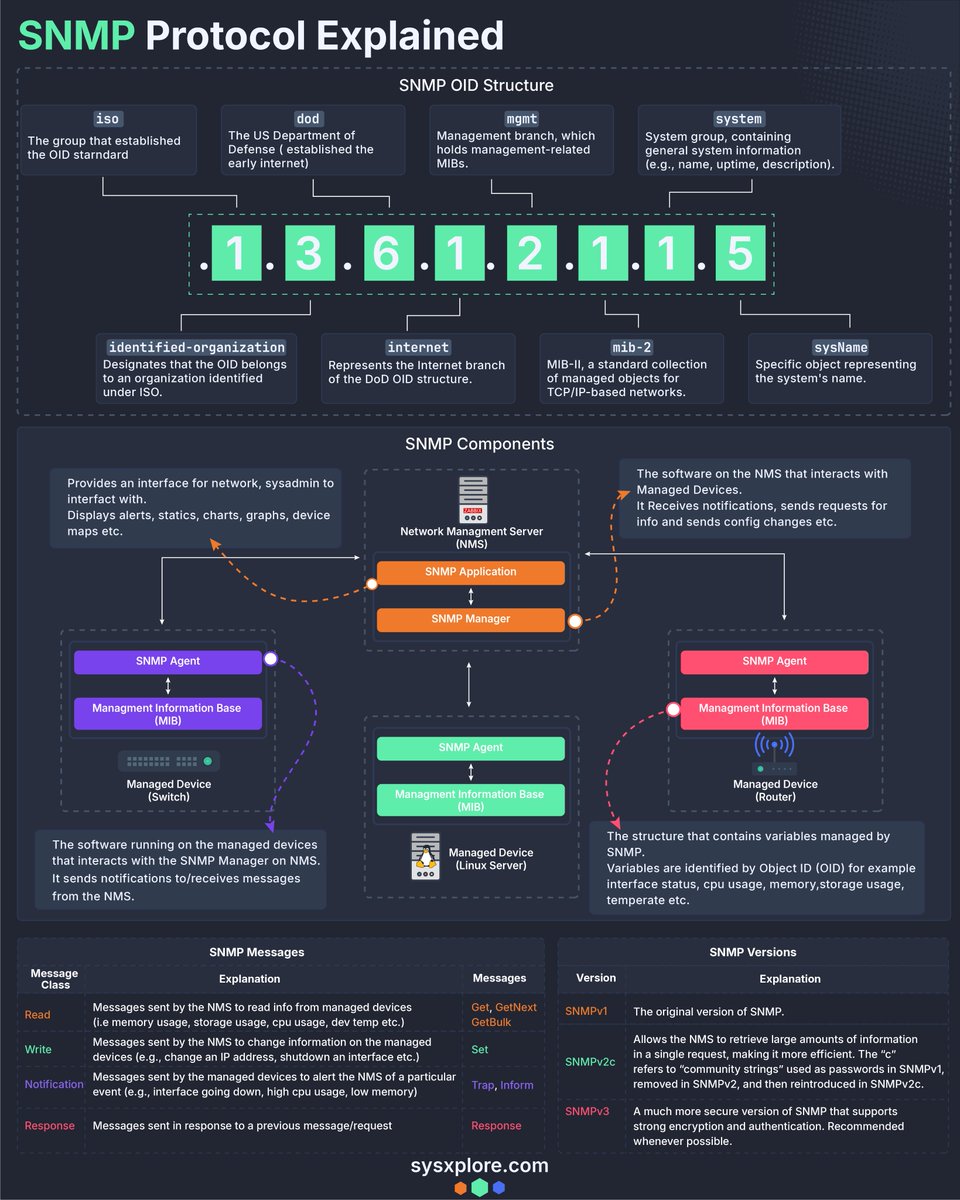
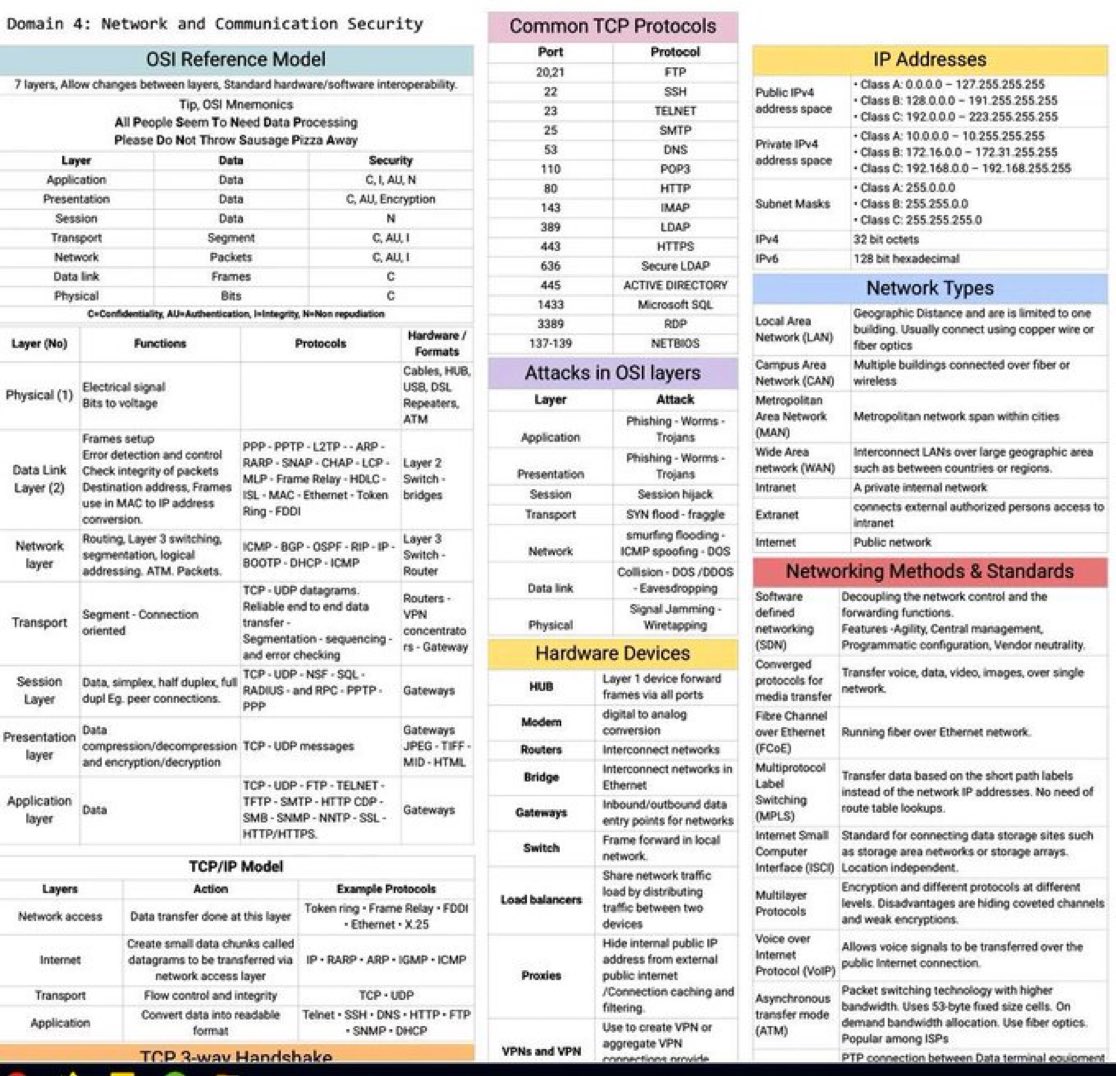
#networksecurityprotocols 검색 결과
🔒 Embark on a journey through the intricacies of 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐏𝐫𝐨𝐭𝐨𝐜𝐨𝐥𝐬! #CyberSecurityJourney #DigitalDefense #NetworkSecurityProtocols #CyberGuardians #CyberSafety #OnlinePrivacy #DigitalSecurity #CyberResilience #infosectrain #learntorise
