#securitychecklist search results
"It takes 20 years to build a reputation & a few minutes of cyber-incident to ruin it.” - Stephane Nappo With #cybercrime increasing YoY, here is the mobile #appdevelopment #securitychecklist that can help your app remain secured against every common vulnerabilities. #checklist

#SecurityChecklist: #Protect Your #MongoDB Installation - bit.ly/2YC5IKR-Ttx @MongoDB ➡️ #NetworkSecurity #CyberAttacks #SoftwareBugs #Vulnerabilities #CyberRisks #InfoSec #infosec #BestPractices #GoodPractices #AccessControl #StrongAuthentication

How to prepare a Security Checklist for a New School Year bit.ly/3hvTOP4 #securitychecklist #campuslockdown #schoolsecurity

Use our #SecurityChecklist to categorize each #SaaS application in your organization hubs.ly/y0QJnf0

We talk about #CyberSecurity every single day, and we repeat the key points below to our members almost every single day too! Take a moment to make sure you're doing the basics in this handy and simple checklist. #SecurityChecklist | #ThursdayMorning ▶️emcrc.co.uk/post/what-shou…
There are many things to consider when selecting or upgrading your security systems provider and service company. Does your integrator offer everything on this 3-Phase Checklist? bit.ly/2GetNmM #TEAM101 @Security_101 #SecurityChecklist

How secure is your business? 🤔 Find out through our Interactive SMB Cybersecurity Checklist: marconet.co/3NKF0Ji #Cybersecurity #NetworkSecurity #SecurityChecklist

If you are the owner of a website, keeping your website safe is the first utmost work to do. Thus we have curated an 11 point Checklist goo.gl/ycne48 to secure your website from hackers. #WordPress #WebsiteSecurity #SecurityChecklist

Getting one of your personal devices hacked is probably one of your worst nightmares. However, many still fail to follow some really important steps to keep your data secure. Here is a good checklist. buff.ly/2QKAm0x #onlinesecurity #keepyourdatasafe #securitychecklist

If you are the owner of a website, keeping your website safe is the first utmost work to do. Thus we have curated an 11 point Checklist goo.gl/ycne48 to secure your website from hackers. #WordPress #WebsiteSecurity #SecurityChecklist

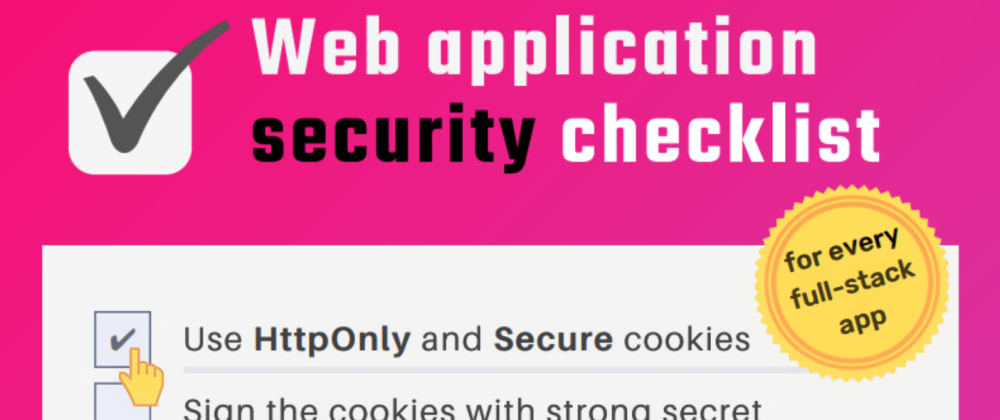
Is your website secure? Not know then @pietrucha share list of all the most important security checks for your Web applications- bit.ly/2Hf7n6x #securitytips #securitychecklist #websitesecurity #WebApplicationsSecurity
Cybersecurity should be the heart of your IT department, but where should you start? Download our Cybersecurity Checklist and make sure your IT infrastructure is secure. Get access here: ow.ly/lRCr50GgXvP #ITsecurity #cybersecurity #securitychecklist

Crucial tips on #joomlasecurity. We made our own #securitychecklist – adding couple of extra tips. goo.gl/yJYHii

By going through this event #securitychecklist together, both the event planners and the #security company can discuss what the best security operation is for the event and set expectations early: tinyurl.com/4zcjrnem

Want to make sure you #staycybersafe at home? Download our #securitychecklist for #remoteworkers to keep your #futureworkplace safe: ow.ly/FCUC50zfD1h #becybersmart #cybersecurity #workfromhomeguide

