#catchvulnerabilities نتائج البحث
Such vulnerabilities also I recommending you to form an dedicated in house team to hunt any and every such and other vulnerabilities and loopholes in your systems #meta #Microsoft #google #instagram #linkedin #x #twitter
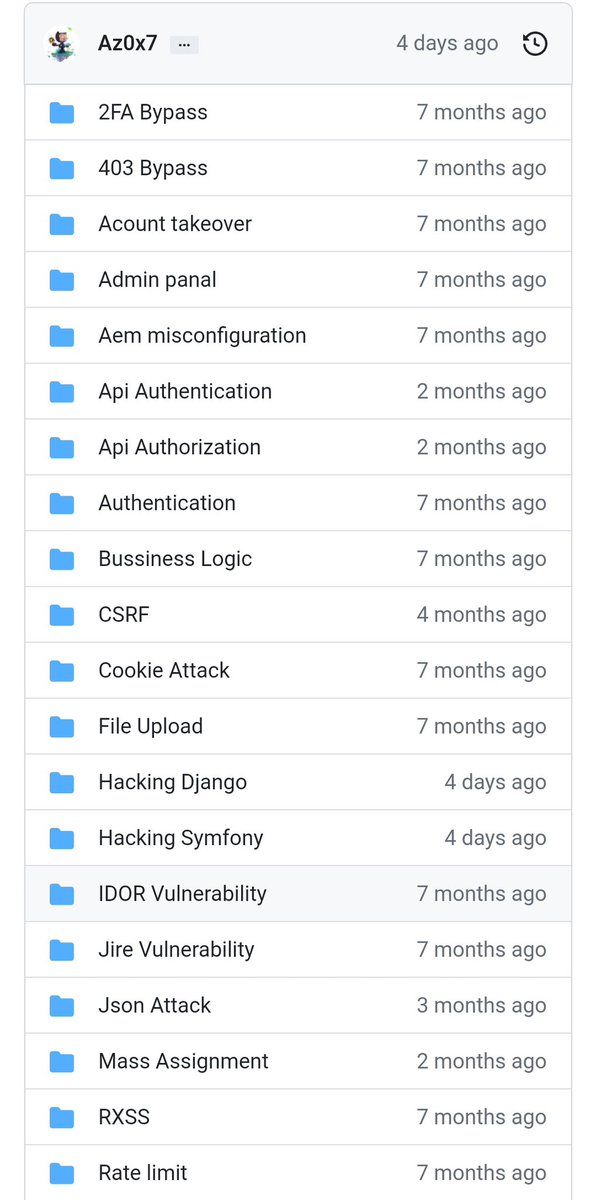
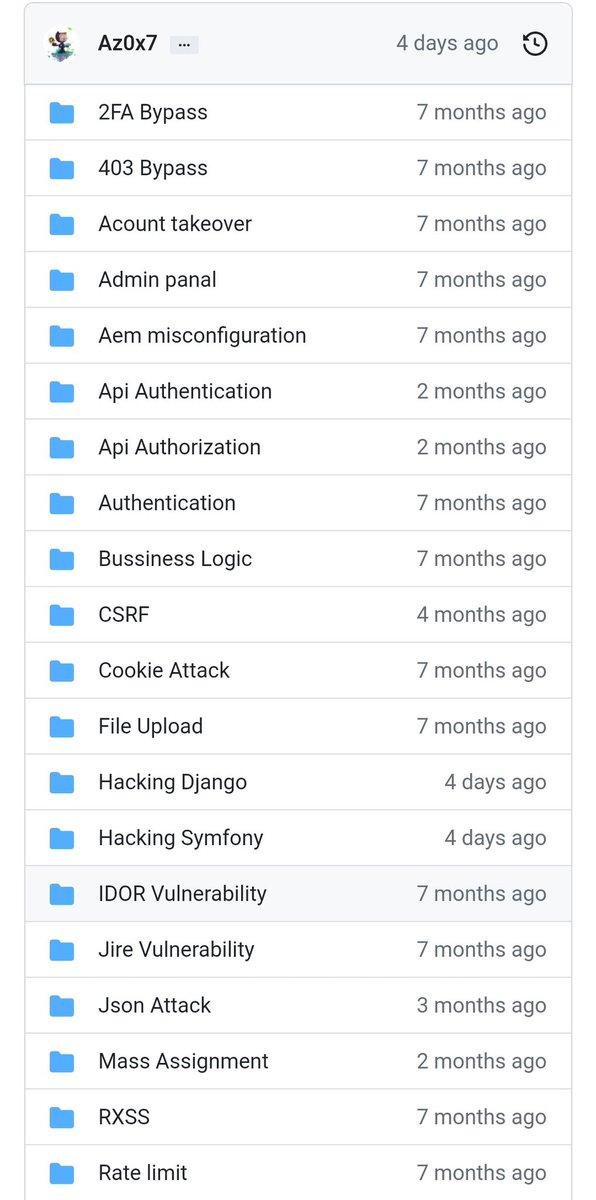
This repository contain a lot of web and api vulnerability checklist , a lot of vulnerability ideas and tips from twitter Source: github.com/Az0x7/vulnerab…

This repository contain a lot of web and API vulnerability checklist , a lot of vulnerability ideas and tips. #bugbounty #bugbountytip #bugbountytips github.com/Az0x7/vulnerab…
Another vulnerable piece of code 🔥 Can you find the vulnerability here? (Not hard-coded credentials) #BugBounty #bugbountytips #Hacking #Hackingtime

Vulnerability checklist: 📓⚔️ This repository contains a lot of web and API vulnerability checklist, a lot of vulnerability ideas, and tips from twitter - github.com/Az0x7/vulnerab… #infosec #cybersec #bugbountytips
