#securesoftwaredevelopment 搜尋結果
buff.ly/1RDfOjO #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZlF1 #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Secure software development: Bad Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2ndrntw

Secure software development: Secure Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2sMP0Zu

Zapraszamy na nasze stoisko podczas @WTHConf Wstai II dowiedz się czym jest Cyberkomponent WOT. Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime


Sub-group discussion on #SecureSoftwareDevelopment #SecuringTheHuman by #InfoSecEvangelist(s) #OperationMFU Mae Fah Luang University

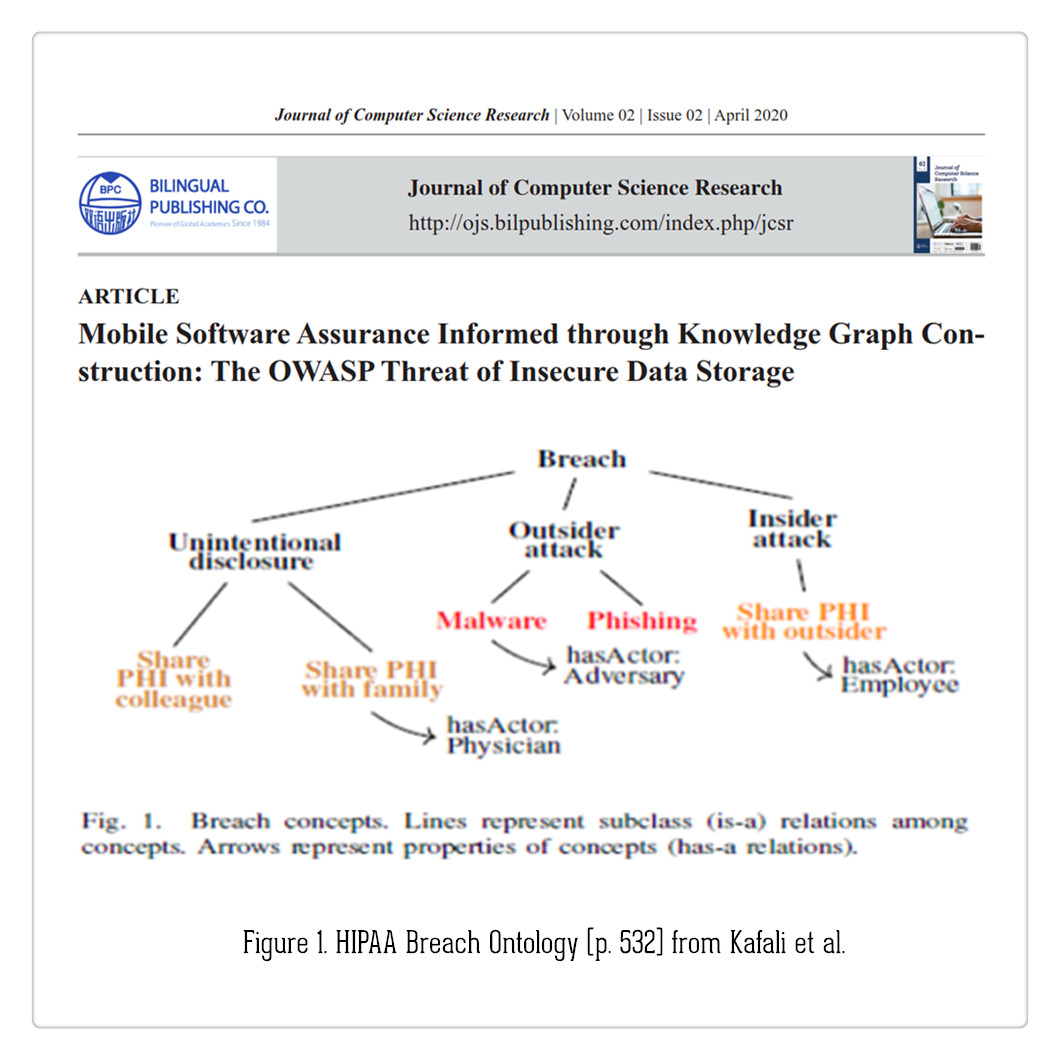
Mobile Software Assurance Informed through Knowledge Graph Construction: The OWASP Threat of Insecure Data Storage #Cybersecurity #Securesoftwaredevelopment #Penetrationtesting #Riskassessment DOI: doi.org/10.30564/jcsr.…
Nasz Cyberkomponent WOT wystawia się na @wthconf.pl. Tutaj znajdziecie więcej info nt Zespołu Działań Cyberprzestrzennych WOT: bit.ly/38C4zcd Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime

buff.ly/1RDfNMV #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZicp #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Chief Product Officer @BrianRocheBos and CTO & Founder @WeldPond continue their discussion on #AI and #securesoftwaredevelopment. Learn more here: bit.ly/3Hw33ew.
Is the #software you rely on daily developed securely? What does #securesoftwaredevelopment look like? Our CTO Brian Nadzan shares his insights Click here for access: hubs.la/Q01NxlFp0 #alternativeassets #privatemarkets #capitalmarkets #SaaS

