#vulnerabilityanalysis search results
Cybersecurity at home is like... #CyberSecurity #VulnerabilityAnalysis #Hackviser #EthicalHacking #CAPT
Unlock IoT device security with the EXPLIoT IoT Security Learning Kit! 🌐🔒 Master UART, I2C, SPI, JTAG, ZigBee, and BLE analysis with this comprehensive kit. Start your IoT security journey today! 👉 store.expliot.io/products/iot-s… #IoTSecurity #VulnerabilityAnalysis #Cybersecurity

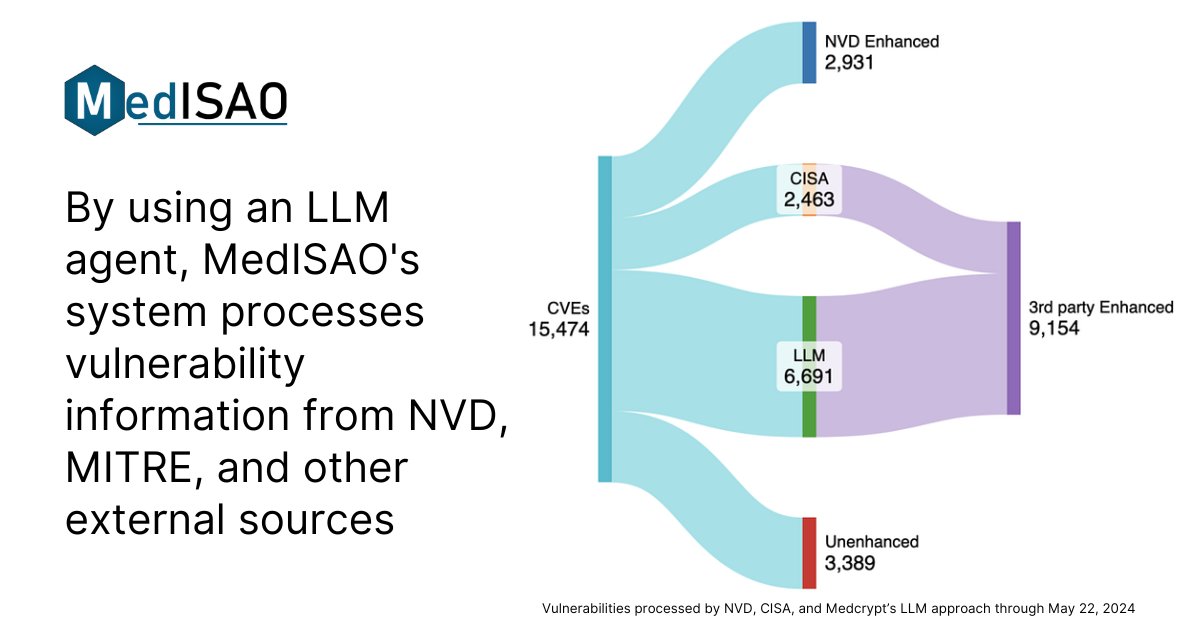
MedISAO Launches AI-Powered Vulnerability Analysis to Address National Vulnerability Database Disruptions prunderground.com/?p=336277 #MedISAO #VulnerabilityAnalysis
Create an EU attrattive market for suppliers is pivotal to increase supply chain diversification in reduce EU market concentration as shown by the results of the @EC_HERA #vulnerabilityAnalysis said @AdrianMEDSforEU at #CMA

cyberdudebivash.com/2025/08/vulner… #CyberDudeBivash #VulnerabilityAnalysis #AIinCybersecurity #ThreatIntel #ZeroDay #AppSec #FutureOfCyber
Safari, Hold Still for NaN Minutes blog.exodusintel.com/2023/12/11/saf… @sherl0ck__ @n30m1nd @XI_Research #VulnerabilityAnalysis #JavaScriptCore #ASLR #Safari
blog.exodusintel.com
Safari, Hold Still for NaN Minutes! - Exodus Intelligence
By Vignesh Rao and Javier Jimenez Introduction In October 2023 Vignesh and Javier presented the discovery of a few bugs affecting JavaScriptCore, the JavaScript engine of Safari. The presentation...
Security Research is the foundation of our work. We uncover hidden vulnerabilities. cyberdagger.com/security-resea… #CyberResearch #VulnerabilityAnalysis

Unearth hidden security risks! Radware's Application Vulnerability Analyzer analyzes server logs to spot vulnerabilities that could jeopardize your enterprise. Shield your data and finances! ow.ly/NMCJ50PU45j #Cybersecurity #VulnerabilityAnalysis #ProtectYourData

