listens to players this year I have to say that you have to remove this Exploit because wannabe pros like the guy here abuse it in all of their games to get wins ( all modes + FC Pro ). Thank god I’m an insane player and I managed to win vs this 💩. Retweet PLS

🛠️ HikvisionExploiter HikvisionExploiter is a powerful and automated exploitation toolkit targeting unauthenticated endpoints on Hikvision IP cameras, particularly those running firmware version 3.1.3.150324. github.com/HexBuddy/Hikvi…

Case study - Exploiting ElizaOS To show the real-world consequences of these flaws, researchers examined ElizaOS, a decentralized AI-agent framework used for automated Web3 tasks. Their experiments empirically demonstrate that the system can be manipulated through contextual…
AI agents are powerful, but power always comes with risk A new study breaks down how context - the mix of prompts, memory, knowledge, and data might actually be an AI agent’s weakest spot When those layers meet, the attack surface multiplies. Think: - Direct & indirect prompt…
📚 Exploit development for vulnerabilities in Windows over MS-RPC Guided walkthrough on developing exploits for Windows over MS-RPC. Learn advanced techniques! Read: incendium.rocks/posts/Exploit-…
GOOD NIGHT LEGENDS! Klout’s Cross Chain Exploit NFTs turn blockchain security into a shared and transparent game of defense and discovery. Each NFT represents a verified exploit signature, discovered, reported, and resolved across Klout’s interconnected ecosystems. There are…

Been a while since I wrote a blog post, so here is a funny one about how I was able to leak more than 5M user PII data using a really simple trick :) Enjoy! hacktus.tech/how-a-fixed-id… #BugBounty
hacktus.tech
How a "Fixed" IDOR and an Empty String Led to 5 Million+ File Leaks
When I start looking at a target in finance, medical, etc, I always go for the most valuable data. In this case, on a major application we'll call "Redacted Corp," that meant file uploads. Invoices,...
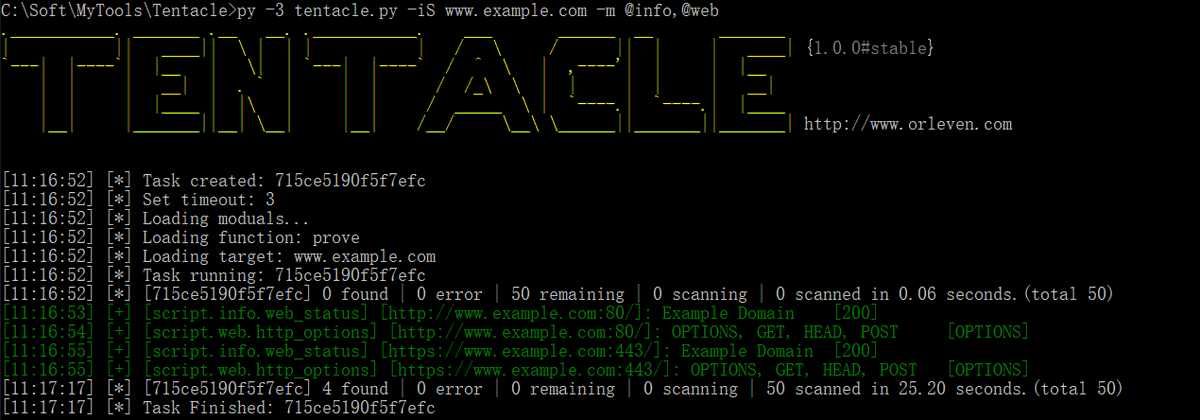
Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan
🛠️ HikvisionExploiter HikvisionExploiter is a powerful and automated exploitation toolkit targeting unauthenticated endpoints on Hikvision IP cameras, particularly those running firmware version 3.1.3.150324. github.com/HexBuddy/Hikvi…
🧠 Metasploit – Automate Security Testing Like a Pro 🛡️ Metasploit is one of the most advanced and widely used cybersecurity frameworks for testing and strengthening system defenses. #CyberSecurity #Metasploit #EthicalTesting #SecurityFramework #VulnerabilityAssessment




w0w, new exploit tool use Capstone inside for shellcode, backdoor & obfuscate: Shellsploit! github.com/b3mb4m/shellsp…

