#webappsecurity search results
Just wrapped up talking about web app security for 4 hours and still not tired! The energy is real when you're passionate about what you do. 🔐💻 #WebAppSecurity #Cybersecurity

Network or Web App Pentesting: where should we focus? With apps handling critical data daily, web app security has never been more vital. But network pentesting remains crucial for overall security. What’s your take? #Cybersecurity #Pentesting #WebAppSecurity
OWASP Web Application Security Risk #webappdevelopment #webapp #webappsecurity #webapplicationdevelopment #webapplicationsecurity #websecurity #infosec #informationsecurity

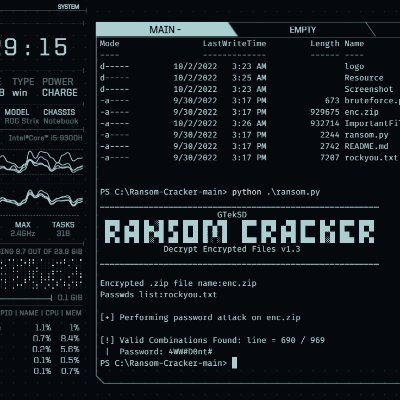
📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap


Attackers are often seen to be utilizing unprotected CORS policies when stealing sensitive data. Always validate Access-Control-Allow-Origin, and especially avoid wildcards in production. Secure your APIs before they secure your breach. 🔐💥 #CyberSecurity #WebAppSecurity #trend

Most people ask how can backend developers enhance their server security...one of the method is jsonwebtokens.🔒 We use JSON Web Tokens (JWT) to protect user data and ensure a robust authentication system. A Thread..k #WebAppSecurity
📋 Web Application Exploit Checklist: Lab-Based Testing for Common Vulnerabilities 💻🛠️ #WebAppSecurity #PenTestingChecklist #EthicalHacking #OWASPTop10 #CyberSecurityTraining #InfoSec #WebSecurity #EducationOnly #BugBounty #RedTeamReady


