#windowssecurity search results
1000+ alumni, 10 editions, and one course that prepares you for 2026’s threats 🎉 In 3 weeks, we're launching the 10th edition of our Advanced Windows Security Course, so join us last-minute 👉cqureacademy.com/cyber-security… #CyberSecurity #WindowsSecurity

Windows & Linux Enumeration: Discover What the System Reveals 🖥️🐧🔍 #Enumeration #LinuxSecurity #WindowsSecurity #InfoSec #EthicalHacking #CyberSecurity #EducationOnly #SystemRecon #PrivilegeEscalation #RedTeamTools




Fresh invite to our Advanced Windows Security Course 2026, served from @BlackHatEvents USA 💌 6 weeks of intensive, no-fluff training for pros fluent in Windows & pentesting. Ready for the challenge? Apply here 👉 cqureacademy.com/cyber-security… #CyberSecurity #WindowsSecurity
I explain how Windows implements ASLR, how it affects reverse engineering and exploitation, and practical ways to analyze or bypass it when needed. reverselabs.dev/blog/aslr-addr… #WindowsSecurity #ReverseEngineering #ExploitDevelopment #MemoryProtection

Windows memory management is one of the most critical areas of #WindowsInternals!❌ Watch @samilaiho bust some myths around it in this demo from our previous Advanced Windows Security Course 👉 youtube.com/watch?v=CBHYp3… #WindowsSecurity
الجزء 2 | 🚨 Windows Forensics Series تحليل العمليات، الشبكة، المستخدمين، الخدمات، والمهام المجدولة 🔍 📌 الهدف: كشف أي نشاط مريب أو Shell يعمل بصمت داخل النظام. #DFIR #WindowsSecurity #CyberSecurity ⬇️ تابع 🧵 1 📌 تحليل العمليات المتقدمة: wmic process list full يعرض…

🛡️¿Qué es el Windows Security Center (WSC)?🛡️ Conoce qué es el Windows Security Center (WSC), aprende sobre este servicio que te permite gestionar tu antimalware. 🔗 Te invitamos a ver el video completo: youtu.be/N0StZjUXlfM #WSC #WindowsSecurity
The registration for our comprehensive Advanced Windows Security Course 2026 is now open 👉 cqureacademy.com/cyber-security… Expect real brain workout with industry experts, spanned across 12 comprehensive modules 🧠🏋️♂️ #WindowsSecurity #ITsecurity #CyberSecurity
Just days away from the @TechMentorEvent at Microsoft HQ! 📆 @PaulaCqure delivers two must-see cybersecurity sessions on August 12th on DPAPI and DPAPI-NG & Forensics Skillset. We hope to see you there! 👀 #Cybersecurity #TechMentor #WindowsSecurity #DPAPI

Ever wondered how a factory can run smoothly with 40 endpoints, 7 servers, and zero IT staff? Sami Laiho, Chief Research Officer and Windows & Security MVP, will share his incredible story. #CyberSecurity #WindowsSecurity #Ransomware #ITLeadership #MVP

I’m excited to share that some of my recent research into Windows internals and native binaries has officially been added to the LOLBAS project. Check out: Eudcedit.exe, Reset.exe lolbas-project.github.io/lolbas/Binarie… #SecurityResearch #LOLBAS #WindowsSecurity #OffensiveSecurity #RedTeam
Are you ready to take your Windows security skills to the expert level? Join me and @Amr_Thabet on June 9th for a super intense Live Virtual Class and let’s uncover modern attack techniques and defense strategies 🕵️♀️ Sign up here ➡️ cqureacademy.com/cyber-security… #WindowsSecurity
Unmasking Malware's Tricks! 🔍 This encyclopedia reveals Windows evasion techniques used by malware to hide in virtual environments. Learn to detect and analyze even the stealthiest threats. buff.ly/3XJLtMT Credit goes to Checkpoint! #Cybersecurity #WindowsSecurity