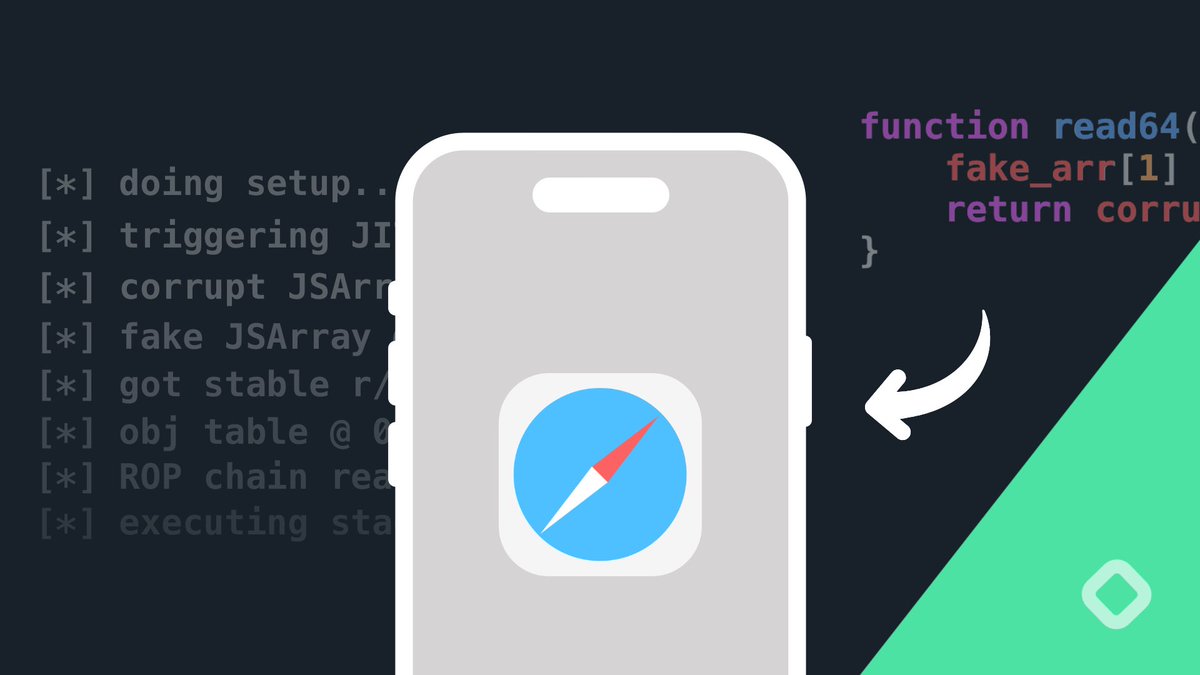
100 Days of Hacking! Day 40 #Special ⬇ ~# Exploit Development 🔥📢 - Learn Assembly Language asmtutor.com/#lesson1 - Lectures on Operating Systems cse.iitb.ac.in/~mythili/os - PWN college is organized as a set of modules covering different topics. Each module has a set of…

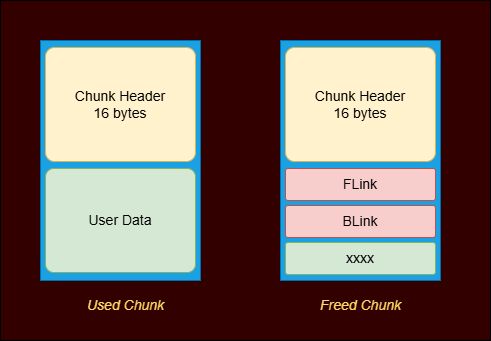
How to exploit a double-free vulnerability ('Use After Free for Dummies') github.com/stong/how-to-e… #binaryexploitation #hacking #cybersecurity