→ Solutions that enable the hybrid cloud approach will continue to drive this simplification and adoption. This means the hybrid cloud architecture will become the mainstream in larger enterprises. realware.com #DigitalTransformation #securesoftwaredevelopment

buff.ly/1UtZicz #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

buff.ly/1RDfNMX #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

Join our SEC Business Webinar on June 23 and register here: r.sec-consult.com/secbusinessweb…. Security Expert Thomas Kerbl will speak about Secure Software Development from the perspective of the Security Requirements Engineer #infosec #securesoftwaredevelopment @Dementophobia

Know More 🌐 riseuplabs.com/secure-softwar… We secure software development includes enabling software security and maintaining software security and the underlying infrastructure. #riseuplabs #securesoftwaredesign #securesoftwaredevelopment

🧐 A tailored solution at off-the-shelf prices is better than sticking with a generic online SaaS platform, don't you think? 👉🏻 Learn more at share.realware.com/smartsaas-real… #Realware #RealwareDigitalTransformation #securesoftwaredevelopment #SmartSaaS

Secure Code Starts with Hiring! Organizations that hire developers with proven cybersecurity skills reduce risk, ensure compliance, and build long-term trust. Read the Blog: shorturl.at/pg9yO #CybersecuritySkills #DeveloperSecurity #SecureSoftwareDevelopment #RapidBrains

SBOM: The Blueprint for Secure Software! 🔒 🚀 Enroll in our Secure Software Development course at 👉 darkrelay.com/courses/secure… #CyberSecurity #SBOM #SecureSoftwareDevelopment #SupplyChainSecurity #SoftwareIntegrity #CyberDefense #InfoSec #StaySecure #InfoNews




医療データ分析と診断のための安全な AI 搭載早期検出システム - InfoQ #ArchitecturalExperimentation #AIHealthcare #SecureSoftwareDevelopment #PrivacyPreservingAI prompthub.info/99057/
prompthub.info
医療データ分析と診断のための安全な AI 搭載早期検出システム – InfoQ - プロンプトハブ
要約: 月次のアーキテクトまたはアスピリングアーキテクトが知っておく必要のある事柄についての概要 Ashish
クライアントアラート: ホワイトハウスの大統領令は連邦サイバーセキュリティの強化を目指す | Jenner & Block - JDSupra #CybersecurityStandards #BidenAdministration #SecureSoftwareDevelopment #FederalContractors prompthub.info/89086/
prompthub.info
クライアントアラート: ホワイトハウスの大統領令は連邦サイバーセキュリティの強化を目指す | Jenner & Block – JDSupra - プロンプトハブ
要約: 2025年1月16日、バイデン前大統領がサイバーセキュリティの強化と促進に関する大統領令を発行 大統領
進化するシフトレフトセキュリティ: ソフトウェア開発セキュリティへのより強力なアプローチ - DevOps.com #ShiftUpSecurity #SecureSoftwareDevelopment #ComprehensiveSecurityApproach #AutomatedSecurityTesting prompthub.info/88320/
prompthub.info
進化するシフトレフトセキュリティ: ソフトウェア開発セキュリティへのより強力なアプローチ – DevOps.com - プロンプトハブ
企業は、堅牢なセキュリティを維持しながら迅速なソフトウェアイノベーションを可能にする必要がある。 シフトレフト
中国ハッキングの脅威が高まる中、バイデン大統領はサイバーセキュリティ基準の強化を命じる - セキュリティ - iTnews #CyberSecurityStandards #SecureSoftwareDevelopment #ChinaCyberThreat #CybersecurityReforms prompthub.info/84764/
prompthub.info
中国ハッキングの脅威が高まる中、バイデン大統領はサイバーセキュリティ基準の強化を命じる – セキュリティ – iTnews - プロンプトハブ
バイデン米大統領は、新しい大統領令で、連邦機関や請負業者に対するサイバーセキュリティ基準を強化するよう呼びかけ
devops.com/cisa-pushes-st… The U.S. agency is continuing to urge businesses to take control of security in their software and product development processes. #cisa #cybersecurity #securesoftwaredevelopment
devops.com
CISA Pushes Steps to Better Secure Software and Product Designs - DevOps.com
The U.S. agency is continuing to urge businesses to take control of security in their software and product development processes.
I just published Building Secure Software with Tech Mind Developers link.medium.com/Wf1G7YE8jOb techminddevelopers.com #securesoftwaredevelopment #techminddevelopers #dataprotection #cybersecurity #softwaresecurity #encryption #safeandsecure #businessprotection #itsecurity

