#datavulnerabilities نتائج البحث
Companies should take necessary steps to protect data in motion. This includes encryption, secure protocols and authentication measures. #DataSecurity #DataInMotion #DataVulnerabilities

Gain an accurate understanding of your organisations #datavulnerabilities & compliance. Watch the Business Lens Demo hubs.ly/H06jYhR0

According to our annual Cyber Claims Study, the costs of #cyberincidents add up to an average of $175K for SMEs. Get more insights into the impact of #datavulnerabilities – download your free copy of our report now: hubs.la/Q02r9Spk0

Companies should take necessary steps to protect data in motion. This includes encryption, secure protocols and authentication measures. #DataSecurity #DataInMotion #DataVulnerabilities

A survey reveals 65% of office workers bypass cybersecurity for productivity, with 80% accessing work apps on personal devices. High-risk behavior is prevalent, exposing organizations to threats. #WorkplaceRisks #CyberAware #DataVulnerabilities #Cybersec… ift.tt/HXMdOtD
Camille @morhardt and I had a great time speaking with 2x Olympic gold medal decathlete @AshtonJEaton ahead of the #TokyoOlympics on this #CyberSecurityInside; he gave some insight into the #datavulnerabilities athletes face. buff.ly/2R1sM7q @IntelSecurity

#GetPicnic and give every employee in your organization a detailed display of their public #datavulnerabilities and the technological means to remove what they want to stop #socialengineering attacks before they happen.
The distribution of COVID vaccines brings challenges in regards to #healthcaredata breaches. The need to limit further outbreaks will create a further drive to share data more broadly, in turn, presenting further opportunities for #datavulnerabilities. bbc.co.uk/news/technolog…
#Dealflow: Bangalore and Boston-based @FireCompass raised $7 million to “ethically #hack” businesses to expose #datavulnerabilities and breaches. impactalpha.com/the-brief-the-…
IntelBroker exploits #DataVulnerabilities to expose and leak sensitive information. Home Depot is the latest to suffer a #DataBreach linked to them. When these breaches occur, I like to circle back to key #Vulnerabilities hackers target. bleepingcomputer.com/news/security/…
CVE-2025-64315 Configuration defect vulnerability in the file management module. Impact: Successful exploitation of this vulnerability may affect app data confidentiality and integr… cve.org/CVERecord?id=C…
🚨 Asahi Data Breach Impacts 2 Million Individuals securityweek.com/asahi-data-bre… #DataBreach #Ransomware #Hacking
OpenAI Data Breach Exposes User Details, Urges Vigilance dlvr.it/TPVdhM #GiReview @gigadgets_
Vigilance.fr #Vulnerability of #Grafana: information disclosure via Databricks Datasource. #patch vigilance.fr/vulnerability/…
Vigilance.fr #Vulnérabilité de #Grafana : obtention d'information via Databricks Datasource. #patch vigilance.fr/vulnerabilite/…
Here's a useful resource for victims of data breaches, including checklists and letter templates: bit.ly/2xFuvUV
🚨 Data Breach in Progress! Watch as I leverage a simple vulnerability on a target web application to access the database. The 'users' table dump is the final payload. This is why input sanitization is not optional. The damage is real, and the data is out.
Cyber Data Breaches — the silent threat that can collapse systems, expose millions, and damage national institutions. 🎧 Watch the latest Dialectic Arc Brief, youtu.be/gzELJOQ0MTc?si… #Cyber #Data #Digital #Algorithms #AI #CyberAttack #Theft #Pakistan