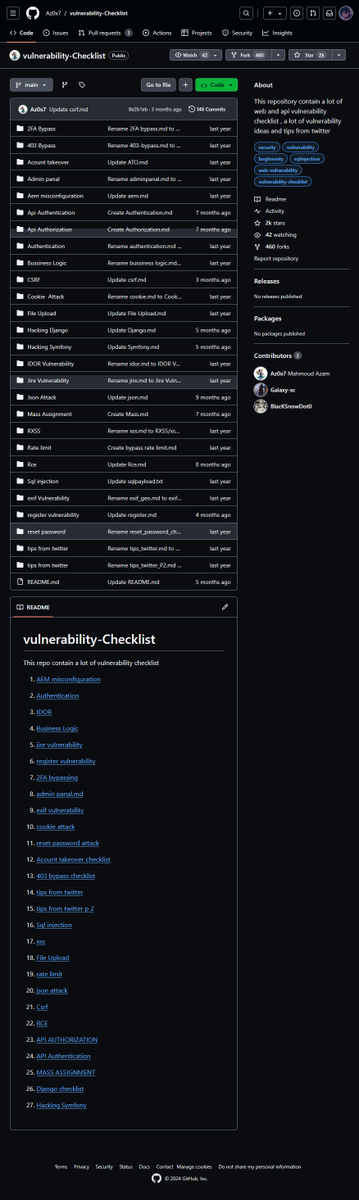
This repository contain a lot of web and api vulnerability checklist Source:github.com/Az0x7/vulnerab… Credits:@wtf_brut #bugbountytips #BugBounty #bugbountytip #bugbounty #infosec #datasecurity #networksecurity #cyberaware #cyberdefense #cyberthreats #cybersafety #cyberattack
The ART of Chaining Vulnerabilities Have a read: ahmdhalabi.medium.com/the-art-of-cha… #cybersecurity #Pentesting #Hacking #bugbountytips #infosec #cybersecuritytips #redteam #coding #100DaysOfHacking #vulnerabilities #BugBounty #100DaysOfCyberSecurity #CyberSecurityAwareness

🚨This repository contain a lot of web and api vulnerability checklist🚨 📥lots of vulnerability ideas and tips from twitter✅ 📥Source github.com/Az0x7/vulnerab… #bugbountytip #bugbountytips #ethicalhacking #CyberSecurity #Pentesting #sqli #xss #CyberSecurityAwareness
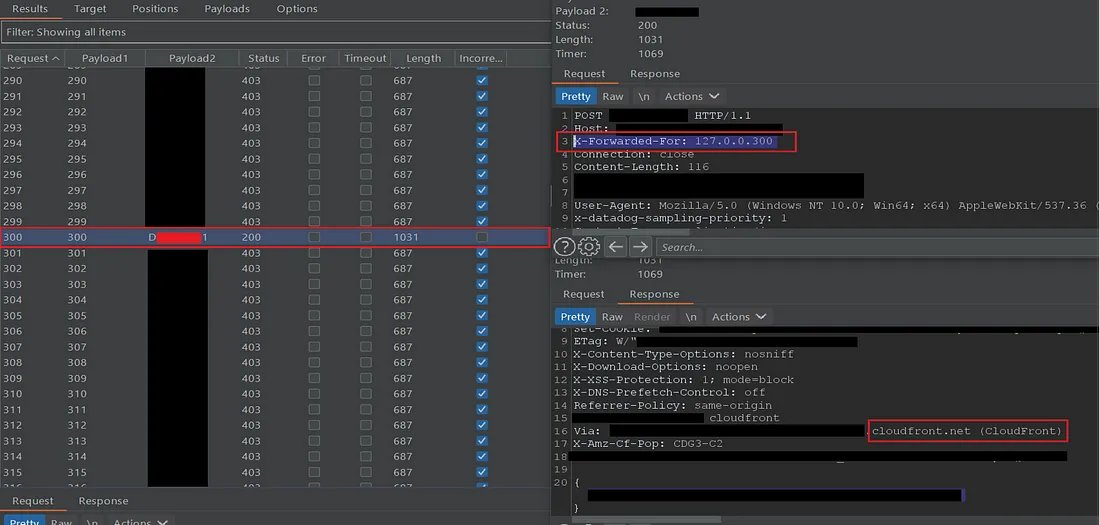
