#webappsecurity نتائج البحث
Just wrapped up talking about web app security for 4 hours and still not tired! The energy is real when you're passionate about what you do. 🔐💻 #WebAppSecurity #Cybersecurity

📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap


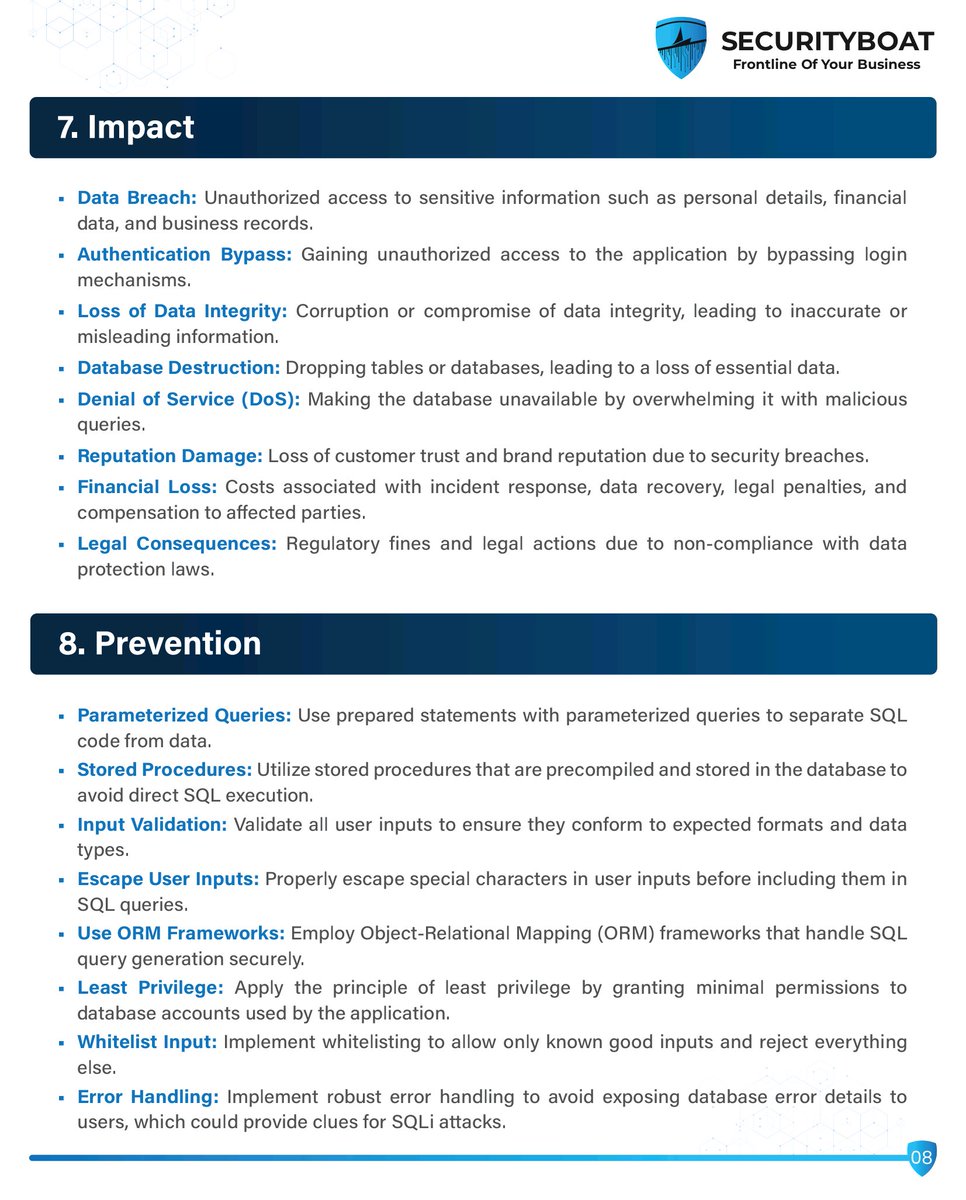
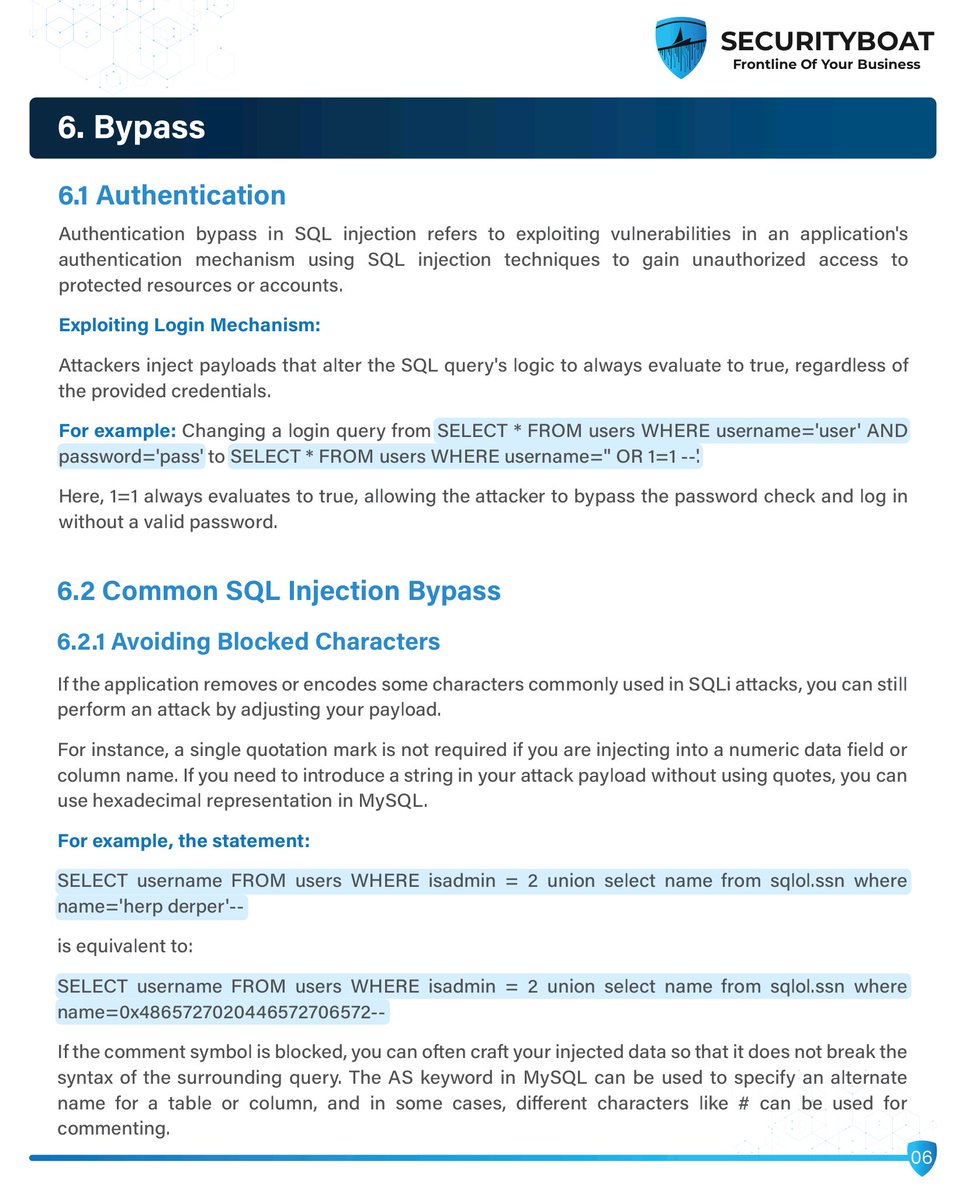
📋 Web Application Exploit Checklist: Lab-Based Testing for Common Vulnerabilities 💻🛠️ #WebAppSecurity #PenTestingChecklist #EthicalHacking #OWASPTop10 #CyberSecurityTraining #InfoSec #WebSecurity #EducationOnly #BugBounty #RedTeamReady


OWASP Web Application Security Risk #webappdevelopment #webapp #webappsecurity #webapplicationdevelopment #webapplicationsecurity #websecurity #infosec #informationsecurity