Ransomware Operator Claims - Week 47 2025 200 Ransomware Victims tracked dbdigest.com/2025/11/ransom… #databreach #databreaches #databreachesdigest #dataprivacy #GDPR #cybersec #cybersecurity #infosec #informationsecurity #cyberattack #hacked #malware #phishing #ransomware #ROCreport
CVE-2025-66250 Unauthenticated Arbitrary File Upload in DB Electronica Mozart FM... vulmon.com/vulnerabilityd… Customizable Vulnerability Alerts: alerts.vulmon.com/?utm_source=tw…
Critical vulnerabilities unveiled: Apache Syncope’s CVE-2025-65998 risks stored passwords; Fluent Bit RCE flaws enable cloud attacks; Oracle KEV exploits affect Canon; major breaches hit Dartmouth, SitusAMC, Almaviva, and more. #DataBreach #CloudSecurity ift.tt/u7mRinL
Vigilance.fr #Vulnerability of #Drupal Access code: user access dated 24/09/2025. #infosec vigilance.fr/vulnerability/…
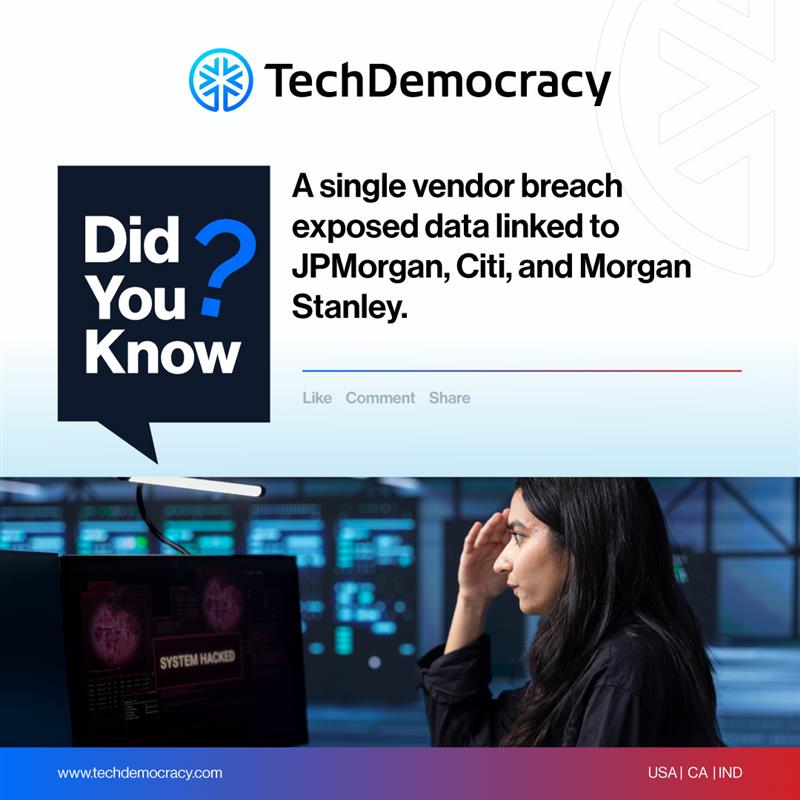
A single vendor #breach let attackers access corporate files and customer-linked data from major banks. This is a clear case of #datatheft made possible by one weak link in the #SupplyChain, a risk many businesses still overlook. #CybersecurityAwareness #CyberDefense
🔴 Critical Flaw in Oracle Identity Manager Under Exploitation darkreading.com/vulnerabilitie… #DataBreach #Exploit #CVE
A major bank hack exposes sensitive customer data — showing how financial trust can vanish with a single breach. In security, stability must be engineered, not assumed. 🏦⚠️ #BankSecurity #Breach buff.ly/Af3fhDx
Global breaches show how identity failures destabilise governance, erode trust, and enable fraud. India must urgently strengthen protections across civic data systems. By David Sehyeon Baek: voicendata.com/security/the-f… #voicendata #data #AI #telecom #security

🔓 KEY VULNERABILITIES • Misconfigured web application firewall • Unpatched software • Overly permissive permissions

[ZDI-25-886|CVE-2025-9189] (0Day) Digilent DASYLab DSB File Parsing Deserialization of Untrusted Data Remote Code Execution Vulnerability (CVSS 7.8; Credit: kimiya) zerodayinitiative.com/advisories/ZDI…
Everyone’s data gets stolen eventually. The question is: how hard are you making it for them? Limit what you share, clean up old accounts, don’t ignore those 2FA prompts. Be prepared 👉 dreamhost.com/blog/data-brea… #DataBreach #Cybersecurity #Privacy
The compromised data included: ✉️ Email addresses 📱 Phone numbers 👤 Names 🏠 Physical addresses All now in the hands of cybercriminals who are actively using it for targeted attacks.
Companies should take necessary steps to protect data in motion. This includes encryption, secure protocols and authentication measures. #DataSecurity #DataInMotion #DataVulnerabilities

Camille @morhardt and I had a great time speaking with 2x Olympic gold medal decathlete @AshtonJEaton ahead of the #TokyoOlympics on this #CyberSecurityInside; he gave some insight into the #datavulnerabilities athletes face. buff.ly/2R1sM7q @IntelSecurity

Companies should take necessary steps to protect data in motion. This includes encryption, secure protocols and authentication measures. #DataSecurity #DataInMotion #DataVulnerabilities

Gain an accurate understanding of your organisations #datavulnerabilities & compliance. Watch the Business Lens Demo hubs.ly/H06jYhR0

According to our annual Cyber Claims Study, the costs of #cyberincidents add up to an average of $175K for SMEs. Get more insights into the impact of #datavulnerabilities – download your free copy of our report now: hubs.la/Q02r9Spk0

Something went wrong.
Something went wrong.
United States Trends
- 1. #socideveloper_com N/A
- 2. #lip_bomb_RESCENE N/A
- 3. #River 3,914 posts
- 4. ARMY Protect The 8thDaesang 22.4K posts
- 5. #DaesangForJin 28.9K posts
- 6. #heatedrivalry 18.4K posts
- 7. Ravens 59.2K posts
- 8. ilya 18.2K posts
- 9. Lamar 46.7K posts
- 10. Shane 22K posts
- 11. Black Friday 269K posts
- 12. Bengals 52.8K posts
- 13. Joe Burrow 21.4K posts
- 14. BNB Chain 8,007 posts
- 15. Connor 15.2K posts
- 16. Zay Flowers 4,255 posts
- 17. Hudson 11.9K posts
- 18. Sarah Beckstrom 230K posts
- 19. Third World Countries 30.5K posts
- 20. scott hunter N/A