Uncover vulnerabilities with Cyberdagger's Security Research. We provide in-depth analysis to strengthen your defenses. Learn more: cyberdagger.com/security-resea… #SecurityResearch #VulnerabilityAnalysis

📢 First paper was published in the special issue: "#VulnerabilityAnalysis and #AdversarialLearning"! Full text at: mdpi.com/2079-9292/12/1… 👉special issue at: mdpi.com/journal/electr… #openaccess #mdpielectronics #electronics

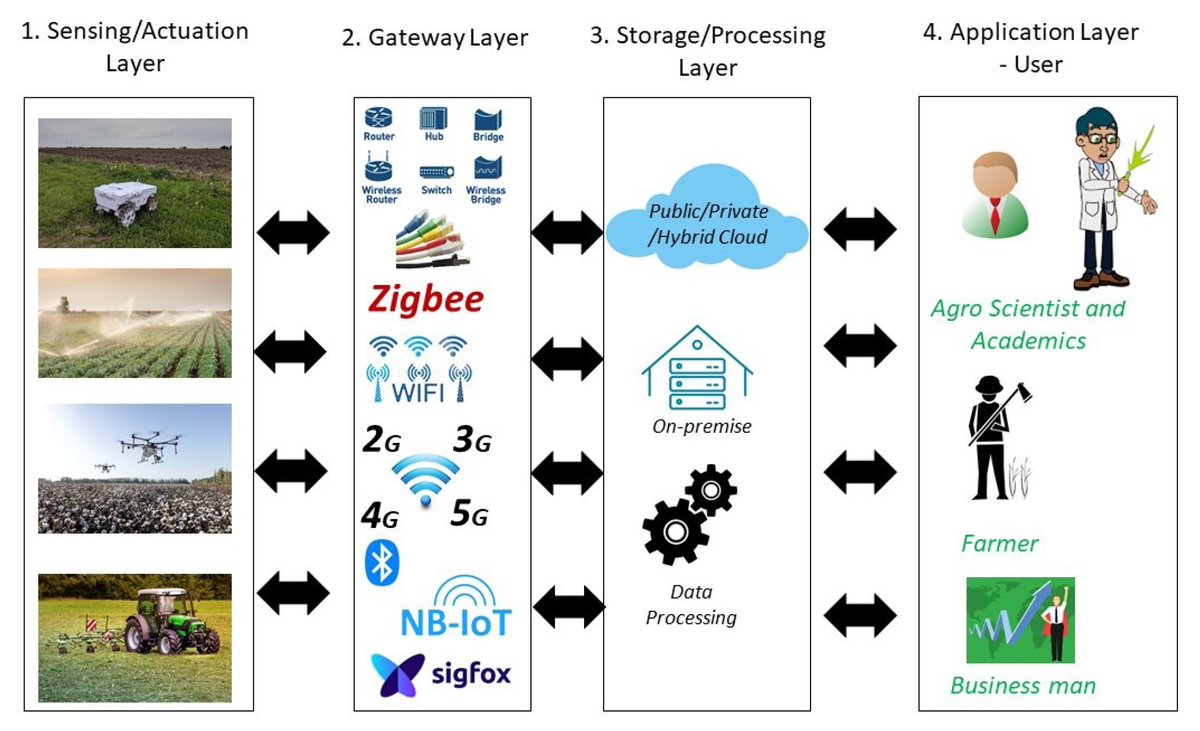
#highlycitedpaper Cyber-Security Threats and Side-Channel Attacks for Digital Agriculture mdpi.com/1424-8220/22/9… #channelattack #vulnerabilityanalysis #poweranalysisattack #securitythreats #cryptography #digitalagriculture #smartagriculture #smartfarming
Enhance Your CEH Skills with Module 5: Vulnerability Analysis Read Here: infosectrain.com/blog/enhance-y… #CEH #VulnerabilityAnalysis #EthicalHacking #CyberSecurity #CEHTraining #ITSecurity #HackingSkills #ProfessionalDevelopment #infosectrain #learntorise

Attacking Android Binder: Analysis and Exploitation of CVE-2023-20938 #AndroidBinder #VulnerabilityAnalysis #Exploitation #AndroidSecurity #RootPrivilege androidoffsec.withgoogle.com/posts/attackin…
#MARCON2023 Workshop 11 - ½ Day Afternoon to learn about the State of Good Repair and how to develop a long-term capital plan with Wayne Cosby, Principal SGR Consultant at @Triad Unlimited marcon.utk.edu! #SGR #VulnerabilityAnalysis #CapitalPlanDevelopment

