Tech Sec
@TechSec_on
Cyber Security Knowledge
Get to know who is currently using quantum computing, which industries are the most active in quantum computing, the cost of quantum computing, how to deploy a quantum environment, and the constraints. An exhaustive 2025 dummies guide. #quantum #qubits medium.com/p/what-is-the-…

Ways to Stop Hacks Through the Back Door: Supply Chain Attack Strategies medium.com/p/ways-to-stop…
Quantum Threats Are Coming: Your Guide to Post-Quantum Cryptography in 2025 medium.com/p/quantum-thre… #quantumcomputer #CyberSecurity #CyberSecurityAwareness #pqc #cyberattck #cryptography

Zero Trust in 2025: Why You Can’t Trust Anyone in Cybersecurity medium.com/p/zero-trust-i… #zerotrust #zta #CyberSecurity #SecurityAwareness

Learning the ins and outs of symmetric encryption: Secure Data Protection medium.com/p/learning-the… #dataprotection #CyberSecurity #cryptograpgy

I just published Cryptography: The Science of Securing Digital Communication medium.com/p/cryptography… #encryption #cryptography #CyberSecurity #RSA #AES #digitalsecurity

#lumma Stealer has new updated defense evasion techniques in below video. #malware #lummac2 #fakecaptcha youtu.be/slZHWVU7OX8

Types of DLL Hijacking link.medium.com/dyDTusD5TQb DLL hijacking attacks can be classified into four main types, depending on how the attacker manipulates the DLL loading process. #persistent #malware #CyberSecurity #dllhijacking
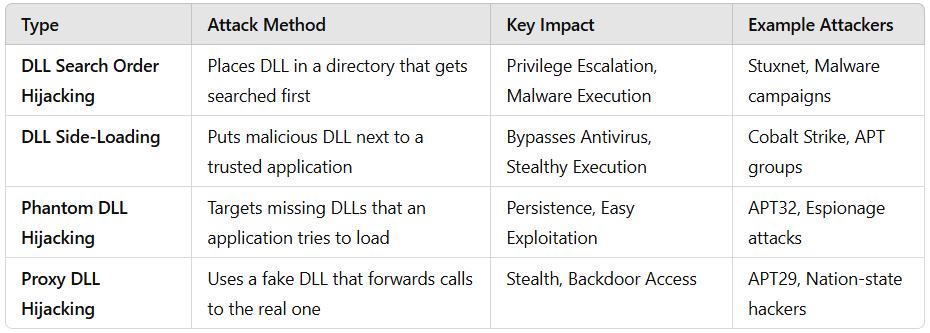
Windows DLL Hijacking link.medium.com/AltxI6MwSQb This article covers how DLL hijacking works, its types, real-world examples, and defensive measures to secure systems from such attacks. #Hacking #Dllhijacking #cybersecurity #Malware #exploit
The Art of Social Engineering - How Hackers Exploit Human Psychology link.medium.com/QUBtj55EQQb Learn how social engineering attacks exploit human psychology to steal data, gain unauthorized access and bypass security systems. This in-depth guide covers social engineering techniques
exploit + lab setup for CVE-2024-45519 github.com/Chocapikk/CVE-…

