#ethicalhacker نتائج البحث
What is an Ethical Hacker? A “guardian hacker” authorized to probe systems and secure them. Advance your skills with CEH courses: v13 (AI-enhanced), CEH v12 (comprehensive), CEH v10 Masterclass (hands-on). bilginc.com/en/blog/what-i… #EthicalHacker #CEH

Jangan sembarang ngehack kalo gamau ditangkep! Tapi tau gasih kalo ternyata ada orang yang sengaja digaji buat ngehack? #Reduksi #SiberSosial #EthicalHacker #CyberSecurity #SocialEngineering #HackerTips
Exploring the Essentials of Cyber Insurance: Three Critical Types to Consider terrycutler.com/exploring-the-… #Insurance #EthicalHacker

Online harassment is real but you don’t have to face it alone. If you’re being threatened, blackmailed, or harassed online, we can help you trace and stop the perpetrators. 💻🛡️ Your safety matters. Reach out today. #OnlineSafety #CyberSecurity #EthicalHacker #StopHarassment



Vulnerability scanners play a pivotal role in safeguarding digital assets by proactively identifying security weaknesses. Let me explain at cybersecuritymadeeasy.com #vulnerabilityscanning #cybersecurity #ethicalhacker #hacker
You might think your business is secure. Hackers are always looking for ways to get in, which is why you always have to stay one step ahead. Visit CybersecurityMadeEasy.com to learn more. #cybersecurity #ethicalhacker #cyberattacks
Any business, regardless of its size, can be affected by ransomware. With our #vulnerabilityscanning services, you'll know exactly your weaknesses. For more info, visit CybersecurityMadeEasy.com #Ransomware #EthicalHacker #CyberSecurity
He was trained on exploits, payloads, and patterns of chaos. Now he uses that knowledge to protect. The future of ethical hacking mentorship is here. AI_Z3RO_HUNT3R — born in the breach. ⚡ #AI #CyberSecurity #EthicalHacker #InfoSec #RedTeam
I am incredibly honored to be globally recognized by @WHO in collaboration with the @UN for disclosing a critical security vulnerabilities in one of their online systems. who.int/about/cybersec… #applicationsecurity #cybersecurity #ethicalhacker

AI is on the front lines of cybersecurity! It is a multiplier of good and bad. AI is building a safer digital future by detecting threats and predicting attacks. CybersecurityMadeEasy.com #AI #EthicalHacker #Cybersecurity
ETHICAL HACKER youtube.com/watch?v=LEjLFE… #EthicalHacker #Music #IndieMusic
youtube.com
YouTube
ETHICAL HACKER
How do I know if I’m doing it right? Suspect a data breach? Common signs: unusual login activity, missing files, or ransom demands. Take immediate action: Change credentials and initiate device scans. Call us at CybersecurityMadeEasy.com #CybersecurityAwareness #EthicalHacker
🧩 Ethical hacking is like a health check-up for your systems. Identify risks, patch vulnerabilities, and safeguard your business continuity. Contact Email: [email protected] #PenTest #EthicalHacker #HireAHacker #privateinvestigations #CyberSecurity #RiskAssessment…

Maintaining business compliance is crucial for protecting both your customers and your business. If you’re struggling to maintain compliance standards, we have a solution. CybersecurityMadeEasy.com #continuity #ethicalhacker

¿Qué es Hacking Ético? Guía Completa del Defensor Digital #EthicalHacker #HackingÉtico #Pentesting #SeguridadOfensiva #WhiteHatHacker #Seguridad esgeeks.com/que-es-hacking…
பீகாரின் Batman! ஆன்லைன் மோசடி சிக்கியவர்களுக்கு இலவசமாக உதவி செய்து அசத்திய இளைஞர்! #Bihar #MrityunjaySingh #EthicalHacker #CyberSecurity #Offbeat #OneindiaTamil | Image: AI Generated

We stay ahead of threats by tracking, detecting, and shutting down digital fraud found . #FraudDetection #DigitalProtection #EthicalHacker #OnlineSafety #CyberDefense #DataSecurity #InfoSec #TechSecurity #FraudPrevention #hacker #scam #scammer #fraud

Your trusted partner in proactive cybersecurity and digital resilience.” Confidential Consultation: 📩 [email protected] 🌐 RecoveryPro.Online 💼 Expertise | Integrity | Security #EthicalHacker #Investigator #StockMarket #InvestmentScam

Per il 10° anno della Geeks 𝟮.𝟰𝟱𝟬€ 𝗶𝗻𝘃𝗲𝗰𝗲 𝗱𝗶 𝟯.𝟰𝟱𝟬€ #EthicalHacker, corso pratico con laboratori di #PenetrationTesting e #VulnerabilityAssessment per lavorare nella #Cybersecurity #CertificazioneInternazionale #EthicalHacking. Febbraio 2025 classi di12 Studenti