Hurry up, this is the last chance to enter our virtual classroom with up to 35% discounts! 🔔 The Back to School offer on our flagship online courses expires tomorrow, so don’t be late for premiere cybersec education 👉 cqureacademy.com/back-to-school/ #Cybersec #CQURE #WindowsSecurity
Episode #65 of our CQURE Hacks just dropped! 💥 In this one, we're tackling the CVE-2025-33073 Windows SMB vulnerability that's turning network access into full system compromise. Watch the demo👉 cqureacademy.com/blog/65-ntlm-r… Your security team needs to see this 👁 #WindowsSecurity…

Over 𝟲𝟬𝟬 𝗺𝗶𝗹𝗹𝗶𝗼𝗻 𝗰𝘆𝗯𝗲𝗿𝗮𝘁𝘁𝗮𝗰𝗸𝘀 hit Windows users every day, that's over a million threats an hour! As hackers step up their infiltration game, even companies like Microsoft are in the line of fire 🔫 #CyberSecurity #DataProtection #WindowsSecurity

What if you could secure Windows like a pro? 🤔 Join one of @PaulaCqure's live virtual classes on Windows Infrastructure and Forensics & Incident Response this August 👉cqureacademy.com/live-virtual-c… #CyberSecurity #WindowsSecurity
September 9th we’re revealing the cards of 2026’s cyber threats landscape 🃏 Sign up for the FREE live webinar with @PaulaCqure, @samilaiho, @Amr_Thabet & Marcin Krawczyk 👉 cqureacademy.com/webinars/vulne… + challenge with BIG prize🎁 #FreeWebinar #Cybersecurity #WindowsSecurity
Another Hackviser's machine 007 solved!! POC: app.hackviser.com/show/sakibulal… #Windows_host_discovery #RDP #windowssecurity

💻 System Information & Resource Monitor – Tracked CPU, memory, disk & network usage for process-level monitoring. 🧠 Command Prompt & Registry Editor – Practiced core commands & registry analysis for system configuration insight. #ThreatDetection #WindowsSecurity
What Are Some Other Famous Apple Ads That Mock Windows Security? dlvr.it/TNZbfQ #AppleAds #GetAMac #WindowsSecurity #TechHumor #Advertising
Remember when the CrowdStrike BSOD fiasco turned the digital world into a dystopian nightmare? Apple does, and they're not letting us forget. Their new ad is a darkly humorous jab at #WindowsSecurity woes. #TechHumor #AppleAd theverge.com/news/794185/ap…...
I explain how Windows implements ASLR, how it affects reverse engineering and exploitation, and practical ways to analyze or bypass it when needed. reverselabs.dev/blog/aslr-addr… #WindowsSecurity #ReverseEngineering #ExploitDevelopment #MemoryProtection

1000+ alumni, 10 editions, and one course that prepares you for 2026’s threats 🎉 In 3 weeks, we're launching the 10th edition of our Advanced Windows Security Course, so join us last-minute 👉cqureacademy.com/cyber-security… #CyberSecurity #WindowsSecurity

Atlas OS : un outil gratuit pour personnaliser et sécuriser Windows facilement. De nombreuses options de configuration sans risque ! #AtlasOS #WindowsTweaker #WindowsSecurity #WindowsOptimization
Today I learned about UAC User Account Control (UAC) is a key part of Windows security. UAC reduces the risk of malware by limiting the ability of malicious code to execute with administrator privileges. learn.microsoft.com/en-us/windows/… #windowssecurity #cybersecurity
AMSI watches script code as it runs and asks your antivirus if it’s safe. Learn how it works, why attackers try to dodge it, and what defenders should do. redsecuretech.co.uk/blog/post/amsi… #AMSI #WindowsSecurity #PowerShell #CyberSecurity #EndpointProtection #InfoSec #ThreatHunting

