#cloudsecurity نتائج البحث
Life Lately, I’ve been playing around a lot with Google Cloud Platform (security~wise) as to becoming an expert security engineer. Not for work but for personal development and I have another guide put together. I’ll share with y’all soon. #CloudSecurity

Azure Local's security features are built-in by default. Microsoft Defender for Cloud gives an overview with recommendations for physical machines, VMs, and Kubernetes clusters. An end-to-end solution! #Azure #CloudSecurity #AzureLocal #AzureArc
Fundamentals of Cloud and Cloud Security-TO READ amazon.com/Fundamentals-C… #CloudSecurity #cloudsecurityebook #cloudsecuritysolution #cybersecurityebook #CybersecurityTraining #CybersecurityCareer #cybersecuritysolutions
I’ve officially earned the ISO 27001 Lead Auditor Certification. 🎉 #CyberSecurity #CloudSecurity #GRC
Litigation against cloud providers is rare and risky. Courts often view liability as a shared responsibility between the provider and the enterprise. Risk assessment & mitigation plans are essential. #CloudSecurity #RiskManagement
ஆன்லைன் பாதுகாப்பில் நிபுணத்துவம் பெற்ற கிளவுட்ஃப்ளேர் நிறுவனம் “latent bug” காரணமாக நேற்று செயலிழந்ததை அடுத்து அதன் பங்கு விலை 1.5 சதவீதம் சரிவைக் கண்டது. #Cloudflare #latentbug #cloudsecurity #CloudComputing #CloudNetwork

☁️ Cloud Security Tools — Essential Toolkit for Modern Teams 🛡️🚀 #CloudSecurity #InfoSec #DevSecOps #CyberSecurity #CSPM #CWPP #IAM #SIEM #ContainerSecurity #Compliance #SecurityTools #CloudComputing ☁️🛡️




Day 26! Locked down AWS access today with IAM! ✅ Explored Users & Groups ✅ Analyzed IAM policies ✅ Applied least privilege access ✅ Tested policy effects ✅ Used secure sign-in URLs Mastering the foundation of cloud security. #AWS #IAM #CloudSecurity
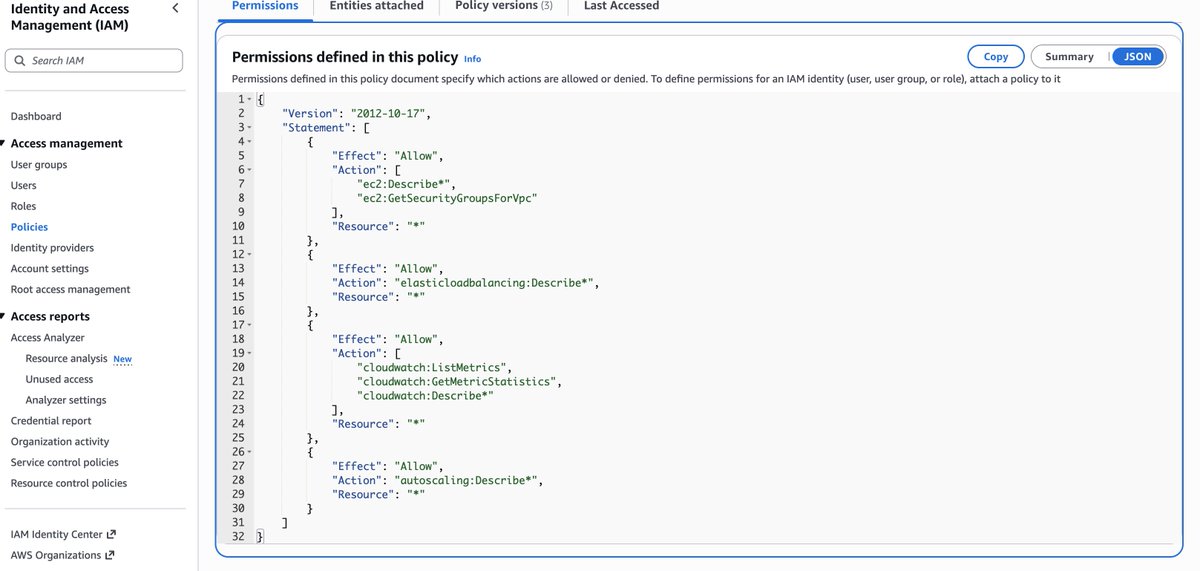
"🛡️ Query your attack surface with Defender EASM using Microsoft Copilot in #Azure! 🔍 Discover assets, risks & vulnerabilities 🤖 Use natural language for instant insights Start here 👉 msft.it/6018tziUE #CloudSecurity #AI #CyberDefense"