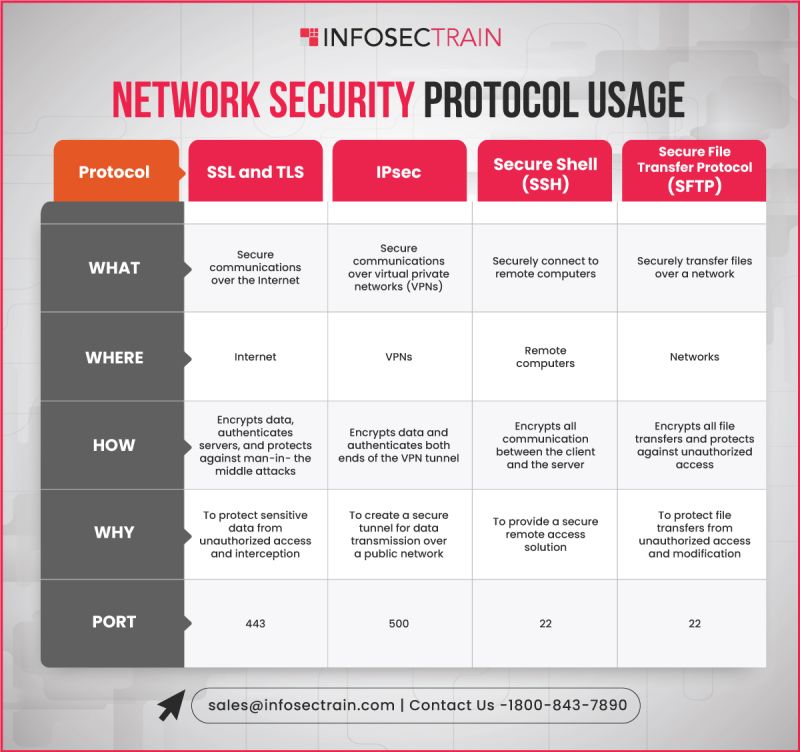
Optimize network security. Integrate hardware and software for robust safeguarding. #networksecurity #networksecurityprotocols #itsecurityservice #itsecuritysolutions #cyberdefense #digitalsecurity #securitysolutions #VareliTecnac #VTPL #solutionssimplified

