#compromiseassessment 検索結果
THOR 10 ⚡️ Lite Free YARA and IOC scanner - Fast and stable - Reduced feature set - Uses the open-source signature set used in LOKI - Windows, Linux, macOS #DFIR #CompromiseAssessment nextron-systems.com/2020/03/20/tho…

The Log4j vulnerability posed a significant risk, especially for one international retailer. In this case study, see how a client improved its cybersecurity posture with help from a Unit 42 Compromise Assessment. Read it now. bit.ly/43Qmqb2. #CompromiseAssessment #log4j

#CompromiseAssessment - Damit Sie die #Kontrolle über Ihr #Business behalten! 10 Mythen rund um Compromise Assessments - informieren Sie sich und vereinbaren Sie ein Gespräch mit unseren #Controlware Experten. LINK: controlware.de/landingpages/c…
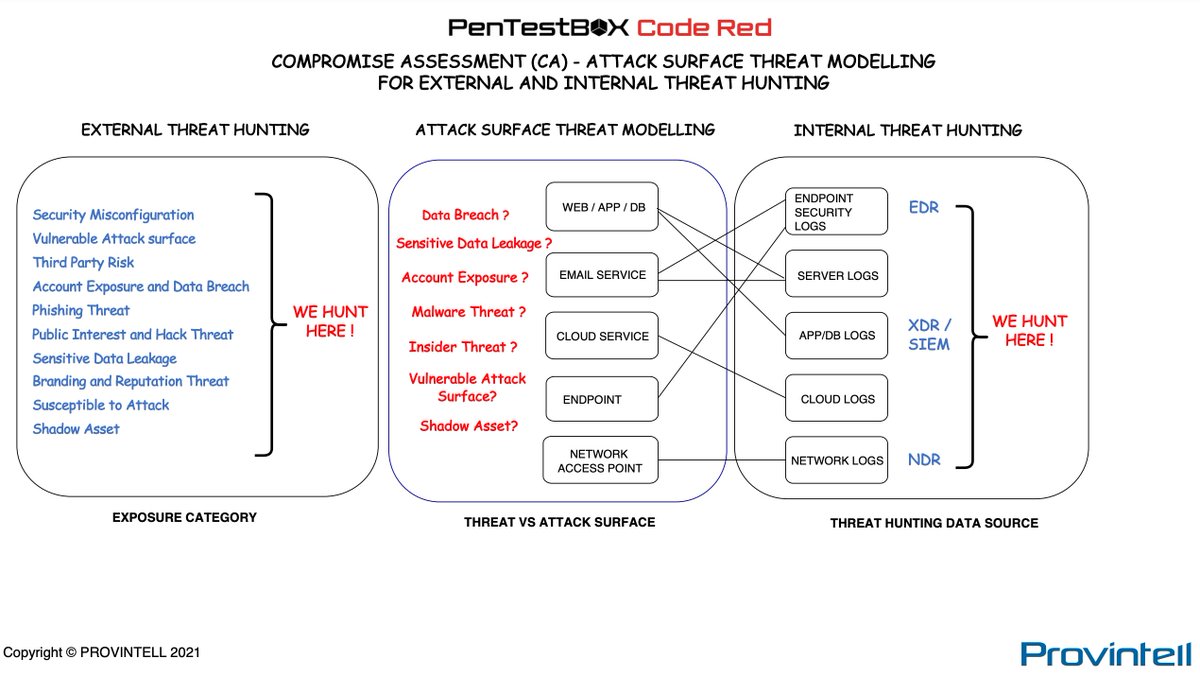
‘𝐖𝐡𝐚𝐭 𝐢𝐬 𝐩𝐨𝐰𝐞𝐫𝐟𝐮𝐥 𝐚𝐛𝐨𝐮𝐭 #ThreatHunting 𝐢𝐬 𝐭𝐡𝐚𝐭 𝐢𝐭 𝐩𝐢𝐭𝐬 𝐡𝐮𝐦𝐚𝐧 𝐝𝐞𝐟𝐞𝐧𝐝𝐞𝐫𝐬 𝐚𝐠𝐚𝐢𝐧𝐬𝐭 𝐡𝐮𝐦𝐚𝐧 𝐚𝐝𝐯𝐞𝐫𝐬𝐚𝐫𝐢𝐞𝐬’ Ask us- provintell.com/ask-superpro/ #PROVINTELL, #CompromiseAssessment, #ThreatHunting, #AttackSurfaceThreatModelling
Contact us today to learn more about how our advanced #compromiseassessment strategy can strengthen your #cybersecurity posture. Together, let's stay ahead of threats and secure a safer #digital future. +961.71.888193 / +96171.888509 #Teknologiia #Dataprotection…