Modern web apps shouldn’t make you choose between speed and security ⚡ Join us on Sept 18 for a live webinar where we’ll discuss how to secure web apps without sacrificing agility. Register now: bit.ly/3HSdLQc #DevSecOps #WebAppSecurity
🔒💻 How secure are your web apps? Ben and Jacob break down the sandboxing concept and download dangers on Big App Energy. Don't miss the full episode on making smarter app choices! 🎧👉🏻 podcasters.spotify.com/pod/show/big-a… #WebAppSecurity #BigAppEnergy #TechTips #CyberSafety
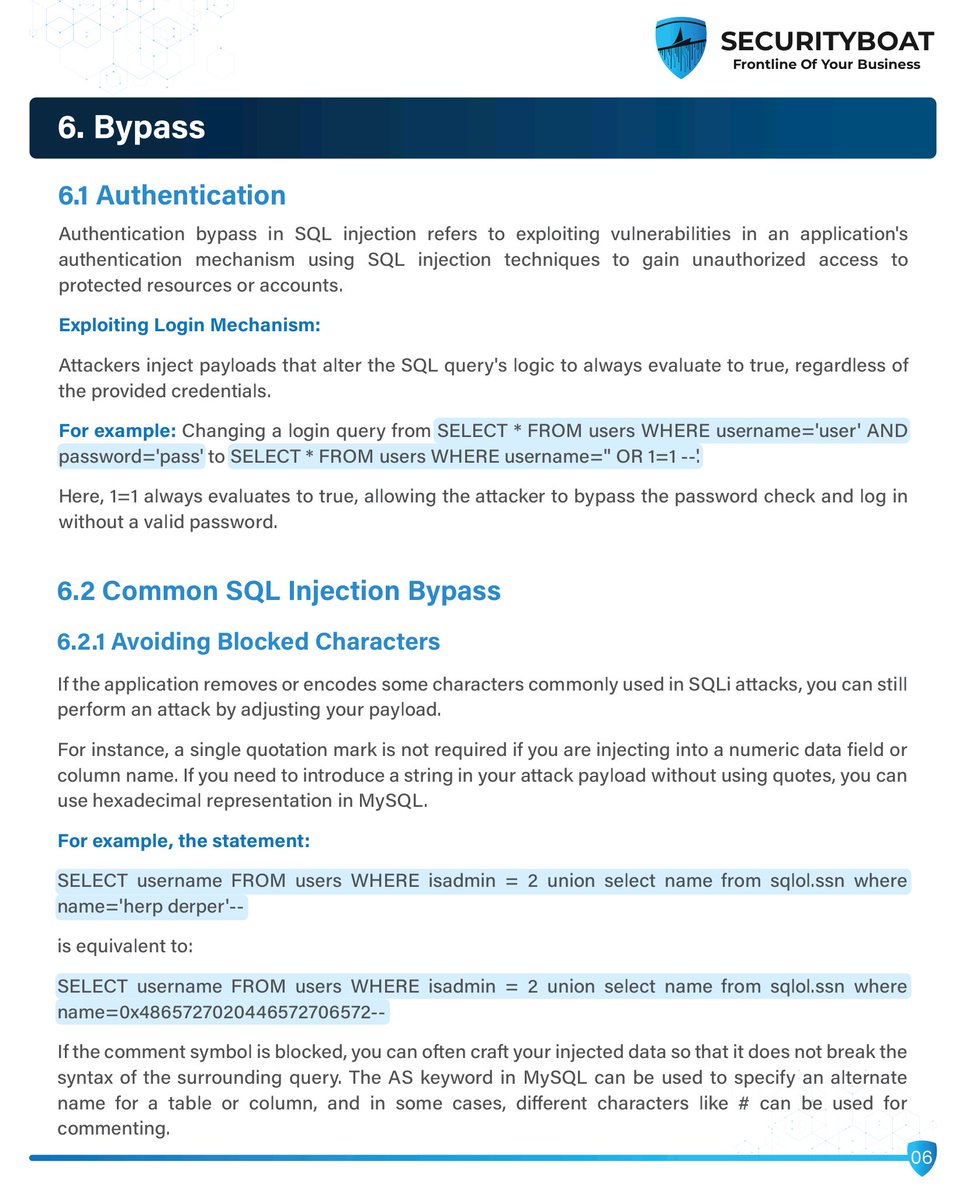
Had the most awesome time previous weekend with @TheLaluka during his OffenSkill level 30 training. It is the best offensive web application security training ever and he is a great mentor with fantastic methodology. offenskill.com #webappsecurity #bugbounty

🍊🔐 Check out my OWASP Juice Shop Lab Walkthrough! 🚀 Dive into the world of web app security with me as we explore vulnerabilities, challenges, and best practices.💻 #OWASP #JuiceShop #WebAppSecurity youtu.be/6n1pI9dJpW4

A penetration test revealed serious vulnerabilities in a web app. Instead of fixing them, the team chose to encrypt HTTP requests, which failed to provide true security. Lesson: encryption is not remediation! 🔒💻 #WebAppSecurity #EncryptionFails link: ift.tt/uM1SBvQ

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/4gBjnLQ #eWPTX #WebAppSecurity #PenetrationTesting

😱Shocking but true😨 A staggering 98% of web applications are sitting ducks for cyber attacks! From malware to malicious redirects, the risks are real. Are you safeguarding your digital presence? #CyberSecurity #WebAppSecurity #StayProtected #InstaSafe #ZeroTrust #malware

Eric’s cybersecurity journey started with hands-on training at Milima Cyber Academy. Want to gain real-world skills too? April 2025 Cohort starts 7th April! Apply now: mca.ac.ug #CybersecurityTraining #WebAppSecurity

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/47PlSYx #eWPTX #WebAppSecurity #PenetrationTesting

New video on my YouTube channel "Bike (HTB SP T1 walkthrough)"! youtu.be/45CcCjO0cNk?fe… #hackthebox #webappsecurity #cybersecuritytraining

🚨 Hands-on Learning Lab. Zero filler. Real-world defense. Join Sofia Visciglia, CTO @ 911CYBER, in person on October 18th at the LAIC Summit for a deep dive: “Web Application Security: From Cloud to Code” RSVP now: laicsummit.com #WebAppSecurity #LAICSummit2025 #

Why wait for hackers to find flaws? Our Web Application Assessments identify weaknesses early so you can fix them fast. Get started with ReadyEdge Security. #SecurityAssessment #WebAppSecurity #EthicalHacking #ReadyEdgeSecurity