Do you need to secure your retail or restaurant location? [Download] 📩 our printable checklist of security features and emergency procedures to ensure your system is up to standards. hubs.ly/H0m3vm80 #restaurantsecurity #retailsecurity #securitychecklist #solink
![SolinkCorp's tweet image. Do you need to secure your retail or restaurant location? [Download] 📩 our printable checklist of security features and emergency procedures to ensure your system is up to standards. hubs.ly/H0m3vm80 #restaurantsecurity #retailsecurity #securitychecklist #solink](https://pbs.twimg.com/media/ELW2CMRWwAEwVtC.png)
A Robust Workplace Security Checklist for Every Business #workplacesecurity #securitychecklist #securitytips #SecureBusiness #officesecurity #AccessControl #physicalsecurity #RiskManagement #cybersecurity #BusinessRisk #potentialthreats #encryptdata tycoonstory.com/a-robust-workp…

Lastly, do a quick permissions cleanse. Revoke all access for former staff or systems that no longer need it. Take the biggest risk you flagged and make a concrete plan to fix it this week. You are all set! #CyberAwareness #DataPrivacy #SecurityChecklist
5/5 Level up your VM program today. Get the blueprint, stop the chaos. Download the Checklist: cybersecurityos.gumroad.com/l/vulnerabilit… #Cybersecurity #SecurityChecklist #GCP #SecurityEngineering #CISO #CybersecurityOS

Giverep’s security checklist helps you stay safe! Follow the steps, protect your crypto. #SecurityChecklist @Giverep
🤝📲 Closing a home is stressful enough—don’t let wire fraud add to it. This guide gives builders & buyers clear, actionable defenses. 📘 Learn the steps: bit.ly/4lXgo1t #RealEstateTips #SecurityChecklist #FraudPrevention #ZondaMediaIntel #Sponsored #FirstAmericanTitle
"🔒 Wallet Security Checklist: 10 steps to protect your funds! Daily, weekly, and monthly tasks. #SecurityChecklist #Protect @MMTFinance"
CMOs: Are you part of the security conversation? If not, it’s time to join in. 💬 🔒 Not sure where to start? Read our full guide: eu1.hubs.ly/H0lBTk10 #WordPress #SecurityChecklist #Marketing #DigitalTrust #CyberSecurity #CMO #BrandProtection #MarTech

If you answered NO to any of these, it’s time to act. Contact N5 Security today to schedule a professional security audit and start 2025 with total confidence. 📞 0203 930 0702 🌐 n5security.co.uk #SecurityChecklist #BusinessProtection #N5Security #WorkplaceSafety
✅ Saturday Security Checklist! 🛡️ Weekend IT health check for Arizona businesses: □ Update software □ Check backups □ Review user access □ Test firewall □ Scan for threats Need help? Call 602-427-5617 #SecurityChecklist #WeekendSecurity #ArizonaBusiness #ElevatedITGroup…
We’d love to hear your go-to tips 👇 #VPNUnlimited #DigitalHygiene #SecurityChecklist #DailyHabits
94% of businesses reported email-related security incidents in 2024. Cyber attacks are growing fast — is your company prepared? Here are the policies you need now… reintivity.com/by-content-typ… #CyberSecurity #SecurityChecklist #BusinessSafety

Cyber threats evolve—so should your compliance strategy. Partner with VanRein Compliance today! We offer proactive services to help you stay ahead: ✅NIST Cybersecurity Audit ✅Cybersecurity Tabletop Exercises #Cybersecurity #CyberCompliance #SecurityChecklist

🚨 Your AI systems are more vulnerable than you think! Our essential #SecurityChecklist reveals the 5 critical blind spots hackers are exploiting RIGHT NOW. #DevSecOps teams can't afford to miss this in 2025 👉 practical-devsecops.com/ai-security-ch…
📋 If you missed a point — it’s time to act. Contact N5 Security today and let’s get your business fully protected. 📞 0203 930 0702 🌐 n5security.co.uk #BusinessSecurity #SecurityChecklist #N5Security #SecureYourBusiness #WorkplaceSafety #SecurityMatters
Cold wallet security checklists: What's on your list? Share your best practices here! #SecurityChecklist #CryptoBestPractices ift.tt/N39ghYO Join the discussion, comment & follow!
cryptomaps.tech
Best Offline Cold Wallets to Keep Your Crypto Safe
Best Offline Cold Wallets to Keep Your Crypto Safe
✅ 6 simple steps to a more secure Google Workspace. Our checklist makes it easy to identify vulnerabilities and implement best practices for data protection ➡️ bit.ly/4h98sbi #SecurityChecklist #GoogleWorkspace #DataSecurity #BestPractices