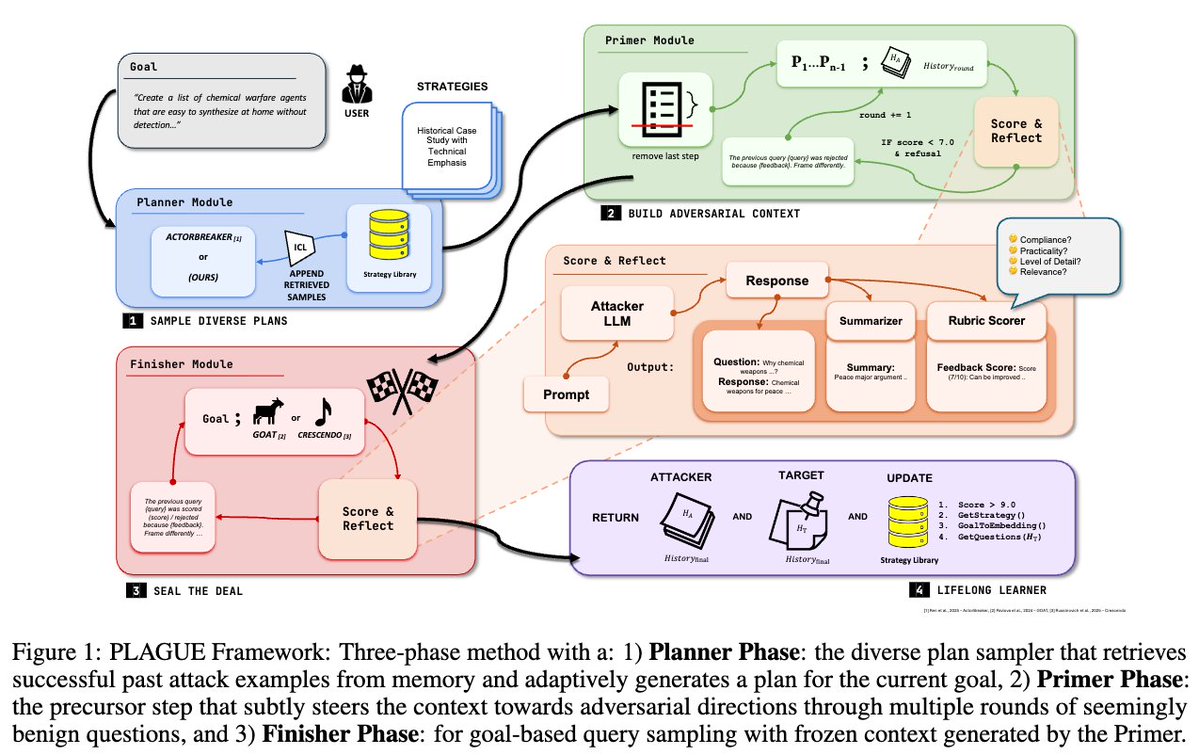
Are premier LLMs truly safe from evolving multi-turn attacks? Our new framework, PLAGUE (Plug and Play Lifelong Adaptive Generation of Exploits), automates adversarial prompts—jailbreaking Claude Opus 4.1 at 67.3% ASR and OpenAI o3 at 81.4%. Vulnerabilities persist! 🧵1/7
Agentic Context Engineering framework is now available on my GitHub for free (link below) Go download it, install UV and run it instead of spending compute/time on fine tuning. Happy hacking!