Some of the major vulnerabilities and related POC’s: ➡SQLi ➡XSS ➡SSRF ➡XXE ➡Path Traversal ➡Open Redirection ➡Account Takeover ➡Remote code execution ➡IDOR ➡CSRF #hacking #bugbounty #bugbountytips Are Found Below🧵(1/n)👇
Back in the day, I needed to figure out a way to learn common vulnerabilities. Quickly. And guess what? That's how the "find the bug" challenges came out. I have compiled them in an article, so you can use them to practice. Here's how: 👇 blog.bytes032.xyz/p/how-to-learn…
Some of the major vulnerabilities and related POC’s: ➡SQLi ➡XSS ➡SSRF ➡XXE ➡Path Traversal ➡Open Redirection ➡Account Takeover ➡Remote code execution ➡IDOR ➡CSRF #hacking #bugbounty #bugbountytips Are Found Below🧵(1/n)👇
List of tutorials and things to look for while hunting for vulnerabilities 🐛 (- compiled by @KathanP19 and other awesome contributors) github.com/KathanP19/HowT… #cybersecurity #bughunting #hacking
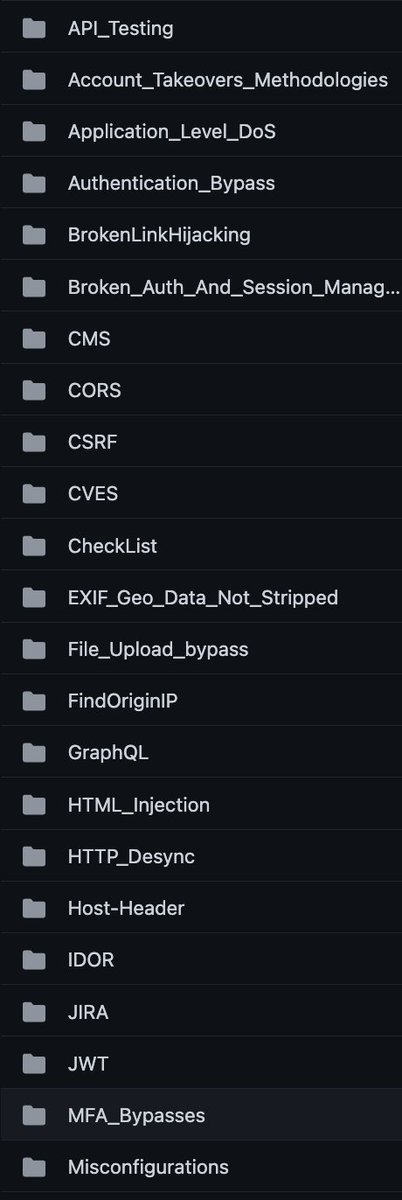
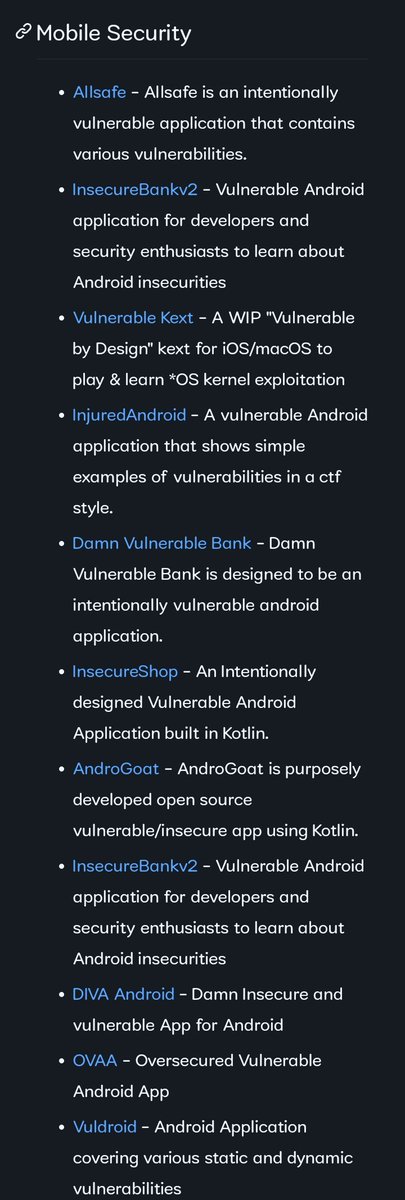
