#cybersecuritytools 搜索结果
💻 Not all hackers wear hoodies… but they do use these OS! From Kali Linux to Parrot OS, these are the top operating systems used by ethical hackers and cybersecurity pros. 🔐⚡ Which one’s your go-to tool? 👇 #HackersOS #CyberSecurityTools #KaliLinux #ParrotOS…
🔎 Cybersecurity Search Engines: Recon Starts Here 🧠💻 #CyberSecurityTools #SearchEnginesForHackers #OSINT #ReconTools #EthicalHacking #InfoSec #RedTeam #Shodan #Censys #GreyNoise #EducationOnly #ThreatIntel #OffensiveSecurity

#SystemHardening #ConfigurationAudit #CyberSecurityTools #ADTECH247inc #BlueTeamOps #DigitalForensics #GovernanceInAction #SecurityAwareness facebook.com/share/p/172qzq…
Cybersecurity Tools-TO READ MORE APPLICATION SECURITY JOB INTERVIEW QUESTIONS AND ANSWERS amazon.com/Application-Se… #cybersecuritytools #applicationsecurityebook #applicationsecurity #softwaresecurity #cybersecurityebook #CybersecurityCareer #CybersecurityTraining
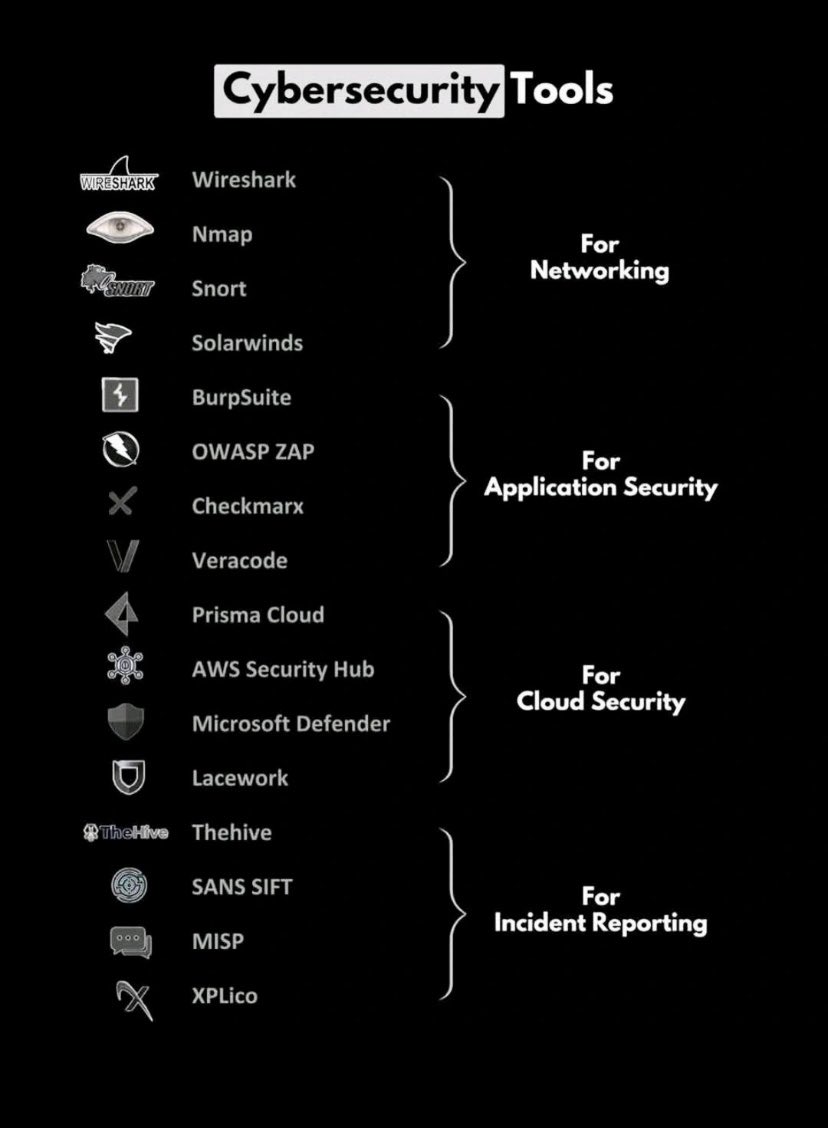
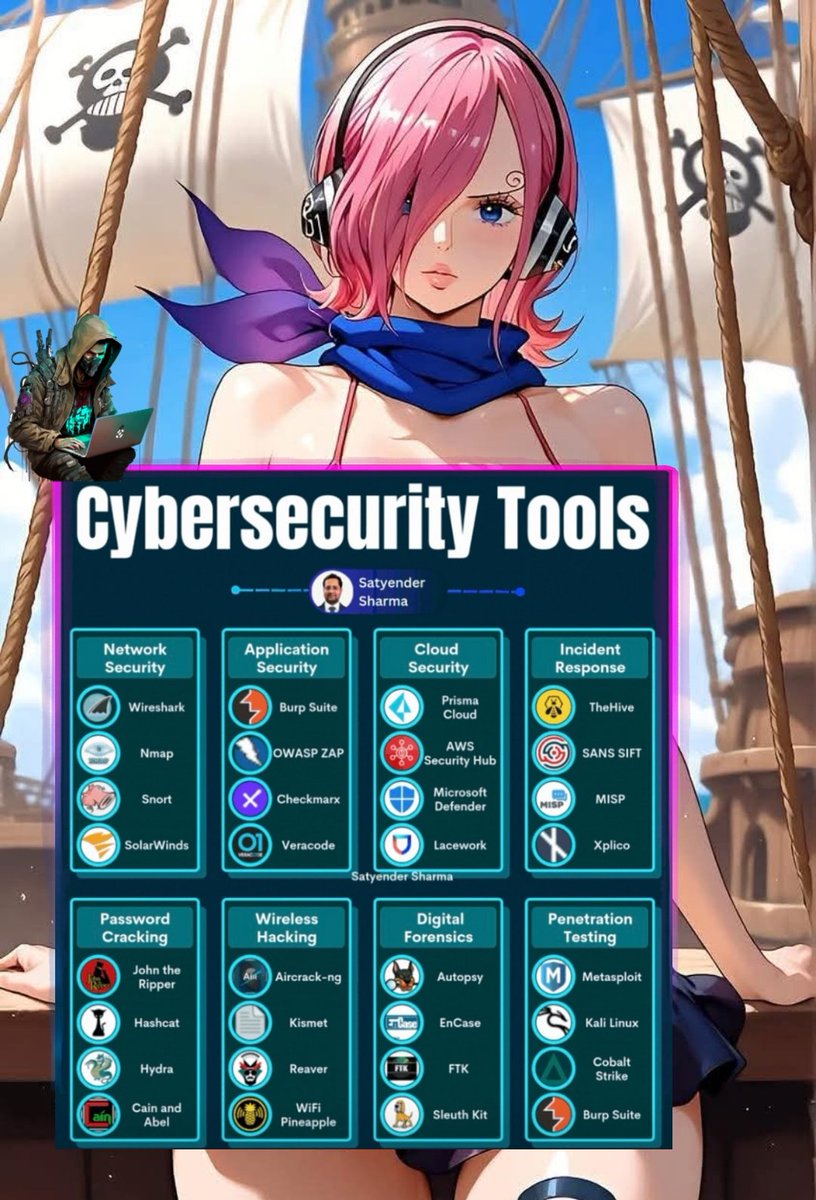
Cybersecurity Tools You Should Know 🔥🛡️💻 #CyberSecurityTools #EthicalHacking #InfoSec #RedTeam #BlueTeam #EducationOnly #SecurityToolkit #PenTestReady #CyberSkills
🚀 New Repository Alert! 🐞 I've shared my techniques to bypass 403 and 401 restrictions along with random bug bounty tips and tricks! 🛠️ 🔗 Check it out: github.com/sabir789/BugBo… #bugbountytips #cybersecuritytools @Jayesh25_ @0x0SojalSec @0xTib3rius