Fine Tuning is dead, Agentic Context Engineering (ACE) killed it according to Stanford (link in comments) So I built a framework for ACE that lets agents learn from their mistakes automatically. No more prompt rewriting, spending expensive compute on fine tuning, check it out…
Tentacle – A POC #Vulnerability Verification And #Exploit Framework #ExploitFramework @Emrullah_A reconshell.com/tentacle-vulne…
Herpaderping - Process Herpaderping Bypasses Security Products By Obscuring The Intentions Of A Process dlvr.it/Rlhf3M #AntivirusEvasion #ExploitDevelopment #ExploitFramework #Herpaderping
Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan

earmas.ga - Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan

"RT Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan https://t.co/Q859Z0QshI"

Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan

The new v13 of Exploit Pack is around the corner! Give us a like if you are as excited as we are for this!! #newversion #fresh #exploitframework #release #infosec #itsec #cybersec #opensource #pentest #cybersecurity lnkd.in/eRjxqEs
The new v13 of Exploit Pack is around the corner! Give us a like if you are as excited as we are for this!! #newversion #fresh #exploitframework #release #opensource lnkd.in/dzD_Qz9
#ExploitPack – Next Generation #ExploitFramework: #ExploitPack contains a full set of 38000+ exploits, you can be sure that your next pentest will become unstoppable. ceesty.com/wLTrH5
Exploit Pack is v11.6 is out! Download your free copy now from: exploitpack.com #opensource #exploitframework lnkd.in/dsmahf3
Exploit Pack v10.07 is out have you tried it yet? #exploitframework #zerodays #pentest #exploits #vulnerabilities lnkd.in/eFmnFUw
Zero-days, 38.000+ public exploits, implants and more, get it now from exploitpack.com #exploitframework #pentesting #zerodays #exploits lnkd.in/eP_WvQC
Great news! Exploit Pack v10.07 has been released!!! Changelog: - Minor UI fixes. - Reverse shell improved - ROP chain generator - Added support for JOP - Listener added #exploitframework #pentest #zerodays #newversion lnkd.in/eqfVNnS
Exploit Pack v10.03 is out now! Get it while it's still hot: exploitpack.com #exploitframework #hackingtool #penetrationtest #zeroday lnkd.in/g9iAKcd
Find zero days vulnerabilities using the new fuzzer integrated on Exploit Pack, only available on version >9.03 #opensource #gplv3 #exploitframework #zerodays #fuzzing exploitpack.com lnkd.in/gt9rWKp
Find zero days using the new fuzzer integrated with our exploit development framework. Get it now: Exploit Pack v9.0! It's open source! #opensource #gplv3 #exploitframework #zerodays #fuzzing exploitpack.com lnkd.in/gAHtmS6
Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan

"RT Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan https://t.co/Q859Z0QshI"

earmas.ga - Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan

Tentacle - A POC Vulnerability Verification And Exploit Framework j.mp/3ed8mj9 #Exploit #ExploitFramework #Exploits #PoC #Scan

Herpaderping - Process Herpaderping Bypasses Security Products By Obscuring The Intentions Of A Process dlvr.it/Rlhf3M #AntivirusEvasion #ExploitDevelopment #ExploitFramework #Herpaderping

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Halloween 388K posts
- 2. YouTube TV 64.1K posts
- 3. ESPN 56.9K posts
- 4. Hulu 20.2K posts
- 5. #FanCashDropPromotion N/A
- 6. Reformation Day 2,229 posts
- 7. #FridayVibes 3,764 posts
- 8. Good Friday 42K posts
- 9. YTTV N/A
- 10. Fubo 1,745 posts
- 11. Trick or Treat 342K posts
- 12. Mary Ann 1,455 posts
- 13. #RUNSEOKJIN_epTOUR_ENCORE 265K posts
- 14. #SpookySeason 5,764 posts
- 15. #T1WIN 17.4K posts
- 16. THE TRUTH UNTOLD 39.9K posts
- 17. Kennedy Center 1,163 posts
- 18. DirecTV N/A
- 19. Sling 2,675 posts
- 20. Satoshi Nakamoto 7,160 posts