#maliciouscode search results
🔎Sophisticated #cybersecurity threats, like "FUD" #crypters, make #maliciouscode fully undetectable for stealthy infiltrations. Our #research paper explores #FUD markets in the #deepweb and their impact on cybersecurity. Read it here 👇 socradar.io/underground-fu…

Some (Ordinals) BTC NFTs have in the pdf malicious code executing instructions in javascript. This code is stealing all user's cryptocurrencies by just opening the PDF. (the code scans the MMwallet and Phantom). Part of the code is in the attached image. #maliciouscode #pdf

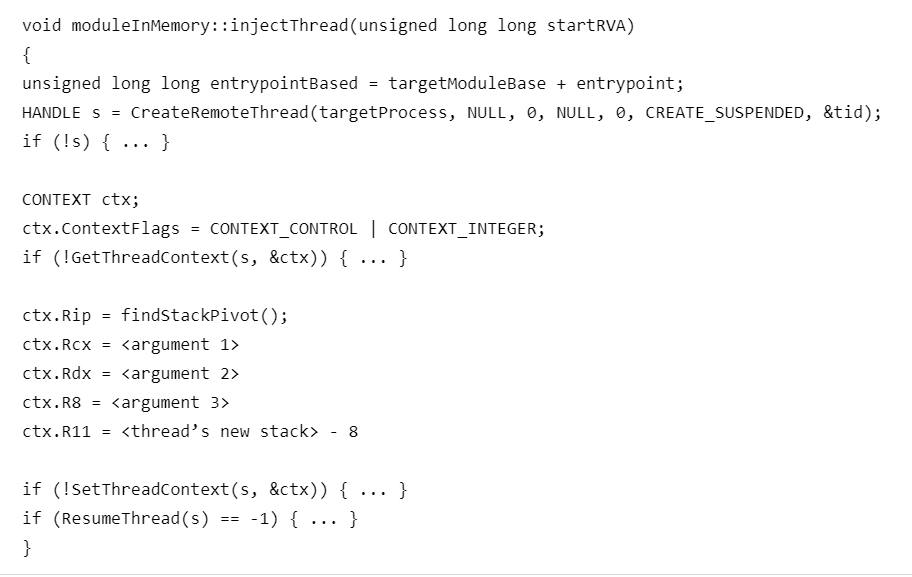
Hiding #MaliciousCode With “#ModuleStomping” - bit.ly/30b8VTg-Ttx #AlizHammond via @FSecure ➡️ #ThreatIntelligence #IDAPro #ShellCode #Exploits #MalwareAnalysis #VirtualAlloc #InfoSec #CyberThreats #Malware #CyberAttacks #CyberDefense #ITsecurity
RT @sucurisecurity Everything you need to know on SEO, as part of your website security. sucur.it/2X22PqQ #SEOSpam #websitesecurity #maliciouscode #SEO

Over 100,000 repositories on #GitHub are infected with #MaliciousCode. Check out this lab collection to defend against these threats: Check out the collection today: 🔒 hubs.ly/Q02n4LZk0 🔒 hubs.ly/Q02n4J8H0 🔒 hubs.ly/Q02n4SNX0

#MaliciousCode In The #PureScript Npm Installer version 3.0.2 And Later- bit.ly/2YUpxxP-Ttx @hdgarrood ➡️ #CyberThreats #Exploits #CyberRisks #InfoSec #Security #CyberSecurity #SecurityPros #CyberAttacks #Vulnerabilities

We're pointing out the red flags in malicious code so you don't have to. 🚩 🚩 We know that #maliciouscode can be challenging to recognize and can remain undetected within applications long before it causes damage. Learn to recognize the red flags. bit.ly/3Otki4O

#CrossSiteScripting is one of the most common vulnerabilities in #WebApps because the attacker has the ability to run #MaliciousCode within the user’s browser. 💻 Learn more about the 3 variants and how you can mitigate security risk here: ow.ly/wH9W50FQuNo
#MalwareAnalysis: #Arm'd & Dangerous, #MaliciousCode Now Native On (#AArch64 #M1) #Apple Silicon bit.ly/3k5dE3H-Ttx @patrickwardle 𝞝 #Enterprises #Organizations #Malware #CyberThreats #InfoSec #macOS #CyberSecurity #AppleSafari #BrowserExtensions #Rosetta #JavaScript




Be aware of malicious code that can infect your devices and compromise your security. Protect yourself by keeping your software up to date and using trusted sources. #MaliciousCode #CyberSecurity

💻 How can #GenerativeAI uplift activities like #MaliciousCode generation, radicalisation & attack planning? 📒 New paper: Turing researchers forecast key inflection points & future threats & suggest mitigations and evaluation approaches: bit.ly/3SvvoYb #DataScience