عزز وضعك الأمني 🛡️ مع خدمة الكشف عن الاختراقات السيبرانية، نستخدم أدوات متطورة مصممة خصيصًا لكشف الاختراقات، رصد التهديدات، منعها، والتعامل معها بسرعة وكفاءة. تواصل معنا واطلب الخدمة! [email protected] #CompromiseAssessment #الأمن_السيبراني

#CompromiseAssessment and #PenetrationTesting serve different benefits and purposes to identify vulnerabilities and current flaws. Understand when to choose them according to their benefits and necessity. #pentest #cybersec #infosec #Pentesting #cyberattack #CyberSecurity

#CompromiseAssessment: Damit Sie die Kontrolle über Ihr Business behalten! 10 Mythen rund um Compromise Assessments - informieren Sie sich und vereinbaren Sie ein Gespräch mit unseren Experten. ▶️controlware.de/landingpages/c…

#CompromiseAssessment: Damit Sie die Kontrolle über Ihr Business behalten! Decken Sie in Ihrem Netzwerk Sicherheitslücken, Malware und Anzeichen für unbefugten Zugriff auf! ➡️ controlware.de/compromise-ass…

Scanning for Indications of MOVEit Transfer Exploitation with THOR Lite #MOVEit #Vulnerability #CompromiseAssessment #IOCs #YARA #Sigma nextron-systems.com/2023/06/03/sca…
Check out this short video explaining how the GuardYoo automated Compromise Assessment Audit Platform can reduce the time, resources and costs usually associated with a project of this importance. #CompromiseAssessment #Cybersecurity #ThreatHunting #InformationSecurity
Attackers can penetrate a network & remain hidden for a long time before being detected. Our proactive #CompromiseAssessment service helps verify if your network has already been breached, enabling faster #IncidentResponse & #Remediation #InfoSec #SIEM #SOC #CyberSecurity #MSSP