Anatomy of a zero-day: Dive into the technical details of recent high-profile vulnerabilities and exploit techniques. #StayingAhead #VulnerabilityAnalysis
Getting started on analyzing the vulnerable banking app created by @commando_skiipz! 🔍💻 Today, I'm focusing on static analysis to check for IPC vulnerabilities. Can't wait to dive deeper and share my findings soon! 💜🔒 #VulnerabilityAnalysis #Cybersecurity #BankingAppSecurity
Strengthen Your Security Posture Today! A proactive #SecurityAssessment helps identify risks before they become costly breaches. Get: ✅ #VulnerabilityAnalysis ✅ Tailored Defense Strategies ✅ Proactive #RiskMitigation Stay secure & compliant—book now! hubs.ly/Q034Hf4-0

Pen test report #PenTestReport #CybersecurityAssessment #VulnerabilityAnalysis #SocialEngineering #SQLInjection #XSS #WeakPasswords #Phishing #Vishing #RiskReduction #ProtectingCriticalInfrastructure #DefendingData #SafeguardingInformation #CybersecurityCompliance
🔔🔔🔔 #MDPIfutureinternet [New Published Papers in 2024] Title: SoK: Analysis Techniques for WebAssembly Please read at: mdpi.com/1999-5903/16/3… Keywords: #WebAssembly; #vulnerabilityanalysis; #browsersecurity; cryptojacking; #smartcontracts @ComSciMath_Mdpi
![FutureInternet6's tweet image. 🔔🔔🔔 #MDPIfutureinternet [New Published Papers in 2024]
Title: SoK: Analysis Techniques for WebAssembly
Please read at: mdpi.com/1999-5903/16/3…
Keywords: #WebAssembly; #vulnerabilityanalysis; #browsersecurity; cryptojacking; #smartcontracts
@ComSciMath_Mdpi](https://pbs.twimg.com/media/GICTUyHbwAA6cLo.jpg)
Steps Involved In Penetration Testing And Their Methodology In Cybersecurity rb.gy/nxj9f #VulnerabilityAnalysis #Security #data #internet #QAcycle

2/ The attacker manipulated flawed cross-chain message verification logic to forge transactions and drain funds. #CrossChainSecurity #VulnerabilityAnalysis #Web3Security
Cybersecurity at home is like... #CyberSecurity #VulnerabilityAnalysis #Hackviser #EthicalHacking #CAPT
Getting started on analyzing the vulnerable banking app created by @commando_skiipz! 🔍💻 Today, I'm focusing on static analysis to check for IPC vulnerabilities. Can't wait to dive deeper and share my findings soon! 💜🔒 #VulnerabilityAnalysis #Cybersecurity #BankingAppSecurity
🧠💻 Source Code Vulnerability Analysis CyberAccord dives deep into your code to detect and eliminate hidden vulnerabilities before attackers find them. Stay secure with expert-level insight. 🔍🔐 Learn more: cyberaccord.com #AppSec #CyberSecurity #VulnerabilityAnalysis

Uncover vulnerabilities with Cyberdagger's Security Research. We provide in-depth analysis to strengthen your defenses. Learn more: cyberdagger.com/security-resea… #SecurityResearch #VulnerabilityAnalysis

Security Research is the foundation of our work. We uncover hidden vulnerabilities. cyberdagger.com/security-resea… #CyberResearch #VulnerabilityAnalysis

!exploitable Episode One - Breaking IoT #doyensec #breakingIoT #vulnerabilityAnalysis #exploitable #IoTChallenge blog.doyensec.com/2025/02/11/exp…
Our Research Team found a High-Risk vulnerability in NETGEAR Nighthawk routers models RAX35, RAX38, RAX40 that leaves users open to Local Area Network (LAN) attacks. Proof of Concept: bit.ly/2T8bt5H -- #threatintel #vulnerabilityanalysis #LANattacks
Unlock IoT device security with the EXPLIoT IoT Security Learning Kit! 🌐🔒 Master UART, I2C, SPI, JTAG, ZigBee, and BLE analysis with this comprehensive kit. Start your IoT security journey today! 👉 store.expliot.io/products/iot-s… #IoTSecurity #VulnerabilityAnalysis #Cybersecurity

MedISAO Launches AI-Powered Vulnerability Analysis to Address National Vulnerability Database Disruptions prunderground.com/?p=336277 #MedISAO #VulnerabilityAnalysis

Empirical #vulnerabilityanalysis of automated #smart contracts security testing on #blockchain, #IBM / #ACM #CASCON2018, dl.acm.org/citation.cfm?i… #vulnerability #Ethereum #Solidity #SecurityTesting #Mythril #Oyente #Securify #SmartCheck