You can't run #MaliciousCode inside of our #cloud, even if it's inside of a #backup because there's nothing to run it on. It's all complete #ObjectStorage. @druvainc truthin.it/morewithless

EtherHiding: Hackers create novel way to hide malicious code in #blockchains 👉 ow.ly/ptmU50PWXmn #EtherHiding #MaliciousCode #Blockchain #BlockchainSecurity #CyberThreats #DataProtection #DigitalSecurity #Hackers #cybersecurity

Deep Secure Researchers identified a new variant of the Ursnif Trojan that uses corrupted Word documents, white text and multiple layers of obfuscation to conceal itself. lnkd.in/dVMnmmg #deepsecure #contentthreatremoval #maliciouscode

The first instance of #MaliciousCode native to Apple Silicon M1 Macs emerged a month after the release of devices equipped with the company’s in-house CPUs. Find out more in our latest blog. 👇 bit.ly/2NGnVXW
অ্যাপটি গুগল প্লে’তে তালিকাভুক্ত হওয়ার পর প্রায় এক বছর পর যে আপডেট আনে, তাতে বিশেষ এই ‘ক্ষতিকারক কোড’ যোগ করে দিয়েছে। #googleplay #irecorder #maliciouscode #ahrat #ahmyth #bdnews24 bangla.bdnews24.com/tech/oovk7cscqq
bangla.bdnews24.com
গোপনে নজরদারি চালাচ্ছিল গুগল প্লে’র জনপ্রিয় অ্যাপ
অ্যাপটি গুগল প্লে’তে তালিকাভুক্ত হওয়ার পর প্রায় এক বছর পর যে আপডেট আনে, তাতে বিশেষ এই ‘ক্ষতিকারক কোড’ যোগ করে দিয়েছে।
Everything you need to know on SEO, as part of your website security. sucur.it/2X22PqQ #SEOSpam #websitesecurity #maliciouscode #SEO
Malicious contracts are often masked as legitimate SPL tokens. SPL Shield detects and flags these malicious contracts instantly upon launch. #MaliciousCode #SPLToken

Why you should delete your browser extensions right now - or do this to stay safe #BrowserExtensions #MaliciousCode #TrustedSources #CreditCardInformation #Linux #MacOS #Cyberthreat zdnet.com/article/why-yo…
Could your CI/CD pipeline be harboring malicious code silently? Red flags include obfuscated scripts, rogue CI jobs, unusual network calls, and secrets misuse. Dive in➡️ xygeni.io/blog/which-of-… #DevSecOps #MaliciousCode #AppSec #CI_CD #SupplyChainSecurity #Xygeni
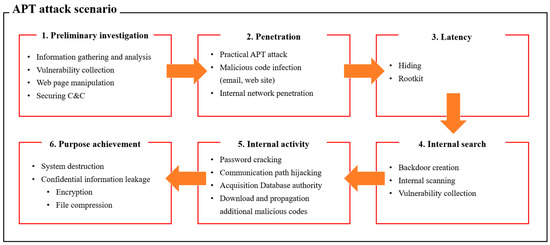
🔥 Read our Review Paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Kyungroul Lee et al. #maliciouscode #detectiontechnique
@FogoChain’s security continuously monitors smart contract bytecode for signs of obfuscated malicious code. #BytecodeMonitoring #MaliciousCode?
Socket researchers found Go modules rigged with code to wipe Linux disks, exposing new risks in open source supply-chain security. #LinuxSecurity #SupplyChainAttack #MaliciousCode

The discovery of security vulnerabilities in Apple AirPlay has raised concerns about the potential for hackers to access networks and disseminate malicious code among different devices. bit.ly/3ERYUUE #MaliciousCode #Cybersecurity #IncreasedRisk

It's not exactly something that is going to affect users but still wild to see such a blatant use of malicious code in the wild. #javascript #cookies #maliciouscode
We're just gonna leave this here.. Knowledge is power. The more you know... #MaliciousCode #HackThePlanet #Anonymous thehackernews.com/2025/03/coffee…
🚨 A new attack method, Rules File Backdoor, targets AI code editors like GitHub Copilot and Cursor, allowing hackers to stealthily inject malicious code. Supply chain risks rise! ⚠️ #AIThreats #MaliciousCode #USA link: ift.tt/jvxtfl4