Got the new-age #cybersecuritytools, talent & resources—so why the #securitygaps? It’s all about integration. In Edition 1 of our new series, Pavel Shepetina explores the hidden cost of misconfigurations & how to avoid them. Read now: link.group-ib.com/4iQFkFX

Lacking a robust system at your organization? We're one demo away: bit.ly/3VljUY8 #cybersecuritytools #cybersecurity

🧠 Top Reverse Engineering Tools Every Cybersecurity Researcher Should Know 🔍🛠️ #ReverseEngineering #CyberSecurityTools #InfoSec #MalwareAnalysis #EthicalHacking #Ghidra #IDAPro #BinaryNinja #EducationOnly #RedTeamTools #CyberAwareness

How prepared are you for cyber-attacks on your business? 🤔 Please don't wait until it's too late. For more info, visit CybersecurityMadeEasy.com #vCISO #cybersecuritytips #cybersecuritytools
Cybersecurity Tool of the Day: Nmap🧿 Download it here: nmap.org #Nmap #NetworkScanner #CybersecurityTools #EthicalHacking #InfoSec #CyberAwareness #DigitalSecurity #TechSavvy #NmapPower

10 Simplified Cyber Security Measures myfrugalbusiness.com/2022/08/most-c… #Cybersec #Security #cybersecuritytools #Firewall #Phishing #MFAs #MFA #VPN #VPNs #IT #CTO #CIO #SaaS #Software

Just got a phishing email from my own company. 🙃 Phishing scams are evolving fast. Use smart email protection like Bitdefender to stay ahead. Cybersecurity tools matter—especially for small businesses. #BayAreaBusiness #PhishingScams #CyberSecurityTools #SmallBusinessSupport
ControlCase’s Cybersecurity Certification Finder Tool will help you initiate the first steps toward IT certification and navigate your journey to compliance adoption success. Take the short online assessment today. hubs.ly/Q02GJnd20 #ControlCase #cybersecuritytools
🔍 Dive into the world of reconnaissance with these 8 powerful tools! From port scanning to information gathering, they uncover hidden gems. Discover their unique purposes and level up your security assessments. #Reconnaissance #CyberSecurityTools #InfoSec #cybersecurity…

Tanner showed our #Interns the vital tools 🧰 and equipment to keep in a physical security go bag. Drop us a comment to share what you keep in your kit. #CybersecurityTools #GoBagEssentials #InfoSecGear #CyberPreparedness

The Central Bank of Kenya invites eligible applicants to submit sealed tenders Procurement of a Cyber Threat Intelligence Solution and Support for Central Bank of Kenya. #cybersecuritytools

Cybersecurity Tool of the Day: Wireshark 🦈 Your Friendly Network Detective! 🕵️ Download it at: wireshark.org #Wireshark #CybersecurityTools #NetworkAnalyzer #TechTips #InfosecDaily #LearnCybersecurity #DigitalSafety #EthicalTech #CyberAwareness

Top Cybersecurity Open-Source Tools: November 2025 digitrendz.blog/?p=89758 #CloudSecurity #CybersecurityTools #Open-sourceSecurity #PenetrationTesting
🔍 Use antivirus and anti-malware tools for extra protection.DM FOR ANY OF THESE TOOLS 🔧 #MalwareProtection #CyberSecurityTools #OnlineSafety

Avast’s Free AI Scam Protection Now Available Worldwide digitrendz.blog/?p=87401 #AiScamProtection #AvastScamGuardian #CybersecurityTools #PhishingDefense
Cybersecurity Tools-TO READ MORE APPLICATION SECURITY JOB INTERVIEW QUESTIONS AND ANSWERS amazon.com/Application-Se… #cybersecuritytools #applicationsecurityebook #applicationsecurity #softwaresecurity #cybersecurityebook #CybersecurityCareer #CybersecurityTraining