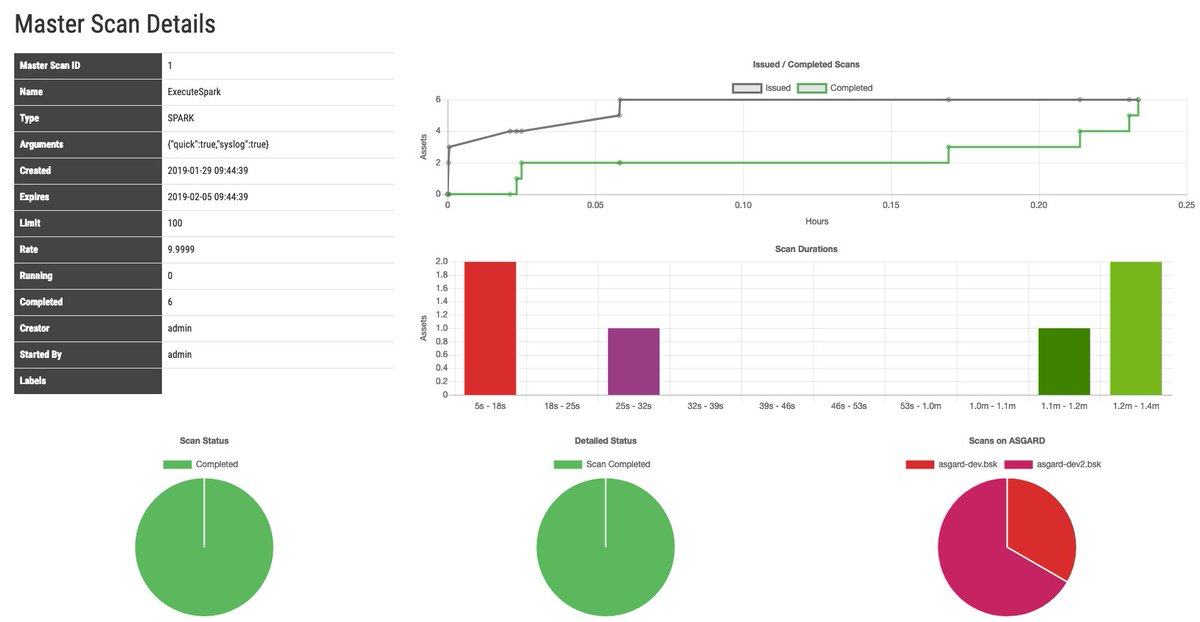
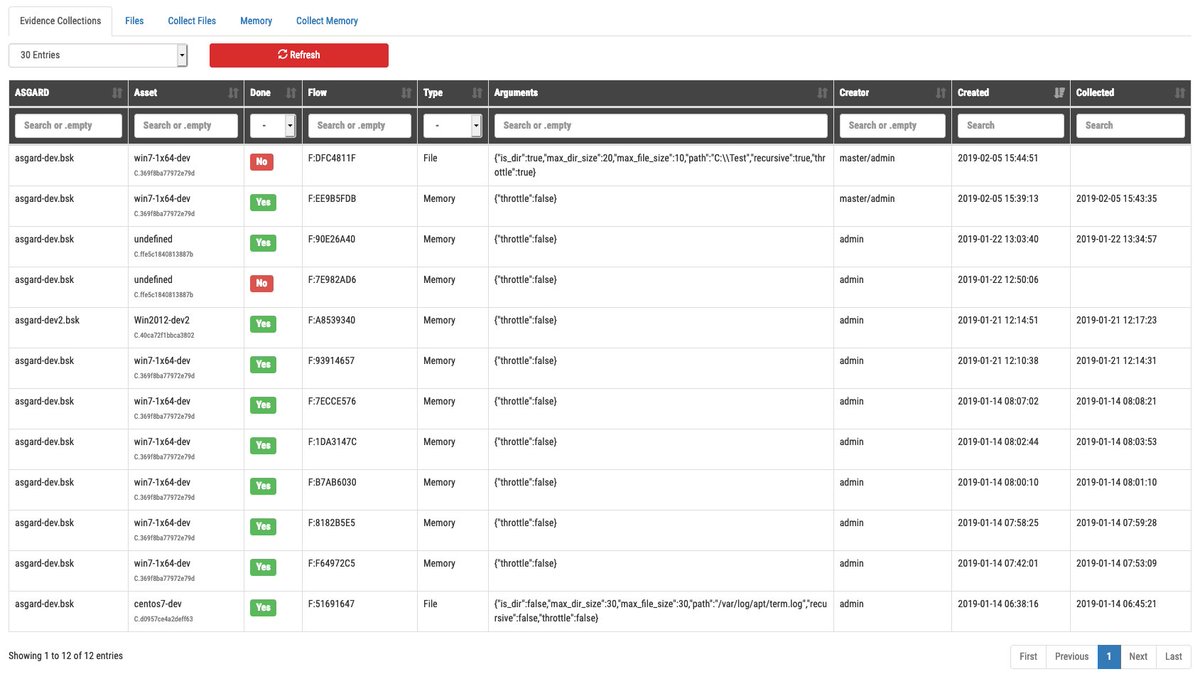
MASTER ASGARD one ASGARD to rule them all > Control more than 100,000 endpoints from a single interface > Run scans > Plan scans > Control assets > IOC management > File & remote memory collection BETA starts soon #DFIR #CompromiseAssessment nextron-systems.com/2019/02/11/mas…