𝐖𝐡𝐚𝐭 𝐢𝐬 𝐭𝐡𝐞 𝐖𝐢𝐧𝐝𝐨𝐰𝐬 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐁𝐮𝐭𝐭𝐨𝐧 𝐚𝐧𝐝 𝐇𝐨𝐰 𝐭𝐨 𝐔𝐬𝐞 𝐈𝐭? A quick and easy guide for all users! 💻🔐 👉 Read more: t.ly/4fq3o #WindowsTips #CyberSecurity #WindowsSecurity #DeviceSecurity #StaySafeOnline #MicrosoftWindows

2025 ADMX templates boost security with app install controls (Windows 11), Excel external link blocking, Office AI settings, and Outlook migration management. Updates include 81+ new policies for SMB, printing, and Defender. #GroupPolicy #WindowsSecurity pupuweb.com/how-do-the-lat…
The @cyber_sec_conf in Orlando, Florida is just 4 days away! 🌴 Join @PaulaCqure’s keynote, session and workshop October 6-9 👉 cybersecurityintersection.com/#!/register See you soon 👀 #CybersecurityIntersection #WindowsSecurity #CybersecConference
Hurry up, this is the last chance to enter our virtual classroom with up to 35% discounts! 🔔 The Back to School offer on our flagship online courses expires tomorrow, so don’t be late for premiere cybersec education 👉 cqureacademy.com/back-to-school/ #Cybersec #CQURE #WindowsSecurity
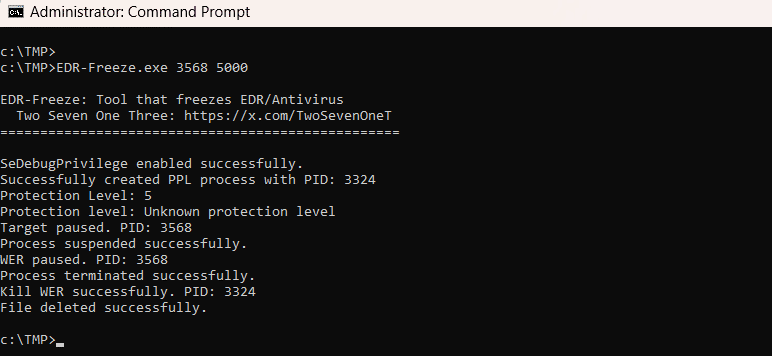
New EDR bypass technique exploits Windows Error Reporting and MiniDumpWriteDump to suspend antivirus tools without vulnerable drivers. Researchers decoded WerFaultSecure to enable stealth attacks. #EDRFrozen #MiniDumpWriteDump #WindowsSecurity ift.tt/6lU8147
Traditional antivirus vs EDR for Windows: ❌ Antivirus: Reactive, signature-based ✅ EDR: Proactive, behavior-based ✅ Real-time monitoring ✅ Threat hunting ✅ Incident response ✅ Forensic analysis Upgrade your Windows security: businesspcsupport.com/endpoint-detec… #WindowsSecurity #EDR
Attention IT Pros! The Microsoft UEFI CA, which SecureBoot relies on, will expire on Monday October 19, 2026, after 15 years of validity. Mark this date in your calendar. Devices require a Firmware/DB update; otherwise, stop booting. 🔒#WindowsSecurity support.microsoft.com/en-us/topic/kb…

I explain how Windows implements ASLR, how it affects reverse engineering and exploitation, and practical ways to analyze or bypass it when needed. reverselabs.dev/blog/aslr-addr… #WindowsSecurity #ReverseEngineering #ExploitDevelopment #MemoryProtection

🚨 Attention Windows users: A new zero-day NTLM vulnerability can expose your NTLM credentials just by viewing a malicious file in Explorer. Microsoft is still working on a patch. #WindowsSecurity #ZeroDay

Windows & Linux Enumeration: Discover What the System Reveals 🖥️🐧🔍 #Enumeration #LinuxSecurity #WindowsSecurity #InfoSec #EthicalHacking #CyberSecurity #EducationOnly #SystemRecon #PrivilegeEscalation #RedTeamTools




We are excited to announce another speaker: Sami Laiho! Sami will be talking about securing Windows and it's entire ecosystem. Don't miss his interview on YouTube: bit.ly/49SlGow #WPNinjaS #WindowsSecurity

