#securityvulnerabilities 검색 결과
Jai shri Ram 🙏 got Bounty $$$ Thanks lord Krishna for this ! #BugBounty #SecurityVulnerabilities #InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware
#DigitalTransformation Brings #SecurityVulnerabilities, Canon Research Says - MSSP Alert bit.ly/2MxHik8

Episode 3 of The @ActiveState Podcast is out! In this episode, Nicole Schwartz and Martin Drohmann dive into the challenges of managing #SecurityVulnerabilities while meeting development deadlines. Watch the full episode: bit.ly/3VVUHVD
HOW TO TRAIN YOUR #Ghidra 🐉 a complex collection of #sourcecode with many third-party dependencies that are known to contain #securityvulnerabilities.👉 kas.pr/4kvx #cybersecuritytraining #ittraining #infosec #reverseengineering
#Jenkins released a new version that fixes multiple #SecurityVulnerabilities. Update now bitn.am/2JCHo3T

The Indian Computer Emergency Response Team (CERT-In) issued a critical advisory on August 2, warning of severe #securityvulnerabilities in various #Apple products. Read more: bit.ly/3yyGmFy

#SecurityVulnerabilities – a zero-day exploit had been discovered in #log4j, a popular #Java logging library. All the library’s versions between 2.0 and 2.14.1 included are affected. Find out more on #InfoQ: bit.ly/31Ldtpz @olimpiupop #SoftwareArchitecture #DevOps

#AI systems can be leveraged to insert hard-to-detect #SecurityVulnerabilities into computer chip designs, enabling even those with limited expertise to create sophisticated hardware attacks. @NYUTandon doi.org/g9576h techxplore.com/news/2025-10-a…
Insufficient logging and monitoring can slow down breach detection and worsen the impact of #SecurityVulnerabilities! ⚠️ Make sure you follow security logging standards, like #OWASP Logging Cheat Sheet guidelines, and enforce separate, restricted access controls. You can use…

MS-LLTD, MDNS, and ICMPv6 represent three commonly employed #networkprotocols, carrying potential #securityvulnerabilities that might not have caught your attention. Check out our #PenteraLabs research to learn more about the business risk they pose: okt.to/nm4UED
Qodana’s intuitive interface makes team onboarding easier! You can use the sunburst diagram to filter, identify, and address issues directly in your IDE. Try it now: jb.gg/vtt82l #CodeQuality #SecurityVulnerabilities #QodanaCloud
Congrats to @Dooflin5 + Jesse Victors for having their research accepted to @thotcon 2023! Their selection demonstrates the high level of expertise our #SecurityEngineers have and places them among the best for identifying + solving even the most unique #securityvulnerabilities.

Understanding the human factor of #digitalsafety techradar.com/pro/understand… @TechRadarPro #securityvulnerabilities

#Log4shell was one of the most critical #SecurityVulnerabilities of the current history. Read the #InfoQ Q&A with Arshan Dabirsiaghi and learn how #ContrastSecurity took an alternative approach to fix the issues: bit.ly/34Xbr6Y @olimpiupop #Java #DependencyManagement

#SecurityVulnerabilities - A new vulnerability in the CRI-O container runtime used by many #Kubernetes installations allows a malicious user to gain root access to the host. The vulnerability was fixed by the CRI-O project: bit.ly/3uI3Bat @talonx #InfoQ #Containers

Severe weather events cause disruptions that could lead to #SecurityVulnerabilities. @barracuda's @GregArnette shares tips on protecting #data in the age of #ClimateChange, via @ITProToday @karendschwartz: ow.ly/8qtD30oLbYb #Cybersecurity #BCDR

Software companies typically provide #softwareupdates for 3 reasons: to add new features, fix known bugs, and #upgradesecurity. Always update to the latest version of your software to protect yourself from new or existing #securityvulnerabilities. 💻 #cybercrime #datasecurity

33 vulnerabilities found in embedded open source networking stacks @Forescout #Amnesia33 #SecurityVulnerabilities #IoT #TCPIP #Authentication #EmbeddedSoftware tinyurl.com/y3pncwg9

