#vulnerabilitytesting ผลการค้นหา
Vulnerability testing is key to spotting security gaps, but traditional methods often miss critical risks. Discover how to refine your exposure management strategy with advanced assessment tools and best practices: hubs.ly/Q03Hhfg80 #cybersecurity #vulnerabilitytesting

🛡️ Hackers won’t wait for you to fix your defenses. Run a basic pen test to find weaknesses before they do: 🔍 Recon 📡 Scan 💻 Exploit 🔗 Persist 📄 Report Proactive beats reactive. #CyberSecurity #TruehostTips #VulnerabilityTesting #SmallBusinessSecurity
Watch The Full video on youtube: youtu.be/o8735559WDs?si… #VAPT #VulnerabilityTesting #PenetrationTesting #Cybersecurity #RiskManagement
Think skipping vulnerability assessments is harmless? Think again! Unpatched weaknesses leave you wide open to attacks. Contact us today and stay secure. #Cybersecurity #VulnerabilityAssessment #VulnerabilityTesting
About 40% of cyber attacks come from people who has been exposed to the network. Through eavesdropping, insecurely entering passwords, less complex passwords being others #cybersecurity #vulnerabilitytesting #blackboxtesting #enterprise #startups

Watch The Full video on youtube: youtu.be/o8735559WDs?si… #VAPT #VulnerabilityTesting #PenetrationTesting #Cybersecurity #RiskManagement
The aim of this test is to exploit the vulnerabilities and gain access to sensitive data or take control of the system. bit.ly/3SEadlq #VAPT #cybersecurity #vulnerabilitytesting #itsecurity #itmanagement #GDPR #businessmanagementtools

S4E Introduction About Us 👉 securityforeveryone.com/about-us Free #cybersecurity Tools 👉securityforeveryone.com/tools/free-sec… Security for Everyone Blog 👉 securityforeveryone.com/blog Our Marketplace: 👉 securityforeveryone.com/marketplace #FreeCyberSecurity #Vulnerabilitytesting #Freetools #Vulnerability
Have you read our latest quarterly report yet? We take a deep dive into #cybersecurity at auDA including #vulnerabilitytesting, #redteamexercises and #scamsawareness. Find out more: auda.org.au/about-auda/cor… #DNS #domainnamesystem #ccTLD

Recently, Cross Gates Good Neighbours completed vulnerability testing with our student services team here at the NEBRC. Here is what David Smith, Volunteer and Trustee, had to feed back to the team. #CyberSecurity #VulnerabilityTesting

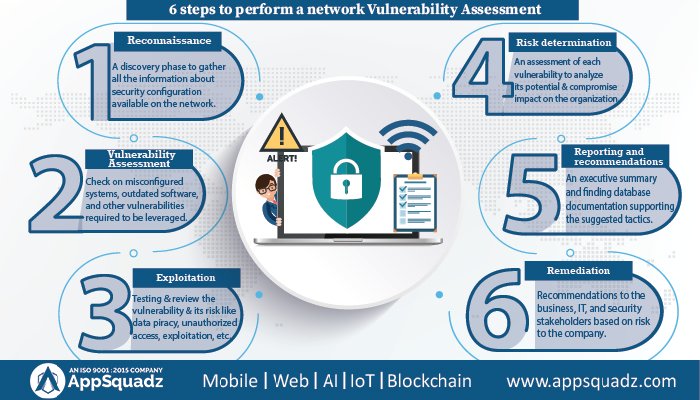
Through this infographic, learn 6 major steps to perform network Vulnerability and penetration testing. @appsquadz #vapt #vapttesting #vulnerabilitytesting #vaptservices
👉 What’s the need for #vulnerabilitytesting when your #developers follow secure development practices? 📌 Watch the impacts of improper #vulnerabilityanalysis: bit.ly/2OaUcGG #appsec #webapplications #manualpentest #webappscanning #apptrana #indusface
Vulnerability and penetration testing are both vital to your organization’s cybersecurity efforts. However, many people think they are the same. #VulnerabilityTesting #PenetrationTesting #Cybersecurity




👉 Know everything about how to do a comprehensive #vulnerabilitytesting - (link in thread) #softwarevulnerabilities #moveit #sqlinjection #cybersecurity #maliciousattacks #assetdiscovery #vulnerabilityscanning #was #pentesting #webapplicationscanning #apptrana #indusface

Own a business and want to safeguard it from cyber attacks? Here are some helpful tips, given by a professional Vulnerability Specialist. #EthicalHacking #VulnerabilityTesting #SMB #CyberSecurityTips zcu.io/Shf6