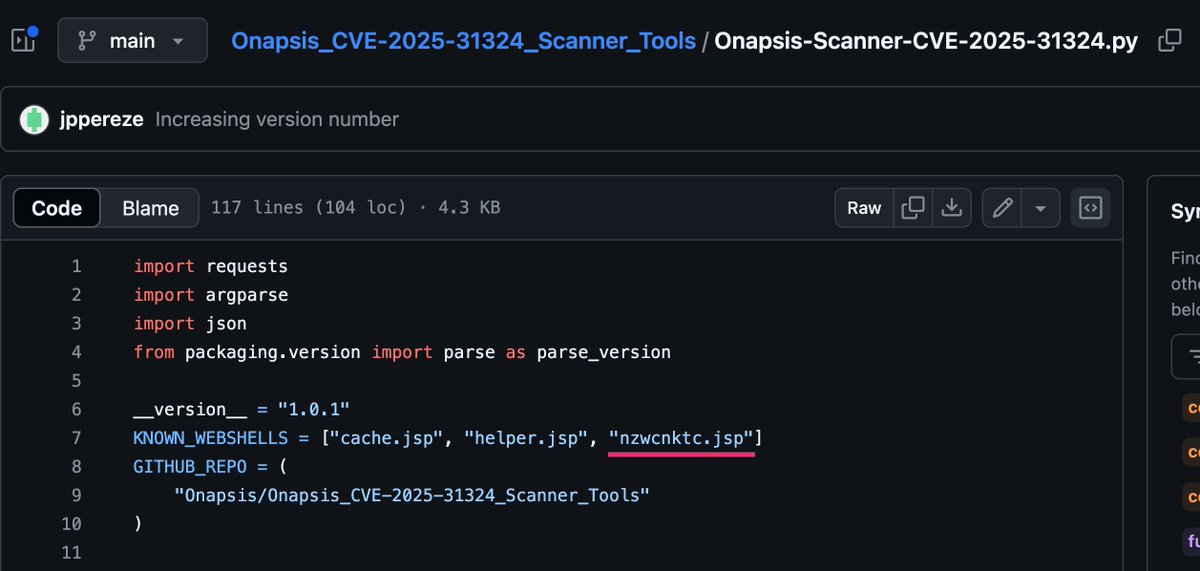
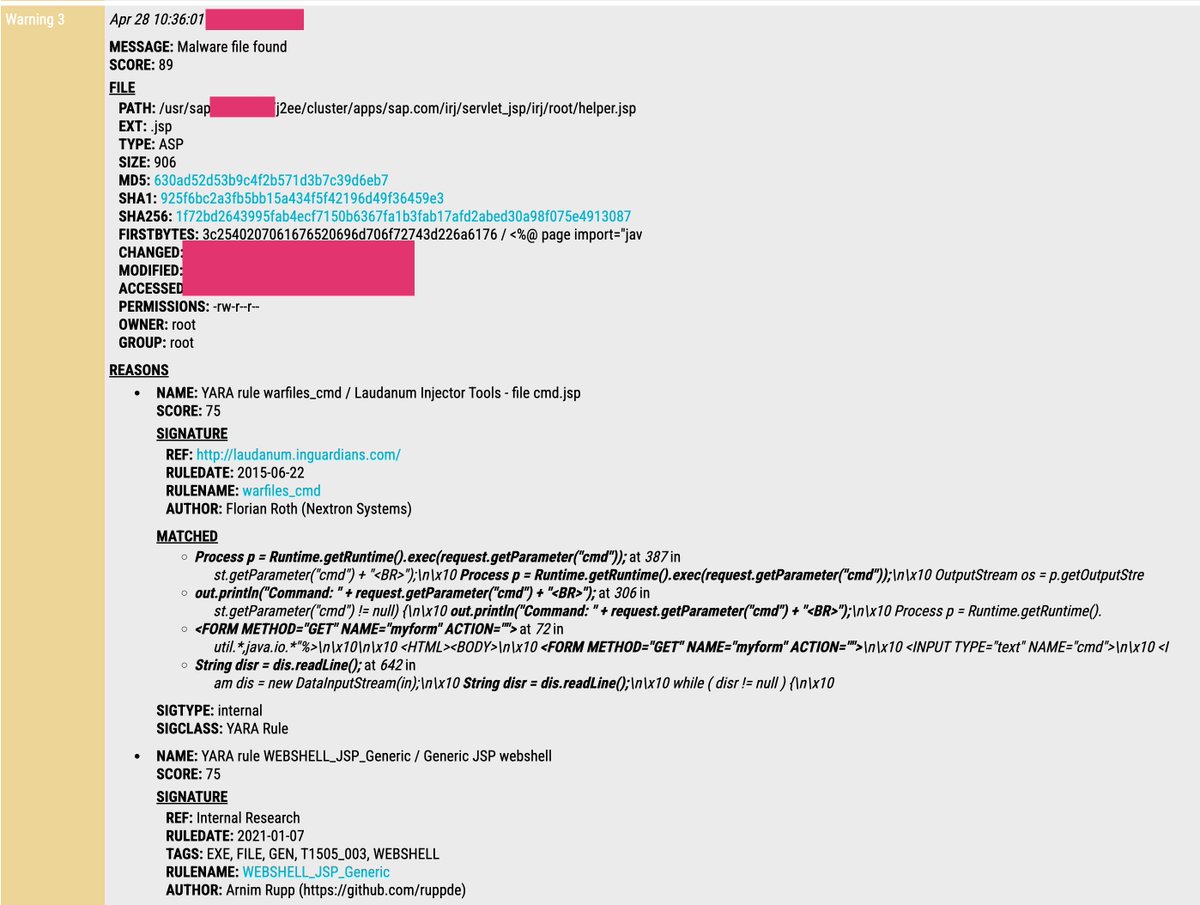
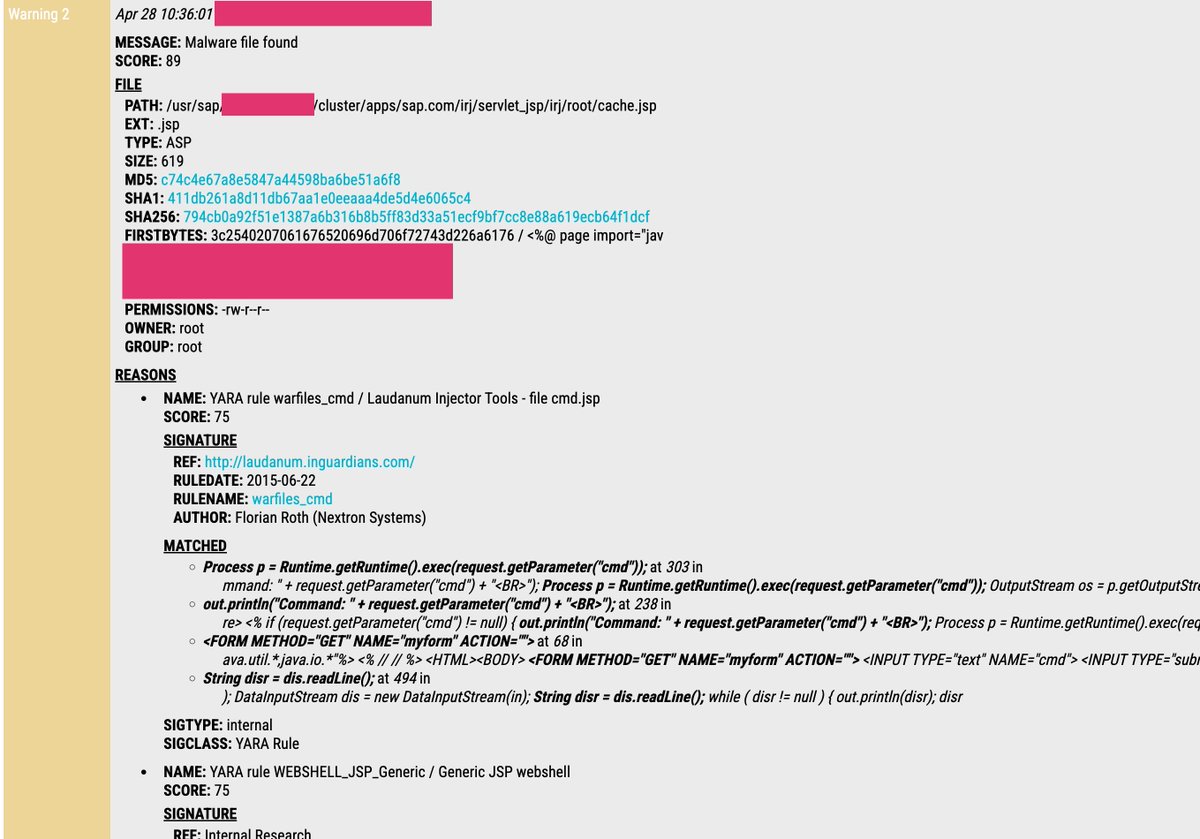
We published a blog post about the exploitation of CVE-2025-31324 in #SAP #NetWeaver Given the use of random webshell names like nzwcnktc.jsp, I highly recommend running a local #CompromiseAssessment Our generic webshell detection rules - even in the open-source sets - would…
A third webshell (nzwcnktc.jsp) was listed in the @onapsis scanner for CVE-2025-31324. It shows attackers use random names to backdoor SAP NetWeaver systems. External detection is unreliable. I recommend running a local compromise assessment. Both THOR Lite and THOR Cloud Lite…
🩺 ow.ly/d2aY50DtU5D | VPN #encryption is useful for orgs with #remotework but VPNs can open up unintended security holes. Don’t trade usability for security. Schedule routine device & network health checks 🏥 with CyCraft. #CompromiseAssessment #cybersecurity #infosec