📁 Pull the latest Nuclei templates: nuclei -update-templates 📚 Clone updated wordlists (SecLists): git clone github.com/danielmiessler… #CyberSecurityTools #RedTeam #BlueTeam
macos users beware! new security tools & a public dataset are launching to tackle growing apple-targeted malware threats. stay safe online 🚫 #macossecurity #cybersecuritytools #antimalware darkreading.com/vulnerabilitie…
Best Cybersecurity Tools for Beginners (2025 Edition) Every pro starts somewhere — the best start with the right toolkit. Cybersecurity isn’t just defense; it’s awareness, detection & response. Here are some 👇 #cybersecuritytools #CyberSecurityAwareness #infosec #launch #alpha

When internal conflicts meet internal investigations… Trust is great... but evidence is better. Digital forensics helps businesses cut through the noise and uncover the facts. #DigitalForensics #CyberSecurityTools #IncidentResponse #CyberCrime #CybersecurityAwarenessMonth

One critical step in #MalwareAnalysis: memory forensics! 🧠 Live memory holds encryption keys, process injections, and C2 data that disk forensics misses. Volatility Framework is your best friend here. What's your go-to memory analysis technique? #InfoSec #CybersecurityTools

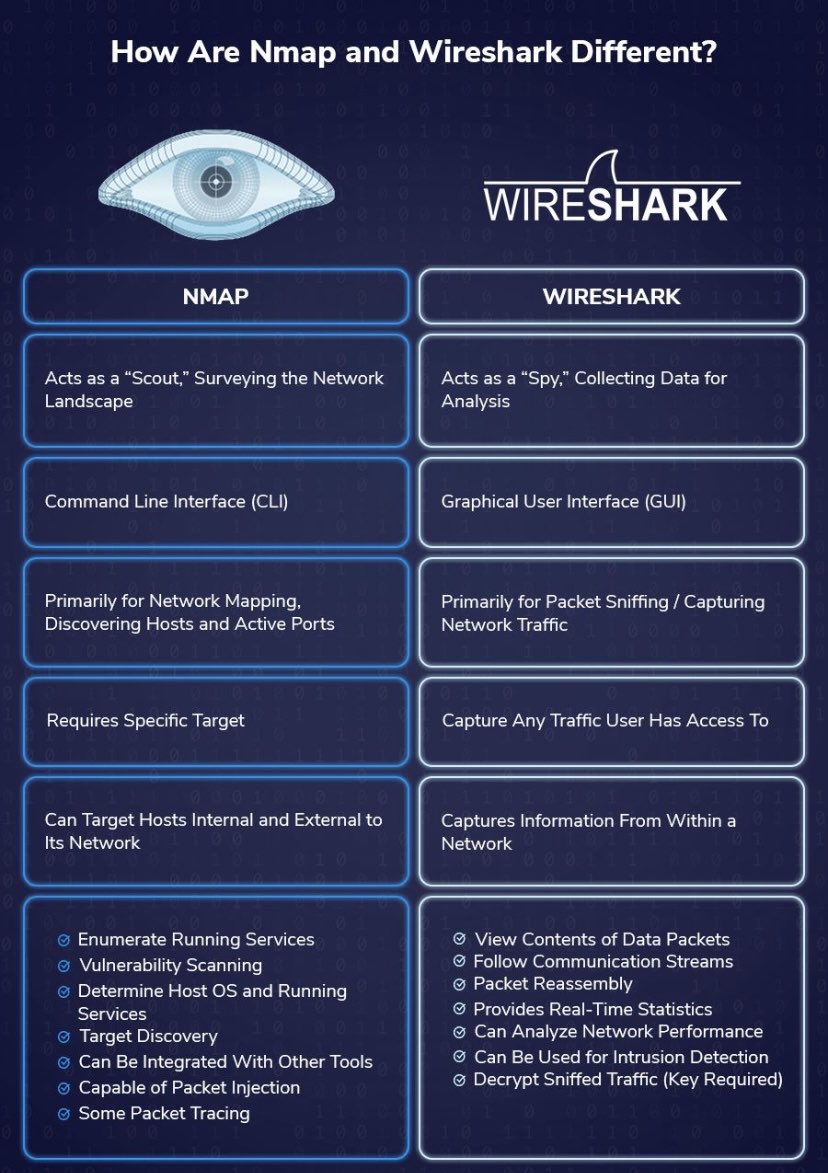
Difference Nmap & Wireshark #cybersecuritytools #cybersecurity #cybersecuritylearning #cybersecurityebook #CybersecurityTraining #CybersecurityCareer #cybersecurityroadmap #cybersecurityteams
command line hex editor for inspecting raw binaries and modifying some bytes. Below is a preview, you can watch the full video on my YouTube channel here: 👇 youtu.be/Q25AryK3gjA?si… #HexEditing #ReverseEngineering #CyberSecurityTools #InfoSec #Cybersecurity #Stodachon #RedTeam
youtube.com
YouTube
Modifying Function Calls in a Binary Using Hex Editing | Reverse...
Talent over Tools: Are You Optimizing Expensive IT and Security Tools? hubs.ly/Q03Mc40Q0 #OneStepSecureIT #CybersecurityTools #CybersecurityTalent
Want to look like a pro in cybersecurity interviews? Mastering tools is like learning the language of cybersecurity. Start learning these 5 tools every beginner should know. DM to Start Your Journey With Us Today! #CybersecurityTools #LaBonneConcepts