A curated list of Intentionally Build Vulnerable Apps and Systems which can be used for Penetration Testing Practice & Bug Bounty too. github.com/kaiiyer/awesom… github.com/vavkamil/aweso…
Have you heard of these 10 obscure web vulnerabilities? @Farah_Hawaa and @hakluke share the top web vulnerabilities that are often missed during security testing. bit.ly/3AWaZkp
This is a bit dated, but it's a very well written article on the vulnerability research process, from setting up the environment to target selection, and from bug hunting via fuzzing to exploitation. Very recommended reading. medium.com/@maxi./finding…
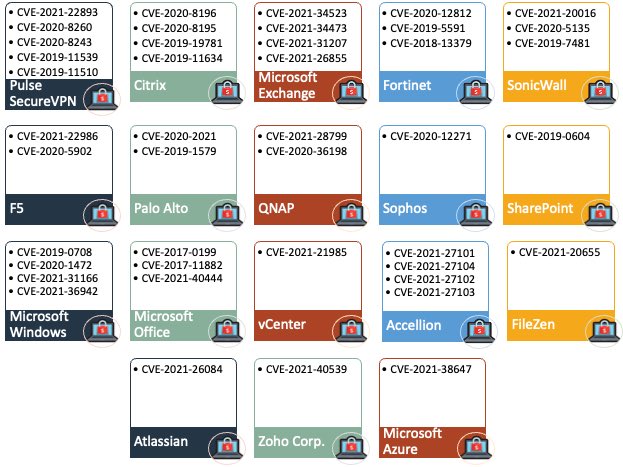
So, we are up to 42 vulnerabilities across 17 technologies (with 1 pending) that ransomware groups exploit for initial access. This is why preaching “just patch” isn’t good enough. I don’t know what the answer is, but what we’re doing clearly isn’t working.
Precision of language is important. A vulnerability is a weakness that has to be exploited by a threat. You don't detect vulnerabilities - you detect the threats that exploit them.