#Controlware #CompromiseAssessment - Damit Sie die Kontrolle über Ihr Business behalten! 10 #Mythen rund um Compromise Assessments - informieren Sie sich und vereinbaren Sie ein Gespräch mit unseren Experten: ▶️ controlware.de/landingpages/c…

🚑. ow.ly/UxkP50D9bvc | A long MTTD can cost your enterprise millions in fines and remediation. A good night’s sleep for your #SOC team? Priceless. Know for sure with our Compromise Assessment Services. #CompromiseAssessment #CyberSecurity #InfoSec #CyberConsultant

🇹🇼 🤝 🇸🇬 CyCraft now provides Fast, Accurate, Simple & Thorough threat detection & response to Singapore. Modern cybercriminals have automated their attacks; have you automated your defenses? Learn How 👉 ow.ly/LHAc50AzL6X #MDR #DFIR #CompromiseAssessment

Attackers can penetrate a network & remain hidden for a long time before being detected. Our proactive #CompromiseAssessment service helps verify if your network has already been breached, enabling faster #IncidentResponse & #Remediation #InfoSec #SIEM #SOC #CyberSecurity #MSSP

We published a blog post about the exploitation of CVE-2025-31324 in #SAP #NetWeaver Given the use of random webshell names like nzwcnktc.jsp, I highly recommend running a local #CompromiseAssessment Our generic webshell detection rules - even in the open-source sets - would…
A third webshell (nzwcnktc.jsp) was listed in the @onapsis scanner for CVE-2025-31324. It shows attackers use random names to backdoor SAP NetWeaver systems. External detection is unreliable. I recommend running a local compromise assessment. Both THOR Lite and THOR Cloud Lite…




عزز وضعك الأمني 🛡️ مع خدمة الكشف عن الاختراقات السيبرانية، نستخدم أدوات متطورة مصممة خصيصًا لكشف الاختراقات، رصد التهديدات، منعها، والتعامل معها بسرعة وكفاءة. تواصل معنا واطلب الخدمة! [email protected] #CompromiseAssessment #الأمن_السيبراني

Attackers can penetrate a network & remain hidden for a long time before being detected. Our proactive #CompromiseAssessment service helps verify if your network has already been breached, enabling faster #IncidentResponse & #Remediation #InfoSec #SIEM #SOC #CyberSecurity #MSSP

Captain's Log: Have we been compromised? 🤔 ThreatNG's #CompromiseAssessment helps you explore your IT environment for any signs of malicious activity. Read more to discover how it can help your organization. #cybersecurity #StarTrek #EASM #ExternalAttackSurface #Security
Suspect a #SecurityBreach ? 🤔 ThreatNG can help with your #CompromiseAssessment! Identify #vulnerabilities, gather evidence from the #darkweb, & assess the impact. Learn more: threatngsecurity.com/glossary/compr… #cybersecurity #EASM #ExternalAttackSurface #VulnerabilityAssessment #Security
Suspect a #SecurityBreach ? 🤔 ThreatNG can help with your #CompromiseAssessment! Identify #vulnerabilities, gather evidence from the #darkweb, & assess the impact. Learn more: threatngsecurity.com/glossary/compr… #cybersecurity #EASM #ExternalAttackSurface #VulnerabilityAssessment #Security
Strengthen your organization with Security Pact Arabia’s Compromise Assessment (CA). Uncover threats, investigate incidents, and contain compromises with expert solutions. Visit securitypact.io #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPactArabia

Strengthen your organization with Security Pact Arabia’s Compromise Assessment (CA). Uncover threats, investigate incidents, and contain compromises with expert solutions. Visit securitypact.io #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPactArabia
Strengthen your organization with Security Pact Arabia’s Compromise Assessment (CA). Uncover threats, investigate incidents, and contain compromises with expert solutions. Visit securitypact.io #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPactArabia

Strengthen your organization with Security Pact Arabia’s Compromise Assessment (CA). Uncover threats, investigate incidents, and contain compromises with expert solutions. Visit securitypact.io #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPactArabia

Strengthen your organization with Security Pact Arabia’s Compromise Assessment (CA). Uncover threats, investigate incidents, and contain compromises with expert solutions. Visit securitypact.io #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPactArabia

Strengthen your organization with Security Pact Arabia’s Compromise Assessment (CA). Uncover threats, investigate incidents, and contain compromises with expert solutions. Visit securitypact.io #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPactArabia

🔴 PURE7 Compromise Assessment Hizmeti ile kurumunuzda geçmişte ya da günümüzde bir saldırgan aktivitesinin olup olmadığını tespit ✉️ Örnek Rapor için: info[at]pure7.com.tr 👉 Konu Başlığı: Compromise Assessment – Kurum Adı #CompromiseAssessment #PURE7
![Pure7Team's tweet image. 🔴 PURE7 Compromise Assessment Hizmeti ile kurumunuzda geçmişte ya da günümüzde bir saldırgan aktivitesinin olup olmadığını tespit
✉️ Örnek Rapor için: info[at]pure7.com.tr
👉 Konu Başlığı: Compromise Assessment – Kurum Adı
#CompromiseAssessment #PURE7](https://pbs.twimg.com/media/GUctcLZWsAA-MJn.jpg)
![Pure7Team's tweet image. 🔴 PURE7 Compromise Assessment Hizmeti ile kurumunuzda geçmişte ya da günümüzde bir saldırgan aktivitesinin olup olmadığını tespit
✉️ Örnek Rapor için: info[at]pure7.com.tr
👉 Konu Başlığı: Compromise Assessment – Kurum Adı
#CompromiseAssessment #PURE7](https://pbs.twimg.com/media/GUctcLZXAAE2T8r.jpg)
![Pure7Team's tweet image. 🔴 PURE7 Compromise Assessment Hizmeti ile kurumunuzda geçmişte ya da günümüzde bir saldırgan aktivitesinin olup olmadığını tespit
✉️ Örnek Rapor için: info[at]pure7.com.tr
👉 Konu Başlığı: Compromise Assessment – Kurum Adı
#CompromiseAssessment #PURE7](https://pbs.twimg.com/media/GUctcLcXYAArBPf.jpg)
![Pure7Team's tweet image. 🔴 PURE7 Compromise Assessment Hizmeti ile kurumunuzda geçmişte ya da günümüzde bir saldırgan aktivitesinin olup olmadığını tespit
✉️ Örnek Rapor için: info[at]pure7.com.tr
👉 Konu Başlığı: Compromise Assessment – Kurum Adı
#CompromiseAssessment #PURE7](https://pbs.twimg.com/media/GUctcLbXcAAuA9S.jpg)
Performing Linux #investigations #atscale" is a must when you have several incident response and #compromiseassessment engagements to collect #forensic #artefacts from various Linux environments.
Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

THOR 10 ⚡️ Lite Free YARA and IOC scanner - Fast and stable - Reduced feature set - Uses the open-source signature set used in LOKI - Windows, Linux, macOS #DFIR #CompromiseAssessment nextron-systems.com/2020/03/20/tho…

Scanning for Indications of MOVEit Transfer Exploitation with THOR Lite #MOVEit #Vulnerability #CompromiseAssessment #IOCs #YARA #Sigma nextron-systems.com/2023/06/03/sca…

‘𝐖𝐡𝐚𝐭 𝐢𝐬 𝐩𝐨𝐰𝐞𝐫𝐟𝐮𝐥 𝐚𝐛𝐨𝐮𝐭 #ThreatHunting 𝐢𝐬 𝐭𝐡𝐚𝐭 𝐢𝐭 𝐩𝐢𝐭𝐬 𝐡𝐮𝐦𝐚𝐧 𝐝𝐞𝐟𝐞𝐧𝐝𝐞𝐫𝐬 𝐚𝐠𝐚𝐢𝐧𝐬𝐭 𝐡𝐮𝐦𝐚𝐧 𝐚𝐝𝐯𝐞𝐫𝐬𝐚𝐫𝐢𝐞𝐬’ Ask us- provintell.com/ask-superpro/ #PROVINTELL, #CompromiseAssessment, #ThreatHunting, #AttackSurfaceThreatModelling

🩺 ow.ly/d2aY50DtU5D | VPN #encryption is useful for orgs with #remotework but VPNs can open up unintended security holes. Don’t trade usability for security. Schedule routine device & network health checks 🏥 with CyCraft. #CompromiseAssessment #cybersecurity #infosec

عزز وضعك الأمني 🛡️ مع خدمة الكشف عن الاختراقات السيبرانية، نستخدم أدوات متطورة مصممة خصيصًا لكشف الاختراقات، رصد التهديدات، منعها، والتعامل معها بسرعة وكفاءة. تواصل معنا واطلب الخدمة! [email protected] #CompromiseAssessment #الأمن_السيبراني