🔓🔑Vulnerable ASP.NET Keys Used to Unlock PC Security💻 Attackers exploiting exposed #ASPNETkeys to inject #maliciouscode into web apps, leading to unauthorized access & potential data breaches. Read 👇 tinyurl.com/aspnk1010 #maliciousViewState #Microsoft
🚨 Would You Spot a Malicious Code Attack in Time? Learn how to identify and neutralize threats before they wreak havoc➡️xygeni.io/blog/indicator… #CyberSecurity #ThreatDetection #MaliciousCode #ApplicationSecurity #DevSecOps #SecureCoding #Xygeni
xygeni.io
Indicators of a Malicious Code Attack
Learn to detect indicators of a malicious code attack with Xygeni. Automate SCA, secrets security, and IaC scanning to stay secure now!
**DOWNLOAD IT NOW** - Tips for Reverse-Engineering #MaliciousCode **CHEAT SHEET** by @lennyzeltser Get it here --> digital-forensics.sans.org/u/K5Z Learn #REM with #FOR610 & @edygert in #SanFrancisco 11/26-12/1 Register--> sans.org/u/JqW | #DFIR

🔎Sophisticated #cybersecurity threats, like "FUD" #crypters, make #maliciouscode fully undetectable for stealthy infiltrations. Our #research paper explores #FUD markets in the #deepweb and their impact on cybersecurity. Read it here 👇 socradar.io/underground-fu…

Be careful when you visit websites as there are many ads and one is infected that will search for vulnerabilities to infect your system... #vulnerability #maliciouscode #malware #computervirus #staysafe #cyber #cybersecurity #gisec #ftw #april2019 #myDubai

Hiding #MaliciousCode With “#ModuleStomping” - bit.ly/30b8VTg-Ttx #AlizHammond via @FSecure ➡️ #ThreatIntelligence #IDAPro #ShellCode #Exploits #MalwareAnalysis #VirtualAlloc #InfoSec #CyberThreats #Malware #CyberAttacks #CyberDefense #ITsecurity

#MaliciousCode In The #PureScript Npm Installer version 3.0.2 And Later- bit.ly/2YUpxxP-Ttx @hdgarrood ➡️ #CyberThreats #Exploits #CyberRisks #InfoSec #Security #CyberSecurity #SecurityPros #CyberAttacks #Vulnerabilities

#MalwareAnalysis: #Arm'd & Dangerous, #MaliciousCode Now Native On (#AArch64 #M1) #Apple Silicon bit.ly/3k5dE3H-Ttx @patrickwardle 𝞝 #Enterprises #Organizations #Malware #CyberThreats #InfoSec #macOS #CyberSecurity #AppleSafari #BrowserExtensions #Rosetta #JavaScript




🔥 Read our Review Paper 📚 Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack 🔗 mdpi.com/2076-3417/13/5… 👨🔬 by Kyungroul Lee et al. #maliciouscode #detectiontechnique

RT @sucurisecurity Everything you need to know on SEO, as part of your website security. sucur.it/2X22PqQ #SEOSpam #websitesecurity #maliciouscode #SEO

#CrossSiteScripting is one of the most common vulnerabilities in #WebApps because the attacker has the ability to run #MaliciousCode within the user’s browser. 💻 Learn more about the 3 variants and how you can mitigate security risk here: ow.ly/wH9W50FQuNo
Over 100,000 repositories on #GitHub are infected with #MaliciousCode. Check out this lab collection to defend against these threats: Check out the collection today: 🔒 hubs.ly/Q02n4LZk0 🔒 hubs.ly/Q02n4J8H0 🔒 hubs.ly/Q02n4SNX0

Some (Ordinals) BTC NFTs have in the pdf malicious code executing instructions in javascript. This code is stealing all user's cryptocurrencies by just opening the PDF. (the code scans the MMwallet and Phantom). Part of the code is in the attached image. #maliciouscode #pdf

Linux systems can still be hacked via USB sticks scmagazineuk.com/linux-systems-… #ciso #MaliciousCode #MemorySticks #Patch #Prevention #USB

Cybercriminals are using the artificial intelligence-driven ChatGPT to create malicious tools and facilitate fraud. #artificialintelligence #maliciouscode #threatactor #security #cybercriminals #OpenAIChatGPT #openai #ChatGPT

Something went wrong.
Something went wrong.
United States Trends
- 1. GTA 6 60.8K posts
- 2. GTA VI 21.5K posts
- 3. Rockstar 52.7K posts
- 4. Antonio Brown 5,901 posts
- 5. GTA 5 8,705 posts
- 6. Nancy Pelosi 129K posts
- 7. Ozempic 19.2K posts
- 8. Paul DePodesta 2,183 posts
- 9. Rockies 4,265 posts
- 10. #LOUDERTHANEVER 1,541 posts
- 11. Grisham 1,934 posts
- 12. GTA 7 1,360 posts
- 13. Justin Dean 1,871 posts
- 14. Kanye 26.5K posts
- 15. Free AB N/A
- 16. Grand Theft Auto VI 44.5K posts
- 17. Fickell 1,117 posts
- 18. Elon Musk 235K posts
- 19. Silver Slugger 3,390 posts
- 20. RFK Jr 31.3K posts