الجزء 2 | 🚨 Windows Forensics Series تحليل العمليات، الشبكة، المستخدمين، الخدمات، والمهام المجدولة 🔍 📌 الهدف: كشف أي نشاط مريب أو Shell يعمل بصمت داخل النظام. #DFIR #WindowsSecurity #CyberSecurity ⬇️ تابع 🧵 1 📌 تحليل العمليات المتقدمة: wmic process list full يعرض…

Struggling with guest access being blocked in Windows environments? Our latest article walks through how to adjust security policies to restore guest access; without compromising your network integrity. pnwcomputers.blogspot.com/2025/09/securi… #PNWComputers #WindowsSecurity #GuestAccess…

Unmasking Malware's Tricks! 🔍 This encyclopedia reveals Windows evasion techniques used by malware to hide in virtual environments. Learn to detect and analyze even the stealthiest threats. buff.ly/3XJLtMT Credit goes to Checkpoint! #Cybersecurity #WindowsSecurity

🔍 Windows OS Security Analysis: Understanding System Architecture 🛡️ 💻 🔐 Hashtags:🔖 #WindowsSecurity #OperatingSystemSecurity #CyberSecurity #InfoSec #SystemHardening #SecurityAnalysis #AccessControls #SecurityConfiguration #DefensiveSecuriy #WindowsAdministration



VerdaCrypt, a sophisticated PowerShell ransomware, targets over 100 file types and uses philosophical ransom notes to manipulate victims. Its stealth mode complicates detection significantly. 🚨🖥️ #RansomwareThreat #WindowsSecurity link: ift.tt/3ho9X7F

