#windowskernel search results
Dive into how the Windows kernel really works — from GS:KPCR to undocumented calls and root-kit hooks. #WindowsKernel #ReverseEngineering #MalwareAnalysis fluxsec.red/reverse-engine… fluxsec.red

Dive deep into 64-bit Windows kernel holes: how wild-copy + user-fault-handling primitives give an exploit chain in Ring-0. theori.io/blog/exploitin… #WindowsKernel #ReverseEngineering #ExploitDev

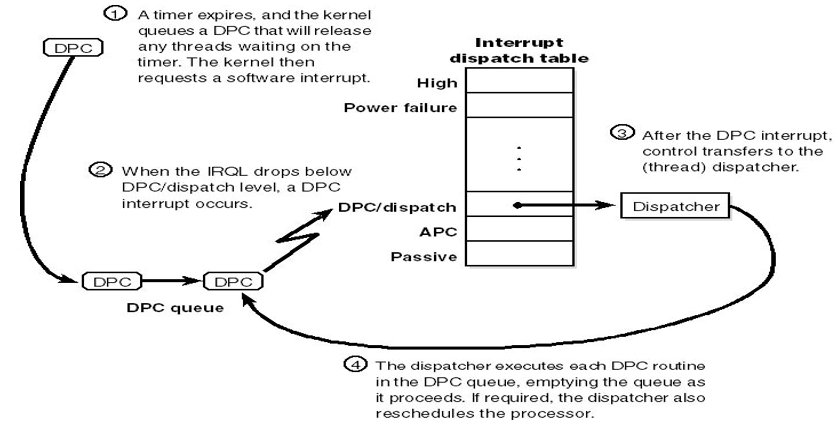
Delivering a Deferred Procedure Call (DPC). #KernelDebugging #WindowsKernel #WindowsInternals #WinDBG #DebugModeOn
Tonight’s workplace @windowsdev #WindowsKernel #WDF #NetAdapterCx #WinsockKernel #openvpn #ovpndco #ovpndcowin

IRQL storm on multi-core system? x86 routes interrupts via Local APIC → logical processor, not physical core. Windows KeSetTargetProcessor can misroute. Debug with !apic + !idt -a—wrong LAPIC ID = missed interrupts. #Interrupts #SMP #WindowsKernel
Are stack expansion and stack guard not present in the 64-bit version of Windows kernel? Stack Guard is not set in RtlCreateUserStack while creating the stack for a new thread #windowskernel #kernel
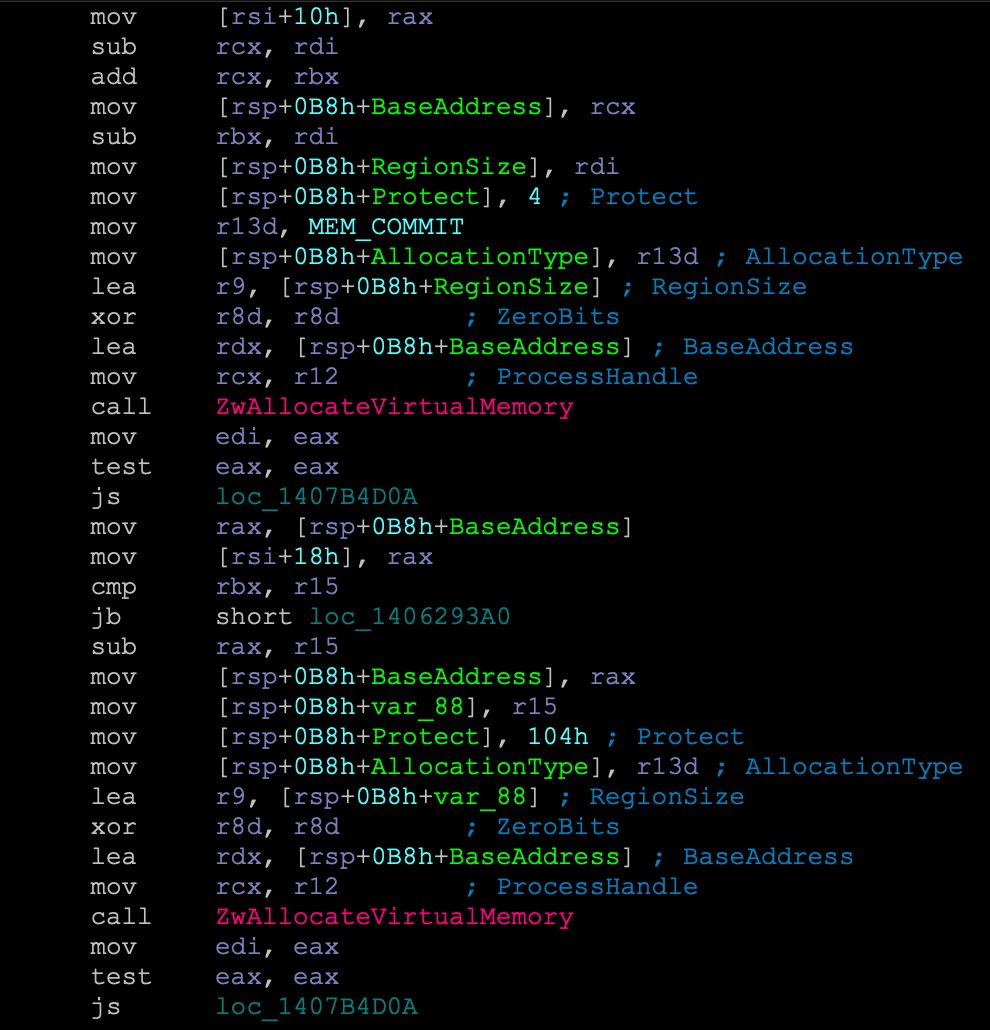
Signing a kenel driver that is built with MinGW, gcc stackoverflow.com/questions/6553… #mingw #gcc #windowskernel