Ever wondered how analysts “see” what’s happening inside a network? That’s where Wireshark comes in! 🌐 It helps experts capture, analyze, and troubleshoot network traffic in real-time. #Wireshark #CybersecurityTools #NetworkAnalysis #LearnCybersecurity #Menagos




#SystemHardening #ConfigurationAudit #CyberSecurityTools #ADTECH247inc #BlueTeamOps #DigitalForensics #GovernanceInAction #SecurityAwareness facebook.com/share/p/172qzq…
I just completed Careers in Cyber room on TryHackMe. Learn about the different careers in cyber security. tryhackme.com/room/careersin… #tryhackme via @realtryhackme #CybersecurityTraining #CyberSecurityTools #cybersecurity
Cybersecurity Tools-TO READ MORE APPLICATION SECURITY JOB INTERVIEW QUESTIONS AND ANSWERS amazon.com/Application-Se… #cybersecuritytools #applicationsecurityebook #applicationsecurity #softwaresecurity #cybersecurityebook #CybersecurityCareer #CybersecurityTraining

🔍 Use antivirus and anti-malware tools for extra protection.DM FOR ANY OF THESE TOOLS 🔧 #MalwareProtection #CyberSecurityTools #OnlineSafety

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Saturday 23.3K posts
- 2. #MeAndTheeSeriesEP3 294K posts
- 3. Texas 159K posts
- 4. #JimmySeaFanconD1 522K posts
- 5. #FELIX_MAMAAwards2025 19.6K posts
- 6. 3-8 Florida 2,514 posts
- 7. #SaturdayVibes 2,597 posts
- 8. #BINIFIED 209K posts
- 9. Go Blue 5,581 posts
- 10. hanbin 28.1K posts
- 11. Katie Miller 3,506 posts
- 12. Sark 5,605 posts
- 13. Go Buckeyes N/A
- 14. Go Bucks 1,445 posts
- 15. Sam Houston N/A
- 16. Arch 25.6K posts
- 17. Georgia 50.1K posts
- 18. Lindor 2,833 posts
- 19. Aggies 9,673 posts
- 20. Austin Reaves 14.8K posts