Some risks -- like #SecurityVulnerabilities and system downtime -- are obvious, others not so much. Good #PatchManagement also requires weighing the possible risks of patching: bit.ly/4ajdA8M

One security breach is enough to destroy years of work! Shocking statistics: •An attack every 11 seconds •95% of breaches were preventable Try this: Enable two-factor authentication now! #SecurityVulnerabilities #DigitalSafety #SecurityTips

Insufficient logging and monitoring can slow down breach detection and worsen the impact of #SecurityVulnerabilities! ⚠️ Make sure you follow security logging standards, like #OWASP Logging Cheat Sheet guidelines, and enforce separate, restricted access controls. You can use…

🚨 New Writeup Alert! 🚨 "Ehxb | File Upload Vulnerabilities I" by Ehxb is now live on IW! Check it out here: infosecwriteups.com/6ed033539682 #hackthebox #securityvulnerabilities #portswigger #tryhackme #hacking
#AI systems can be leveraged to insert hard-to-detect #SecurityVulnerabilities into computer chip designs, enabling even those with limited expertise to create sophisticated hardware attacks. @NYUTandon doi.org/g9576h techxplore.com/news/2025-10-a…
#SecurityVulnerabilities #Reputation #InvestorProtection #Compliance #Functionality #CodeQuality as your presale is life get an audit and protect your investors
#SecurityResearchers have found that in roughly 80% of cases, spikes in malicious activity are a precursor to the disclosure of new #SecurityVulnerabilities (CVEs) within six weeks. #Cybersecurity ow.ly/sXYM50WCVr1
WordPress vulnerability in three popular file manager plugins installed in up to 1.3 million sites enables arbitrary file deletion. #wordpressplugins #SecurityVulnerabilities searchenginejournal.com/vulnerability-…
searchenginejournal.com
Vulnerability In 3 WordPress File Plugins Affects 1.3 Million Sites
WordPress vulnerability in three popular file manager plugins installed in up to 1.3 million sites enables arbitrary file deletion
🚨 Security Nightmare? AI-powered developer tools built on the #ModelContextProtocol (MCP) are introducing critical #SecurityVulnerabilities like: ➡️ Credential leaks ➡️ Unauthorized file access ➡️ Remote code execution 🔗 bit.ly/40XihDE #AIagents #Security