How to display the PML4E, PDPTE, PDE and PTE of the PTE itself in windbg / kd? stackoverflow.com/questions/6673… #windows #windowskernel #pagetables #windbg #kd

Here is the training stats of our @nullcon Goa, 2020 training on "Windows Kernel Exploitation" 📊 You can check training stats in the gif below. 👇 Want to join our next training? #Cybersecurity #WindowsKernel #Cyberattack #Security #InfoSec #ITSecurity #InfoSecurity
🚨 Blog 6 is out! Jay Pandya breaks down Out-Of-Bounds in Windows kernel drivers—how it works, how it breaks, and why it matters. Read it now via White Knight Labs: whiteknightlabs.com/2025/07/01/und… #Infosec #WindowsKernel #CyberSecurity #ExploitDev

Exploring #WindowsKernel with #Fibratus and #Logsene #devops #devopsnews #guestpost by @rabbitstack bit.ly/2gERrr5

Microsoft patched a high-severity Windows Kernel privilege escalation vulnerability in February, six months after being informed that the flaw was being exploited as a zero-day. #Microsoft #WindowsKernel #vulnerability #securitypatch #zeroday #cybersecurity #WindowsAppLocker
Windows 10 bug 0xD1 DRIVER_IRQL_NOT_LESS_OR_EQUAL caused by tunnel.sys dereferencing NULL during Teredo flow teardown. A race condition between tcpip!LruCleanupDpcRoutine and tcpip!UdpCloseEndpoint triggers the crash. #WindowsKernel #RaceCondition ift.tt/nglMaV3
hendryadrian.com
BugCheck 0xD1: Potential race condition in Teredo cleanup during flow teardown
A Windows 10 kernel-only crash dump (build 19041) shows a 0xD1 DRIVER_IRQL_NOT_LESS_OR_EQUAL caused by tunnel.sys (Teredo) dereferencing a NULL previous pointer while unlinking a flow list entry,...
🚀Boost your skills to the kernel level! 🖥️Learn the basics of Windows & driver internals, different memory corruption classes & fuzzing of kernel-mode drivers by Ashfaq @HackSysTeam 🎟️Get your ticket➡️bit.ly/3NWsFCH #NullconGoa2022 #training #windowskernel #infosec

Join our free #webinar: 🎯 "Windows Kernel Exploitation for Red Team Operators" 👉 loom.ly/VTXooaA This talk will guide you step-by-step into the world of #WindowsKernel exploitation, offering insights and tools needed to adapt and excel in modern #RedTeam operations.

#Vulnerabilities: #WindowsKernel cng.sys Pool-Based Buffer Overflow In #IOCTL 0x390400 - bit.ly/2GkXgwj-Ttx #ProjectZero @google 𝞝 #Enterprises #Organizations #SecurityFlaws #InfoSec #PrivilegeEscalation #CyberSecurity #DoS #PrivilegeEscalation #Cryptography #Exploitation

Liberan 71 parches de seguridad por recientes ataques a #MicrosoftOffice y #WindowsKernel. bit.ly/1OWoGEg

Dive deep into 64-bit Windows kernel holes: how wild-copy + user-fault-handling primitives give an exploit chain in Ring-0. theori.io/blog/exploitin… #WindowsKernel #ReverseEngineering #ExploitDev