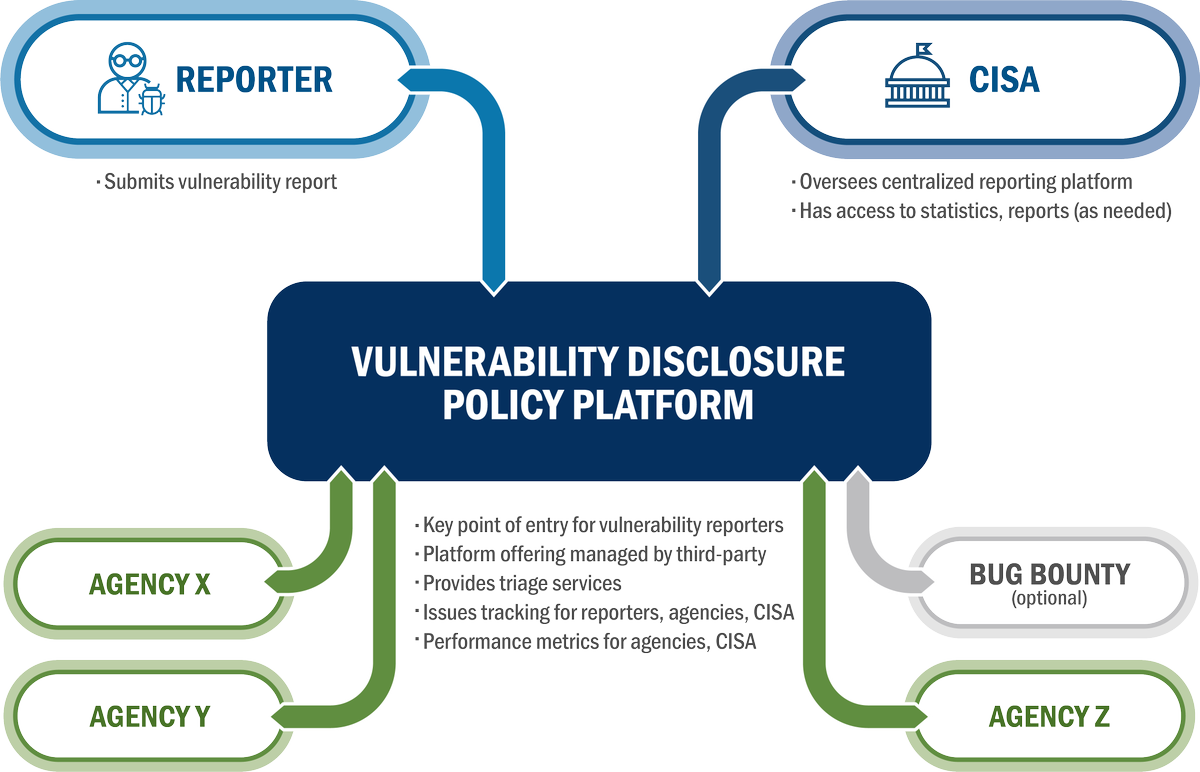
It shouldn’t be hard to report a vulnerability. @CISAgov's NEW Vulnerability Disclosure Platform makes it easy & safe to notify federal agencies of vulnerabilities so they can be fixed. See a vulnerability? Report it: go.usa.gov/xFkgz Research community 🤝 @CISAgov
Here's a new Vulnerability Coordination Maturity Model to benchmark capabilities when a security bug is reported: hackerone.com/blog/vulnerabi…
Something went wrong.
Something went wrong.
United States Trends
- 1. Cyber Monday 50.3K posts
- 2. Admiral Bradley 2,875 posts
- 3. TOP CALL 11.5K posts
- 4. GreetEat Corp. N/A
- 5. Shakur 6,507 posts
- 6. #Rashmer 18.7K posts
- 7. #GivingTuesday 3,155 posts
- 8. Adam Thielen 2,719 posts
- 9. Alina Habba 36.3K posts
- 10. Hartline 3,017 posts
- 11. MSTR 29.8K posts
- 12. Check Analyze N/A
- 13. Token Signal 3,812 posts
- 14. Toosii 1,093 posts
- 15. #IDontWantToOverreactBUT 1,522 posts
- 16. MRIs 2,071 posts
- 17. UCLA 7,132 posts
- 18. Marty Supreme 3,654 posts
- 19. LA PIJAMADA VIRAL 57.8K posts
- 20. Clarie 4,050 posts