BeyondTrust and AWS are partnering again to strengthen cloud identity security. Smart privilege controls + JIT access = stronger protection. Read more ⬇️ aws.amazon.com/blogs/apn/enha… #IdentitySecurity #CloudSecurity
Cloud innovation moves fast — and now vulnerability management does too. Introducing Tenable Cloud Vulnerability Management in Tenable One for unified, agentless visibility across cloud environments. spr.ly/601875CgM #exposuremanagement #cloudsecurity

Cloud outages cost 10-15x more than just downtime due to reputational damage. Small businesses may not recover. Consider cyber insurance—it can cover losses SLAs miss, even reputational hits. #CloudSecurity #CyberInsurance
Least privilege access across resources enforced✅ every user gets only what they truly need. Tightened security, reduced risk. #CloudSecurity #AWS #DevOps


By using the cloud for BC/DR, businesses achieve goals, dramatically reducing recovery times and costs while ensuring critical operations can weather any storm. It’s the smart way to protect revenue and reputation. #DRBC #CloudSecurity #TechInnovation linkedin.com/posts/oluwaseu…
Why can't enterprises get a handle on the #cloud misconfiguration problem? buff.ly/X3PHhVN @CSOonline @MariaKorolov #tech #cloudsecurity #digital #innovation #business #leadership #CIO #CTO #CDO #CEO #CISO #cybersecurity #digitaltransformation #cloudproviders #IT

Your data deserves fortress-level protection. 🛡️ Learn how Snowflake’s multi-layered security, encryption, and IAM framework keep your cloud data safe. 👉 bit.ly/47tH71r #Snowflake #CloudSecurity #DataProtection
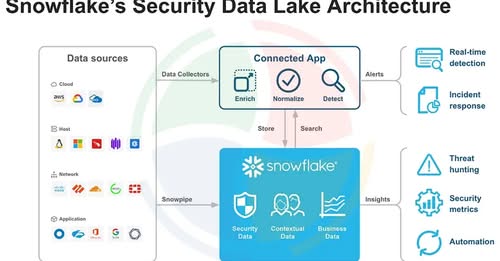
🚨 AI is breaking AppSec, CloudSec, & DevSecOps silos. We spoke to Tejas Dakve (Bloomberg) & Aditya Patel (Cloud Architect): “Security must shift from ‘no’ → ‘safe yes.’” ⚡ Why old AppSec models fail 🔄 How AI changes collaboration 🎧 Full ep LIVE tomorrow 👇 #CloudSecurity
Defeating malicious hackers seems unlikely, so it is better to be aware of the most common threats and prepare with proactive and reactive strategies to match the risks. RT @antgrasso #CloudComputing #CloudSecurity #CyberAttacks

Microsoft boosts security with new Defender features like Predictive Shielding, enhances threat hunting, and integrates Sentinel with AWS, Okta, Proofpoint data. GitHub Advanced Security now links with Defender for Cloud. #CloudSecurity #AITools #USA ift.tt/3HVsfvm
By using the cloud for BC/DR, businesses achieve goals, dramatically reducing recovery times and costs while ensuring critical operations can weather any storm. It’s the smart way to protect revenue and reputation. #DRBC #CloudSecurity #TechInnovation linkedin.com/posts/oluwaseu…
ஆன்லைன் பாதுகாப்பில் நிபுணத்துவம் பெற்ற கிளவுட்ஃப்ளேர் நிறுவனம் “latent bug” காரணமாக நேற்று செயலிழந்ததை அடுத்து அதன் பங்கு விலை 1.5 சதவீதம் சரிவைக் கண்டது. #Cloudflare #latentbug #cloudsecurity #CloudComputing #CloudNetwork

📞 Contact us: +91 63648 79344 🌐 Visit: codersnest.in [Cloud Computing, Cloud Solutions, Disaster Recovery, Secure Digital Infrastructure, App Development, Cloud Security, CodersNest] #CloudComputing #DigitalTransformation #CloudSecurity #AppDevelopment #CodersNest
![CodersNest70901's tweet image. 📞 Contact us: +91 63648 79344
🌐 Visit: codersnest.in
[Cloud Computing, Cloud Solutions, Disaster Recovery, Secure Digital Infrastructure, App Development, Cloud Security, CodersNest]
#CloudComputing #DigitalTransformation #CloudSecurity #AppDevelopment #CodersNest](https://pbs.twimg.com/media/G6GkyF9bMAU6Qyl.jpg)
Apono @Apono_official Secures $34 Million in Series B #CloudSecurity #IdentityManagement #CyberSecurity #PrivilegedAccess #AI #AccessManagement #SeriesB #Funding thesaasnews.com/news/apono-sec…
Principle of Least Privilege in AWS Give users only the permissions they need, nothing more. ✅ Reduces security risks ✅ Limits blast radius if credentials are compromised ✅ Keeps your AWS environment safer #AWS #CloudSecurity #DevOps
From APTs to spoofing—lock down your communication with enterprise-grade email security add-ons. visit - intechdc.com/acronis #EnterpriseSecurity #CloudSecurity #EmailProtection #AntiSpoofing #IntechDCHosting