Insufficient logging and monitoring can slow down breach detection and worsen the impact of #SecurityVulnerabilities! ⚠️ Make sure you follow security logging standards, like #OWASP Logging Cheat Sheet guidelines, and enforce separate, restricted access controls. You can use…
Untrusted and risky automation solutions, like Telegram bots, expose users to hacks, phishing, and systemic risks. @MagicNewton offers a secure alternative. #SecurityVulnerabilities #RiskyAutomation
Untrusted and risky automation, often via Telegram bots, exposes users to hacks, phishing, and systemic risks. @MagicNewton #PrivateKeyRisk #SecurityVulnerabilities
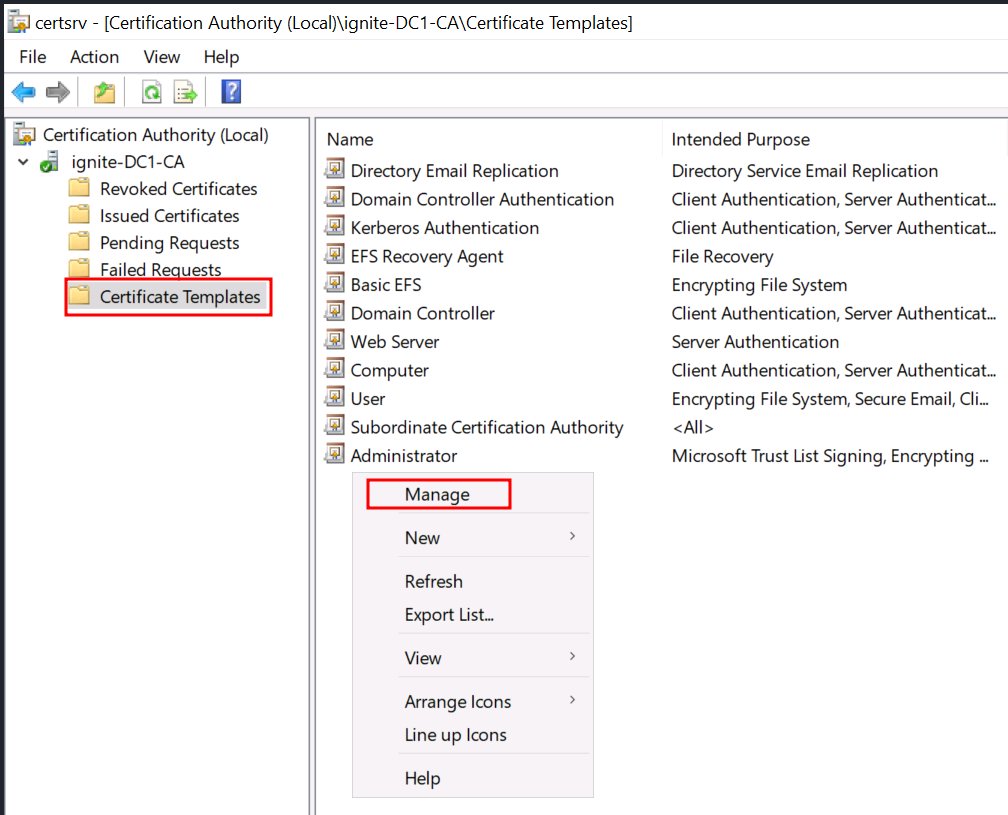
Misconfigured AD CS certificate templates with ESC9 enable privilege escalation—attackers can impersonate Domain Admins by exploiting weak certificate mappings and security extensions. Stay vigilant! 🛡️ #ActiveDirectory #SecurityVulnerabilities ift.tt/PmOYbLV
🛡️ $302M crypto losses in May expose critical #SecurityVulnerabilities. @CertiK reveals code exploits driving massive industry risk. Will stricter #SmartContract audits restore investor confidence? Urgent protocol review needed.
Google Releases June Security Bulletin for Android Devices to Fix Vulnerabilities | Linn Freedman, Data Privacy + Cybersecurity Insider dataprivacyandsecurityinsider.com/2025/06/google… #Google #Android #securityvulnerabilities
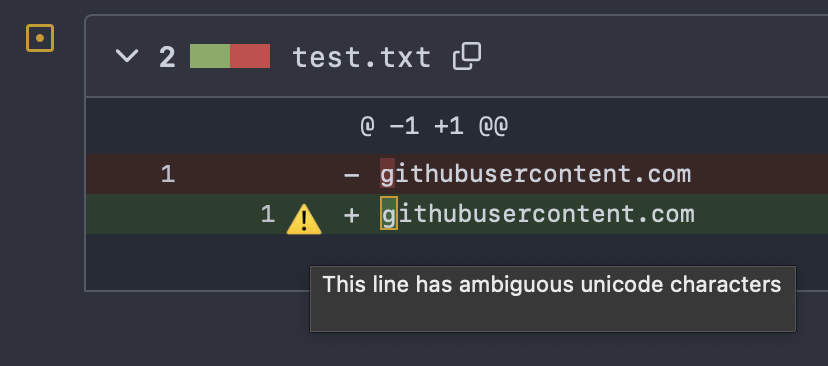
Malicious Unicode? 🛑 It can happen to the best of us. A recent post by @badger highlights how these characters can sneak past code reviews! daniel.haxx.se/blog/2025/05/1… Qodana’s NonAsciiCharacters inspection flags this to help you catch hidden #securityvulnerabilities
Bug bounty hunters have earned $2M+ on FOGO, identifying 500+ critical vulnerabilities since 2023. #BugBountyPayouts #SecurityVulnerabilities
JUST IN: Critical security vulnerabilities found in the Model Context Protocol (MCP). Threats include Tool Poisoning, Rug-Pull Updates, Retrieval-Agent Deception, Server Spoofing, and Cross-Server Shadowing. User safety and data integrity at risk. #MCP #SecurityVulnerabilities
Jai shri Ram 🙏 got Bounty $$$ Thanks lord Krishna for this ! #BugBounty #SecurityVulnerabilities #InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware

#DigitalTransformation Brings #SecurityVulnerabilities, Canon Research Says - MSSP Alert bit.ly/2MxHik8

#Jenkins released a new version that fixes multiple #SecurityVulnerabilities. Update now bitn.am/2JCHo3T

#SmartHomes #SecurityNews #SecurityVulnerabilities #CyberAttack #CyberSecurityUpdates #CyberSecurityEvent #CyberSecurityReport #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace

🌟 Meet Sahil Bugade, a passionate cybersecurity enthusiast from MIT ADT University! 🚀 Recently, he made history by entering NASA's Hall of Fame for uncovering a security vulnerability in their digital assets. 🛡️ #CybersecurityHero #NASA #SecurityVulnerabilities #MITADT

Severe weather events cause disruptions that could lead to #SecurityVulnerabilities. @barracuda's @GregArnette shares tips on protecting #data in the age of #ClimateChange, via @ITProToday @karendschwartz: ow.ly/8qtD30oLbYb #Cybersecurity #BCDR

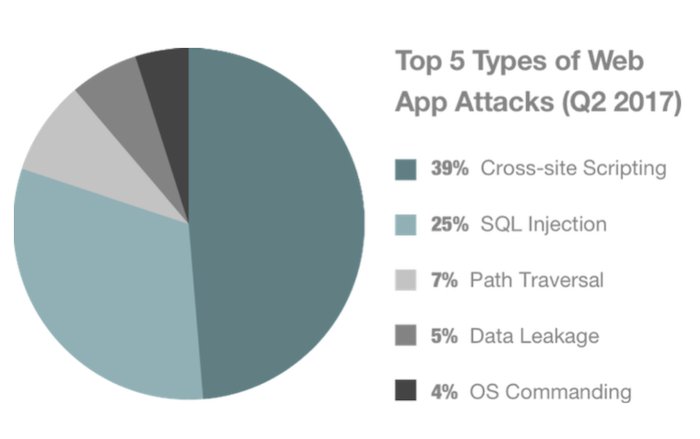
How to correct #SecurityVulnerabilities in #WebApplications? @RStyleLab shares some useful tips for businesses buff.ly/2HEELlc #WebDevelopment #WebApps #WebAppSecurity #CyberSecurity #CrossSiteScripting #SQLinjection #OpenSource via @clutch_co
33 vulnerabilities found in embedded open source networking stacks @Forescout #Amnesia33 #SecurityVulnerabilities #IoT #TCPIP #Authentication #EmbeddedSoftware tinyurl.com/y3pncwg9

Common Python Security Problems - websystemer.no/common-python-… #programming #python #securityvulnerabilities

Know how #MachineLearning is being used to handle #securityvulnerabilities by @farwa_sajjad96 via @datamadesimple bigdata-madesimple.com/machine-learni… #artificialintelligence #AI #ML #Cybersecurity #Security #technology #mistralsolutions

Understanding the human factor of #digitalsafety techradar.com/pro/understand… @TechRadarPro #securityvulnerabilities

Systemic Racism Is a Cybersecurity Threat on.cfr.org/3fzsdZw #CyberSecurity #SecurityVulnerabilities #AppsUnify

Is your company ready to face #cyberattacks? Komodo Consulting helps you identify #securityvulnerabilities in your application before hackers do. bit.ly/3tJCixt #datasecurity #cyberattacks #quotes

If you are using this plugin, we strongly recommend that you update to the latest version immediately to protect your site. Stay safe and secure online! #WordPress #OnlineCourses #SecurityVulnerabilities #ProtectYourSite

Congrats to @Dooflin5 + Jesse Victors for having their research accepted to @thotcon 2023! Their selection demonstrates the high level of expertise our #SecurityEngineers have and places them among the best for identifying + solving even the most unique #securityvulnerabilities.