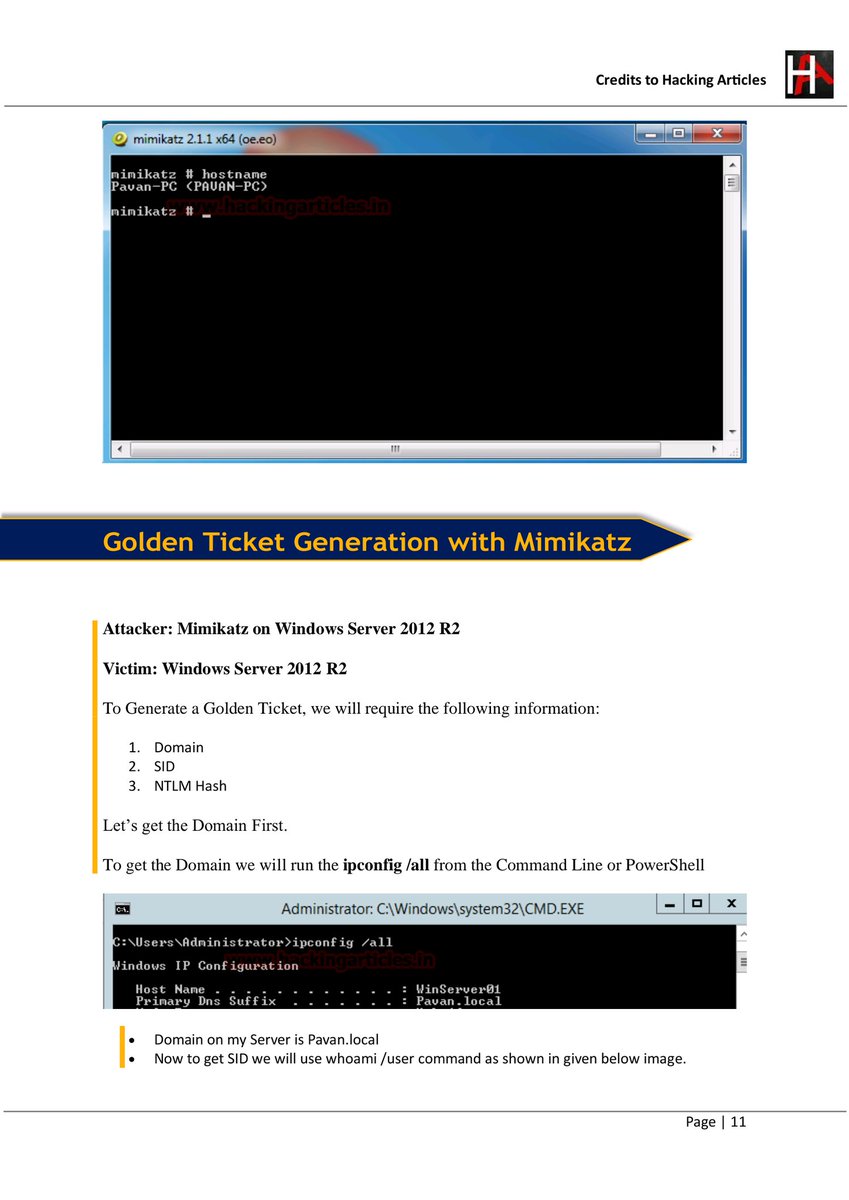
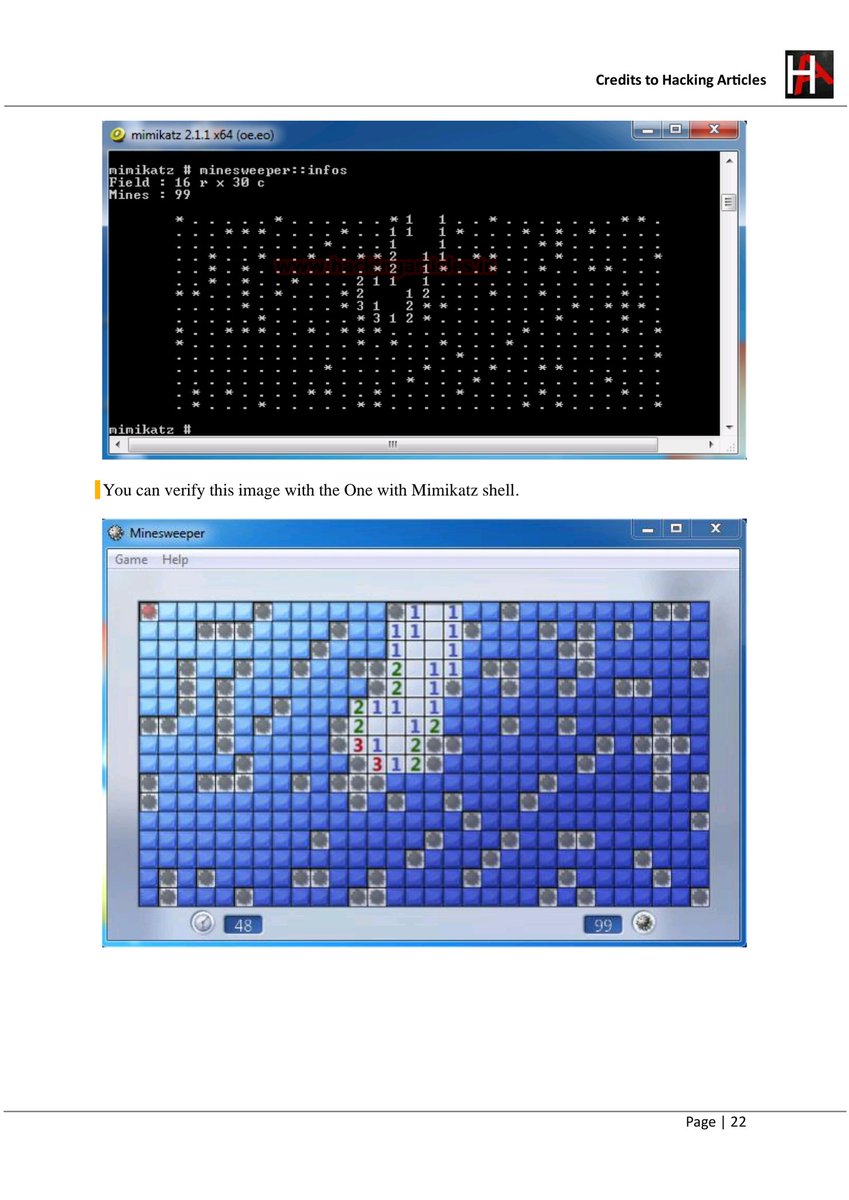
Credential Extraction in Windows Environments: Understanding Mimikatz 🧠🪪💻 #Mimikatz #WindowsSecurity #PenetrationTesting #EthicalHacking #InfoSec #CredentialSecurity #EducationOnly #RedTeam #CyberAwareness