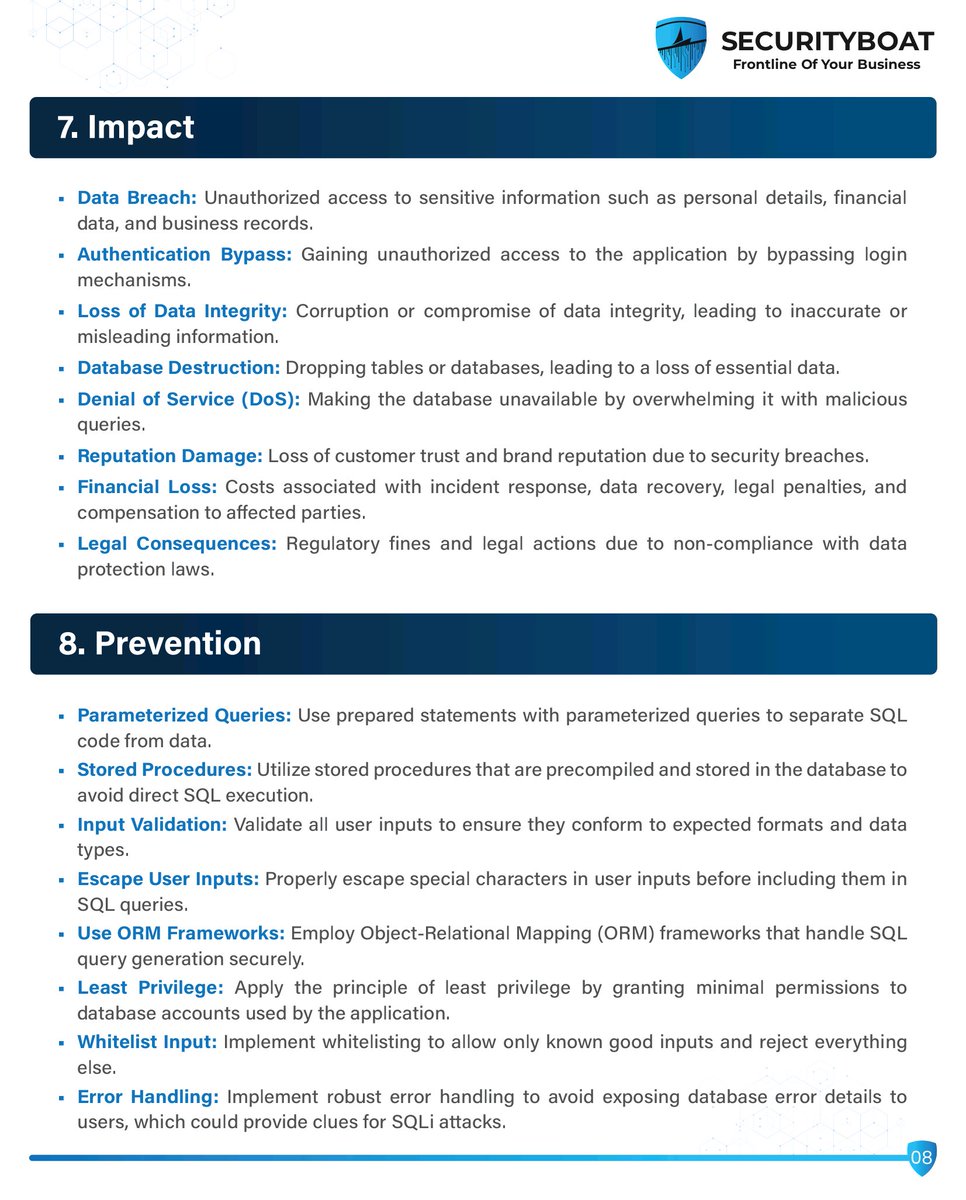
💡 Why it matters: Attackers can steal or corrupt your data through malicious queries. 🛡️ Action: Deploy Quttera Website Protection to block SQLi payloads at the WAF layer. #SQLi #WebAppSecurity #Quttera #Website #Malware