Cloud Access Security Broker (CASB) - Bulut Güvenliği. Bulutta Kör Noktalara Son: CASB ile Gölge BT'yi Aydınlatın sympro.net/cloud-access-s… #CASB #BulutGüvenliği #CloudSecurity #ShadowIT #GölgeBT #SaaS #IaaS #DLP #VeriKoruma #BulutDLP #SiberGüvenlik #ErişimKontrolü #UyumYönetimi

@Netskope expands its collaboration with @Microsoft, delivering new AI and cloud security integrations across Purview, Entra GSA, and 365 Copilot. #Netskope #Microsoft #CloudSecurity #AIsecurity #SASE #SSE #Cybersecurity electronicsmedia.info/2025/11/19/net…
:#CertificateLifecycle #CertificateManager #CloudSecurity #DevSecOps #IdentitySecurity #cybersecurity #KubernetesSecurity #MachineIdentity #OpenShift #PKI #WorkloadIdentity my.sociabble.com/SzFeKUaKDya1
⚠️ Urgent threat! New #ShadowRay attacks are actively hijacking Ray clusters, secretly converting them into crypto miners. Secure your infrastructure before it's too late! #CyberSecurity #CloudSecurity bleepingcomputer.com/news/security/…
AI in hybrid environments increases network load companies must adapt security strategies. #AI #CloudSecurity
#CloudSecurity #RedTeam #EthicalHacking #AWS #Azure #GCP #CyberSecurity #Pentesting #BlueTeam #DevSecOps #CyberDefenseStrategy
Why does this matter? It enables secure data aggregation in untrusted environments (like the cloud), preserving privacy without sacrificing functionality. #CloudSecurity #DataProtection
Homomorphic Addition (HA) in Fully Homomorphic Encryption (FHE): Homomorphic Addition (HA) lets you add encrypted data (ciphertexts) directly. When you decrypt the result, it equals the sum of the original unencrypted data. It's like adding while keeping secrets safe! #FHE

Life Lately, I’ve been playing around a lot with Google Cloud Platform (security~wise) as to becoming an expert security engineer. Not for work but for personal development and I have another guide put together. I’ll share with y’all soon. #CloudSecurity

Day 26! Locked down AWS access today with IAM! ✅ Explored Users & Groups ✅ Analyzed IAM policies ✅ Applied least privilege access ✅ Tested policy effects ✅ Used secure sign-in URLs Mastering the foundation of cloud security. #AWS #IAM #CloudSecurity

☁️ Your cloud has public exposure you don't know about. Run these 6 commands. Find what's exposed. Fix it before attackers do. 🔎 📌 Save this for your next incident review. #CloudSecurity #AWS #Azure #SOC #CyberDefenders

ஆன்லைன் பாதுகாப்பில் நிபுணத்துவம் பெற்ற கிளவுட்ஃப்ளேர் நிறுவனம் “latent bug” காரணமாக நேற்று செயலிழந்ததை அடுத்து அதன் பங்கு விலை 1.5 சதவீதம் சரிவைக் கண்டது. #Cloudflare #latentbug #cloudsecurity #CloudComputing #CloudNetwork

The Latio 2025 Cloud Security Market Report confirms what we’ve long believed: the future of #cloudsecurity lies in Continuous Threat Exposure Management (CTEM). At Tenable, we’re leading this evolution - empowering organizations with a unified view of... ow.ly/Azn1106p0bh

Your data deserves fortress-level protection. 🛡️ Learn how Snowflake’s multi-layered security, encryption, and IAM framework keep your cloud data safe. 👉 bit.ly/47tH71r #Snowflake #CloudSecurity #DataProtection

Your customers trust you to defend their data. Learn 10 reasons why your business wins when you invest in #CloudSecurity. Download the white paper: ow.ly/3H6E50Xbt92