0-Day Flaw CVE-2024-38200 in Microsoft Office Exposes NTLMv2 Hashes: PoC Exploit Released securityonline.info/0-day-flaw-cve…
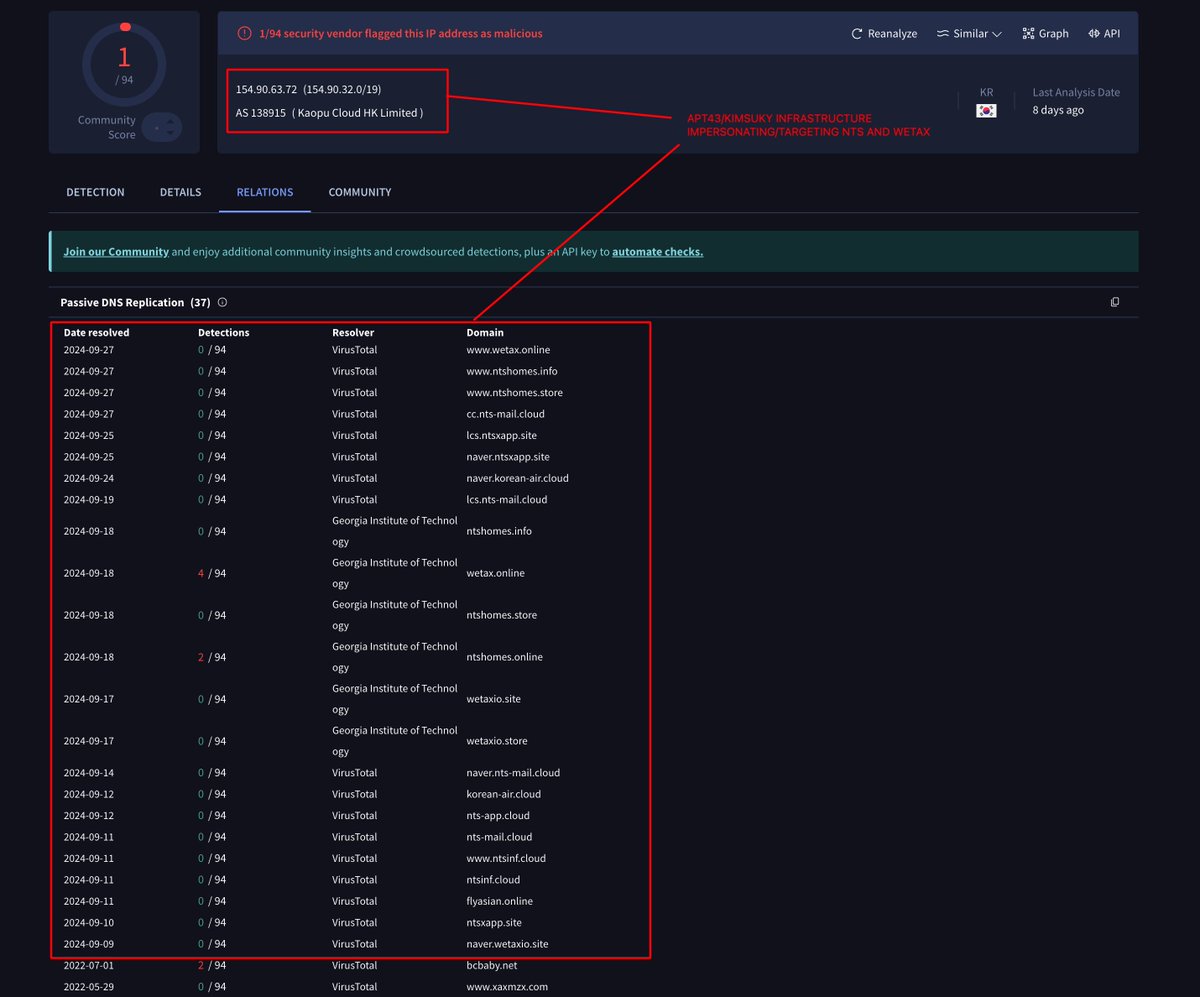
🇰🇵APT43 (Kimsuky) is targeting/impersonating the🇰🇷Korean National Tax Service (NTS) and Wetax. virustotal.com/gui/ip-address… AS 138915 Kaopu Cloud HK Limited /154.90.63.72 /wetax.online /ntshomes.info /ntshomes.store /cc.nts-mail.cloud /lcs.ntsxapp.site /naver.ntsxapp.site…
OAuth 2.0 Explained. OAuth 2.0 is an authorization framework that enables applications to access a user’s data on another service (like Facebook or GitHub) without sharing the user’s password. It’s essentially a digital handshake between the app, service, and user, with…
Zloader 🚨! This evolved trojan now comes with stronger encryption and 64-bit support, posing a bigger threat than ever. Stay informed on the latest malware risks! 🔐💻 #CyberSecurity #Zloader #Malware #Ransomware #trojan youtu.be/uKBsGuRu5P8

youtu.be/uUa0tMn0m4s 🚨 UNC2970, a North Korea-linked cyber espionage group, is targeting job seekers in U.S. critical infrastructure with fake job offers! 🎯 #trojan #UNC2970 #infosec #cybersecurity #cybersecuritytips #cybersecurityawareness #informationsecurity #jobseekers

🔍💻 Dive into the world of cybersecurity with our latest video on PEAKLIGHT, the stealthy memory-only malware! 🦠 Learn how it infiltrates systems and delivers dangerous payloads. Stay safe out there! 🚨 #CyberSecurity #Malware #TechSec #stealer #dropper youtu.be/9l0ALRqE4xY

youtube.com
YouTube
🚨 Unveiling PEAKLIGHT: The Stealthy Malware Dropper 🦠 | How Hackers...
Lumma information Stealer! 😱 | Malware-as-a-Service 🕵️♂️ youtu.be/L_z9_TjC4Ug?si… #lumma #informationtechnology #YouTube #malware

youtube.com
YouTube
Lumma information Stealer! 😱 | Malware-as-a-Service 🕵️♂️
United States Trends
- 1. Luka 57.6K posts
- 2. Lakers 44.3K posts
- 3. Clippers 16.8K posts
- 4. #DWTS 93.3K posts
- 5. #LakeShow 3,385 posts
- 6. Kris Dunn 2,360 posts
- 7. Robert 132K posts
- 8. Reaves 10.3K posts
- 9. Kawhi 5,869 posts
- 10. Jaxson Hayes 2,226 posts
- 11. Ty Lue 1,481 posts
- 12. Alix 14.9K posts
- 13. Elaine 45.8K posts
- 14. Jordan 117K posts
- 15. Collar 41K posts
- 16. Zubac 2,249 posts
- 17. Dylan 34.7K posts
- 18. NORMANI 6,076 posts
- 19. Colorado State 2,353 posts
- 20. Godzilla 36.5K posts
Something went wrong.
Something went wrong.