“Found means fixed,” says @github's @_mph4 of the transformation unfolding with #AIAgents able to identify and fix software development #SecurityVulnerabilities in real-time. Watch Hanley, #OutshiftByCisco's @vijoy, and @VentureBeat's @LouisColumbus. 🎦 cs.co/6012m8CKm

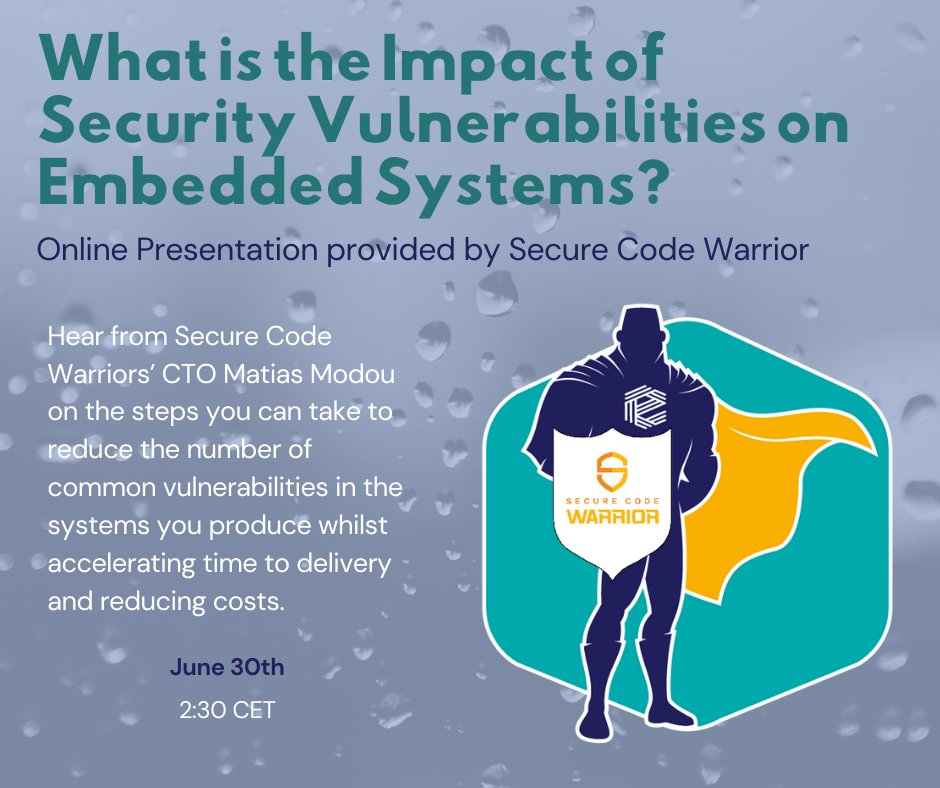
Join us on this 40 minute webinar being broadcast on 30th June 2020 at 2:30pm CET emenda.com/secure-code-wa… #SecurityVulnerabilities #EmbeddedSystems #Emenda #Webinar #SecCodeWarrior
Something went wrong.
Something went wrong.
United States Trends
- 1. Warner Bros 137K posts
- 2. HBO Max 61.2K posts
- 3. #FanCashDropPromotion 1,608 posts
- 4. #NXXT_CleanEra N/A
- 5. #FridayVibes 4,917 posts
- 6. Good Friday 61.2K posts
- 7. Paramount 29.6K posts
- 8. Ted Sarandos 4,576 posts
- 9. Jake Tapper 62.6K posts
- 10. NextNRG Inc 2,101 posts
- 11. Cyclist 2,391 posts
- 12. David Zaslav 2,269 posts
- 13. TINY CARS 1,863 posts
- 14. $NFLX 5,969 posts
- 15. The EU 149K posts
- 16. National Security Strategy 14.1K posts
- 17. Bandcamp Friday 2,163 posts
- 18. #FridayMotivation 4,860 posts
- 19. Core PCE 3,445 posts
- 20. #FridayFeeling 2,110 posts