Read out the blog on what are the major advantages does penetration testing have over vulnerability testing? bit.ly/3z53N4L @appsquadz #vapt #vulnerabilitytesting #vaptservices #appsquadz #appdevelopmentcompany

Check out @kevinbeaver's step-by-step demonstration of how to use the @metasploit Framework for enterprise. #PenTesting #Metasploit #VulnerabilityTesting bit.ly/32Mo26m

👉 #vulnerabilitytesting evaluates the security of a system or an application to identify potential weaknesses or #vulnerabilities that malicious actors could exploit. For more details: (Link in thread) #cybersecurity #sqlinjection #penetrationtesting #apptrana #indusface

Think skipping vulnerability assessments is harmless? Think again! Unpatched weaknesses leave you wide open to attacks. Stay secure and learn more. #Cybersecurity #VulnerabilityAssessment #VulnerabilityTesting bit.ly/3LaW1hj

Our #SecurityTestingServices along with #Penetration & #VulnerabilityTesting that look beyond traditional #WebAapplicationSecurity considerations. More@ qainfotech.com/security-testi… #PenetrationTestingServices #WebSecurityTestingServices #AppSecurity #CyberSecurityExperts @QAInfoTech

Vulnerability testing is key to spotting security gaps, but traditional methods often miss critical risks. Discover how to refine your exposure management strategy with advanced assessment tools and best practices: hubs.ly/Q03Hhfg80 #cybersecurity #vulnerabilitytesting

#vulnerabilitytesting is for everyone. Contact us for help. standardusercyber.com/contact. #cyberpros

Regular audits and penetration tests help identify weaknesses in your data protection strategy, allowing for timely remediation. #SecurityAudit #DataProtection #VulnerabilityTesting

🛡️ Hackers won’t wait for you to fix your defenses. Run a basic pen test to find weaknesses before they do: 🔍 Recon 📡 Scan 💻 Exploit 🔗 Persist 📄 Report Proactive beats reactive. #CyberSecurity #TruehostTips #VulnerabilityTesting #SmallBusinessSecurity
🛡️ Before releasing a medical device, run a vulnerability test—catching issues early protects patients and your reputation. Proactive testing is key to quality and compliance. #MedicalDeviceSecurity #VulnerabilityTesting #QualityAssurance #NaveSecurity

Watch The Full video on youtube: youtu.be/o8735559WDs?si… #VAPT #VulnerabilityTesting #PenetrationTesting #Cybersecurity #RiskManagement
Watch The Full video on youtube: youtu.be/o8735559WDs?si… #VAPT #VulnerabilityTesting #PenetrationTesting #Cybersecurity #RiskManagement
🔒 At Fanan Limited, we believe in staying one step ahead. Regular vulnerability & penetration testing are key to safeguarding our data and customers. Stay secure, stay confident! #CyberSecurity #VulnerabilityTesting #FananLimited

Vulnerability Testing for AWS Deployments #Aws #Cloud #Vulnerabilitytesting plainenglish.io/blog/vulnerabi…
plainenglish.io
Vulnerability Testing for AWS Deployments
Vulnerability Testing for AWS Deployments
Vulnerability testing is key to spotting security gaps, but traditional methods often miss critical risks. Discover how to refine your exposure management strategy with advanced assessment tools and best practices: hubs.ly/Q03bvhmQ0 #cybersecurity #vulnerabilitytesting

💡 Tip for developers: Regularly test your open source AI models for vulnerabilities! The lack of standardized security protocols can leave your project exposed to cyber threats. #VulnerabilityTesting #SecureCoding
🔬Critical flaw in Illumina DNA sequencers puts sensitive genomic data at risk. Proactive testing is key to securing healthcare tech 🔒 Secure your systems with Delfence’s Vulnerability Assessments. Stay ahead of threats. #CyberSecurity #HealthcareIT #VulnerabilityTesting

Vulnerability testing is key to spotting security gaps, but traditional methods often miss critical risks. Discover how to refine your exposure management strategy with advanced assessment tools and best practices: hubs.ly/Q03Hhfg80 #cybersecurity #vulnerabilitytesting

#vulnerabilitytesting is for everyone. Contact us for help. standardusercyber.com/contact. #cyberpros

Check out @kevinbeaver's step-by-step demonstration of how to use the @metasploit Framework for enterprise. #PenTesting #Metasploit #VulnerabilityTesting bit.ly/32Mo26m

🛡️ Before releasing a medical device, run a vulnerability test—catching issues early protects patients and your reputation. Proactive testing is key to quality and compliance. #MedicalDeviceSecurity #VulnerabilityTesting #QualityAssurance #NaveSecurity