Exploring Windows Privilege Escalation on Hack The Box's Arctic machine! 🖥️ An Nmap scan reveals a hidden Admin panel for Adobe ColdFusion 8. Strategies and exploits are key! #WindowsSecurity #PrivilegeEscalation #USA link: ift.tt/TK1HVcv

🛡️CISA warns of Windows flaw used in infostealer malware attacks🛡️ bleepingcomputer.com/news/security/… #CISA #WindowsSecurity #CyberSecurity #InfoStealer #Malware #CyberThreats #SecurityAlert #Infosec #Vulnerability

Coming soon... New test results of security solutions for #Windows 10 by @avtestorg ! #WindowsSecurity #cybersecurity #certification #review

🚨 New Blog Post Read the full post to understand the risks and how to protect your systems: ow.ly/608550VZPNB #Cybersecurity #WindowsSecurity #PrivilegeEscalation #Vulnerability #InfoSec

Just days away from the @TechMentorEvent at Microsoft HQ! 📆 @PaulaCqure delivers two must-see cybersecurity sessions on August 12th on DPAPI and DPAPI-NG & Forensics Skillset. We hope to see you there! 👀 #Cybersecurity #TechMentor #WindowsSecurity #DPAPI

Over 𝟲𝟬𝟬 𝗺𝗶𝗹𝗹𝗶𝗼𝗻 𝗰𝘆𝗯𝗲𝗿𝗮𝘁𝘁𝗮𝗰𝗸𝘀 hit Windows users every day, that's over a million threats an hour! As hackers step up their infiltration game, even companies like Microsoft are in the line of fire 🔫 #CyberSecurity #DataProtection #WindowsSecurity

LDAPNightmare PoC Exploit Crashes LSASS and Reboots Windows Domain Controllers dlvr.it/THlY2G #LDAPNightmare #Cybersecurity #WindowsSecurity #DoS #CVE2024

🚨 Microsoft urges users to act fast as 3 new zero-day vulnerabilities are actively exploited. Protect your systems by staying up-to-date with patches and improving security measures. #CyberSecurity #ZeroDay #WindowsSecurity #Microsoft #PatchYourSystems zurl.co/eVdQZ

⚠️New Windows Driver Signature bypass allows kernel rootkit installs⚠️ bleepingcomputer.com/news/security/… #WindowsSecurity #DriverBypass #Rootkit #CyberThreats #Malware #InfoSec #KernelExploitation #CyberSecurity #Vulnerability #ThreatHunting

Something went wrong.
Something went wrong.
United States Trends
- 1. Auburn 46K posts
- 2. Brewers 65.2K posts
- 3. Georgia 67.9K posts
- 4. Cubs 56.4K posts
- 5. Utah 25.2K posts
- 6. Gilligan 6,112 posts
- 7. #byucpl N/A
- 8. Kirby 24.2K posts
- 9. Arizona 41.7K posts
- 10. #SEVENTEEN_NEW_IN_TACOMA 32.1K posts
- 11. Wordle 1,576 X N/A
- 12. #AcexRedbull 4,164 posts
- 13. Michigan 62.8K posts
- 14. #Toonami 2,981 posts
- 15. #BYUFootball 1,017 posts
- 16. Boots 50.6K posts
- 17. Hugh Freeze 3,271 posts
- 18. mingyu 87.1K posts
- 19. Amy Poehler 4,875 posts
- 20. Holy War 2,209 posts