🚑. ow.ly/UxkP50D9bvc | A long MTTD can cost your enterprise millions in fines and remediation. A good night’s sleep for your #SOC team? Priceless. Know for sure with our Compromise Assessment Services. #CompromiseAssessment #CyberSecurity #InfoSec #CyberConsultant

🇹🇼 🤝 🇸🇬 CyCraft now provides Fast, Accurate, Simple & Thorough threat detection & response to Singapore. Modern cybercriminals have automated their attacks; have you automated your defenses? Learn How 👉 ow.ly/LHAc50AzL6X #MDR #DFIR #CompromiseAssessment

The Log4j vulnerability posed a significant risk, especially for one international retailer. In this case study, see how a client improved its cybersecurity posture with help from a Unit 42 Compromise Assessment. Read it now. bit.ly/43Qmqb2. #CompromiseAssessment #log4j

#CompromiseAssessment and #PenetrationTesting serve different benefits and purposes to identify vulnerabilities and current flaws. Understand when to choose them according to their benefits and necessity. #pentest #cybersec #infosec #Pentesting #cyberattack #CyberSecurity

#CompromiseAssessment: Damit Sie die Kontrolle über Ihr Business behalten! 10 Mythen rund um Compromise Assessments - informieren Sie sich und vereinbaren Sie ein Gespräch mit unseren Experten. ▶️controlware.de/landingpages/c…

Contact us today to learn more about how our advanced #compromiseassessment strategy can strengthen your #cybersecurity posture. Together, let's stay ahead of threats and secure a safer #digital future. +961.71.888193 / +96171.888509 #Teknologiia #Dataprotection…

#CompromiseAssessment: Damit Sie die Kontrolle über Ihr Business behalten! Decken Sie in Ihrem Netzwerk Sicherheitslücken, Malware und Anzeichen für unbefugten Zugriff auf! ➡️ controlware.de/compromise-ass…

🩺 VPN encryption is useful for orgs with remote work, but VPNs can open up unintended security holes. 🔓 Don’t trade usability for security. Schedule routine device & network health checks 🏥 with CyCraft. Learn More 👉 ow.ly/mMtr50ETtIm #CompromiseAssessment #VPN

Attackers can penetrate a network & remain hidden for a long time before being detected. Our proactive #CompromiseAssessment service helps verify if your network has already been breached, enabling faster #IncidentResponse & #Remediation #InfoSec #SIEM #SOC #CyberSecurity #MSSP

#Controlware #CompromiseAssessment - Damit Sie die Kontrolle über Ihr Business behalten! 10 #Mythen rund um Compromise Assessments - informieren Sie sich und vereinbaren Sie ein Gespräch mit unseren Experten: ▶️ controlware.de/landingpages/c…

MASTER ASGARD one ASGARD to rule them all > Control more than 100,000 endpoints from a single interface > Run scans > Plan scans > Control assets > IOC management > File & remote memory collection BETA starts soon #DFIR #CompromiseAssessment nextron-systems.com/2019/02/11/mas…



Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations. Visit securitypact.net or email [email protected]. #CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact

If we could suggest only one thing organizations can do to protect from #databreach? Run a #compromiseassessment - right now and regularly. Learn more: ow.ly/RsPo50BSDQ2 #cloudcomputing #ransomware #cybersecurity #informationsecurity #cyberattack #cloudsecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. #TheGamingAwards N/A
- 2. Good Thursday 29.9K posts
- 3. #WeekndTourLeaks N/A
- 4. #ThursdayThoughts 1,888 posts
- 5. #thursdaymotivation 1,952 posts
- 6. #TikTokCouplesAreFake N/A
- 7. Happy Friday Eve N/A
- 8. FAYE SHINE IN ARMANI 145K posts
- 9. Nnamdi Kanu 78.1K posts
- 10. Crockett 62.9K posts
- 11. Ray Dalio 1,310 posts
- 12. FEMA 87.3K posts
- 13. LINGORM CH3 CALENDAR SIGN 881K posts
- 14. The 2024 88.2K posts
- 15. FREE HAT 2,099 posts
- 16. Wordle 1,615 X N/A
- 17. The Hunger Games 14.1K posts
- 18. The CDC 13.6K posts
- 19. The 1990 7,659 posts
- 20. NO CAP 14.8K posts





