In computer security, a #vulnerability is a weakness which allows an attacker to reduce a system's information assurance. #computersecurity #vulnerabilitytesting #security #hacking

What is the Vulnerability Testing Process that Companies Should Follow >> hubs.ly/H0mpkgW0 via @appknox #Cybersecurity #VulnerabilityAssessment #VulnerabilityTesting #Infosec #CyberAware #VAPT #Pentest #defstar5 #makeyourownlane #Mpgvip #AI

The aim of this test is to exploit the vulnerabilities and gain access to sensitive data or take control of the system. bit.ly/3SEadlq #VAPT #cybersecurity #vulnerabilitytesting #itsecurity #itmanagement #GDPR #businessmanagementtools

Cybersecurity is important, but have you heard about vulnerability testing? 🤔 Stay tuned for our upcoming blog post on why vulnerability testing is crucial for protecting your digital assets. 🔔 #cybersecurity #vulnerabilitytesting #protectyourassets #digitalassets

Next week! We're back on @securityweekly technique demonstrations, binary code analysis, and a pop quiz! (Aren't you glad I gave you the heads up? 😉) @SecWeekly #threatanalysis #vulnerabilitytesting #binarycode #binaryanalysis #applicationsecurity #cyberdefense

Spritle Software just had an awesome knowledge-sharing session hosted by Karthik on Vulnerability Testing. 🛡️🔍 We delved into the world of identifying and addressing potential security weaknesses in our systems. #vulnerabilitytesting #cybersecurity #knowledgesharing #Spritle

Through this infographic, learn 6 major steps to perform network Vulnerability and penetration testing. @appsquadz #vapt #vapttesting #vulnerabilitytesting #vaptservices

👉 Know everything about how to do a comprehensive #vulnerabilitytesting - (link in thread) #softwarevulnerabilities #moveit #sqlinjection #cybersecurity #maliciousattacks #assetdiscovery #vulnerabilityscanning #was #pentesting #webapplicationscanning #apptrana #indusface

Take a proactive approach to thwarting cyber criminals... #securitytesting #vulnerabilitytesting #penetrationtesting #wirelesstesting #cybertesting #cybersecurity #CyberGuard ogl.co.uk/security-testi…

Vulnerability Testing vs Penetration Testing #vulnerabilitytesting #cybersecurity #securecoding #penetrationtesting #datasecurity #pentesting

Vulnerability Testing or Penetration Testing: Which one is perfect for maintaining IT security? A proactive cyber security plan includes both of them to ensure a foolproof strategy of minimizing online threats and building cyber resilience. #Vulnerabilitytesting #penetrationtest

Learn how to use the @metasploit Framework for #VulnerabilityTesting and #PenetrationTesting #Metasploit. Tutorial by @kevinbeaver. bit.ly/2Oa78dV

"While most organizations today have gone through some of the other forms of assessment (#VulnerabilityTesting, #PenetrationTesting, #ApplicationTesting) it is important to know if you as an organization are at the stage of exploring #RedTeaming." firecompass.com/blog/how-do-yo…

About 40% of cyber attacks come from people who has been exposed to the network. Through eavesdropping, insecurely entering passwords, less complex passwords being others #cybersecurity #vulnerabilitytesting #blackboxtesting #enterprise #startups

Recently, Cross Gates Good Neighbours completed vulnerability testing with our student services team here at the NEBRC. Here is what David Smith, Volunteer and Trustee, had to feed back to the team. #CyberSecurity #VulnerabilityTesting

Think skipping vulnerability assessments is harmless? Think again! Unpatched weaknesses leave you wide open to attacks. Stay secure and learn more. #Cybersecurity #VulnerabilityAssessment #VulnerabilityTesting bit.ly/3LaW1hj

Something went wrong.
Something went wrong.
United States Trends
- 1. phil 68.1K posts
- 2. phan 70.7K posts
- 3. Columbus 213K posts
- 4. President Trump 1.25M posts
- 5. Middle East 312K posts
- 6. Springer 11K posts
- 7. Gilbert 9,303 posts
- 8. Doug Eddings N/A
- 9. Kincaid 1,306 posts
- 10. Falcons 12.4K posts
- 11. Mike McCoy N/A
- 12. Yesavage 3,112 posts
- 13. Thanksgiving 58.9K posts
- 14. Martin Sheen 1,124 posts
- 15. Cam Talbot N/A
- 16. #LGRW 1,972 posts
- 17. Monday Night Football 6,313 posts
- 18. Brian Callahan 12.8K posts
- 19. Titans 35.6K posts
- 20. John Oliver 8,830 posts