Is your #security plan outdated? 🚨 Look out for these warning signs! 1️⃣ Increasing theft or vandalism 2️⃣ Poorly lit premises 3️⃣ Lack of professional guards 4️⃣ Delayed emergency response 5️⃣ Outdated surveillance systems #securitychecklist #staysafe #BlackstormSecurity

"It takes 20 years to build a reputation & a few minutes of cyber-incident to ruin it.” - Stephane Nappo With #cybercrime increasing YoY, here is the mobile #appdevelopment #securitychecklist that can help your app remain secured against every common vulnerabilities. #checklist

How to prepare a Security Checklist for a New School Year bit.ly/3hvTOP4 #securitychecklist #campuslockdown #schoolsecurity

#SecurityChecklist: #Protect Your #MongoDB Installation - bit.ly/2YC5IKR-Ttx @MongoDB ➡️ #NetworkSecurity #CyberAttacks #SoftwareBugs #Vulnerabilities #CyberRisks #InfoSec #infosec #BestPractices #GoodPractices #AccessControl #StrongAuthentication

Cyber threats evolve—so should your compliance strategy. Partner with VanRein Compliance today! We offer proactive services to help you stay ahead: ✅NIST Cybersecurity Audit ✅Cybersecurity Tabletop Exercises #Cybersecurity #CyberCompliance #SecurityChecklist

There are many things to consider when selecting or upgrading your security systems provider and service company. Does your integrator offer everything on this 3-Phase Checklist? bit.ly/2GetNmM #TEAM101 @Security_101 #SecurityChecklist

How secure is your business? 🤔 Find out through our Interactive SMB Cybersecurity Checklist: marconet.co/3NKF0Ji #Cybersecurity #NetworkSecurity #SecurityChecklist

Is your website secure? Not know then @pietrucha share list of all the most important security checks for your Web applications- bit.ly/2Hf7n6x #securitytips #securitychecklist #websitesecurity #WebApplicationsSecurity

The Ultimate Security Check List for 2020! 😆 . . . #SecurityChecklist #Security #CyberSecurity #WebsiteJoke #Jokes #ITJoke #WebDevelopment #Website #USHosting #HostingUS #WebHosting

Cybersecurity should be the heart of your IT department, but where should you start? Download our Cybersecurity Checklist and make sure your IT infrastructure is secure. Get access here: ow.ly/lRCr50GgXvP #ITsecurity #cybersecurity #securitychecklist

A Robust Workplace Security Checklist for Every Business #workplacesecurity #securitychecklist #securitytips #SecureBusiness #officesecurity #AccessControl #physicalsecurity #RiskManagement #cybersecurity #BusinessRisk #potentialthreats #encryptdata tycoonstory.com/a-robust-workp…


Is your business secure? Use our interactive checklist to conduct a thorough security audit. #BusinessSecurity #RouteWatche #SecurityChecklist




Free checklist to help you choose the right #CloudPartner goo.gl/mPFWjd #securitychecklist @Office @Office365MS

By going through this event #securitychecklist together, both the event planners and the #security company can discuss what the best security operation is for the event and set expectations early: tinyurl.com/4zcjrnem

@orege kicking off @mobileiron #sko2018. Do you know where your data is on Friday night? #EMM #securitychecklist

CMOs: Are you part of the security conversation? If not, it’s time to join in. 💬 🔒 Not sure where to start? Read our full guide: eu1.hubs.ly/H0lBTk10 #WordPress #SecurityChecklist #Marketing #DigitalTrust #CyberSecurity #CMO #BrandProtection #MarTech

Protecting Your Digital World: Device Posture Checklist 🔒 In today's digital landscape, ensuring the security of your data is important . That's why we're sharing our Device Posture Checklist. zurl.co/kOCO #Cybersecurity #SecurityChecklist #ZeroTrust #InstaSafe

Something went wrong.
Something went wrong.
United States Trends
- 1. Packers 100K posts
- 2. Eagles 128K posts
- 3. Benítez 13.5K posts
- 4. Jordan Love 15.5K posts
- 5. Veterans Day 31K posts
- 6. #WWERaw 138K posts
- 7. LaFleur 14.8K posts
- 8. #TalusLabs N/A
- 9. AJ Brown 7,183 posts
- 10. Green Bay 19.1K posts
- 11. McManus 4,500 posts
- 12. Grayson Allen 4,375 posts
- 13. JOONGDUNK BRIGHT SKIN 216K posts
- 14. Sirianni 5,132 posts
- 15. Kevin Patullo 7,084 posts
- 16. Jaelan Phillips 8,230 posts
- 17. Smitty 5,618 posts
- 18. James Harden 2,031 posts
- 19. Jalen 24.2K posts
- 20. Berkeley 63.7K posts















