How SyanSoft Technologies Builds Secure Software Applications for Modern Enterprises In today's digital era, the security of #softwareapplications is more critical than ever. #SecureSoftwareDevelopment

That sounds quite compelling. So, welcome to the ever-evolving world of DevSecOps by downloading Sai Sravan's "SECURING THE CI/CD PIPELINE." Let the journey start here! #SecureSoftwareDevelopment #PrivacyByDesign #Compliance #RiskManagement

Check out the specifics of DevSecOps with the help of Sai Sravan's tutorial. Do not miss your chance – get a wealth of information and start using his knowledge right now! #SecureSoftwareDevelopment #PrivacyByDesign #Compliance #RiskManagement

Sai Sravan's thorough introduction to new professional endeavors or projects is a valuable resource for anyone interested in development. Strive for success that corresponds to the goal! #SecureSoftwareDevelopment #PrivacyByDesign #Compliance #RiskManagement

buff.ly/1RDfOjO #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZlF1 #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Zapraszamy na nasze stoisko podczas @WTHConf Wstai II dowiedz się czym jest Cyberkomponent WOT. Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime


Secure Code Starts with Hiring! Organizations that hire developers with proven cybersecurity skills reduce risk, ensure compliance, and build long-term trust. Read the Blog: shorturl.at/pg9yO #CybersecuritySkills #DeveloperSecurity #SecureSoftwareDevelopment #RapidBrains

Nasz Cyberkomponent WOT wystawia się na @wthconf.pl. Tutaj znajdziecie więcej info nt Zespołu Działań Cyberprzestrzennych WOT: bit.ly/38C4zcd Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime

Mobile Software Assurance Informed through Knowledge Graph Construction: The OWASP Threat of Insecure Data Storage #Cybersecurity #Securesoftwaredevelopment #Penetrationtesting #Riskassessment DOI: doi.org/10.30564/jcsr.…

buff.ly/1MuAxqg #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZlVM #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Secure software development: Bad Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2ndrntw

Secure software development: Secure Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2sMP0Zu

@ixtelme is presenting @Checkmarx #DevSecOps - A Faster, Less Bumpy Route. Find the quickest path to achieving a #securesoftwaredevelopment lifecycle (SDLC) by learning which of our AppSec solutions best fits your organization’s security goals. #cybersecurity

buff.ly/1RDfNMX #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZicz #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Designing and Developing Secure Software cisin.com/coffee-break/t… #SecureSoftwareDevelopment #SoftwareDevelopment #cisin #HireSoftwareDeveloper #SoftwareDevelopmentSecurity #Cyberattacks #softwaredevelopers

Developing Secure and Robust Software Solutions bit.ly/459PSKs #SecureSoftwareDevelopment #SecureSoftwareFrameworks #cisin #SoftwareDevelopment #SoftwareDevelopmentTeam

Know More 🌐 riseuplabs.com/secure-softwar… We secure software development includes enabling software security and maintaining software security and the underlying infrastructure. #riseuplabs #securesoftwaredesign #securesoftwaredevelopment

Is the #software you rely on daily developed securely? What does #securesoftwaredevelopment look like? Our CTO Brian Nadzan shares his insights Click here for access: hubs.la/Q01NxlFp0 #alternativeassets #privatemarkets #capitalmarkets #SaaS

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 73.7K posts
- 2. #heatedrivalry 25.5K posts
- 3. LeBron 107K posts
- 4. Gibbs 20.3K posts
- 5. Lions 91.7K posts
- 6. Pickens 14.6K posts
- 7. scott hunter 5,385 posts
- 8. fnaf 2 26.4K posts
- 9. Paramount 20.3K posts
- 10. Warner Bros 22K posts
- 11. Shang Tsung 30.2K posts
- 12. #OnePride 10.6K posts
- 13. Brandon Aubrey 7,412 posts
- 14. Ferguson 11K posts
- 15. #PowerForce N/A
- 16. Eberflus 2,684 posts
- 17. CeeDee 10.6K posts
- 18. #criticalrolespoilers 2,097 posts
- 19. Cary 39.8K posts
- 20. Goff 8,744 posts
