☁️ Cloud Security Tools — Essential Toolkit for Modern Teams 🛡️🚀 #CloudSecurity #InfoSec #DevSecOps #CyberSecurity #CSPM #CWPP #IAM #SIEM #ContainerSecurity #Compliance #SecurityTools #CloudComputing ☁️🛡️




Ayush Priya, Lead Data & Cloud Security Engineer @ CRED. He’ll share strategies to secure sensitive information in cloud-native environments using encryption, access controls, and advanced threat detection. #CyberSecurity #CloudSecurity #DataProtection #Infosec

Ready to level up your #cloudsecurity game? 🔒 Master Azure's robust security features & prep for AZ-500. Become the security champion your IT needs: bit.ly/3JkHtyd #azure #microsoft #training #certification #learningpath

Why can't enterprises get a handle on the #cloud misconfiguration problem? buff.ly/X3PHhVN @CSOonline @MariaKorolov #tech #cloudsecurity #digital #innovation #business #leadership #CIO #CTO #CDO #CEO #CISO #cybersecurity #digitaltransformation #cloudproviders #IT

We’re excited to welcome Shaleen Dev P.K. & Joshua Bahirvani @ Microsoft as they demonstrate strategies to disrupt fake digital identities and automated abuse in cloud environments. #CyberSecurity #CloudSecurity #Infosec #ThreatIntel #AIsecurity

Defeating malicious hackers seems unlikely, so it is better to be aware of the most common threats and prepare with proactive and reactive strategies to match the risks. RT @antgrasso #CloudComputing #CloudSecurity #CyberAttacks

☁️ The 2025 Latio Cloud Security Market Report by James Berthoty confirms the #cloudsecurity market is evolving to Continuous Threat Exposure Management (#CTEM) for unified risk. That’s why we’re excited Tenable is recognized for leading the charge on this strategic shift. 📊...

𝐇𝐨𝐰 𝐂𝐥𝐨𝐮𝐝 𝐒𝐭𝐨𝐫𝐚𝐠𝐞 𝐏𝐫𝐨𝐭𝐞𝐜𝐭𝐬 𝐘𝐨𝐮𝐫 𝐃𝐚𝐭𝐚 𝐟𝐫𝐨𝐦 𝐋𝐨𝐬𝐬 𝐚𝐧𝐝 𝐓𝐡𝐞𝐟𝐭 Your data deserves more than a hard drive! ☁️ Learn how cloud storage defends against theft, loss, and cyberattacks. Stay secure in 2025. #CloudSecurity #DataProtection…

From compliance to containers—secure your AWS stack with: ✅ NIST, PCI DSS, GDPR ✅ Serverless & IoT protection ✅ Multi-cloud & hybrid strategies Built for cloud pros & security enthusiasts. 🛡️ #CloudSecurity #AWS #DevSecOps #CyberResilience 🔗 ow.ly/VQ7H50X6qT6

In today’s digital-first world, businesses rely on SaaS applications and cloud platforms to accelerate growth, collaboration, and innovation. bit.ly/3vgw3Rn #eScan #CloudSecurity #SaaSProtection #Cybersecurity #SecureEveryWorkflow #EmpowerEveryMove

🔐 Nearly 80% of breaches in 2025 involve stolen credentials. We reviewed the 8 best enterprise password managers for 2025, comparing features, pricing, and ideal use cases. 👉 See the full list: techrepublic.com/article/enterp… #Cybersecurity #CloudSecurity #PasswordManager #Infosec…

Cloud innovation moves fast — and now vulnerability management does too. Introducing Tenable Cloud Vulnerability Management in Tenable One for unified, agentless visibility across cloud environments. spr.ly/601875CgM #exposuremanagement #cloudsecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. #TT_Telegram_sam11adel N/A
- 2. LeBron 82.4K posts
- 3. #DWTS 53.6K posts
- 4. #LakeShow 3,926 posts
- 5. Peggy 18.8K posts
- 6. Whitney 15.9K posts
- 7. Reaves 8,493 posts
- 8. Keyonte George 1,914 posts
- 9. Orioles 7,086 posts
- 10. Macklin Celebrini 2,571 posts
- 11. Jazz 27.3K posts
- 12. Grayson 7,043 posts
- 13. Taylor Ward 3,596 posts
- 14. #TheFutureIsTeal 1,573 posts
- 15. Kwara 150K posts
- 16. DUSD N/A
- 17. Tatum 16.7K posts
- 18. #Lakers 1,616 posts
- 19. Rantanen 2,097 posts
- 20. ELAINE 17.4K posts