Another milestone attain for completing another Cyber security course on Security information and event managements(SIEMs) at letsdefend. #BlueTeamer #socanalyst #ethicalhacker #cybersecurity Check my cybersecurity transcript app.letsdefend.io/user/aguifeany…
From scanning to securing, every ethical hacker’s mission is the same — protect before the attack happens. Your system’s biggest risk isn’t a hacker… it’s ignoring cybersecurity. 💡 Tip: Always use MFA + strong passwords. #CyberAwareness #EthicalHacker #CyberSecurity

Geeks Academy turns 10 and offers 10 #scholarships worth €1,000. Become an #EthicalHacker with hands-on training in #PenetrationTesting and #VulnerabilityAssessment. Includes #EXIN certs + #career support. Starting November. is.gd/Ethical_Hacker…

If your site suddenly shows Japanese text or spam links in Google it’s likely a Japanese keyword hack. I recently helped a client fully recover from this attack cleaned malware, removed injected links, and restored their rankings. #WordPressSecurity #WebsiteHack #EthicalHacker
At Ethical Hacker, we stay ahead of threats by tracking, detecting, and shutting down digital fraud before it strikes. Your safety is our 24/7 mission CyberSecurity. #FraudDetection #DigitalProtection #EthicalHacker #OnlineSafety #CyberDefense #DataSecurity #InfoSec…

பீகாரின் Batman! ஆன்லைன் மோசடி சிக்கியவர்களுக்கு இலவசமாக உதவி செய்து அசத்திய இளைஞர்! #Bihar #MrityunjaySingh #EthicalHacker #CyberSecurity #Offbeat #OneindiaTamil | Image: AI Generated

Exploring the Essentials of Cyber Insurance: Three Critical Types to Consider terrycutler.com/exploring-the-… #Insurance #EthicalHacker

What is an Ethical Hacker? A “guardian hacker” authorized to probe systems and secure them. Advance your skills with CEH courses: v13 (AI-enhanced), CEH v12 (comprehensive), CEH v10 Masterclass (hands-on). bilginc.com/en/blog/what-i… #EthicalHacker #CEH

Online harassment is real but you don’t have to face it alone. If you’re being threatened, blackmailed, or harassed online, we can help you trace and stop the perpetrators. 💻🛡️ Your safety matters. Reach out today. #OnlineSafety #CyberSecurity #EthicalHacker #StopHarassment




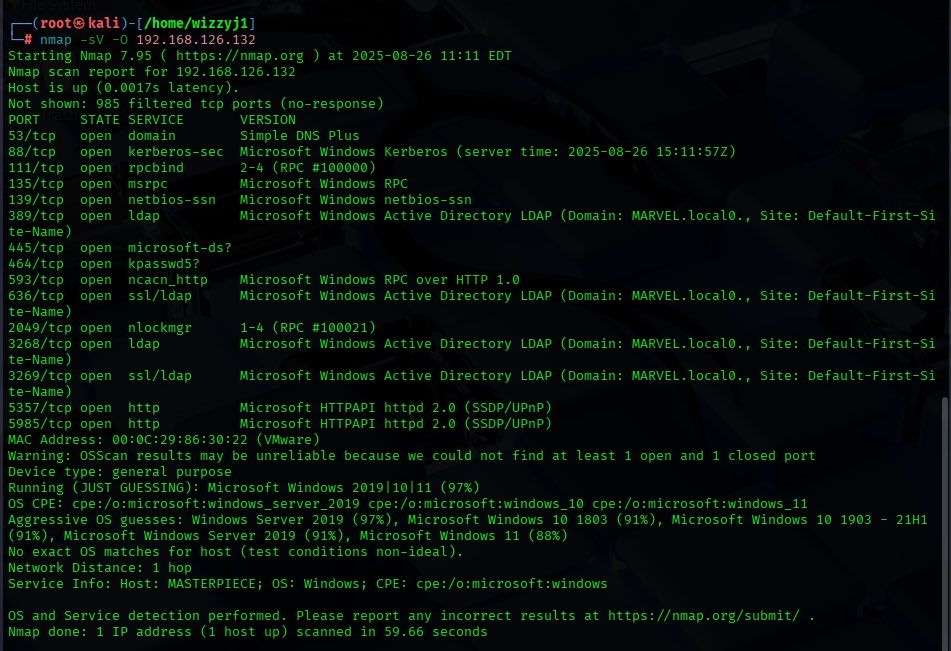
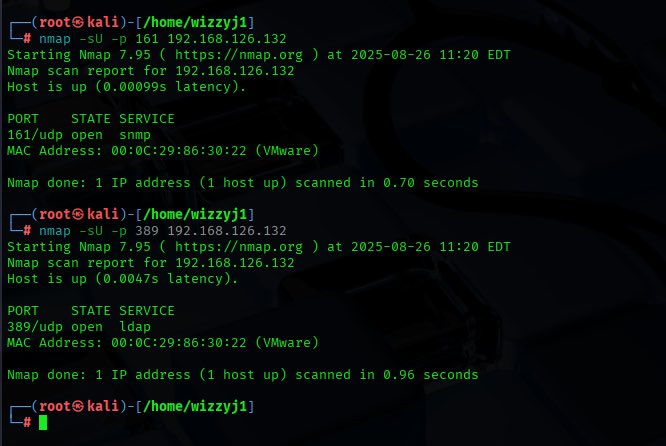
Performed SNMP and LDAP enumeration to retrieve informations about switches,routers,printers,user names,domain controller,OS version etc after my Nmap scan result #CyberSecurity #EthicalHacker #LifeofAPentester #SNMPEnumeration #LDAPEnumeration
Ethical hacking for good purpose and social media recovery. #ethicalhacker #computer #programming #coding #python #security #developer #java #hacked #anonymous #programmer #hack #computerscience #coder #Germany #hacker #cybersecurity #cyber #hacking #linux #Kuwait_University