Add null bytes (%00) to test site blocks. Helps find weak spots in security rules. Safe in a test lab only. #InfoSec #Exploits #webappsecurity

eWPTX: Our most advanced web app penetration testing certification covering API pentesting, SQL/NoSQL injection, Authentication attacks, and more. For experienced pentesters ready for the ultimate challenge. bit.ly/4qzAX7C #WebAppSecurity #PenetrationTesting

eWPTX: Our most advanced web app penetration testing certification covering API pentesting, SQL/NoSQL injection, Authentication attacks, and more. For experienced pentesters ready for the ultimate challenge. bit.ly/4odKI9V #WebAppSecurity #PenetrationTesting

eWPTX: Our most advanced web app penetration testing certification covering API pentesting, SQL/NoSQL injection, Authentication attacks, and more. For experienced pentesters ready for the ultimate challenge. bit.ly/3LtRdqo #WebAppSecurity #PenetrationTesting

🔒 Is your web app secure? Learn how Web App Pen Testing finds flaws before hackers do. 👉 7asecurity.com/blog/2025/10/y… #CyberSecurity #WebAppSecurity #PenTest
ก่อนจะปิดงบปีนี้ ตรวจสุขภาพระบบเว็บของคุณแล้วหรือยัง? ช่องโหว่เล็ก ๆ วันนี้ อาจกลายเป็น Data Breach มหาศาลในวันพรุ่งนี้💥 อ่านเพิ่มเติมได้ที่⬇️ bigfish.co.th/resources/4-195 #BigFish #BurpSuite #WebAppSecurity #VulnerabilityTesting #Cybersecurity #VulnerabilityScanner

Just because your site looks safe doesn’t mean it is. Secure your admin panel, update plugins, and monitor logs. Prevention is cheaper than recovery. 🔐 #CyberSecurityTips #WebAppSecurity
🔐 Keep your web apps secure with a clear visual guide. Spot key security areas, apply strategies, and strengthen defenses against threats. Download now. ow.ly/VXzQ50X4Ie7 . . . #WebAppSecurity #CyberSecurity #DataProtection #SafeAeon
A secure web app means trust, fewer breaches, and stronger growth. Our Web Application Assessments provide actionable insights to strengthen your defenses. Contact ReadyEdge Security today! #BusinessSecurity #WebAppSecurity #CyberRisk #ReadyEdgeSecurity

Just wrapped up talking about web app security for 4 hours and still not tired! The energy is real when you're passionate about what you do. 🔐💻 #WebAppSecurity #Cybersecurity

Felt it in one of my recent pentest engagements. The team had an API, which wasn't kinda production-ready but was still used in prod. This heavily leaked PII #pentest #webappsecurity #apisecurity

🔍 Unleashing the Power of Google Dorks: Your Ultimate Arsenal for Bug Bounties, Web Security, and Pentesting! 🛡️💻 | Discovering Vulnerabilities, One Query at a Time | #BugBounty #WebAppSecurity #Pentesting #GoogleDorks Credit - @TakSec

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/4gBjnLQ #eWPTX #WebAppSecurity #PenetrationTesting

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/47PlSYx #eWPTX #WebAppSecurity #PenetrationTesting

📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap




Expect security layers to fail: There are really useful tools to keep web applications safe. Take Web Application Firewalls (WAFs). They inspect web traffic and discard requests to your server if they look malicious. They're a huge benefit to security. #WebAppSecurity 1/2

Using numeric IDs for database records can be a security risk! A problem so common that attackers seeing a numeric ID WILL try to abuse it. They'll change the ID and try to access other people's data. Use GUIDs instead, e.g. ac037242-6e11-475c-a429-92ed1d2abc1c #WebAppSecurity

SAML Raider 2.0.0 is here! Upgraded to the Montoya API, now with a smoother build and better user experience. Perfect for your pentesting toolkit. Check it out and read our blog post! ✨#BurpSuite #SAML #WebAppSecurity blog.compass-security.com/2024/07/saml-r…

📋 Web Application Exploit Checklist: Lab-Based Testing for Common Vulnerabilities 💻🛠️ #WebAppSecurity #PenTestingChecklist #EthicalHacking #OWASPTop10 #CyberSecurityTraining #InfoSec #WebSecurity #EducationOnly #BugBounty #RedTeamReady