IRQL storm on multi-core system? x86 routes interrupts via Local APIC → logical processor, not physical core. Windows KeSetTargetProcessor can misroute. Debug with !apic + !idt -a—wrong LAPIC ID = missed interrupts. #Interrupts #SMP #WindowsKernel
Dive into how the Windows kernel really works — from GS:KPCR to undocumented calls and root-kit hooks. #WindowsKernel #ReverseEngineering #MalwareAnalysis fluxsec.red/reverse-engine… fluxsec.red

Check Point Research found a Windows kernel bug in Rust-based win32kbase_rs.sys triggered by malformed EMF/EMF+ metafiles causing SYSTEM_SERVICE_EXCEPTION (BSOD). Fixed in OS Build 26100.4202 via KB5058499. #WindowsKernel #RustLang #USA ift.tt/urw7G0v
hendryadrian.com
Denial of Fuzzing: Rust in the Windows kernel
Check Point Research discovered a vulnerability in the new Rust-based win32kbase_rs.sys Windows kernel component that could be triggered by malformed EMF/EMF+ metafiles to cause a SYSTEM_SERVICE_EX...
Microsoft's September 2025 Patch Tuesday fixes 86 CVEs, including 3 critical Windows kernel vulnerabilities with CVSS up to 8.8, plus issues in Edge, SQL Server, NTLM, SMB, and more. #WindowsKernel #PatchTuesday #USA ift.tt/nkh2OvA
hendryadrian.com
Microsoft Patch Tuesday September 2025 Fixes Risky Kernel Flaws
Microsoft released September 2025 patches addressing 86 CVEs, including three critical Windows kernel vulnerabilities with high exploitation risks. These updates also fix flaws in Edge, SQL Server,...
Microsoft patched 86 vulnerabilities in September 2025 across Windows, SharePoint, Office, and SQL Server. None exploited yet, but 8 rated highly likely for exploitation, including critical remote code execution flaws. #WindowsKernel #SharePointFlaws ift.tt/M0wroST
hendryadrian.com
Microsoft Patches 86 Vulnerabilities
Microsoft's September 2025 Patch Tuesday fixed 86 vulnerabilities across Windows and other products, with none exploited in the wild but several rated highly likely for exploitation. Key patches...
Windows 10 bug 0xD1 DRIVER_IRQL_NOT_LESS_OR_EQUAL caused by tunnel.sys dereferencing NULL during Teredo flow teardown. A race condition between tcpip!LruCleanupDpcRoutine and tcpip!UdpCloseEndpoint triggers the crash. #WindowsKernel #RaceCondition ift.tt/nglMaV3
hendryadrian.com
BugCheck 0xD1: Potential race condition in Teredo cleanup during flow teardown
A Windows 10 kernel-only crash dump (build 19041) shows a 0xD1 DRIVER_IRQL_NOT_LESS_OR_EQUAL caused by tunnel.sys (Teredo) dereferencing a NULL previous pointer while unlinking a flow list entry,...
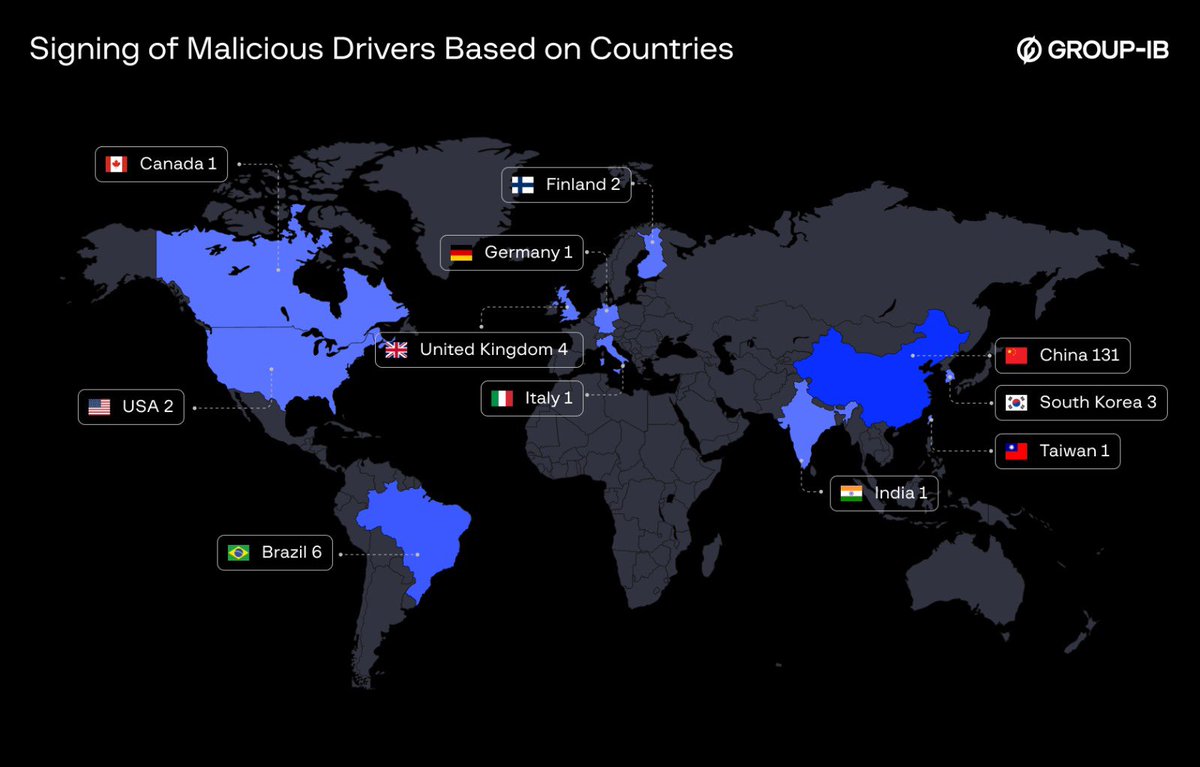
Threat Actors are now weaponizing #WindowsKernel loaders for more stealthy and flexible attacks. By using signed kernel loaders TA has the ability to adjust their attacks on the fly, leaving minimal forensic traces making it harder to detect. Out of 600+ signed #maliciousdrivers…