Most people ask how can backend developers enhance their server security...one of the method is jsonwebtokens.🔒 We use JSON Web Tokens (JWT) to protect user data and ensure a robust authentication system. A Thread..k #WebAppSecurity
🔒💻 How secure are your web apps? Ben and Jacob break down the sandboxing concept and download dangers on Big App Energy. Don't miss the full episode on making smarter app choices! 🎧👉🏻 podcasters.spotify.com/pod/show/big-a… #WebAppSecurity #BigAppEnergy #TechTips #CyberSafety
🚨 Hands-on Learning Lab. Zero filler. Real-world defense. Join Sofia Visciglia, CTO @ 911CYBER, in person on October 18th at the LAIC Summit for a deep dive: “Web Application Security: From Cloud to Code” RSVP now: laicsummit.com #WebAppSecurity #LAICSummit2025 #

Had the most awesome time previous weekend with @TheLaluka during his OffenSkill level 30 training. It is the best offensive web application security training ever and he is a great mentor with fantastic methodology. offenskill.com #webappsecurity #bugbounty

New video on my YouTube channel "Bike (HTB SP T1 walkthrough)"! youtu.be/45CcCjO0cNk?fe… #hackthebox #webappsecurity #cybersecuritytraining

Modern web apps shouldn’t make you choose between speed and security ⚡ Join us on Sept 18 for a live webinar where we’ll discuss how to secure web apps without sacrificing agility. Register now: bit.ly/3HSdLQc #DevSecOps #WebAppSecurity
Attackers are often seen to be utilizing unprotected CORS policies when stealing sensitive data. Always validate Access-Control-Allow-Origin, and especially avoid wildcards in production. Secure your APIs before they secure your breach. 🔐💥 #CyberSecurity #WebAppSecurity #trend

😱Shocking but true😨 A staggering 98% of web applications are sitting ducks for cyber attacks! From malware to malicious redirects, the risks are real. Are you safeguarding your digital presence? #CyberSecurity #WebAppSecurity #StayProtected #InstaSafe #ZeroTrust #malware

Eric’s cybersecurity journey started with hands-on training at Milima Cyber Academy. Want to gain real-world skills too? April 2025 Cohort starts 7th April! Apply now: mca.ac.ug #CybersecurityTraining #WebAppSecurity

A penetration test revealed serious vulnerabilities in a web app. Instead of fixing them, the team chose to encrypt HTTP requests, which failed to provide true security. Lesson: encryption is not remediation! 🔒💻 #WebAppSecurity #EncryptionFails link: ift.tt/uM1SBvQ

Harnessing the power of machine learning algorithms, we automatically discover APIs by monitoring application traffic. Innovo seamlessly integrates out-of-the-box policies, creating a positive security model based on your organization’s schema specification. #WebAppSecurity

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/47PlSYx #eWPTX #WebAppSecurity #PenetrationTesting

Our Chris Tams with a reminder on why security needs to feature high in the Software Development Life Cycle. Responses still contain too much information which simply doesn't need to be there - Information disclosure through insecure design pentestpartners.com/security-blog/… #webappsecurity

Modern businesses are relying more on online operations, including remote work and quick data sharing across distances. Strong web application security is crucial for survival and success in the digital age. Learn More: clouddefense.ai/web-applicatio… #CloudDefenseAI #WebAppSecurity

Innovo's firewall diligently monitors both incoming and outgoing web traffic, establishing a proactive defense against potential security threats. #WebAppSecurity #WAFProtection #CyberDefense #WebSecurity #InnovoWAF #AppFirewall #DigitalSafety #OnlineProtection #SecuredWeb
𝗢𝘂𝗿 𝗪𝗲𝗯 𝗔𝗽𝗽 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗦𝗲𝗿𝘃𝗶𝗰𝗲𝘀 At Cynical Technology, we stand with the defenders finding the vulnerabilities before attackers do, and turning your web application into a fortress. #WebAppSecurity #VulnerabilityAssessment #CynicalTechnology