Optimize security. Network protection ensures robust defenses—safeguarding data integrity, ensuring business continuity, and fortifying against potential threats. 🛡️ #networksecurity #networksecurityprotocols #itsecurityservice #itsecuritysolutions #cyberdefense #VareliTecnac

Network Security Protocols room is good refresher. tryhackme.com/room/networkse… #tryhackme #security #networksecurityprotocols via @realtryhackme
The world is changing. Security breaches are growing every day. KYC can’t solve this only @idOS_network can. Either become history with security flaws, or secure your future.

We’re excited to share that Certik is conducting a full security audit of the Qubetics dVPN and Chain Abstraction Protocol, a key milestone as we advance toward mainnet. This audit reinforces our commitment to building a secure, resilient, and transparent Web3 infrastructure.

GM Across the digital landscape, a vast and open frontier unfolds one that demands guardians to protect and shape it. That’s where @wardenprotocol comes in. Standing as the immutable layer where asset security meets decentralized intent, the network redefines what it means to…

Your data should follow you, not the app. @idOS_network makes that possible, keeping personal information private, secure, and fully under your control. For businesses, idOS solves a critical bottleneck: KYC re-sharing. Builders can verify users once, comply with regulations,…

#Day58 of #100DaysOfCybersecurity Today, I explored Firewalls & Intrusion Detection Systems (IDS) — two of the most essential components in network defense. They serve as the first line of protection against unauthorized access, malicious traffic, and suspicious network…

[@idOS_network:init] → attester_linked:true → credential_status:verified → encryption:active → storage_layer:L1 → access_control:on-chain → cross_chain:enabled(40+) System integrity: stable Human node: sovereign Data flow: permissioned State updated →…
![v__duncan's tweet image. [@idOS_network:init]
→ attester_linked:true
→ credential_status:verified
→ encryption:active
→ storage_layer:L1
→ access_control:on-chain
→ cross_chain:enabled(40+)
System integrity: stable
Human node: sovereign
Data flow: permissioned
State updated →…](https://pbs.twimg.com/media/G3X6XuwWcAAfLQU.jpg)
Lenovo CVE-2025-8061: PoC for popping a system shell against the LnvMSRIO.sys driver GitHub: github.com/symeonp/Lenovo…


Network ports and protocols You will need this for your network+ and security+.

Best of TCP/IP Cheatsheet Credit: networkwalks.com/networkwalks-s… #infosec #cybersecurity #pentesting #oscp #informationsecurity #hacking #DataSecurity #CyberSec #Hackers #tools #bugbountytips #Linux #websecurity #Network #NetworkSecurity #cybersecurityawareness

Your assets deserve better security. Your data deserves better insight. @wardenprotocol and @KaitoAI bring both to Web3. Secure smarter. Build faster. #WardenProtocol #CryptoSecurity #AI A PFP made by @wardenprotocol is below

Something went wrong.
Something went wrong.
United States Trends
- 1. Flacco 86.3K posts
- 2. Bengals 81.3K posts
- 3. Bengals 81.3K posts
- 4. Tomlin 22K posts
- 5. #clubironmouse 3,119 posts
- 6. Ramsey 19.3K posts
- 7. #criticalrolespoilers 8,235 posts
- 8. Chase 108K posts
- 9. Chase 108K posts
- 10. #WhoDidTheBody 1,619 posts
- 11. yeonjun 119K posts
- 12. #WhoDey 6,906 posts
- 13. #SEVENTEEN_NEW_IN_LA 45.7K posts
- 14. Cuomo 85.6K posts
- 15. Teryl Austin 2,819 posts
- 16. Andrew Berry 3,293 posts
- 17. Xenoverse 3 N/A
- 18. Tame Impala 5,627 posts
- 19. Max Scherzer 14.6K posts
- 20. Burrow 9,955 posts