🚨 Blog 6 is out! Jay Pandya breaks down Out-Of-Bounds in Windows kernel drivers—how it works, how it breaks, and why it matters. Read it now via White Knight Labs: whiteknightlabs.com/2025/07/01/und… #Infosec #WindowsKernel #CyberSecurity #ExploitDev

Over 20 vulnerabilities in Windows Kernel Streaming (KS) revealed, mainly affecting frame buffer handling & MDL misuse, risking memory corruption & privilege escalation. Stay alert to these critical flaws! 🛡️ #WindowsKernel #BufferFlaws #US ift.tt/j3dimq6
Deep dive into how syscalls work in the Windows kernel, exploring structures, debugging, and reversing techniques. alice.climent-pommeret.red/posts/a-syscal… #WindowsKernel
🚨 New Writeup Alert! 🚨 "CVE-2025–21333 Windows heap-based buffer overflow analysis" by Alessandro Iandoli is now live on IW! Check it out here: infosecwriteups.com/d1b597ae4bae #kernelexploit #windowskernel #privilegeescalation #hyperv #windowssandbox
infosecwriteups.com
CVE-2025–21333 Windows heap-based buffer overflow analysis
CVE-2025–21333 is a Windows vulnerability detected by Microsoft as exploited by threat actors. Microsoft patched the vulnerability on…
0x06 - Approaching Modern Windows Kernel Type Confusions #WindowsKernel #TypeConfusions #Exploitation #VirtualMemory #PagedMemory wetw0rk.github.io/posts/0x06-app…
0x04 - Introduction to Windows Kernel Write What Where Vulnerabilities #WindowsKernel #WriteWhatWhere #Exploitation #Vulnerability #ArbitraryWrite wetw0rk.github.io/posts/0x04-wri…
0x08 - Modern Windows Kernel Race Conditions #WindowsKernel #RaceConditions #Exploitation #BufferOverflow #CodeExecution wetw0rk.github.io/posts/0x08-mod…
0x07 - Introduction to Windows Kernel Race Conditions #WindowsKernel #RaceCondition #VulnerabilityType #Exploitation #DoubleFetch wetw0rk.github.io/posts/0x07-int…
Join our free #webinar: 🎯 "Windows Kernel Exploitation for Red Team Operators" 👉 loom.ly/VTXooaA This talk will guide you step-by-step into the world of #WindowsKernel exploitation, offering insights and tools needed to adapt and excel in modern #RedTeam operations.