If you want to stop digital threats before they hit, this book is your best guide. Get smart, stay safe, and get Insider Secrets. #CyberSecurity #EthicalHacker #SmilingEyesPress

Maintaining business compliance is crucial for protecting both your customers and your business. If you’re struggling to maintain compliance standards, we have a solution. CybersecurityMadeEasy.com #continuity #ethicalhacker

Clear communication: We provide regular, detailed reports on your systems and maintain open lines of communication. For a free consultation, reach out to us at CybersecurityMadeEasy.com #Cybersecurity #EthicalHacker

Proven experience: They have an extensive track record of successfully managing cybersecurity services for businesses in your industry. For a free consultation, reach out to us at CybersecurityMadeEasy.com #Cybersecurity #EthicalHacker

Think like a hacker. The best ethical hackers are naturally curious. Are you? 👉 Follow @real3uni for More #EthicalHacker #HackerMindset #TechCurious #CybersecurityLife #LearnToHack #HackTheFuture #WhiteHatHacker #GenZTechies #TechEducation #CyberReady #DigitalDefenders…

We stay ahead of threats by tracking, detecting, and shutting down digital fraud found . #FraudDetection #DigitalProtection #EthicalHacker #OnlineSafety #CyberDefense #DataSecurity #InfoSec #TechSecurity #FraudPrevention #hacker #scam #scammer #fraud

Predictable pricing: We offer transparent pricing with no hidden fees. Want to see how we measure up? Let’s talk! For a free consultation, reach out to us at CybersecurityMadeEasy.com #Cybersecurity #EthicalHacker

I am incredibly honored to be globally recognized by @WHO in collaboration with the @UN for disclosing a critical security vulnerabilities in one of their online systems. who.int/about/cybersec… #applicationsecurity #cybersecurity #ethicalhacker

Don’t just use the internet - protect it. 💻 Learn how real-world hackers think, act, and get stopped. 📍 CEH v13 is your ticket to the frontline of cyber defense. 🔗 Enroll today: 3university.io/certified-ethi… #EthicalHacker #CEHv13 #CybersecurityCareer #DigitalDefense

#Hacking #CyberSecurity #EthicalHacker #DigitalForensics #CyberDefense #Hackers #InfoSec #TechExpert #DataRecovery #CryptoRecovery #InvestmentSecurity #AccountProtection #SocialMediaSecurity #SocialMediaRecovery #AccountHacking #SpyOnSocialMedia #SocialMediaSpy #OnlineMonitoring…

Prioritizes security: They implement comprehensive security measures and continuously monitor your systems to keep your business protected. For a free consultation, reach out to us at CybersecurityMadeEasy.com #Cybersecurity #EthicalHacker

𝐓𝐨𝐩 𝐏𝐫𝐨𝐠𝐫𝐚𝐦𝐦𝐢𝐧𝐠 𝐋𝐚𝐧𝐠𝐮𝐚𝐠𝐞𝐬 𝐟𝐨𝐫 𝐇𝐚𝐜𝐤𝐢𝐧𝐠 𝐢𝐧 𝟐𝟎𝟐𝟓 #Hacking #EthicalHacker #CyberSecurity #ProgrammingLanguage #AI #AINews #AnalyticsInsight #AnalyticsInsightMagazine Read More👇 zurl.co/l0gNO

Something went wrong.
Something went wrong.
United States Trends
- 1. Austin Reaves 44K posts
- 2. Steelers 84.8K posts
- 3. Tomlin 12.4K posts
- 4. Packers 66.6K posts
- 5. Tucker Kraft 15.5K posts
- 6. Jordan Love 16.8K posts
- 7. Derry 20K posts
- 8. #GoPackGo 10.7K posts
- 9. #BaddiesAfricaReunion 9,732 posts
- 10. #LakeShow 3,748 posts
- 11. Pretty P 4,057 posts
- 12. Zayne 20.6K posts
- 13. #breachlan2 2,897 posts
- 14. Dolly 12.6K posts
- 15. #LaGranjaVIP 70.9K posts
- 16. Rodgers 38.7K posts
- 17. Teryl Austin 2,176 posts
- 18. yixing 10.2K posts
- 19. Sabonis 2,495 posts
- 20. yeonjun 52.1K posts