#Remediation-verification #Penetrationtest #Vulnerabilityanalysis #Mitigationdevelopment #Vulnerabilityverification #Securesourcescode #VAPT #Infosec #cybersecurity #cybersecurityservice | @briskinfosec bit.ly/2LfyKet

NETGEAR Nighthawk 4-Stream Dual-Band WiFi 6 Router vulnerability analysis. Our proof of concept: bit.ly/3haG8ZK -- #threatintel #securityresearch #vulnerabilityanalysis #LANattacks
#highlycitedpaper Cyber-Security Threats and Side-Channel Attacks for Digital Agriculture mdpi.com/1424-8220/22/9… #channelattack #vulnerabilityanalysis #poweranalysisattack #securitythreats #cryptography #digitalagriculture #smartagriculture #smartfarming

“Household Level #VulnerabilityAnalysis—Index and Fuzzy Based Methods” by Martina Baučić 👉mdpi.com/2220-9964/9/4/… #ClimateChange #FuzzyLogic #SeaLevelRise

@WFP engages communities in #vulnerabilityanalysis using household economy approach in #Gambia with drivers' support



What is Vulnerability Analysis? | Types of Vulnerability Analysis | CEH V11 youtu.be/5xflxX_MBWo #VulnerabilityAnalysis #CEHV11 #Training #Certification #Crawsec

#MARCON2023 Workshop 11 - ½ Day Afternoon to learn about the State of Good Repair and how to develop a long-term capital plan with Wayne Cosby, Principal SGR Consultant at @Triad Unlimited marcon.utk.edu! #SGR #VulnerabilityAnalysis #CapitalPlanDevelopment

Vulnerability Analysis of CVE-2018-12613 – phpMyAdmin 4.8.1 Remote Code Execution. Get details here: bit.ly/3cNbkzb #vulnerabilityanalysis #phpMyAdmin #Vulnerability

📢 First paper was published in the special issue: "#VulnerabilityAnalysis and #AdversarialLearning"! Full text at: mdpi.com/2079-9292/12/1… 👉special issue at: mdpi.com/journal/electr… #openaccess #mdpielectronics #electronics

Unearth hidden security risks! Radware's Application Vulnerability Analyzer analyzes server logs to spot vulnerabilities that could jeopardize your enterprise. Shield your data and finances! ow.ly/NMCJ50PU45j #Cybersecurity #VulnerabilityAnalysis #ProtectYourData

TOR’s for Baseline, Vulnerability Analysis and Political Economy Analysis. Access full details on goo.gl/91bLBQ . #CommunityPolicing #VulnerabilityAnalysis #PoliticalEconomyAnalysis

We’re looking for a Reverse Engineer with expertise in Software Defined Radios! Join a team composed of leaders in #RF, #computersecurity, system #vulnerabilityanalysis and #softwareengineering. Apply here: lnkd.in/gRNVUnb5

🔔🔔🔔 #MDPIfutureinternet [New Published Papers in 2024] Title: SoK: Analysis Techniques for WebAssembly Please read at: mdpi.com/1999-5903/16/3… Keywords: #WebAssembly; #vulnerabilityanalysis; #browsersecurity; cryptojacking; #smartcontracts @ComSciMath_Mdpi
![FutureInternet6's tweet image. 🔔🔔🔔 #MDPIfutureinternet [New Published Papers in 2024]
Title: SoK: Analysis Techniques for WebAssembly
Please read at: mdpi.com/1999-5903/16/3…
Keywords: #WebAssembly; #vulnerabilityanalysis; #browsersecurity; cryptojacking; #smartcontracts
@ComSciMath_Mdpi](https://pbs.twimg.com/media/GICTUyHbwAA6cLo.jpg)
JSRAT – Secret Command & Control Channel Backdoor to Control Victims Machine Using JavaScript bit.ly/3936yrD #Backdoor #ExploitationTools #VulnerabilityAnalysis

Something went wrong.
Something went wrong.
United States Trends
- 1. #RaiseHail 2,384 posts
- 2. Good Sunday 80.4K posts
- 3. Matt Gay N/A
- 4. #PhinsUp 2,175 posts
- 5. Achane 1,841 posts
- 6. #AskFFT N/A
- 7. Jacob Martin N/A
- 8. Mariota 1,125 posts
- 9. #sundayvibes 6,133 posts
- 10. #Dolphins N/A
- 11. Chris Rodriguez N/A
- 12. Spain 72.8K posts
- 13. Kenneth Grant N/A
- 14. CRod N/A
- 15. Kliff N/A
- 16. Who Dey 8,103 posts
- 17. Blessed Sunday 22.6K posts
- 18. Portugal 60.8K posts
- 19. Full PPR N/A
- 20. Merritt 1,559 posts




