API Security Google Dorks: hego.gitbook.io #BugBounty #WebAppSecurity #PenTesting #HackerMindset #EthicalHacking #OWASPTop10 #XSS #SQLInjection #CSRF #SecurityTesting #InfoSec #AppSec #VulnerabilityDiscovery #BugbountyTips #BurpSuite #PentestTools #API #APISecurity

🍊🔐 Check out my OWASP Juice Shop Lab Walkthrough! 🚀 Dive into the world of web app security with me as we explore vulnerabilities, challenges, and best practices.💻 #OWASP #JuiceShop #WebAppSecurity youtu.be/6n1pI9dJpW4

Most people ask how can backend developers enhance their server security...one of the method is jsonwebtokens.🔒 We use JSON Web Tokens (JWT) to protect user data and ensure a robust authentication system. A Thread..k #WebAppSecurity

Attackers are often seen to be utilizing unprotected CORS policies when stealing sensitive data. Always validate Access-Control-Allow-Origin, and especially avoid wildcards in production. Secure your APIs before they secure your breach. 🔐💥 #CyberSecurity #WebAppSecurity #trend

A penetration test revealed serious vulnerabilities in a web app. Instead of fixing them, the team chose to encrypt HTTP requests, which failed to provide true security. Lesson: encryption is not remediation! 🔒💻 #WebAppSecurity #EncryptionFails link: ift.tt/uM1SBvQ

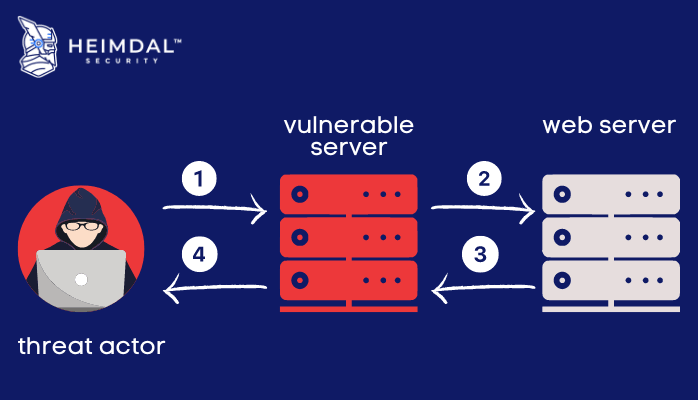
👉 Try #virtualpatching and start fixing your #vulnerabilities in a day! Understand how: (link in thread) @tumblr #webappsecurity #databreaches #vulnerabilitymanagement #vulnerabilityassessment #waf #apptrana #indusface

eWPTX: Our most advanced web app penetration testing certification 100% hands-on exam covering: API pentesting (25%) SQL/NoSQL injection Authentication attacks WAF bypass techniques Server-side attacks bit.ly/48paCCo #eWPTX #WebAppSecurity #PenetrationTesting

Our Chris Tams with a reminder on why security needs to feature high in the Software Development Life Cycle. Responses still contain too much information which simply doesn't need to be there - Information disclosure through insecure design pentestpartners.com/security-blog/… #webappsecurity

Had the most awesome time previous weekend with @TheLaluka during his OffenSkill level 30 training. It is the best offensive web application security training ever and he is a great mentor with fantastic methodology. offenskill.com #webappsecurity #bugbounty

Something went wrong.
Something went wrong.
United States Trends
- 1. Grammy 226K posts
- 2. Clipse 13.7K posts
- 3. Kendrick 51K posts
- 4. Dizzy 8,408 posts
- 5. olivia dean 11.5K posts
- 6. addison rae 18.2K posts
- 7. gaga 87.8K posts
- 8. AOTY 16.5K posts
- 9. Leon Thomas 14.3K posts
- 10. Katseye 97.5K posts
- 11. #FanCashDropPromotion 3,385 posts
- 12. Kehlani 29.5K posts
- 13. ravyn lenae 2,423 posts
- 14. lorde 10.5K posts
- 15. Durand 4,254 posts
- 16. Album of the Year 53.3K posts
- 17. Alfredo 2 N/A
- 18. The Weeknd 9,713 posts
- 19. #FridayVibes 6,727 posts
- 20. #FursuitFriday 11.1K posts