🚀 New Post: Boost Web Security: WAF Safeguard your website with Web Application Firewall (WAF). Learn how to boost web security and prot... 🔗 Read more: kubaik.github.io/boost-web-secu… #WebAppSecurity #Blockchain #CyberSecurity #Cybersecurity #innovation
#WooCommerce — Checkout Hijack via Parameter Tampering 🚨 Why it matters: Attackers replace checkout endpoints with fraudulent URLs → instant customer trust collapse 🛡️ Action: Block tampered HTTP requests with Quttera WAF. quttera.com/web-applicatio… #CVE #WebAppSecurity…

Is your web app ready for 2025? Don’t leave it vulnerable. Make sure it has: ✔ Two-Factor Authentication ✔ End-to-End Encryption ✔ Regular Security Audits Protect your users and your business. #WebSecurity #CyberSecurity #webappsecurity #TechTrends
#Joomla — Remote File Inclusions 🚨 Why it matters: RFI attacks upload shells and take full control 🛡️ Action: Block payloads with Web Application Firewall for full-perimeter defense quttera.com/web-applicatio… #CyberSecurity #WebAppSecurity #FullPerimeterSecurity

Why rely on generic scans? Our certified analysts manually probe every path, exploit weak apps, and validate fixes in real time—so you go live with confidence. 👉 Explore the full service → infosightinc.com/web-applicatio… #WebAppSecurity #PenTesting #ExpertLed #InfoSight…
Authentication & Sessions Test authenticated areas using cookies: sqlmap -u "site.com/dashboard" --cookie="session=abc123" Or use Burp Suite export: sqlmap -r request.txt #WebAppSecurity #BugBounty
🚨JS Overlay Credential Theft Why it matters: Overlaid login forms capture user and admin credentials 🛡️ Action: Use WAF to block overlay-based attacks at the script level quttera.com/web-applicatio… #InfoSec #Malware #WebAppSecurity

🚨Parameter Pollution Attacks Why it matters: Attackers manipulate URL parameters to bypass validation 🛡️ Action: Use Quttera WAF to block polluted multi-parameter payloads quttera.com/web-applicatio… #CyberSecurity #WebAppSecurity #Quttera

A good refresher of what I learnt in CompTIA Security+ concerning Web Application Security, and including some cool practical exercises. #TryHackMe #OWASP #webappsecurity

𝗢𝘂𝗿 𝗪𝗲𝗯 𝗔𝗽𝗽 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗦𝗲𝗿𝘃𝗶𝗰𝗲𝘀 At Cynical Technology, we stand with the defenders finding the vulnerabilities before attackers do, and turning your web application into a fortress. #WebAppSecurity #VulnerabilityAssessment #CynicalTechnology

Meet Brett Mulé, a trusted expert delivering top-notch penetration testing, web app security, and CTI-driven projects to safeguard your digital world. #CyberSecurity #PenetrationTesting #WebAppSecurity #CTI #CyberIntelligence #SecureIntegrations #TrustedPartner

#WooCommerce — Checkout Hijack via Parameter Tampering 🚨 Why it matters: Attackers replace checkout endpoints with fraudulent URLs → instant customer trust collapse 🛡️ Action: Block tampered HTTP requests with Quttera WAF. quttera.com/web-applicatio… #CVE #WebAppSecurity…

Something went wrong.
Something went wrong.
United States Trends
- 1. rUSD N/A
- 2. #DMDCHARITY2025 853K posts
- 3. #TusksUp N/A
- 4. #AEWDynamite 21K posts
- 5. #TheChallenge41 2,231 posts
- 6. Diddy 74.7K posts
- 7. #Survivor49 2,931 posts
- 8. Earl Campbell 2,121 posts
- 9. seokjin 160K posts
- 10. Free Tina 14K posts
- 11. Yeremi N/A
- 12. Jamal Murray 7,577 posts
- 13. Steve Cropper 6,758 posts
- 14. Monkey Wards N/A
- 15. Milo 12.7K posts
- 16. Californians 6,667 posts
- 17. Isaiah Stewart 1,787 posts
- 18. Metroid Prime 4 12.3K posts
- 19. Ryan Nembhard 3,873 posts
- 20. fnaf 2 17K posts



