[Cracking Windows Kernel with HEVD] Chapter 3: Can we rop our way into triggering our shellcode? #windowskernel #exploit #HEVD #ROPchain #privilegeescalation mdanilor.github.io/posts/hevd-3/
This #WindowsKernel vulnerability is being exploited to escalate privileges and steal data. Check out the #CybersecurityThreatAdvisory for steps to protect your environment now: bit.ly/3Yki3Ej #CybersecurityThreatAdvisory
Dive into how the Windows kernel really works — from GS:KPCR to undocumented calls and root-kit hooks. #WindowsKernel #ReverseEngineering #MalwareAnalysis fluxsec.red/reverse-engine… fluxsec.red

Dive deep into 64-bit Windows kernel holes: how wild-copy + user-fault-handling primitives give an exploit chain in Ring-0. theori.io/blog/exploitin… #WindowsKernel #ReverseEngineering #ExploitDev

Delivering a Deferred Procedure Call (DPC). #KernelDebugging #WindowsKernel #WindowsInternals #WinDBG #DebugModeOn

Tonight’s workplace @windowsdev #WindowsKernel #WDF #NetAdapterCx #WinsockKernel #openvpn #ovpndco #ovpndcowin

Threat Actors are now weaponizing #WindowsKernel loaders for more stealthy and flexible attacks. By using signed kernel loaders TA has the ability to adjust their attacks on the fly, leaving minimal forensic traces making it harder to detect. Out of 600+ signed #maliciousdrivers…


Are stack expansion and stack guard not present in the 64-bit version of Windows kernel? Stack Guard is not set in RtlCreateUserStack while creating the stack for a new thread #windowskernel #kernel

🚨 Blog 6 is out! Jay Pandya breaks down Out-Of-Bounds in Windows kernel drivers—how it works, how it breaks, and why it matters. Read it now via White Knight Labs: whiteknightlabs.com/2025/07/01/und… #Infosec #WindowsKernel #CyberSecurity #ExploitDev

Microsoft patched a high-severity Windows Kernel privilege escalation vulnerability in February, six months after being informed that the flaw was being exploited as a zero-day. #Microsoft #WindowsKernel #vulnerability #securitypatch #zeroday #cybersecurity #WindowsAppLocker

Signing a kenel driver that is built with MinGW, gcc stackoverflow.com/questions/6553… #mingw #gcc #windowskernel

How to display the PML4E, PDPTE, PDE and PTE of the PTE itself in windbg / kd? stackoverflow.com/questions/6673… #windows #windowskernel #pagetables #windbg #kd

Exploring #WindowsKernel with #Fibratus and #Logsene #devops #devopsnews #guestpost by @rabbitstack bit.ly/2gERrr5

Here is the training stats of our @nullcon Goa, 2020 training on "Windows Kernel Exploitation" 📊 You can check training stats in the gif below. 👇 Want to join our next training? #Cybersecurity #WindowsKernel #Cyberattack #Security #InfoSec #ITSecurity #InfoSecurity
Liberan 71 parches de seguridad por recientes ataques a #MicrosoftOffice y #WindowsKernel. bit.ly/1OWoGEg

🚀Boost your skills to the kernel level! 🖥️Learn the basics of Windows & driver internals, different memory corruption classes & fuzzing of kernel-mode drivers by Ashfaq @HackSysTeam 🎟️Get your ticket➡️bit.ly/3NWsFCH #NullconGoa2022 #training #windowskernel #infosec

Windows kernel pool spraying fun - Part 1 - Determine kernel object size bit.ly/2x4AORC #infosec #hacking #windowskernel #cyber

The severity of the Elevation of Privilege - Windows Kernel (CVE-2024-30088) has increased. А repository with technical details on this vulnerability and PoC appeared on GitHub. #Microsoft #Windows #WindowsKernel #ZDI #NtQueryInformationToken ➡️ t.me/avleonovcom/13…

#Vulnerabilities: #WindowsKernel cng.sys Pool-Based Buffer Overflow In #IOCTL 0x390400 - bit.ly/2GkXgwj-Ttx #ProjectZero @google 𝞝 #Enterprises #Organizations #SecurityFlaws #InfoSec #PrivilegeEscalation #CyberSecurity #DoS #PrivilegeEscalation #Cryptography #Exploitation

Something went wrong.
Something went wrong.
United States Trends
- 1. Sesko 43K posts
- 2. Ugarte 15K posts
- 3. Richarlison 20.3K posts
- 4. #SaturdayVibes 4,529 posts
- 5. Gameday 30.2K posts
- 6. Amorim 62.4K posts
- 7. De Ligt 24.3K posts
- 8. Good Saturday 31.9K posts
- 9. #Caturday 4,644 posts
- 10. Cunha 24.6K posts
- 11. Casemiro 22.7K posts
- 12. Tottenham 78.5K posts
- 13. #TOTMUN 17.1K posts
- 14. Vicario 1,935 posts
- 15. #MUFC 23.9K posts
- 16. Lando 40.6K posts
- 17. Manchester United 83.8K posts
- 18. Dalot 12.3K posts
- 19. #BrazilGP 67.2K posts
- 20. Bortoleto 19.1K posts




























